Next in Part 1 we will learn about the remaining methods of protecting personal data in the process of building Android applications:
- Anti screenshot
- Encrypt personal data
- Protect the source code of the application
- Install biometric protection
Anti screenshot
When we made sure that all log information was not printed when running the application, the cache was deleted when the application exited. But it can still be easy for users to take screenshots related to our application, which can lead to copyright violations. For example, when reading a copyrighted comic, users need to confirm the information before they can open the reading, but here users can still take screenshots of each page and save it. To prevent this, we have an effective way to combat screenshots. We can add the following code to the onCreate () function in the application’s Activity
1 2 | window <span class="token punctuation">.</span> <span class="token function">setFlags</span> <span class="token punctuation">(</span> WindowManager <span class="token punctuation">.</span> LayoutParams <span class="token punctuation">.</span> FLAG_SECURE <span class="token punctuation">,</span> WindowManager <span class="token punctuation">.</span> LayoutParams <span class="token punctuation">.</span> FLAG_SECURE <span class="token punctuation">)</span> |
The above code will notify the system that our application window has FLAG_SECURE , which will prevent screen capture whether intentionally or unintentionally.
When building and running the application on the real machine, at the program window we try to take a screenshot to see a Toast message with the content “Couldn’t capture screenshot” or “Can’t take screenshot due to security policy, “ or a Toast with similar content.
Encrypt personal data
With important personal information when stored, or report files, information of the application is sent to the server we should choose to encrypt its information before being saved to the device memory. or sent.
To do this we can use a fairly powerful and popular algorithm in the community, AES (Advanced Encryption Standard). This algorithm has many different encryption modes: ECB, CBC, CFB, OFB, CTR in which CBC (Cipher Block Channing) is a good security mode and is also quite easy to use.
Here is how to use this algorithm in the application, first we declare the algorithm to use, encryption mode, Padding type is the type.
1 2 3 4 5 6 7 8 9 10 11 12 | <span class="token keyword">private</span> <span class="token keyword">const</span> <span class="token keyword">val</span> MODE <span class="token operator">=</span> <span class="token string">"AES/CBC/PKCS5Padding"</span> <span class="token keyword">private</span> <span class="token keyword">const</span> <span class="token keyword">val</span> ALGORITHM <span class="token operator">=</span> <span class="token string">"AES"</span> <span class="token keyword">private</span> <span class="token keyword">fun</span> <span class="token function">cipher</span> <span class="token punctuation">(</span> opMode <span class="token operator">:</span> Int <span class="token punctuation">,</span> secretKey <span class="token operator">:</span> String <span class="token punctuation">)</span> <span class="token operator">:</span> Cipher <span class="token punctuation">{</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> secretKey <span class="token punctuation">.</span> length <span class="token operator">!=</span> <span class="token number">32</span> <span class="token punctuation">)</span> <span class="token keyword">throw</span> <span class="token function">RuntimeException</span> <span class="token punctuation">(</span> <span class="token string">"SecretKey length is not 32 chars"</span> <span class="token punctuation">)</span> <span class="token keyword">val</span> c <span class="token operator">=</span> Cipher <span class="token punctuation">.</span> <span class="token function">getInstance</span> <span class="token punctuation">(</span> MODE <span class="token punctuation">)</span> <span class="token keyword">val</span> sk <span class="token operator">=</span> <span class="token function">SecretKeySpec</span> <span class="token punctuation">(</span> secretKey <span class="token punctuation">.</span> <span class="token function">toByteArray</span> <span class="token punctuation">(</span> Charsets <span class="token punctuation">.</span> UTF_8 <span class="token punctuation">)</span> <span class="token punctuation">,</span> ALGORITHM <span class="token punctuation">)</span> <span class="token keyword">val</span> iv <span class="token operator">=</span> <span class="token function">IvParameterSpec</span> <span class="token punctuation">(</span> secretKey <span class="token punctuation">.</span> <span class="token function">substring</span> <span class="token punctuation">(</span> <span class="token number">0</span> <span class="token punctuation">,</span> <span class="token number">16</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">toByteArray</span> <span class="token punctuation">(</span> Charsets <span class="token punctuation">.</span> UTF_8 <span class="token punctuation">)</span> <span class="token punctuation">)</span> c <span class="token punctuation">.</span> <span class="token function">init</span> <span class="token punctuation">(</span> opMode <span class="token punctuation">,</span> sk <span class="token punctuation">,</span> iv <span class="token punctuation">)</span> <span class="token keyword">return</span> c <span class="token punctuation">}</span> |
In the above code we use the AES algorithm to encrypt, the encryption mode is CBC , the Padding type is ” PKCS5Padding “. The “cipher” function takes two parameters:
- opMode: the mode is encoding or decoding
- secretKey: key used for encryption as well as decryption, this key must be used consistently in both cases of encryption and decryption, otherwise it will not decode the encrypted information.
