Link to download apk file: UnCrackable-Level1.apk
UnCrackable Level 1 is the first lesson of reverse android apk in Owasp’s mobile reverse engineeing exercise series.
Original repo link: https://github.com/OWASP/owasp-mstg/tree/master/Crackmes
To be true for the purpose of practice, I will do this lesson by the method: Static and Dynamic.
Decompiled code structure
Structure of the decompiled code file by the bytecode viewer:
1 2 3 4 5 6 7 8 9 10 11 | sg.vantagepoint/ ├── a/ │ ├── a.class │ ├── b.class │ ├── c.class └── uncrackable1/ ├── a.class ├── MainActivity$1.class ├── MainActivity$2.class └── MainActivity.class |
The file name and the function name are all abc so it can be confusing and confusing during the process.
Bypass root check
As soon as the application is opened, a message “Root detected” will appear. Click the “OK” button, the program will be off.
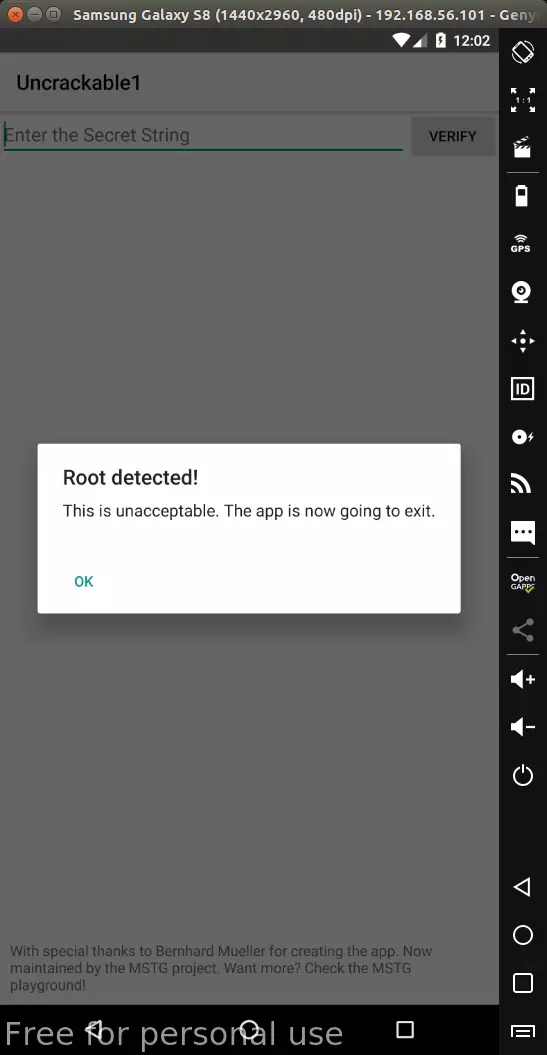
So the first step is to bypass the root check. If only to see the functionality of the app like, you can install the apk on a device that is not rooted. Of course we don’t do that, if detected, we bypass it immediately.
