
XSS is a common bug in Web applications. So in this article we will learn how to find XSS errors using Burp suite tool in combination with PhantomJS.
Supplementary knowledge
Before going into details of using tools to find XSS errors, we need to clarify two things:
- What is XSS error?
- What is PhantomJS
What is PhantomJS?
PhantomJS is no longer under development.
This article will not talk about PhantomJS in detail, so to understand it, PhantomJS is like our browser. Of particular importance is that PhantomJS is used via the command line and we program it to be able to interact with HTTP / S requests and responses.
To get a better look at PhantomJS or what is PhantomJS? . Or read in English on the PhantomJS wiki.
Install the tool
1. Install the XSS Validator extension
If you don’t have a Burp suite yet, follow the instructions at home: https://portswigger.net/support/getting-started-with-burp-suite
After installing Burp, continue to install the extension XSS validator . Open BApp Sotre : Extender -> BApp Store
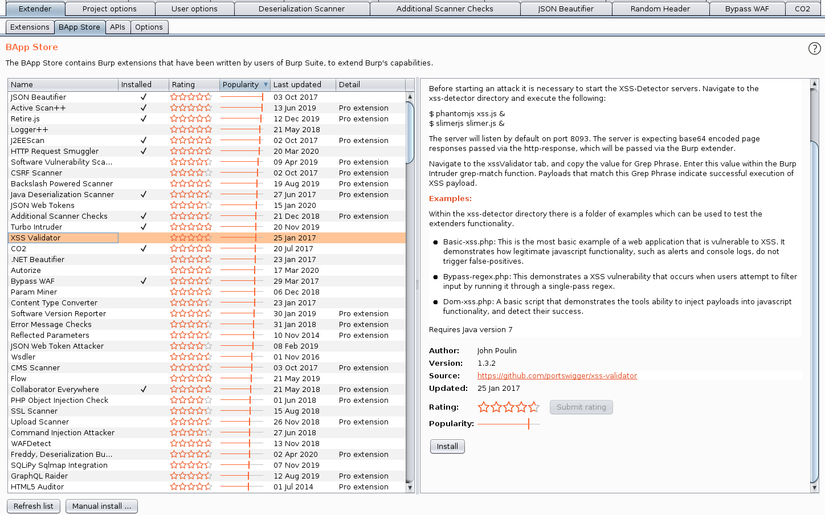
The results are shown as in the picture, to install XSS validator we choose Install . So complete the first step!
2. Install PhantomJS
To download and install PhantomJS at the following address https://phantomjs.org/download.html
PhantomJS supports the following platforms: Windows, macOS, Linux, and FreeBSD.
If the computer you are using is Linux, you can quickly install it using the command
1 2 | <span class="token function">sudo</span> apt <span class="token function">install</span> -y phantomjs |
3. Download the file server running for PhantomJS
Use the following command to clone repo xssvalidator about
1 2 | <span class="token function">git</span> clone https://github.com/nVisium/xssValidator.git |
Demo
In this section assume we already know the basic use of Burp suite.
First we have to run the xss server.
1 2 3 4 | <span class="token function">cd</span> xssValidator/ <span class="token function">cd</span> xss-detector/ phantomjs xss.js |
In the next step, we run Burp suite and switch intercept to off mode.
Next we go to the page that contains the suspect XSS link. As in the example here, we use portswigger’s XSS lab.
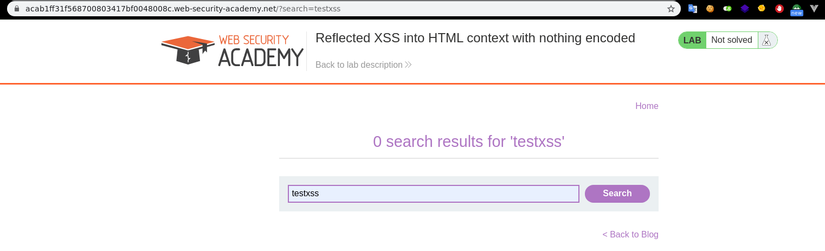
We proceed to fill and send, then into the HTTP history of the burp and view the request information. 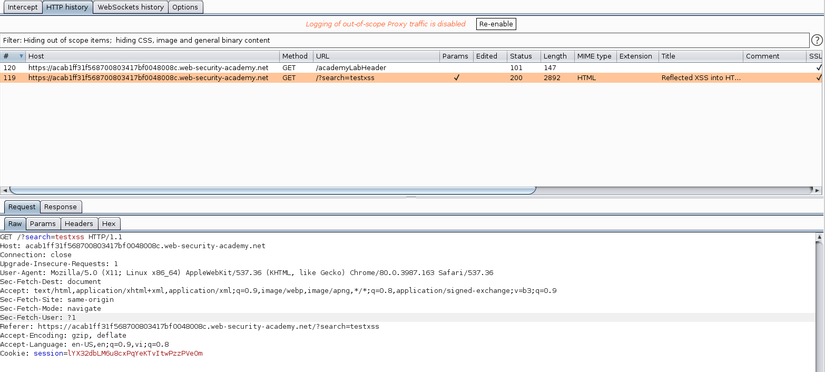
Send a request containing an XSS questionable link to Burp’s Intruder page by pressing Ctrl + R. Edit only 1 payload is the search on the url.