Next we create two encrypt functions to encrypt and decrypt to decode as shown below
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 | <span class="token keyword">fun</span> <span class="token function">encrypt</span> <span class="token punctuation">(</span> strToEncrypt <span class="token operator">:</span> String <span class="token punctuation">,</span> secretKey <span class="token operator">:</span> String <span class="token operator">=</span> BuildConfig <span class="token punctuation">.</span> AES_SECRET_KEY <span class="token punctuation">)</span> <span class="token operator">:</span> String <span class="token operator">?</span> <span class="token punctuation">{</span> <span class="token keyword">try</span> <span class="token punctuation">{</span> <span class="token keyword">val</span> encrypted <span class="token operator">=</span> <span class="token function">cipher</span> <span class="token punctuation">(</span> Cipher <span class="token punctuation">.</span> ENCRYPT_MODE <span class="token punctuation">,</span> secretKey <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">doFinal</span> <span class="token punctuation">(</span> strToEncrypt <span class="token punctuation">.</span> <span class="token function">toByteArray</span> <span class="token punctuation">(</span> Charsets <span class="token punctuation">.</span> UTF_8 <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token keyword">return</span> <span class="token function">String</span> <span class="token punctuation">(</span> Base64 <span class="token punctuation">.</span> <span class="token function">encode</span> <span class="token punctuation">(</span> encrypted <span class="token punctuation">,</span> Base64 <span class="token punctuation">.</span> DEFAULT <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token keyword">catch</span> <span class="token punctuation">(</span> e <span class="token operator">:</span> Exception <span class="token punctuation">)</span> <span class="token punctuation">{</span> Timber <span class="token punctuation">.</span> <span class="token function">e</span> <span class="token punctuation">(</span> e <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token keyword">return</span> <span class="token keyword">null</span> <span class="token punctuation">}</span> <span class="token keyword">fun</span> <span class="token function">decrypt</span> <span class="token punctuation">(</span> strToDecrypt <span class="token operator">:</span> String <span class="token operator">?</span> <span class="token punctuation">,</span> secretKey <span class="token operator">:</span> String <span class="token operator">=</span> BuildConfig <span class="token punctuation">.</span> AES_SECRET_KEY <span class="token punctuation">)</span> <span class="token operator">:</span> String <span class="token operator">?</span> <span class="token punctuation">{</span> <span class="token keyword">try</span> <span class="token punctuation">{</span> <span class="token keyword">val</span> byteStr <span class="token operator">=</span> Base64 <span class="token punctuation">.</span> <span class="token function">decode</span> <span class="token punctuation">(</span> strToDecrypt <span class="token operator">?</span> <span class="token punctuation">.</span> <span class="token function">toByteArray</span> <span class="token punctuation">(</span> Charsets <span class="token punctuation">.</span> UTF_8 <span class="token punctuation">)</span> <span class="token punctuation">,</span> Base64 <span class="token punctuation">.</span> DEFAULT <span class="token punctuation">)</span> <span class="token keyword">val</span> decrypted <span class="token operator">=</span> <span class="token function">String</span> <span class="token punctuation">(</span> <span class="token function">cipher</span> <span class="token punctuation">(</span> Cipher <span class="token punctuation">.</span> DECRYPT_MODE <span class="token punctuation">,</span> secretKey <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">doFinal</span> <span class="token punctuation">(</span> byteStr <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token keyword">return</span> decrypted <span class="token punctuation">}</span> <span class="token keyword">catch</span> <span class="token punctuation">(</span> e <span class="token operator">:</span> Exception <span class="token punctuation">)</span> <span class="token punctuation">{</span> Timber <span class="token punctuation">.</span> <span class="token function">e</span> <span class="token punctuation">(</span> e <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token keyword">return</span> <span class="token keyword">null</span> <span class="token punctuation">}</span> |
- Encrypt function: get an encrypted string and key
- Decrypt function: get encrypted string and key to decode
To encode a sequence of information in an application, we simply call the following:
1 2 | <span class="token keyword">val</span> textEncrypt <span class="token operator">=</span> <span class="token function">encrypt</span> <span class="token punctuation">(</span> <span class="token string">"String for encrypt"</span> <span class="token punctuation">,</span> <span class="token string">"password"</span> <span class="token punctuation">)</span> |
With the decode simply call the following
1 2 | <span class="token keyword">val</span> textDecrypt <span class="token operator">=</span> <span class="token function">decrypt</span> <span class="token punctuation">(</span> textEncrypt <span class="token punctuation">,</span> <span class="token string">"password"</span> <span class="token punctuation">)</span> |
We can see the encryption is quite simple, but it will help our information more secure, avoiding unauthorized access to information.