Code to check root:
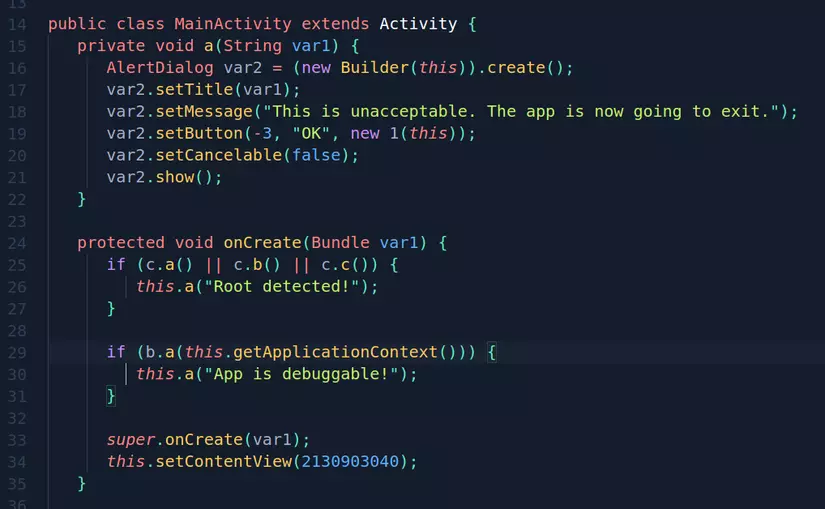
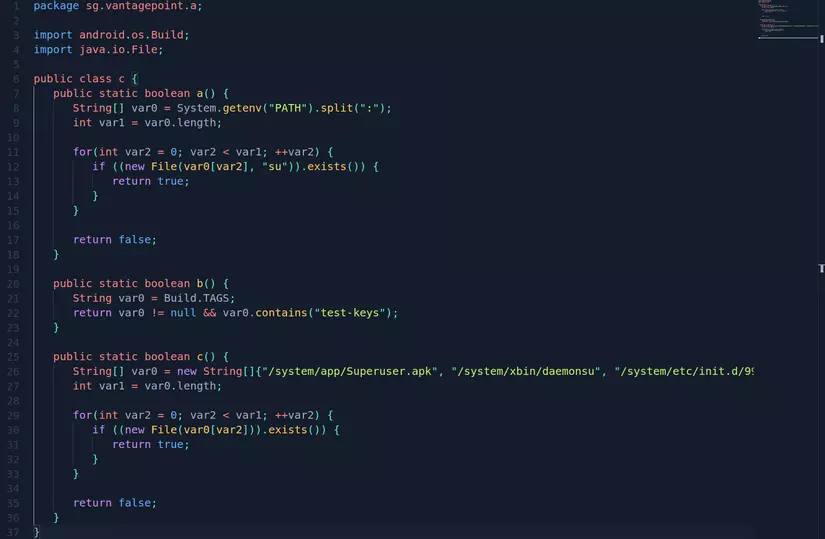
The root test is done in three ways, the c class in package sg.vantagepoint.a will do this
Static: patch apk
Decompile with apktool: java -jar apktool_2.4.1.jar d UnCrackable-Level1.apk
Edit the code 3 functions ca () , cb () and cc () in smali / sg / vantagepoint / a. The fix is very simple, just make sure these 3 functions always return false : fix the const / 4 segments before the return statement to declare all 0x0. For example: const/4 v0, 0x1 -> const/4 v0, 0x0
Rebuild using apktool: java -jar apktool_2.4.1.jar b UnCrackable-Level1
Generate key: keytool -genkeypair -v -keystore key.keystore -alias publishingdoc -keyalg RSA -keysize 2048 -validity 10000
Sign new apk: jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore ./key.keystore UnCrackable-Level1.apk publishingdoc
Reinstalled and no further notifications appeared.
Modified smali code: c.smali
Dynamic: hook by Frida
The first idea is that I will hook and fix the contents of 3 functions ca () , cb () and cc () return false all. That will pass the root check of the app:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | <span class="token keyword">import</span> frida <span class="token keyword">import</span> sys <span class="token keyword">def</span> <span class="token function">onMessage</span> <span class="token punctuation">(</span> message <span class="token punctuation">,</span> data <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> message <span class="token punctuation">)</span> package <span class="token operator">=</span> <span class="token string">"owasp.mstg.uncrackable1"</span> jscode <span class="token operator">=</span> <span class="token triple-quoted-string string">""" Java.perform(function () { send("[-] Starting hooks sg.vantagepoint.a.c"); var rootCheck = Java.use("sg.vantagepoint.a.c"); rootCheck.a.implementation = function() { return false; }; rootCheck.b.implementation = function() { return false; }; rootCheck.c.implementation = function() { return false; }; }); """</span> process <span class="token operator">=</span> frida <span class="token punctuation">.</span> get_usb_device <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> attach <span class="token punctuation">(</span> package <span class="token punctuation">)</span> script <span class="token operator">=</span> process <span class="token punctuation">.</span> create_script <span class="token punctuation">(</span> jscode <span class="token punctuation">)</span> script <span class="token punctuation">.</span> on <span class="token punctuation">(</span> <span class="token string">"message"</span> <span class="token punctuation">,</span> onMessage <span class="token punctuation">)</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> <span class="token string">"[*] Hooking"</span> <span class="token punctuation">,</span> package <span class="token punctuation">)</span> script <span class="token punctuation">.</span> load <span class="token punctuation">(</span> <span class="token punctuation">)</span> sys <span class="token punctuation">.</span> stdin <span class="token punctuation">.</span> read <span class="token punctuation">(</span> <span class="token punctuation">)</span> |
But failed. I checked and thought that the code was not wrong. I guess the reason the hook failed was because these functions were called as soon as the program started (called right onCreate () ) so frida couldn’t prepare it.