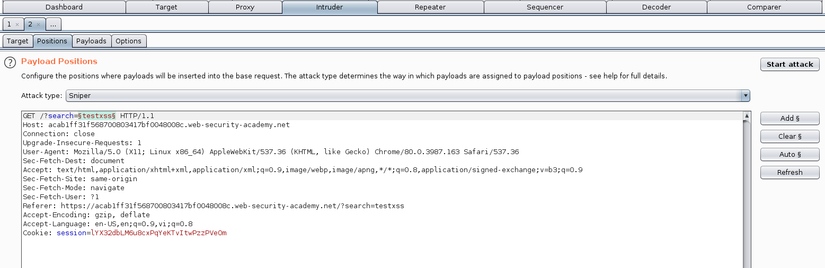
Next, we proceed to configure the XSS payload . In the Payloads tab, we change the Payload type to Extension-generated
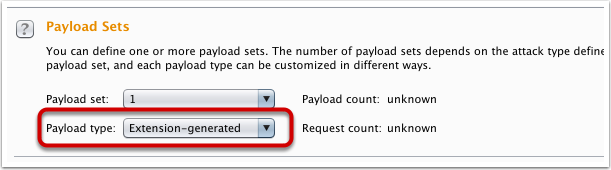
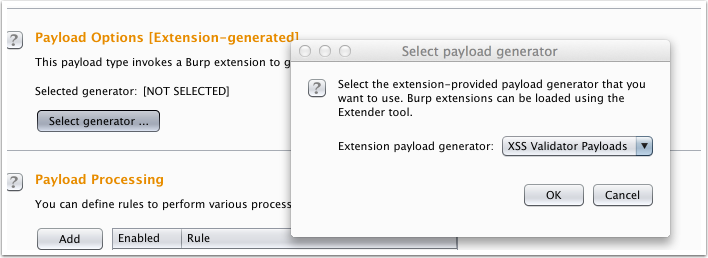
Edit Payload Options, select Select generator … and select XSS validator Payloads.
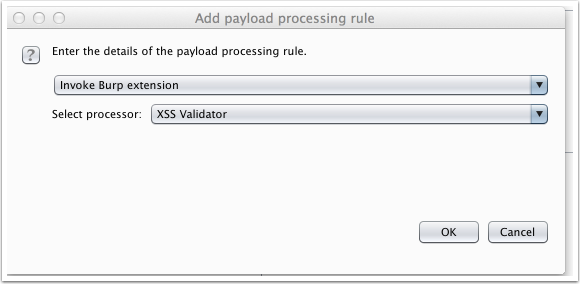
Edit the Payload Processing section, Select Add -> Invoke Burp extension -> XSS Validator.
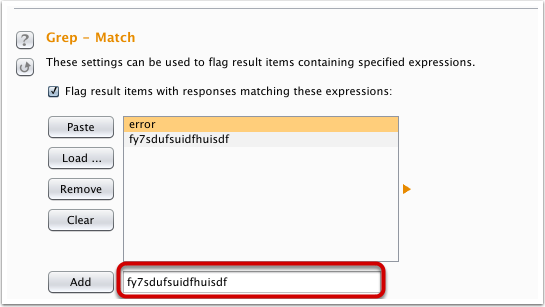
In the Options section, we use the Grep-Math section to burp the active payloads from which we will know if the link is XSS or not. First clear all content, and add the following value: fy7sdufsuidfhuisdf
Finally click Start to start the attack and check the results. If there is an area like the image below, the link has an XSS error.
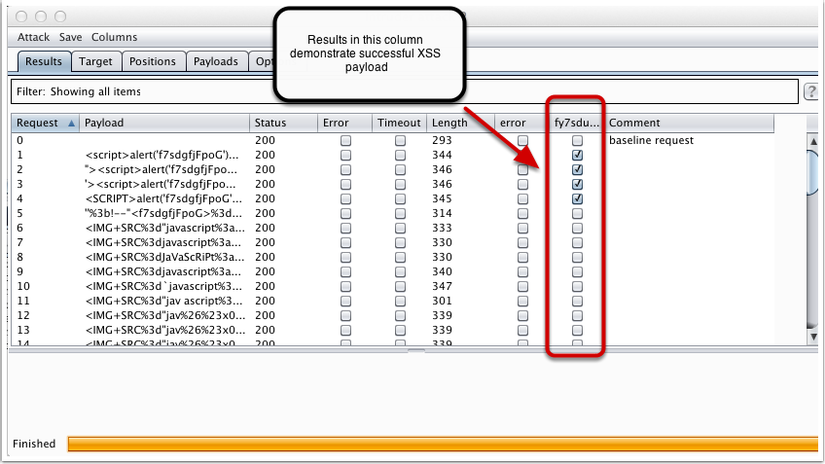
So our understanding is the end!