Protect the source code of the application
When building an application into an APK file for release , the source code for the application will be packaged in the classes.dex file. This leads to the fact that if our application is distributed to users, it is likely that the source code of the application will be easily stolen or reused for other purposes. This is very dangerous and can lead to serious problems when the application is commercial products, related to user information, credit cards, bank accounts …
In order to limit the disclosure of source code, we can use an available method, ProGuard . This is a tool for optimizing Java bytecode code, it helps Java and Android applications significantly reduce the size when it is possible to remove unnecessary variables and functions in the application. ProGuard is advertised to reduce the size of the application to 90% and operate 20% faster, but its useful function is also in the ability to minimize the ” reverse ” of the source code when it can. Tampering with class names, variables and functions, it is difficult to read and translate.
To accomplish this we need to pay attention to the following 2 files:
- Application build.gradle file: to declare the use of proguard in any build debug or release, source code protection methods.
- File proguard-rules.pro : declare functions, classes do not need ProGuard because it is related to the 3rd application, or the application’s input if ProGuard, the file or class name will not find the right name and application could not start.
First we need to determine which Proguard is included in the build of the debug or release application, and usually Proguard only works for the release because it is now complete and ready to distribute to users. is the declaration for enabling ProGuard for the build release from file build.gradle
1 2 3 4 5 6 7 8 9 10 11 12 13 | android <span class="token punctuation">{</span> buildTypes <span class="token punctuation">{</span> debug <span class="token punctuation">{</span> testCoverageEnabled <span class="token operator">!</span> project <span class="token punctuation">.</span> <span class="token function">hasProperty</span> <span class="token punctuation">(</span> <span class="token string">'android.injected.invoked.from.ide'</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> release <span class="token punctuation">{</span> shrinkResources <span class="token boolean">true</span> minifyEnabled <span class="token boolean">true</span> proguardFiles <span class="token function">getDefaultProguardFile</span> <span class="token punctuation">(</span> <span class="token string">'proguard-android.txt'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'proguard-rules.pro'</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> |
With the above declaration we can see
- minifyEnabled: used to activate ProGuard, remove unused code, rename classes, variables and functions when building
- shrinkResources: used to eliminate unused resources when building
- proguardFiles: to declare a list of classes, variables, functions and libraries that do not need ProGuard
Next, we will report when the classes, functions, libraries we should ignore need not ProGuard to ensure the program can work properly. Below is a sample file for bypassing ProGuard with libraries outside our application scope
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 | # Add project specific ProGuard rules here <span class="token punctuation">.</span> # You can control the set of applied configuration files using the # proguardFiles setting in build <span class="token punctuation">.</span> gradle <span class="token punctuation">.</span> # # For more details <span class="token punctuation">,</span> see # http <span class="token operator">:</span> <span class="token operator">/</span> <span class="token operator">/</span> developer <span class="token punctuation">.</span> android <span class="token punctuation">.</span> com <span class="token operator">/</span> guide <span class="token operator">/</span> developing <span class="token operator">/</span> tools <span class="token operator">/</span> proguard <span class="token punctuation">.</span> html # If your project uses WebView with JS <span class="token punctuation">,</span> uncomment the following # and specify the fully qualified <span class="token keyword">class</span> <span class="token class-name">name</span> to the JavaScript <span class="token keyword">interface</span> # <span class="token keyword">class</span> <span class="token operator">:</span> # <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">fqcn <span class="token punctuation">.</span> of <span class="token punctuation">.</span> javascript <span class="token punctuation">.</span> interface <span class="token punctuation">.</span> for <span class="token punctuation">.</span> webview</span> <span class="token punctuation">{</span> # <span class="token keyword">public</span> <span class="token operator">*</span> <span class="token punctuation">;</span> # <span class="token punctuation">}</span> # Uncomment <span class="token keyword">this</span> to preserve the line number information <span class="token keyword">for</span> # debugging stack traces <span class="token punctuation">.</span> # <span class="token operator">-</span> keepattributes SourceFile <span class="token punctuation">,</span> LineNumberTable # If you keep the line number information <span class="token punctuation">,</span> uncomment <span class="token keyword">this</span> to # hide the original source file name <span class="token punctuation">.</span> # <span class="token operator">-</span> renamesourcefileattribute SourceFile # Support libs <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> v4 <span class="token punctuation">.</span> app <span class="token punctuation">.</span> Fragment</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> ViewModel</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> os <span class="token punctuation">.</span> Parcelable</span> <span class="token punctuation">{</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> CREATOR <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> v7 <span class="token punctuation">.