Introduce
Most web applications today use redirect . If your site redirects to the same URL as the query string, you may be exposed to phishing attacks . I will give an example of how you are helping fraudsters via email 
How it works
Open redirect occurs when the application redirects the user to a URL provided by an untrusted source by not validating the URL. It is often used to phishing attacks – attacks with malicious links sent in emails in an attempt to trick users into accessing harmful sites. By sending a link pointing to your website but redirecting it to a malicious site, an attacker can circumvent phishing protection. This type of attack can affect the trust of users in your site since this vulnerability occurred.
And this is how it works …
The Mal guy from the series wants to try this vulnerability on your site, which is usually a useful feature, but your site does not check for redirected URLs. Vic is a normal user, Mal wants to trick Vic into accessing malicious websites. Mal invents a URL that redirects to his malicious site: www.example.com?next=http://www.haxxed.com . To make it more believable, he encodes the redirect parameter, and adds a few extra parameters to the query: www.example.com?_g=DernKFjelgnne&vid=iguana-party&referrer=email&next=http%3A%2F%2Fwww.haxxed.com . Mal sent a link to Vic via email. The link is your website and it is not black-listed as a malicious site by Vic ‘s email provider, so there will be no warning when the email is scanned.
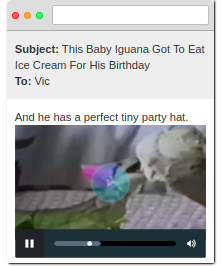
After clicking on the link, Vic is redirected to the login page because it is not already logged in to your website
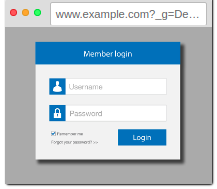
As soon as the login is successful, the redirect param is processed. The site did not check the URL with param next and Vic was redirected to a malicious site, he was phishinged .
If your site allows open redirect you could inadvertently help attackers to take advantage of your users.
Risky
This is a common error, easy to exploit and also worrying. Redirects are a useful function when building websites. If the user tries to access a resource before logging in, it will normally redirect them to the login page, replace it with the origin URL on the query param, and after the user successfully logs in, automatically switches direct them to the original path. This feature enhances the user experience, but you also need to make sure that it is redirected to be safe, otherwise you put the user in danger by allowing phishing attacks .
Current mail services do a great job at handling spam and malicious mail, their method is to analyze outbound links in html emails. These links are compared to a blacklist of banned domains, which will automatically move to the spam mailbox.
So this is the preferred hole for spammers and phishers .
prevent
- Do not allow redirecting to another page by checking the URL: All URLs must be relative (Note that URLs beginning with // will be interpreted by the browser as an unknown protocol, absolute URLs) – so they will be rejected as well). If you need to navigate to another page, list it on the
white list. - Check
Referrerwhen redirecting. - Check the code at the client
summary
Above is a brief introduction to Open redirect , hopefully useful for you. Happy coding! 
