1. Make a problem
When you first start analyzing a published vulnerability (1-day), one of the jobs that need to be done is to compare two versions of the same executable file to find the patched code. This requires retrieving the old version of the target file. There are different ways to do this:
- Install two updates (KBxxx) side by side, performing file extraction after each update:
This method is very simple, easy to understand, but has a big drawback: it takes a lot of time because the time to update Windows is quite long. - Download the necessary files from Microsoft through the winbinex tool:
This works for most files, but when Microsoft decides to revoke old versions of a file, we won’t be able to download it (for example, try downloading any entry in the file list). bootmgr.efi has been withdrawn by Microsoft following the appearance of the BlackLotus malware).
It can be seen that the above methods may be simple but not effective and comprehensive. In this article, we learn about the method to collect the files needed for analysis through manual extraction of patches for Windows operating system. Summary: We will simulate the Windows update process, but only on a specific file.
The main topics will be presented:
- About “patch tuesday” – when Microsoft updates its products
- About “cumulative update” – how Microsoft updates the Windows operating system
- Method to extract files before and after the update
- Method of comparing two versions of the same file – before and after update
This article is aimed at readers who are interested in vulnerability analysis of Windows OS and have background knowledge about software decompile.
2. About “patch tuesday” – the time when Microsoft updated Windows operating system
First of all, let’s talk quickly about the concept of “patch tuesday”. For those of you who don’t know: this phrase refers to the time when Microsoft releases patches for Windows operating system worldwide – on the second Tuesday of the month. On this day, hackers will focus on reviewing Microsoft patches, thereby analyzing vulnerable components and writing pocs. Readers can look to the reviews on ZDI for an overview of the newly discovered vulnerabilities. Example of the latest review – June 2023: https://www.zerodayinitiative.com/blog/2023/6/13/the-june-2023-security-update-review .
3. About “quality update” – how Microsoft is updating the Windows operating system
Previously, Microsoft provided three update methods for Windows operating systems:
- Full update: Download all files that have changed since the release of the version of Windows being installed on the system. This ensures that it is possible to update from every update to the latest update.
- Delta udpate: Download all files that need to be updated, replace files that need to be replaced from the previous update .
- Express update: Similar to full update, but requires the client to provide a list of files that need to be updated first, then download.
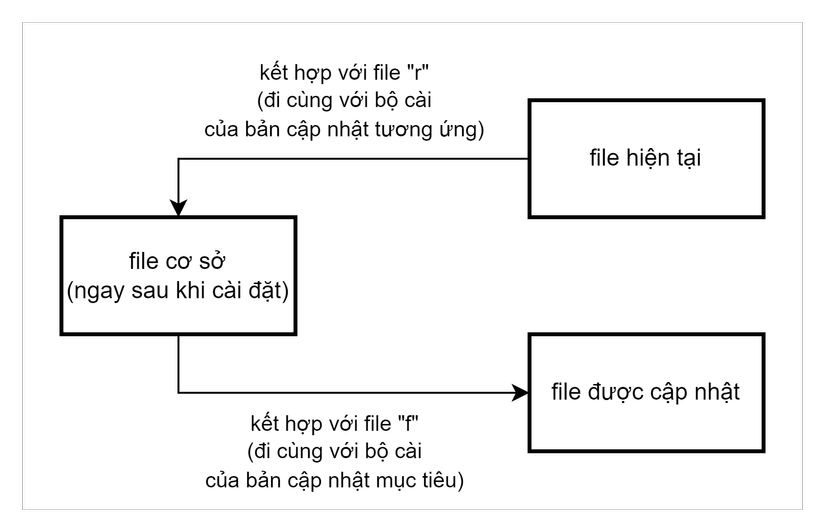
It can be seen that the common disadvantage of all three methods above is that they require a rather heavy download – 1GB. But from the beginning of 2019, Microsoft switched to using a new method called “quality update” . This method overcomes the oversized update packet size limitation of the old methods. The steps to take with each file to update include:
- Revert the current version of the file to be updated to the original version (the version immediately after installing Windows).
- Patch the original version created after step 1 to the latest version.