=> Need to find a function that has not been called as soon as the program starts so that Frida can hook and fix the content.
Note that the app closes only when pressing OK button in root detection notification. So the second idea is to hook and change the function of that button. Here is the executable of the OK button:
1 2 | var2 <span class="token punctuation">.</span> <span class="token function">setButton</span> <span class="token punctuation">(</span> <span class="token operator">-</span> <span class="token number">3</span> <span class="token punctuation">,</span> <span class="token string">"OK"</span> <span class="token punctuation">,</span> <span class="token keyword">new</span> <span class="token class-name">1</span> <span class="token punctuation">(</span> <span class="token keyword">this</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
New 1 (this) is the code in MainActivity $ 1.class:
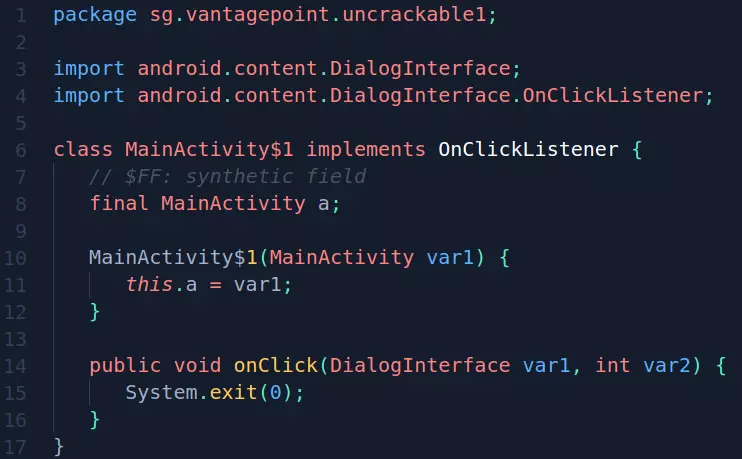
When clicking the OK button, it will run the System.exit (0) function, if you want to prevent the program from closing, we can hook and edit the exit function content:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | <span class="token keyword">import</span> frida <span class="token keyword">import</span> sys <span class="token keyword">def</span> <span class="token function">onMessage</span> <span class="token punctuation">(</span> message <span class="token punctuation">,</span> data <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> message <span class="token punctuation">)</span> package <span class="token operator">=</span> <span class="token string">"owasp.mstg.uncrackable1"</span> jscode <span class="token operator">=</span> <span class="token triple-quoted-string string">""" Java.perform(function () { send("[-] Starting hooks java.lang.System.exit"); var sysexit = Java.use("java.lang.System"); sysexit.exit.implementation = function(var_0) { send("[+] Success: prevent application exit"); }; }); """</span> process <span class="token operator">=</span> frida <span class="token punctuation">.</span> get_usb_device <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> attach <span class="token punctuation">(</span> package <span class="token punctuation">)</span> script <span class="token operator">=</span> process <span class="token punctuation">.</span> create_script <span class="token punctuation">(</span> jscode <span class="token punctuation">)</span> script <span class="token punctuation">.</span> on <span class="token punctuation">(</span> <span class="token string">"message"</span> <span class="token punctuation">,</span> onMessage <span class="token punctuation">)</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> <span class="token string">"[*] Hooking"</span> <span class="token punctuation">,</span> package <span class="token punctuation">)</span> script <span class="token punctuation">.</span> load <span class="token punctuation">(</span> <span class="token punctuation">)</span> sys <span class="token punctuation">.</span> stdin <span class="token punctuation">.</span> read <span class="token punctuation">(</span> <span class="token punctuation">)</span> |
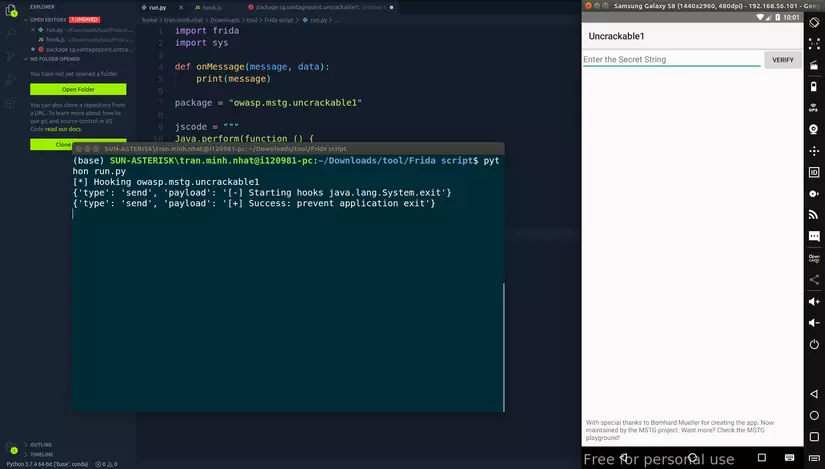
Success! We have bypassed the root check.
