1. A little bit about digital copyright
The issue of copyright ownership is always an important issue when sharing and trading. Previously, paper books and songs were registered for intellectual property to ensure the rights of the creators and owners. This way, if someone wants to use the copyrighted products, they will have to comply with the regulations, requirements of the author, …
Currently when a lot of data and content is posted on the Internet, the issue of copyright management is also improved. Paper books and songs have a unit that manages illegal printing and use by competent authorities. Books, videos, music, … and digital data are even more strictly controlled.
For example, the battle between a cracker and a gaming unit . Cracker always wants to crack the copyright to play free games, publishers always want to protect their products so they can sell the game.
Dao a yard high, ma a staff high.
The better the game maker found the better ways to control the copyright, the more the crackers also increased their hands when constantly cracking famous offline games. Some games even have crack online =))
2. What is DRM?
Let’s talk a little bit so everyone has a small view of digital rights. DRM is also a way to protect digital rights for Ebook, PDF, audio, video files …
DRM – Digital Rights Management :
- Digital: only digital media, usually audio files, ebooks, videos, movies, games, …
- Rights: copyright. Represents the copyright owner, distributor, rights, terms and conditions for users, …
- Management: the control over the file, the ability to access content, …
DRM is essentially a way to control the copyright of digital data content based on encryption.
By using DRM, the copyright owner can control how users (digital product buyers) use their products. For example, limit the number of file installs, time limit to use, limit file users, …
3. How does DRM work?
Basically, DRM works based on encrypting the file contents with a secret key . When there is a need to use the file, a separate application to read the file will decode the file. Now we can use the file.
The operation process is more specific as follows:
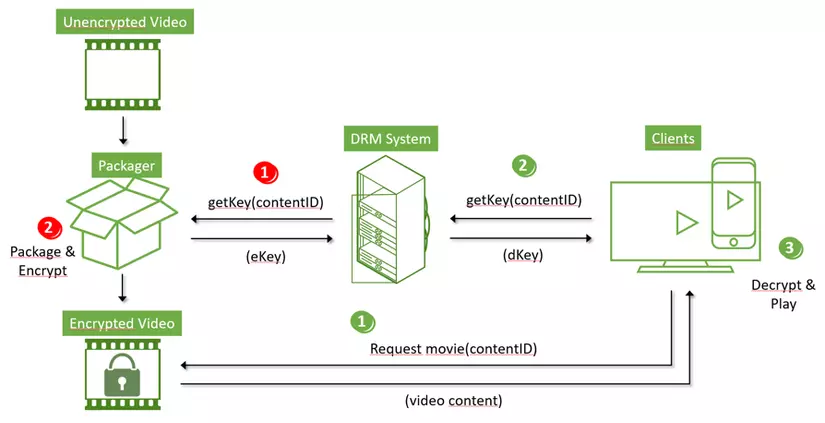
To operate, a DRM System is required to provide the Encryption key to encrypt and Decryption key to decrypt the file.
Encryption (red):
- First, the person performing the packaging will send a request to DRM System to receive eKey.
- Then use eKey to encrypt the file.
- Encrypted files will be shared out when needed.
- Sometimes the Encryption key is generated by the person who originally packaged the file. Then this key is stored on DRM System.
Decode (blue):
- When there is a need to use the file. User will open X file with specialized application. (File X is a file containing information about the content the user wants to access)
- The application will download encrypted content.
- Once you have the Encrypted file, the application will ask for a Decryption key from the DRM System.
- If the authentication information is accepted, DRM System will return dKey. The application will decode the DRM file with this dKey for users to use.
4. Benefits and inconveniences of DRM
DRM control brings both benefits and inconveniences.
Benefit:
- Owners can control user books using file.
- No need to use a separate application to read file content, DRM-controlled content can be read via 3rd party applications (There is no status as music on Spotify can only be played online on the Spotify app, counting Even when you buy a Premium package, the downloaded music can only be played on the Spotify app).
- No cumbersome confirmation when accessing, which enhances the user experience.
Limit:
- Some users find it inconvenient and annoying that they don’t have full control over the file they bought.
- While there is no specific application for reading files, reading DRM files is still required through certain applications. Without DRM, users can open the file with any application that allows reading the file format.
- Files with DRM will no longer be usable when the copyright provider is deactivated, while regular files can be used permanently.
5. Should DRM (pirated) be removed from file?
As I mentioned in Part 1 of the article, the battle between digital rights protection and copyright crack is always going on. Of course with DRM is no exception.
Nowadays, it is easy to find tools online to remove DRM from files. Popular platforms such as Spotify also have a way to decode music files to share outside (If I remember correctly, Spotify has a way to remove Digital license).
But respect for copyright is what everyone should do.
A PTIT teacher once told me, “As a programmer, we should respect software copyrights.”
Reference source:
