SQL Injection mining techniques
Tautology Base SQLi This is a common and very easy technique to change the meaning of a relational expression in a test clause.

The above code accepts recipient from user and executes database query: retrieves information about AcctNum from customer table with balance column value less than 100 and username equal to recipent value. However, when the value entered is recipent = ‘anyone’ or 1 = 1; #; then the query statement becomes:
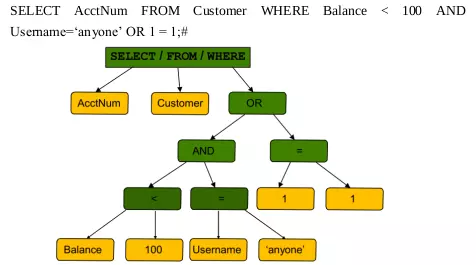
Because 1 = 1 always returns TRUE, the conditional expression returns TRUE, so the query statement will return all data of the AcctNum column in the Customer table.
–Make a demo attack
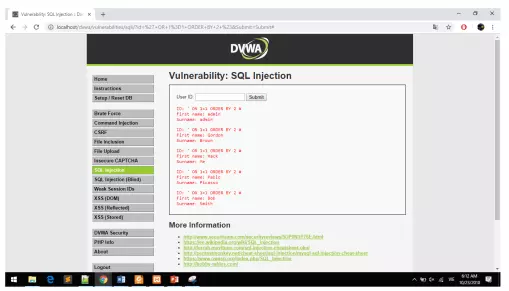
eg on Dvwa an open source PHP / MYSQL application suite containing web application layer vulnerabilities.
Perform “1 ‘or 1 = 1; #” in the User ID box and submit. The returned data is all user information in the database 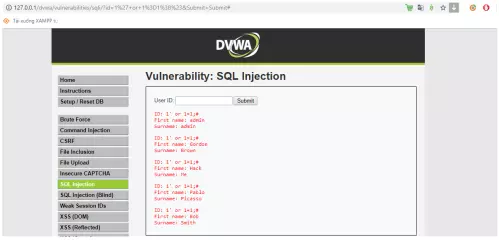 Explanation: The figure below is the source code for querying the database based on the user ID.
Explanation: The figure below is the source code for querying the database based on the user ID. 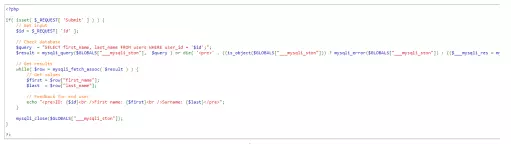
We have a query statement
$ query = ” SELECT firstname, lastname FROM users WHERE userid = ‘$ id’; “;
When entering id = 1 ‘or 1 = 1; #, the variable id is passed into the query statement, the given query statement becomes SELECT first_name, last_name FROM users WHERE user_id =’ 1 ‘or 1 = 1; #; ‘; ”
Since 1 = 1 is always true, the conditional expression WHERE user_id = ‘1’ or 1 = 1; #; ‘; always returns TRUE, causing the query statement to perform a query of all data in the user table.
Union Query Based
In MySQL, the UNION clause allows to combine the results of queries with the condition that the SELECT clause must have the same number of columns and the same data type.
However, through UNION, an attacker can easily pass a query to extract information from the database:
- Determine the number of columns in the Select clause: If the column’s STT is less than or equal to the number of columns listed in the query => executed successfully; otherwise returns an error message.
- Guess the table name, column name.
- Check data type.
- Unauthorized data extraction.
- Perform all the above risks to other databases if decentralized vulnerabilities exist on the DBMS.
– Perform a demo attack
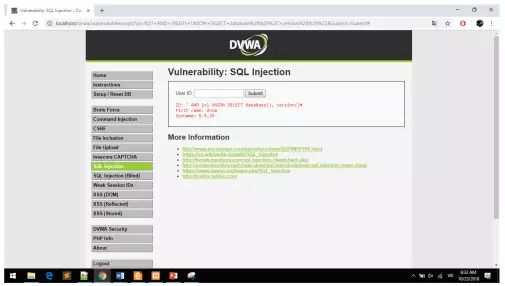
Enter the input value as: ‘AND 1 = 1 UNION SELECT database (), version () # At this time, the query statement will become:
$ query = “SELECT firstname, lastname FROM users WHERE userid = ” 1 = 1 UNION SELECT database (), version () #;
Similar to Tautology SQLi, because the conditional clause returns TRUE, this statement will perform a database query, execute the UNION clause to retrieve information about the database, the version of the database.
Order By Clause
In MySQL, the ORDER BY clause sorts the results by a certain column listed in the SELECT clause.
Similar to UNION QUERY BASE, in this technique, the attacker injects the following code:
- Guess the number of columns listed in the query: If the column number is less than or equal to the number of columns listed in the query => performed successfully; otherwise returns an error message.
- Guess the name of the database column in the query: If the column name in the clause matches the column name in the query: done successfully; otherwise returns an error message.
– Perform a demo attack
Enter the input value as: ‘OR 1 = 1 ORDER BY 2; #
At this time, the database query becomes:
$ query = “SELECT firstname, lastname FROM users WHERE userid = ” OR 1 = 1 ORDER BY 2″; # “
Similar to Tautology SQLi, because the conditional clause returns TRUE, this statement will perform a database query, execute the ORDERBY clause, which will retrieve all the data in the user table and sort by column 2 in the sentence. query.
Boolean Base and Time Base Blind SQL Injection
In some cases, the system does not return an SQL statement execution error message, an attacker can use the following two techniques to perform information exploration about the database:
- Boolean Base Blind SQL Injection: use true / false return query The basis of this technique is the comparison of true and false to find each character of information such as table name, column name … Therefore, With a range of alphanumeric values (including upper and lowercase), and some special characters, matching becomes very difficult and time-consuming. Therefore, the exploitation of bugs is mainly conducted by tools.
- Time-base BLIND SQL INJECTION: checking query execution time However, both of these methods take a long time to exploit Blind SQLi errors, so they often use support tools like SQL map.