Actually, it is not really bypass root check because we only prevent the exit program when pressing OK button. But what we really need is access to the main functions of the app, and whether or not the root bypass is not important, because the remaining functions of the app are not affected depending on the root device or not.
Get flag
At MainActivity of the app has input function and test button. If the input is correct (enter the flag), it will say “Success”, otherwise “Nope”. This function is handled in the MainActivity.verify () function.
The input test is handled by class sg.vantagepoint.uncrackable1.a :
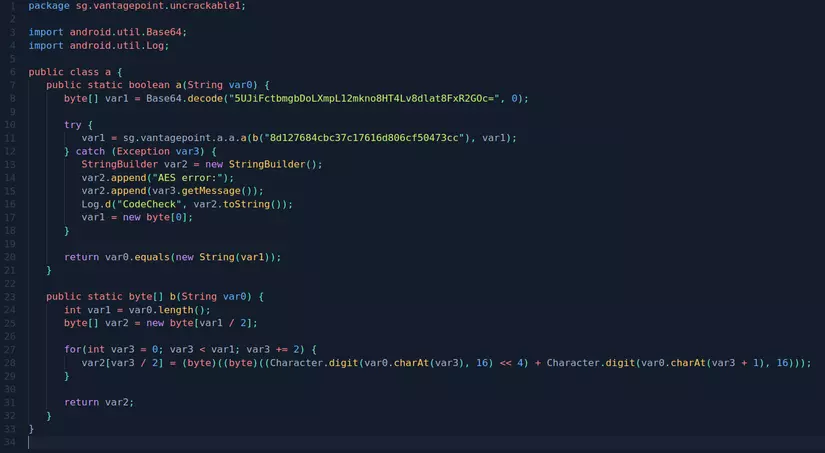
No matter what the code does, we just need to consider how the flow of the check input process works:
1 2 3 4 5 6 7 8 9 10 11 12 | -> Decode B64 xâu "5UJiFctbmgbDoLXmpL12mkno8HT4Lv8dlat8FxR2GOc=" và convert sang mảng kiểu byte (1) -> Gọi hàm sg.vantagepoint.uncrackable1.a.b() để convert hex string "8d127684cbc37c17616d806cf50473cc" thành mảng kiểu byte (2) -> Gọi hàm sg.vantagepoint.a.a.a() với 2 tham số lần lượt là mảng kiểu byte từ bước 2 và bước 1. -> Chuyển kết quả của hàm sg.vantagepoint.a.a.a() thành String (4) -> So sánh input nhập vào với string tại bước 4 -> Nếu input giống với string tại bước 4 thì đúng là flag và hiện thông báo Success. |
We will change this flow, the goal is to get the result of the function sg.vantagepoint.aaa () with the correct parameter is 2 array of bytes.
Dynamic: hook by Frida
When hooking with frida, I think of 2 directions of hook:
Method 1: After you have run the check input function once, use Java.choose () to search the heap and reuse that function with the correct input. So we will get the result of the – flag to find.