Illustration:
To download the installer, you need to first get the update code from Microsoft’s release note (for example, April 2023 is “KB5025221”), then download the installer from Microsoft Update Catalog
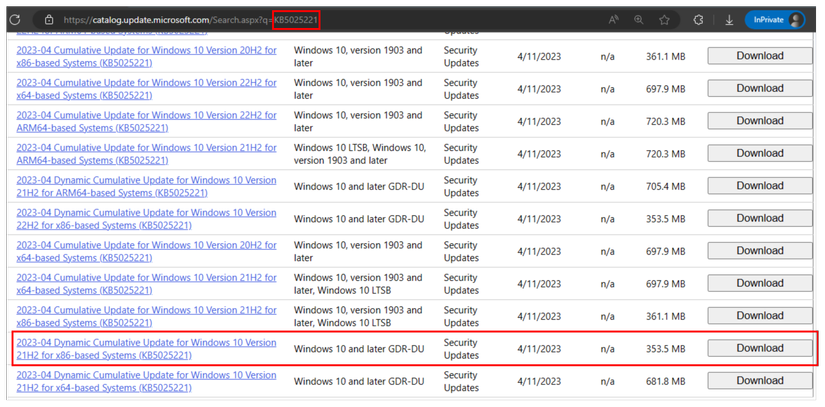
Description of the update directory for Microsoft:
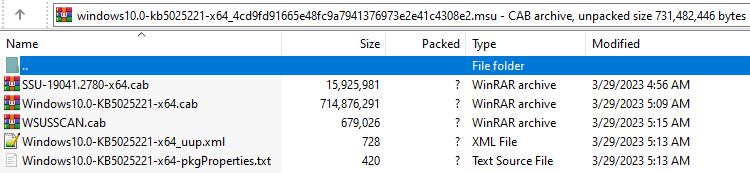
- Updates for Windows are distributed as MSU files. This file is actually a ZIP file. If you double click on this MSU file, Windows will extract the files inside and update all the files present in the updater. Inside this archive is the structure:

- There are key components in an update:
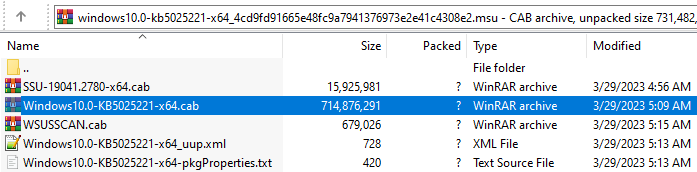
- Security update:

This is the component we are interested in. Extract this file until you get the following directory:

This is the directory of the Windows components that will be updated. - Update feature update:

We do not need to care about this component.
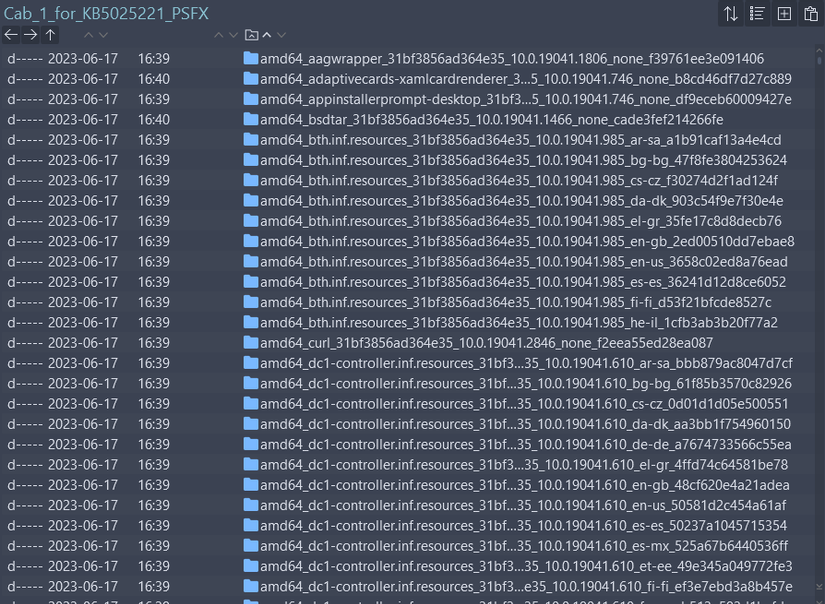
- Security update:
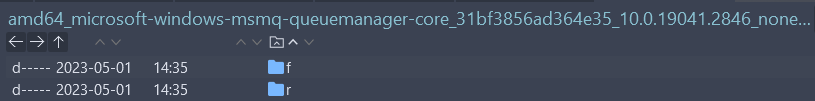
Each service that needs to be updated has a corresponding folder in the Cab_1_for_KB5025221_PSFX folder. In that folder there will be 2 smaller folders, named “f” and “r”. The “r” directory stands for “reverse” and contains files to combine with the updated file to create the original file. The “f” directory stands for “forward” and contains the forward file to combine with the original file to create the updated file. For example:
- In the folder containing the update of the
msmqservice in the April 2023 installation package:

- In each directory “f” and “r” there will be files to update:


4. Demo method of extracting files before and after the update
4.1. Steps to take
Our goal: Extract a specific file from the update. To select the target file, one can analyze the target software, list the binaries used, then search the update directory to see which files are in that list. In this article we will extract the mqqm.dll file that is used by the mqsvc process of the “Windows Message Queueing” service. The version prior to the April 2023 update of this program contained vulnerability CVE-2023-21554 with a CVSS score of 9.8.
