Upload, Download files are common functions on Web applications, App. However, few people know when implementing this function will have vulnerabilities that create security injection. In this series I will introduce flaws that often arise in file upload or file download functionality.
1. Overview of issues when uploading, downloading files
There are the following attacks against file uploads and downloads:
- 12Tấn công DoS đối với chức năng upload
- 12Tấn công chạy file Script trên Server
- 12Tấn công khiến người sử dụng download file có chứa mã độc
- 12Download vượt quá quyền hạn của file
Below I will explain each attack case.
1.1 DoS attack against upload function
For the upload function of a Web application, there is a possibility that a DoS (Denial of Service Attack) attack will take up a huge amount of resources in the Website by continuously sending large files.
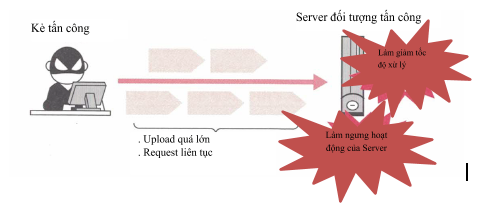
DoS attacks will have effects such as slow processing speed, or worst case scenario, server downtime.
In the countermeasures of this type of attack, limiting the file upload size is a very effective measure. For PHP, it is possible to limit the size of the upload function using config php.ini.
| Variable name | Meaning | Default value |
|---|---|---|
| file_uploads | Is it possible to use the file upload function? | ON |
| upload_max_filesize | Maximum size of each file | 2MB |
| max_file_uploads | Maximum number of files that can be sent | 20 |
| post_max_size | max body size of POST Request | 8MB |
| memory_limit | max size memory | 128MB |
In case the app doesn’t provide file upload functionality, set file_uploads to Off.
Or you can limit Request body size with Apache’s httpd.conf config. This setting can be used in languages other than PHP, and it is also possible to set error requests by checking at an early stage so it is very effective in improving the resistance to DoS attacks. Below is the config in case the body size of the Request is reduced to 100Kb.
1 2 | LimitRequestBody 102400 |
For the limitation method for other languages, please refer to the instruction manuals for each language.
**Attention: **
The content explained above only revolves around checking the size of the uploaded file. However, to improve resistance to DoS attacks, other parameters should be checked. For example, when processing files on the server, the file size after decompression will be more noticeable than the file size when compressed. Therefore, not only need to check the file size when uploading, but also take into account the file size after extracting (if any) and try to check in the first stage.
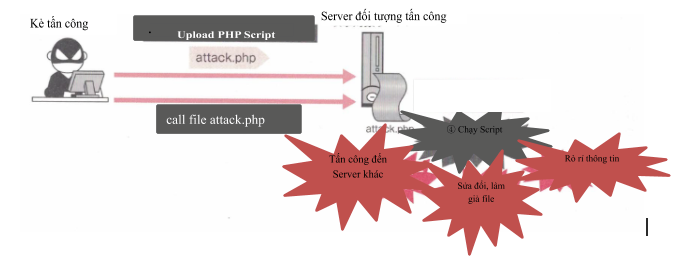
1.2 Run the Script file on the Server
In case the user uploads the script file to the server, it can cause effects such as information leakage, file tamper modification, attacks on other servers, …
1.3 Attack causing a user of the system to download a file containing malicious code
A third attack that takes advantage of an uploader is an attacker uploading a file containing malicious code. When another user queries that file, there may be situations like running Script on the user’s PC or being infected with malware. 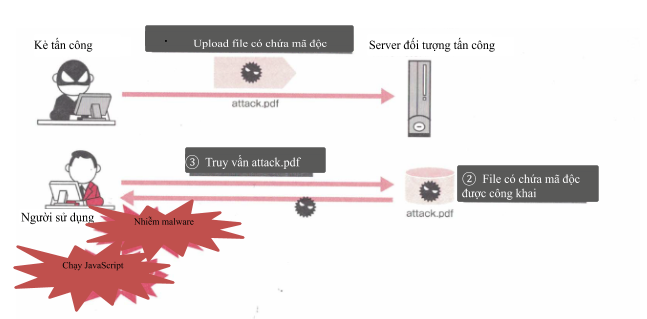
The reason to run JavaScript when downloading is because the file was uploaded to HTML in error.
On the other hand, the technique of infecting malware when downloading files is a technique that takes advantage of the vulnerabilities of the program opening the downloaded file.
In cases where a user is infected with malware due to a file download, the direct responsibility for the infection lies with the person who uploaded the malware, but there are cases where the uploader operator is also responsible. Therefore, when checking the service spec of the Website, it is necessary to base on the nature of the Website to decide whether to fight malware on the site or not.
1.4 Download has exceeded the permissions of the file
One problem when downloading fille is that in the case where the file is inherently only the user with the rights can download, the user without the permission can still download it.
The cause of this problem is that in many cases, the access limit for the file is not set and the file can be downloaded based on URL speculation.
* Next I will describe the methods of attack and prevention *
2. Run Script on the Server by file upload
2.1 Overview
In the uploader there is a section to save the file uploaded by the user to the Web Server’s public directory. If you can upload files with script extensions of languages such as php, asp, aspx, jsp … you can run the uploaded Script file on the Web Server.
Running a script that is sent from the outside can cause the same effects as OS Command Injection. Specifically, these effects are as follows:
- 12Truy vấn, làm giả, sửa đổi, xóa file trong Web Server
- 12Gửi mail ra bên ngoài
- 12Tấn công đến Server khác
To prevent scripts from being run on the server by file upload, you can take either of the following measures, or both simultaneously.