This method just stopped at my idea, but I have not done it. Because the parameter transmission is a byte array array I have not done. If you want to convert the hex string to a byte array using the sg.vantagepoint.uncrackable1.ab () function, there’s always a problem, because sg.vantagepoint.uncrackable1.ab () and sg.vantagepoint.aaa () are in two different classes. .
So I need to find another way to hook
Method 2: Use Java.use () to hook the sg.vantagepoint.aaa () function and fix the content of the function right before the function is run. The idea is that I will hook the sg.vantagepoint.aaa () function, fix the content for this function to call its own instance before being hooked. A little confusing huh, specifically as shown in the following picture:
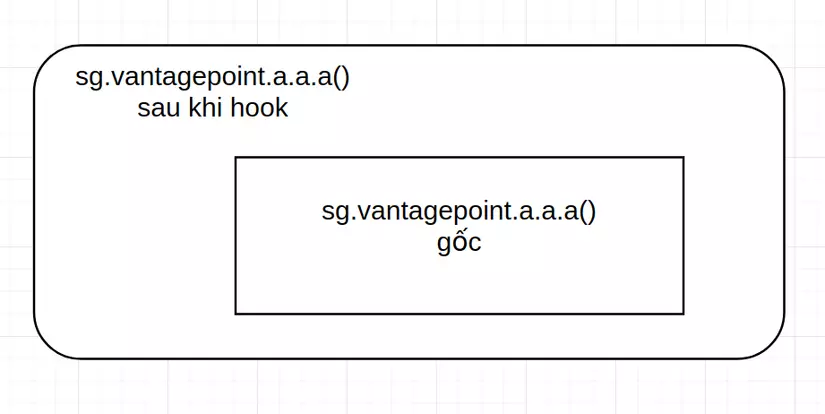
Following that idea, we have the script:
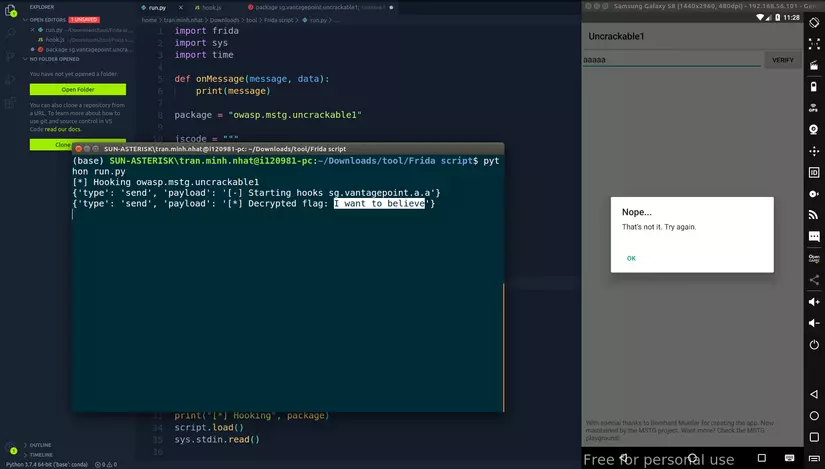
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 | <span class="token keyword">import</span> frida <span class="token keyword">import</span> sys <span class="token keyword">import</span> time <span class="token keyword">def</span> <span class="token function">onMessage</span> <span class="token punctuation">(</span> message <span class="token punctuation">,</span> data <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> message <span class="token punctuation">)</span> package <span class="token operator">=</span> <span class="token string">"owasp.mstg.uncrackable1"</span> jscode <span class="token operator">=</span> <span class="token triple-quoted-string string">""" Java.perform(function () { send("[-] Starting hooks sg.vantagepoint.a.a"); var aes_decrypt = Java.use("sg.vantagepoint.a.a"); aes_decrypt.a.implementation = function(var_0, var_1) { var ret = this.a.call(this, var_0, var_1); var flag = ""; for (var i=0; i < ret.length; i++){ flag += String.fromCharCode(ret[i]); } send("[*] Decrypted flag: " + flag); return ret; }; }); """</span> time <span class="token punctuation">.</span> sleep <span class="token punctuation">(</span> <span class="token number">1</span> <span class="token punctuation">)</span> process <span class="token operator">=</span> frida <span class="token punctuation">.</span> get_usb_device <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> attach <span class="token punctuation">(</span> package <span class="token punctuation">)</span> script <span class="token operator">=</span> process <span class="token punctuation">.</span> create_script <span class="token punctuation">(</span> jscode <span class="token punctuation">)</span> script <span class="token punctuation">.