</span> widget <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">interface</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> v7 <span class="token punctuation">.</span> widget <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> v4 <span class="token punctuation">.</span> app <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">interface</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> v4 <span class="token punctuation">.</span> app <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> test <span class="token punctuation">.</span> espresso <span class="token punctuation">.</span> IdlingResource</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> test <span class="token punctuation">.</span> espresso <span class="token punctuation">.</span> IdlingRegistry</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> common <span class="token punctuation">.</span> base <span class="token punctuation">.</span> Preconditions</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> * <span class="token operator">*</span> # Guava <span class="token operator">-</span> dontwarn javax <span class="token punctuation">.</span> annotation <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn javax <span class="token punctuation">.</span> inject <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn sun <span class="token punctuation">.</span> misc <span class="token punctuation">.</span> Unsafe # Test <span class="token operator">-</span> ignorewarnings <span class="token operator">-</span> dontnote junit <span class="token punctuation">.</span> framework <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontnote junit <span class="token punctuation">.</span> runner <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn android <span class="token punctuation">.</span> test <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn android <span class="token punctuation">.</span> support <span class="token punctuation">.</span> test <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn org <span class="token punctuation">.</span> junit <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn org <span class="token punctuation">.</span> hamcrest <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn com <span class="token punctuation">.</span> squareup <span class="token punctuation">.</span> javawriter <span class="token punctuation">.</span> JavaWriter <span class="token operator">-</span> dontwarn org <span class="token punctuation">.</span> mockito <span class="token punctuation">.</span> * <span class="token operator">*</span> # Retrofit <span class="token operator">-</span> keepattributes Signature <span class="token punctuation">,</span> InnerClasses <span class="token punctuation">,</span> EnclosingMethod <span class="token operator">-</span> keepclassmembers <span class="token punctuation">,</span> allowshrinking <span class="token punctuation">,</span> allowobfuscation <span class="token keyword">interface</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token annotation punctuation">@retrofit2</span> <span class="token punctuation">.</span> http <span class="token punctuation">.</span> * <span class="token generics function"><span class="token punctuation"><</span> methods <span class="token punctuation">></span></span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn org <span class="token punctuation">.</span> codehaus <span class="token punctuation">.</span> mojo <span class="token punctuation">.</span> animal_sniffer <span class="token punctuation">.</span> IgnoreJRERequirement <span class="token operator">-</span> dontwarn javax <span class="token punctuation">.</span> annotation <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn kotlin <span class="token punctuation">.</span> Unit <span class="token operator">-</span> dontwarn retrofit2 <span class="token punctuation">.</span> -KotlinExtensions # Glide <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">com <span class="token punctuation">.</span> bumptech <span class="token punctuation">.</span> glide <span class="token punctuation">.</span> module <span class="token punctuation">.</span> GlideModule</span> <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">com <span class="token punctuation">.</span> bumptech <span class="token punctuation">.</span> glide <span class="token punctuation">.</span> module <span class="token punctuation">.</span> AppGlideModule</span> <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">enum</span> com <span class="token punctuation">.</span> bumptech <span class="token punctuation">.</span> glide <span class="token punctuation">.</span> load <span class="token punctuation">.</span> ImageHeaderParser$ <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> $VALUES <span class="token punctuation">;</span> <span class="token keyword">public</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # RxJava <span class="token operator">&</span> RxAndroid <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> schedulers <span class="token punctuation">.</span> Schedulers</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token generics function"><span class="token punctuation"><</span> methods <span class="token punctuation">></span></span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> schedulers <span class="token punctuation">.</span> ImmediateScheduler</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token generics function"><span class="token punctuation"><</span> methods <span class="token punctuation">></span></span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> schedulers <span class="token punctuation">.</span> TestScheduler</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token generics function"><span class="token punctuation"><</span> methods <span class="token punctuation">></span></span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> schedulers <span class="token punctuation">.</span> Schedulers</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">test</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> internal <span class="token punctuation">.</span> util <span class="token punctuation">.</span> unsafe <span class="token punctuation">.