- 12File do user upload lên không đưa vào public directory
- 12Giới hạn file upload (không cho upload file script)
2.2 Technical attack and influence
Suppose we have implemented the file Upload screen as follows:
1 2 3 4 5 6 7 8 | <body> <form action="upload.php" method="POST" enctype="multipart/form-data"> File:<input type="file" name="imgfile" size="20"><br> <input type="submit" value="Upload"> </form> </body> |
upload.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | <?php $tmpfile = $_FILES["imgfile"]["tmp_name"]; $tofile = $_FILES["imgfile"]["name"]; if (!is_upload_file($tmpfile)){ die('File have not been uploaded'); } else if(!move_uploaded_file($tmpfile,'img/' <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> )){ die('Cannot upload file'); } $imgurl='img/'.urlencode($tofile); ?> <body> <a href="<?php echo htmlspecialchars(@imgurl); ?>"><?php echo htmlspecialchars($tofile, ENT_NOQUOTES, 'UTF-8');?></a> have been uploaded<br> <img src="<?php echo htmlspecialchars($imgurl); ?>"> </body> |
At this point we have the screen Upload file okay. However, instead of uploading the image file, we will upload the script file below.
acttack.php
1 2 3 4 5 6 | <pre> <?php system('bin/cat etc/passwd'); ?> </pre> |
This PHP Script calls the cat command using the system function, then displays the contents of / etc / passwd. After uploading the script file, the browser screen will show ” acttack.php have been uploaded”. Click the link acttack.php on the screen to run the script and display the contents etc / passwd
2.3 The cause of the hole arises
Script file upload running vulnerability occurs when the following conditions are met:
- 12File upload được lưu vào public directory
- 12Có thể upload các file script
For the uploader, creating an application that meets the above two conditions will become the cause of the vulnerability. Therefore, the failure to satisfy at least one of the two above-mentioned conditions becomes the countermeasure to resolve this gap.
2.4 For books
As explained above, the two conditions for running Script file upload are when the file is saved to the public directory and the user can specify the script file to upload.
Breaking one of the two conditions becomes the countermeasure of this problem, but since there are cases where the spec requires permission to upload script files, we will go into solving the problem of “not saving uploaded files to public directory”.
Edit file upload.php again as follows
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | <?php function get_upload_file_name(tofile){ //giản lược } $tmpfile = $_FILES["imgfile"]["tmp_name"]; $tofile = $_FILES["imgfile"]["name"]; if (!is_upload_file($tmpfile)){ die('File have not been uploaded'); } $tofile=get_upload_filename($orgfile); if(!move_uploaded_file($tmpfile,$tofile)){ die('Cannot upload file'); } $imgurl='download.php?file=' .basename($tofile); ?> <body> <a href="<?php echo htmlspecialchars(@imgurl); ?>"><?php echo htmlspecialchars($orgfile, ENT_NOQUOTES, 'UTF-8');?></a> have been uploaded<br> <img src="<?php echo htmlspecialchars($imgurl); ?>"> </body> |
The upload code has been edited in 2 places. First change the location of the file from public directory (/ img) to the filename the get_upload_file_name function returns, then create the url image (download.php).
Below is the source of the get_upload_file_name function.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 | define('UPLOADPATH', '/var/upload'); function get_upload_file_name($tofile) { //check đuôi file $info = pathinfo($tofile); $ext = strtolower($info['extension']); //lowercase extension if($ext !='gif'&& $ext !='jpg'&& $ext !='png'){ die('error msg'); } // gen uniqued file name $count = 0; do { $file = sprintf('%s/%08x.%s', UPLOADPATH, mt_rand(), $ext); //create file. Nếu file đã tồn tại thì out error $fp = @fopen($file, 'x'); } while($fp === FALSE && ++$count <10); if($fp === FALSE){ die ('error msg'); } fclose($fp); return $file; } |
At get_upload_file_name function, first get the extension, confirm whether it’s one of the three gif, jpg, or png extensions. Next, after using a random number to create a non-duplicate file name with the original extension, check if the file name is duplicated or not. The reason to set the option ‘x’ of fopen and then open the file after creating the file name is because an error will occur in case the file already exists. In that case, recreate the file and then repeat the above operation. Keep doing this until fopen no longer occurs. However, there are also cases where the error occurs due to a reason other than the file name conflict, so in case the number of filename rebuilds exceeds 10 times, the processing will be stopped.
Then close the file. The file created here will not be deleted but overwritten with move_uploaded_file function. If you delete this file, the uniqueness of the filename will not be guaranteed.
Next, below is the source of download.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <?php // Note : có lỗ hổng XSS trong cách implement này define('UPLOADPATH', '/var/upload'); $mimes = array('gif' => 'image/gif', 'jpg' => 'image/jpg', 'png' => 'image/png'); $file = $_GET('file'); $info = pathinfo('file'); //get file info $ext = strtolower($info['extension']); $content_type = $mimes[$ext]; //get Content-Type if(!$content_type){ die('error msg'); } header('Content-Type:'.$content_type); readfile(UPLOADPATH.'/'.basename($file)); ?> |
This script specifies the filename using the querystring file. First, in case of getting the extension with the extension other than gif, jpg, png, then set error. Then, after output Content-Type for each extension, read the data of the file with readfile and keep the output. Entering the filenames received with the querystring into the basename function is the argument of the Directory Traversal vulnerability.
By the current argument you can prevent script file upload running. However, in this script, if the user uses Internet Explorer (IE), it is likely that he will encounter a Cross Site Scripting attack.
[Continue..]