</span> on <span class="token punctuation">(</span> <span class="token string">"message"</span> <span class="token punctuation">,</span> onMessage <span class="token punctuation">)</span> <span class="token keyword">print</span> <span class="token punctuation">(</span> <span class="token string">"[*] Hooking"</span> <span class="token punctuation">,</span> package <span class="token punctuation">)</span> script <span class="token punctuation">.</span> load <span class="token punctuation">(</span> <span class="token punctuation">)</span> sys <span class="token punctuation">.</span> stdin <span class="token punctuation">.</span> read <span class="token punctuation">(</span> <span class="token punctuation">)</span> |
Hook result:
Static: patch apk
In this get flag section, I show the following method to patch code smali, because for me this is harder, until I write this tutorial, I will succeed: <
By this method, I did not change the flow of the decrypt to a flag, but only inserted 1 step in that process. The way to do this is to add an extra step for the application to display the result after decrypt, before the sg.vantagepoint.aaa () function returns the result of comparing the input with the flag.
Here is the smali return code, which compares the two strings:
1 2 3 4 5 6 7 8 9 10 11 12 | new-instance v1, Ljava/lang/String; invoke-direct {v1, v0}, Ljava/lang/String;-><init>([B)V # Chúng ta sẽ viết thêm code vào đây invoke-virtual {p0, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z # So sánh 2 string move-result p0 return p0 |
In order for the program to print a flag, I will add a command to print the log. Once the flag has been printed to the log, we can easily view it using adb logcat .
The structure of the print string command logs out with the smali code as follows:
1 2 | invoke-static {v0, v1}, Landroid/util/Log;->d(Ljava/lang/String;Ljava/lang/String;)I |
Where v0 and v1 variables are log-tag and log-message respectively . These two variables can be replaced by two other variables already declared by the program. I avoid declaring new variables in smali code because I do not know much about Dalvik opcode and the Android system.
In the above smali code, the v1 variable is the flag we are trying to get. I also do not know how to log-tag, so keep printing the flag / flag at all:
1 2 3 4 5 6 7 8 9 10 11 12 | new-instance v1, Ljava/lang/String; invoke-direct {v1, v0}, Ljava/lang/String;-><init>([B)V invoke-static {v1, v1}, Landroid/util/Log;->d(Ljava/lang/String;Ljava/lang/String;)I # patch here invoke-virtual {p0, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z move-result p0 return p0 |
The steps to build, sign apk and install are too basic, I will not write again. After installing and typing the input randomly to check, the flag has been printed in the log:
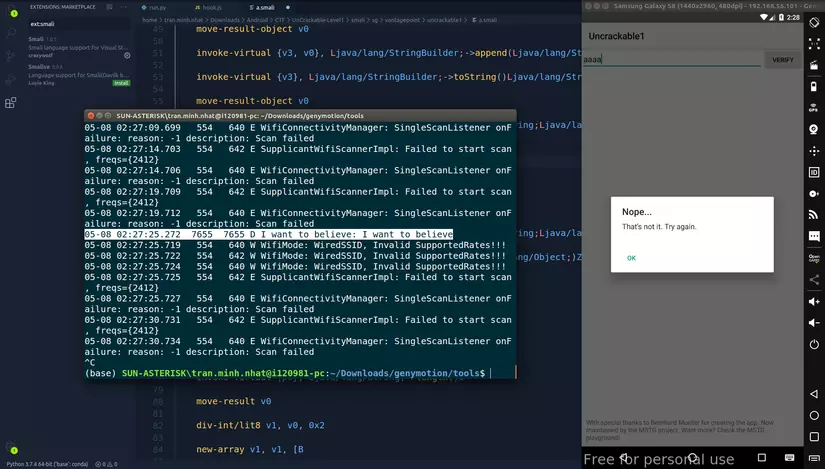
Edited smali code: a.smali