</span></span> <span class="token operator">*</span> ArrayQueue <span class="token operator">*</span> Field <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token keyword">long</span> producerIndex <span class="token punctuation">;</span> <span class="token keyword">long</span> consumerIndex <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">rx <span class="token punctuation">.</span> internal <span class="token punctuation">.</span> util <span class="token punctuation">.</span> unsafe <span class="token punctuation">.</span> BaseLinkedQueueProducerNodeRef</span> <span class="token punctuation">{</span> <span class="token keyword">long</span> producerNode <span class="token punctuation">;</span> <span class="token keyword">long</span> consumerNode <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">io <span class="token punctuation">.</span> reactivex <span class="token punctuation">.</span> observers <span class="token punctuation">.</span> DisposableObserver</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Google Play Service <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> android <span class="token punctuation">.</span> gms <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> android <span class="token punctuation">.</span> gms <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">java <span class="token punctuation">.</span> util <span class="token punctuation">.</span> ListResourceBundle</span> <span class="token punctuation">{</span> <span class="token keyword">protected</span> Object <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token function">getContents</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> android <span class="token punctuation">.</span> gms <span class="token punctuation">.</span> common <span class="token punctuation">.</span> internal <span class="token punctuation">.</span> safeparcel <span class="token punctuation">.</span> SafeParcelable</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token keyword">final</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token operator">*</span> NULL <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepnames <span class="token annotation punctuation">@com</span> <span class="token punctuation">.</span> google <span class="token punctuation">.</span> android <span class="token punctuation">.</span> gms <span class="token punctuation">.</span> common <span class="token punctuation">.</span> annotation <span class="token punctuation">.</span> KeepName <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token operator">-</span> keepclassmembernames <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token annotation punctuation">@com</span> <span class="token punctuation">.</span> google <span class="token punctuation">.</span> android <span class="token punctuation">.</span> gms <span class="token punctuation">.</span> common <span class="token punctuation">.</span> annotation <span class="token punctuation">.</span> KeepName <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Gson <span class="token operator">-</span> keepattributes Signature <span class="token operator">-</span> keepattributes <span class="token operator">*</span> Annotation <span class="token operator">*</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">sun <span class="token punctuation">.</span> misc <span class="token punctuation">.</span> Unsafe</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn sun <span class="token punctuation">.</span> misc <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> gson <span class="token punctuation">.</span> examples <span class="token punctuation">.</span> android <span class="token punctuation">.</span> model <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> gson <span class="token punctuation">.</span> TypeAdapterFactory</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> gson <span class="token punctuation">.</span> JsonSerializer</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> gson <span class="token punctuation">.</span> JsonDeserializer</span> # OkHttp3 <span class="token operator">-</span> keepattributes Signature <span class="token operator">-</span> keepattributes <span class="token operator">*</span> Annotation <span class="token operator">*</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">okhttp3 <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">interface</span> <span class="token class-name">okhttp3 <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn okhttp3 <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontnote okhttp3 <span class="token punctuation">.</span> * <span class="token operator">*</span> # Okio <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">sun <span class="token punctuation">.</span> misc <span class="token punctuation">.</span> Unsafe</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn java <span class="token punctuation">.</span> nio <span class="token punctuation">.</span> file <span class="token punctuation">.</span> * <span class="token operator">-</span> dontwarn org <span class="token punctuation">.</span> codehaus <span class="token punctuation">.</span> mojo <span class="token punctuation">.</span> animal_sniffer <span class="token punctuation">.</span> IgnoreJRERequirement <span class="token operator">-</span> keep <span class="token keyword">interface</span> <span class="token class-name">org <span class="token punctuation">.</span> parceler <span class="token punctuation">.</span> Parcel</span> <span class="token operator">-</span> keep <span class="token annotation punctuation">@org</span> <span class="token punctuation">.</span> parceler <span class="token punctuation">.</span> Parcel <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token operator">*</span> $$Parcelable <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn java <span class="token punctuation">.</span> lang <span class="token punctuation">.</span> invoke <span class="token punctuation">.</span> * <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> codepath <span class="token punctuation">.</span> models</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> fields <span class="token punctuation">></span></span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Dagger <span class="token number">2</span> <span class="token operator">-</span> dontwarn com <span class="token punctuation">.