Introductory security series – CSRF – Spectacular tricks
In the Three Kingdoms, talented martial arts masters who commanded control, sat in the position to win thousands of miles away.
In Tu Chan, the players have the technique of "How Not to Wrestle" to control objects from afar, or "Astronaut Sword", using air legs to manipulate non-swords or statutory.
Today, hackers have similar "tactics" called CRSF. Hackers can sit at website A to entice users to attack site B and other C sites.
This article will explain how hackers attack, and guide how to prevent you from programming.
Basic about CSRF
CSRF has a full name, Cross Site Request Forgery (Another name is XSRF). The flaw is quite common, Netflix and Youtube have also been victims of the vulnerability.
The consequences of it are also "slightly" serious so CRSF is pleased to be in the top 10 of OWASP's security holes.
The operation principle of CRSF is very simple. In the previous article, we know that the server will store user cookies to distinguish users. Each time a user sends a request to a domain, the cookie is sent .
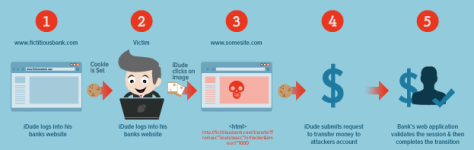
- First, the user must log into the page he needs (temporarily called page A).
- To seduce users, hackers will create a malicious website.
- When the user accesses this unique web, a request will be sent to page A that the hacker wants to attack (via form, img, …).
- Since this request has a user's cookie attached, the destination A website will mistakenly assume that this is a user-made request .
- Hackers can impersonate users to do actions such as changing passwords, transferring money, etc.
To make it easier to understand, please read the example below.
Common types of attacks
Type 1. Use the form
Once upon a time, there were two brothers who were called Tung and Toong. Tung, his brother, taking care of his education, and his animal friends and his wife. My younger brother, Toong, came back all day and went to heaven and earth and found a massage place.
One day, quarreling with his wife, sadness wanted to leave the massage. Unfortunately, asking for the address is no one asked because the credit is too low.
Knowing Toong is a member of a staff, he begs to let him borrow acc but lest he be spoiled, so he won't let him. What a good brother !! Religion, Tung decided to use CSRF bug to steal the account of Tuong.
Let's look at the HTML of the heavenly password change form. This form includes 2 fields as password and password_confirm , submit to http://thiendia.com/account/security-save
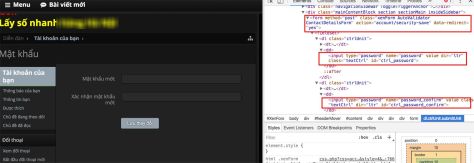
Pretend to fake a JAV site, pretending to send a bad brother. There is a hidden form on the web page with the same values as the above form (Please note the HTML form on the left and the right button).

Young people blindly blind IT, accidentally entered the link and clicked on the button. A request to change the password is sent to thiendia, along with the cookie account of the Wall.
It's done! We just need to use the new email + password 123456 to log in to the bad brother's account.

Type 2. Use img tag
The story is not over yet. There is a massage place, but the money is held by his wife, Tung has no money to go for a massage. Decided to hack Tuong's bank account .
Use JAVBank (Japan America Vietnam Bank). Each bank transfer, the bank will create a URL. Assuming that person A wants to transfer 1000 to B, the created url will be in the form of http://jav.bank?from=Person1&to=Person2&amount=1000 .
Leave this url in 1 img tag. When Wall access the page, the browser will call GET request, attached to the cookie on JAVBank of the Wall. Through cookies, the bank confirms that it is the Wall , transferring money to Tong .
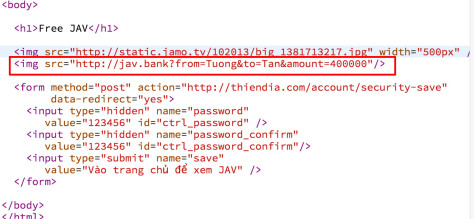
Having money has a place, Lie to his wife on the way to massage. The following story has 18+ content, so I don't know anymore ….
Note
Of course, in the post is just an example. In principle, GET requests are only used to access data , not to perform data change operations such as edit / delete.
Banks often protect very carefully by setting cookies with a short life time, not allowing money transfer without OTP code, etc.
In addition, thiendia also has good security measures (see below) so you don't use this method to steal your friends' account, don't try!
However, in the old days, when security holes were not popular, this is exactly how hackers use. Just post a photo with the same link on a forum, there will be countless people trapped when visiting that forum.
Prevention for website
Here are some basic ways to prevent CSRF:
- Using CSRF Token : In each form or request, we attach a CSRF token. This token is created based on the user's session. When sending to the server, we check the authenticity of this session. Since this token is randomly generated based on the session , the hacker cannot fake it (frameworks like RoR, CodeIgniter, ASP.NET MVC support CSRF token).
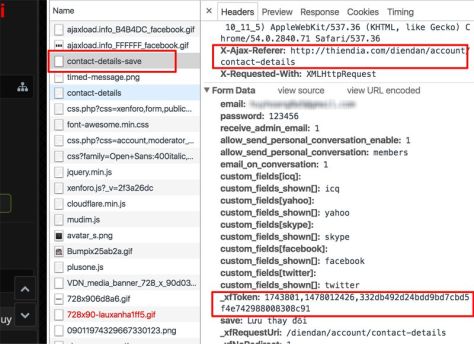
Artwork from heaven, this page has CSRF token
- Check the Referer and Origin values in the header: Origin tells us the site called this request. This value is attached to each request, the hacker cannot edit it. Check this value, if it is a strange page, do not process the request.
- Check the X-Requested-With- header header: The request contains this header as a safe request, because this header prevents us from sending requests to another domain ( details ).
- Be careful to prevent XSS errors: With XSS, hackers can install malicious code on the site that needs to attack. At this point, all methods of preventing CSRF such as tokens and referrers are disabled . Juno_okyo uncle used to apply a CSRF combined CSS error to attack the server ( Details ).
Conclusion
Days before this error are quite serious and common. Recently frameworks are almost defaults to this error, so the frequency of meeting is less. However, we still have to take precautions, especially the website code itself (especially code in PHP, ahihi).
In addition, as a user, you need to know how to protect yourself in the following ways:
- Log out of your account after use to avoid storing cookies.
- Do not click ads or buttons.
- Don't visit dangerous, dangerous pages. As mentioned above, many times when we do not press any button, just access the page, the browser automatically posts based on javascript or img tag.
Source for further reference:
- https://en.wikipedia.org/wiki/Cross-site_request_forgery
- https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
- http://stackoverflow.com/questions/17478731/whats-the-point-of-the-x-requested-with-header
- https://www.youtube.com/watch?v=m0EHlfTgGUU
- I want to post more heavenly links, but I think everyone knows it, so that's it
Other articles belong to the introductory security series
_ Series introduction security – SQL injection – God security vulnerability
_ Series security introduction – how dangerous is the xss security hole?
_ Series security introduction – Archive cookies – pity anyone who thinks unbelievably
_ Series security introduction – How "HTTP SECURITY" HTTP protocol
_ Introduction security series – Basic security for developers
ITZone via toidicodedao
