Security at the endpoint (Endpoint) – The inevitable trend of security on cyberspace
- Tram Ho
According to market analysis and analysis firm Gartner, businesses need to be fully equipped with Information Security (ATTT) solutions to be able to detect malware and signs of attacks on their systems. Since then, businesses have reasonable preventive measures. Featured including the EDR solution (Endpoint Detection and Response – Detect and troubleshoot from the endpoint – the first computers exposed to network attacks) has been recommended by businesses / groups. functional use.
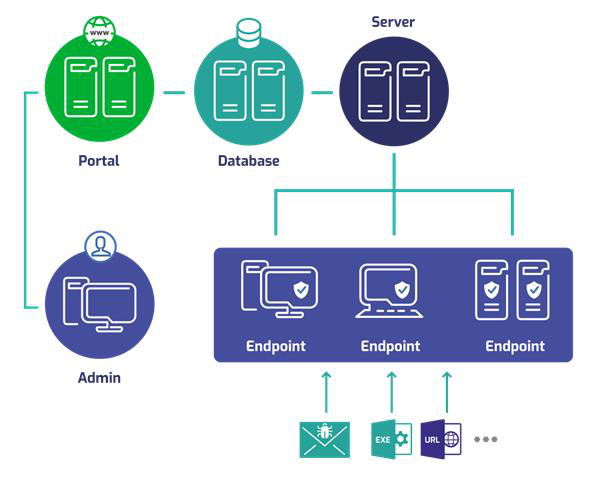
In essence, EDR is like a series of network security cameras on each endpoint computer, to collect all data about the events that occur on these devices. They will then be gathered at a common database, and analyzed under the eyes of network security experts, to detect, investigate and eliminate threats to the network in an instant.
Facing this new security trend, however, in Vietnam, many businesses / organizations have not been able to access this solution yet, partly because EDR solutions of big foreign companies are very expensive, partly because Concern in customer support in case of emergency due to the support team of airlines not in Vietnam
Foreseeing this need, in the past few years, Viettel Cyber Security (VCS) has researched and developed its own EDR solution called VCS-aJiant. Sticking to the requirements and guidelines for complete EDR solutions, VCS-aJiant aspires to compete on par with other EDR solutions in the world.
Deep monitoring of the system for early detection of suspicious behavior
One of the first notable features of VCS-aJiant lies in the technology that monitors the deepest behavior of the system is the driver level. Using Filter Driver technology, the Endpoint Security feature monitors all behaviors related to file processing, File, Process, Memory, Registry and Network. on user computers and servers – Endpoints in organization and enterprise information systems.
This monitoring technology allows VCS-aJiant to identify suspicious behaviors and then they are sent to the Back-End system for centralized analysis. In-depth monitoring of system behaviors helps VCS-aJiant to quickly detect suspicious behaviors as well as data sources related to those behaviors.
Based on deep monitoring in the system, VCS-aJiant can detect even when there are only signs of attack activity instead of waiting until the consequences of the system are compromised. This not only gives administrators an early warning of suspicious behavior, before the system breach takes place, but also allows VCS-aJiant to identify and classify the warning level for each. this activity.
All events will be saved on VCS-aJiant
Integration of products in the ecosystem
Despite the ability to identify suspicious behavior early, EDR solutions can become ineffective if not integrated and synchronized with complementary products in the ecosystem. Meanwhile, VCS-aJiant solution not only has the ability to operate independently, but when placed in the ecosystem of security solutions solutions of Viettel Network Security, combined with a team of high-quality security experts High quality, businesses / organizations are placed in a layer of security against deliberate and advanced attacks from hackers.
Experience and knowledge inside the product
As the largest network operator (ISP) in Vietnam and expanding in 10 different markets around the world, VCS-aJiant’s “real battle” to protect infrastructure and networks of Viettel’s network helps This solution has a remarkable advantage compared to competitors when there is a lot of experience and a wealth of offensive knowledge.

This shows that VCS-aJiant is not only worthy of being one of the leading EDR solutions in Vietnam market but also is on its way to becoming a security product to compete with competitors in the international arena.
Source : Genk