</span> google <span class="token punctuation">.</span> errorprone <span class="token punctuation">.</span> annotations <span class="token punctuation">.</span> * <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">javax <span class="token punctuation">.</span> inject <span class="token punctuation">.</span> Provider</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">javax <span class="token punctuation">.</span> inject <span class="token punctuation">.</span> Provider</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">dagger <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token punctuation">,</span> allowobfuscation <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token annotation punctuation">@javax</span> <span class="token punctuation">.</span> inject <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token annotation punctuation">@dagger</span> <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token operator">*</span> $$ModuleAdapter <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token operator">*</span> $$InjectAdapter <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token operator">*</span> $$StaticInjection <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">javax <span class="token punctuation">.</span> inject <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn dagger <span class="token punctuation">.</span> internal <span class="token punctuation">.</span> codegen <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn dagger <span class="token punctuation">.</span> producers <span class="token punctuation">.</span> internal <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> dontwarn dagger <span class="token punctuation">.</span> shaded <span class="token punctuation">.</span> auto <span class="token punctuation">.</span> common <span class="token punctuation">.</span> * <span class="token operator">*</span> # LifecycleObserver's empty constructor is considered to be unused by proguard <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> LifecycleObserver</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # ViewModel's empty constructor is considered to be unused by proguard <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> ViewModel</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Keep Lifecycle State and Event enums values <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> Lifecycle</span> $State <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> Lifecycle</span> $Event <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token annotation punctuation">@android</span> <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> OnLifecycleEvent <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keepclassmembers <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> LifecycleObserver</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> LifecycleObserver</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">implements</span> <span class="token class-name">android <span class="token punctuation">.</span> arch <span class="token punctuation">.</span> lifecycle <span class="token punctuation">.</span> GeneratedAdapter</span> <span class="token punctuation">{</span> <span class="token generics function"><span class="token punctuation"><</span> init <span class="token punctuation">></span></span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Enum classes <span class="token operator">-</span> keepclassmembers <span class="token keyword">enum</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token function">values</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">valueOf</span> <span class="token punctuation">(</span> java <span class="token punctuation">.</span> lang <span class="token punctuation">.</span> String <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> # Logs <span class="token operator">-</span> assumenosideeffects <span class="token keyword">class</span> <span class="token class-name">android <span class="token punctuation">.</span> util <span class="token punctuation">.</span> Log</span> <span class="token punctuation">{</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">d</span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">w</span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">v</span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">public</span> <span class="token keyword">static</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token function">i</span> <span class="token punctuation">(</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">.</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> ## Fabric <span class="token operator">-</span> keepattributes SourceFile <span class="token punctuation">,</span> LineNumberTable <span class="token operator">-</span> keep <span class="token keyword">public</span> <span class="token keyword">class</span> <span class="token operator">*</span> <span class="token keyword">extends</span> <span class="token class-name">java <span class="token punctuation">.</span> lang <span class="token punctuation">.</span> Exception</span> <span class="token operator">-</span> keep <span class="token keyword">class</span> <span class="token class-name">com <span class="token punctuation">.</span> crashlytics <span class="token punctuation">.</span></span> <span class="token operator">*</span> <span class="token operator">*</span> <span class="token punctuation">{</span> <span class="token operator">*</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">-</span> dontwarn com <span class="token punctuation">.</span> crashlytics <span class="token punctuation">.</span> * <span class="token operator">*</span> <span class="token operator">-</span> optimizations <span class="token operator">!</span> <span class="token keyword">class</span> <span class="token operator">/</span> merging <span class="token comment">/* </span> |
As mentioned, using ProGuard will minimize the source code decompilation of the application, help limit the disclosure of code or eavesdrop on important information. They are essential for building distributed applications on Google Play.