From the explanation of how Microsoft updates the Windows operating system, we can figure out how to do it:
- Get the current version of the target file.
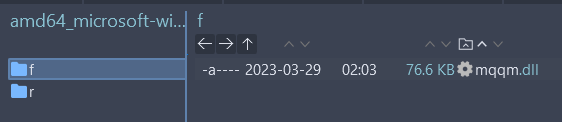
- Collect the
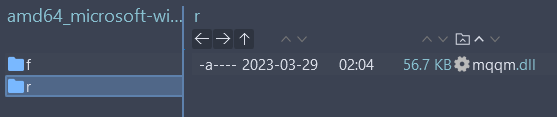
rfile corresponding to the current version of the target file. - Collect the
ffile corresponding to the target file from the update. - Recreate the base file.
- Create file after update.
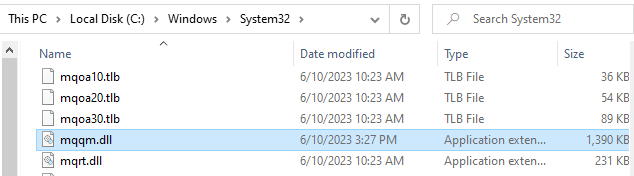
4.2. Get the current version of the target file
This step is quite simple. Just go to the current directory of the target file. In this case the path is C:WindowsSystem32 .
4.3. Collect r
The corresponding r file of the current version target file is located in two places:
- In the installer (MSU file) of the respective update.
- The folder
C:WindowsWinSxS.
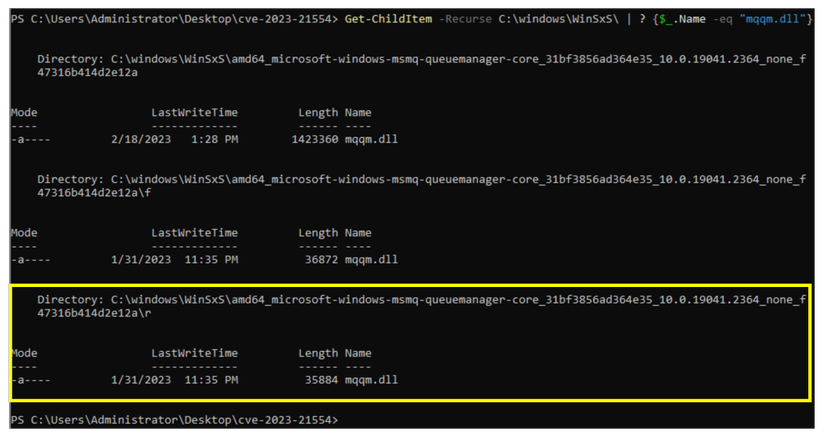
The fastest way is to get it from the folder C:WindowsWinSxS . Use the powershell command:
1 2 | Get-ChildItem -Recurse C:WindowsWinSxS | ? {$_.Name -eq "mqqm.dll"} |
Result:
If you want to collect from the current update, you need to know the update code. Run the systeminfo command on CMD to get the latest update code:
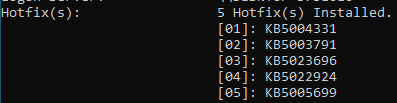
Then download the corresponding version from the Microsoft Catalog Update.