Install biometric protection
Our application can be secure by requiring users to enter a password before opening a certain interface. But there is also the risk of our passwords being accidentally hacked by someone or the hackers themselves.
So in order to ensure that it is only us who cannot access the application, smartphone devices now support biometric authentication. Faces, iris or fingerprints are good examples. We are going to set up biometric authentication on our application to ensure that only we have access to the application and no one else.
First in the build.gradle part of the application, we declare the use of the biometric library
1 2 | implementation <span class="token string">'androidx.biometric:biometric:1.0.1'</span> |
Next, to prevent crashes we need to check if the device supports biometric authentication. If not, then prompt the user to choose an alternative method such as conventional password authentication …
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | val biometricManager <span class="token operator">=</span> BiometricManager <span class="token punctuation">.</span> <span class="token function">from</span> <span class="token punctuation">(</span> <span class="token keyword">this</span> <span class="token punctuation">)</span> when <span class="token punctuation">(</span> biometricManager <span class="token punctuation">.</span> <span class="token function">canAuthenticate</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> BiometricManager <span class="token punctuation">.</span> BIOMETRIC_SUCCESS <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">showAuthentication</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> BiometricManager <span class="token punctuation">.</span> BIOMETRIC_ERROR_NO_HARDWARE <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Biometric features no support with current hardware."</span> <span class="token punctuation">)</span> <span class="token comment">//Use password authentication in this case</span> BiometricManager <span class="token punctuation">.</span> BIOMETRIC_ERROR_HW_UNAVAILABLE <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Biometric features are currently unavailable."</span> <span class="token punctuation">)</span> BiometricManager <span class="token punctuation">.</span> BIOMETRIC_ERROR_NONE_ENROLLED <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Please associate a biometric credential with your account."</span> <span class="token punctuation">)</span> <span class="token keyword">else</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"An unknown error occurred. Please check your Biometric settings"</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> |
If the device supports biometric authentication, we will call showAuthentication () function to display the authentication information to the user.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 | <span class="token keyword">private</span> fun <span class="token function">showAuthentication</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> val executor <span class="token operator">=</span> Executors <span class="token punctuation">.</span> <span class="token function">newSingleThreadExecutor</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> biometricPrompt <span class="token operator">=</span> <span class="token function">BiometricPrompt</span> <span class="token punctuation">(</span> <span class="token keyword">this</span> <span class="token punctuation">,</span> executor <span class="token punctuation">,</span> object <span class="token operator">:</span> BiometricPrompt <span class="token punctuation">.</span> <span class="token function">AuthenticationCallback</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> override fun <span class="token function">onAuthenticationError</span> <span class="token punctuation">(</span> errorCode <span class="token operator">:</span> Int <span class="token punctuation">,</span> errString <span class="token operator">:</span> CharSequence <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">super</span> <span class="token punctuation">.</span> <span class="token function">onAuthenticationError</span> <span class="token punctuation">(</span> errorCode <span class="token punctuation">,</span> errString <span class="token punctuation">)</span> runOnUiThread <span class="token punctuation">{</span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Authentication error: $errString"</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> override fun <span class="token function">onAuthenticationFailed</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">super</span> <span class="token punctuation">.</span> <span class="token function">onAuthenticationFailed</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> runOnUiThread <span class="token punctuation">{</span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Authentication failed"</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> override fun <span class="token function">onAuthenticationSucceeded</span> <span class="token punctuation">(</span> result <span class="token operator">:</span> BiometricPrompt <span class="token punctuation">.</span> AuthenticationResult <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">super</span> <span class="token punctuation">.</span> <span class="token function">onAuthenticationSucceeded</span> <span class="token punctuation">(</span> result <span class="token punctuation">)</span> runOnUiThread <span class="token punctuation">{</span> <span class="token function">toast</span> <span class="token punctuation">(</span> <span class="token string">"Authentication succeeded!"</span> <span class="token punctuation">)</span> <span class="token function">showListPerson</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> promptInfo <span class="token operator">=</span> BiometricPrompt <span class="token punctuation">.</span> PromptInfo <span class="token punctuation">.</span> <span class="token function">Builder</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">setTitle</span> <span class="token punctuation">(</span> <span class="token string">"Biometric login for your app"</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">setSubtitle</span> <span class="token punctuation">(</span> <span class="token string">"Log in using your biometric credential"</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">setDeviceCredentialAllowed</span> <span class="token punctuation">(</span> <span class="token boolean">true</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">build</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> biometricPrompt <span class="token punctuation">.</span> <span class="token function">authenticate</span> <span class="token punctuation">(</span> promptInfo <span class="token punctuation">)</span> <span class="token punctuation">}</span> |
This function will display the authentication interface as shown below.