4.4. Collect files f
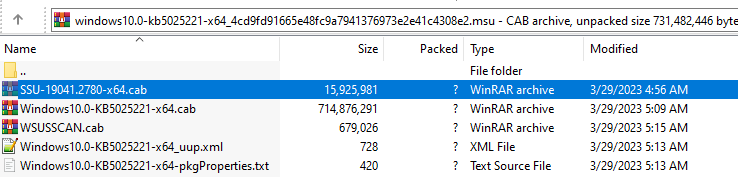
To get the file f , just find the target file name in the update installer directory:
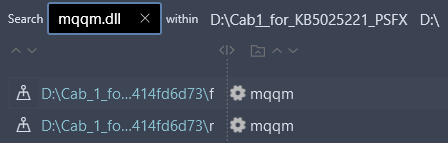
4.5. Create an updated file using files r and f
Now that we have enough materials, just assembling the components together will create the target file. There are two ways to do it:
- Write your own code using the library of win32. See instructions here .
- Use the patch_extract tool. Command:
python delta_patch.py -i <chosen_file> -o <output_file> <reverse_file_of_input_file> <forward_file_of_output_file>
The second way is more convenient and still works with the latest update for Windows so it should be preferred.
Result:
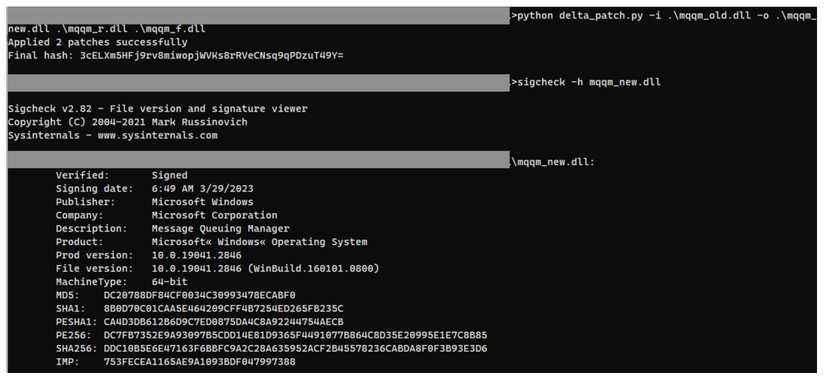
5. Compare two versions of the target file – before and after update
Diff two versions of mqqm.dll using the BinDiff tool in the IDA Pro environment:
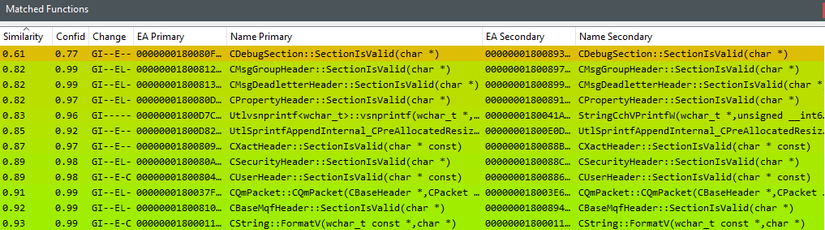
6. Summary
So we have successfully assembled the target file manually. This approach, although laborious, is guaranteed to be successful and can be performed automatically in large numbers. Our next step might be to automate the extraction of patched files and automate patch analysis using bindiff thereby focusing more on vulnerability analysis.
Readers, if you have any questions/suggestions, please leave a comment so we can discuss!
7. References
- https://wumb0.in/extracting-and-diffing-ms-patches-in-2020.html – One of the lecturers at SANS institute wrote about creating a patched file from an update.
- https://kienmanowar.wordpress.com/2019/10/07/reversing-with-ida-from-scratch-p22/ – article by expert Kien Manowar on how to use diffing tools.
- https://www.coresecurity.com/core-labs/articles/how-deal-microsoft-monthly-updates-reverse-engineering-binary-patches – expert Ricardo Narvaja shows how
- https://learn.microsoft.com/en-us/windows/deployment/update/psfxwhitepaper – Official Microsoft documentation on the update implementation process.
- https://devblogs.microsoft.com/oldnewthing/20200210-00/?p=103426 – expert Raymond Chen explains the patch distribution method for Windows.
- https://cve-north-stars.github.io/docs/Security-Patches – part of “CVE-north-star”, a pretty rewarding free course on the topic of one-day analytics.
- https://www.youtube.com/watch?v=p9Ls9rOEgBk&ab_channel=BSidesCharm – Stephen Sims – one of the lecturers at SANS institute presented on the topic of patch analysis.