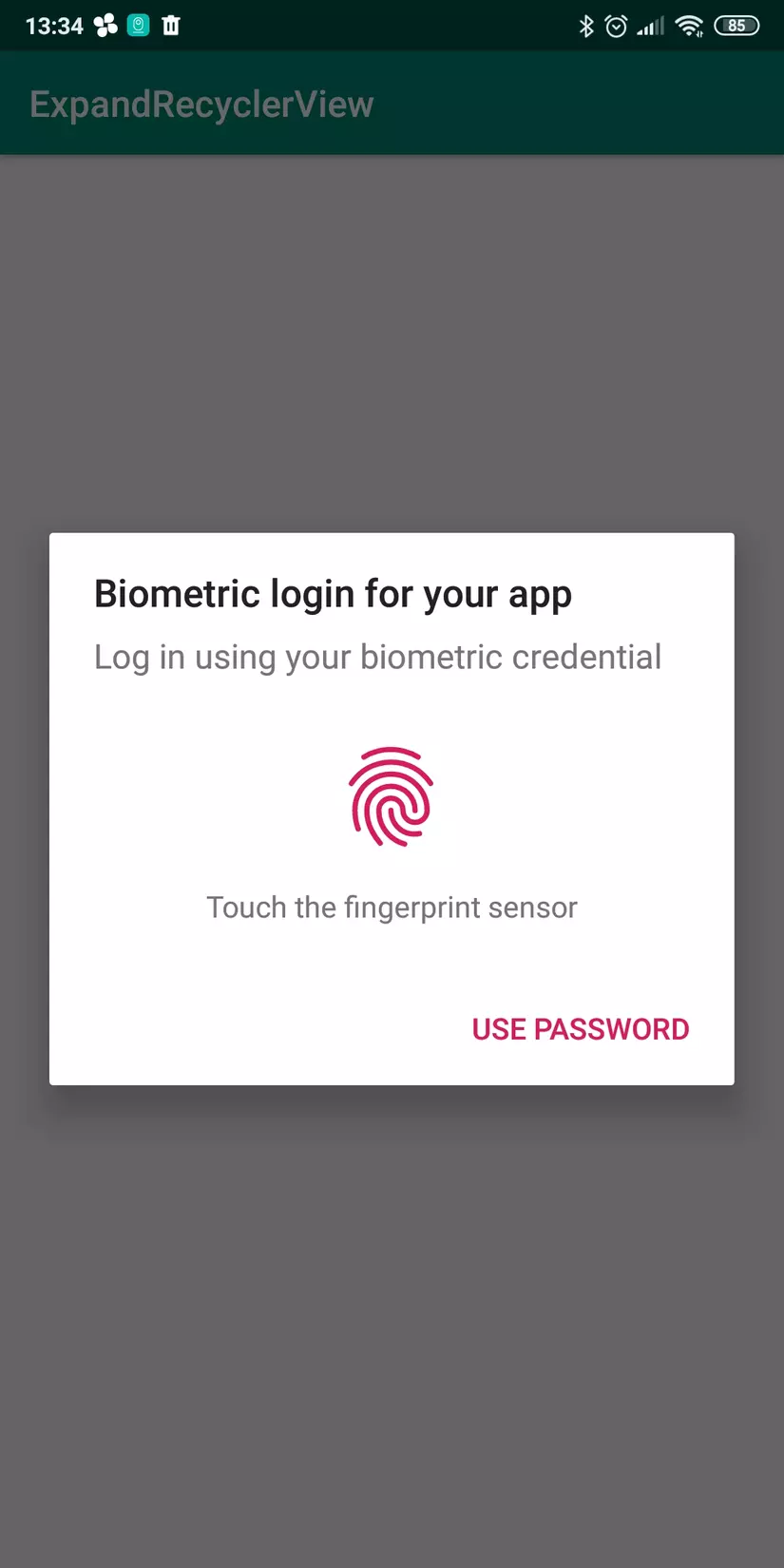
If the user authenticates, then the call will show showListPersion () function, which shows the list of users, we can see through the figure below.
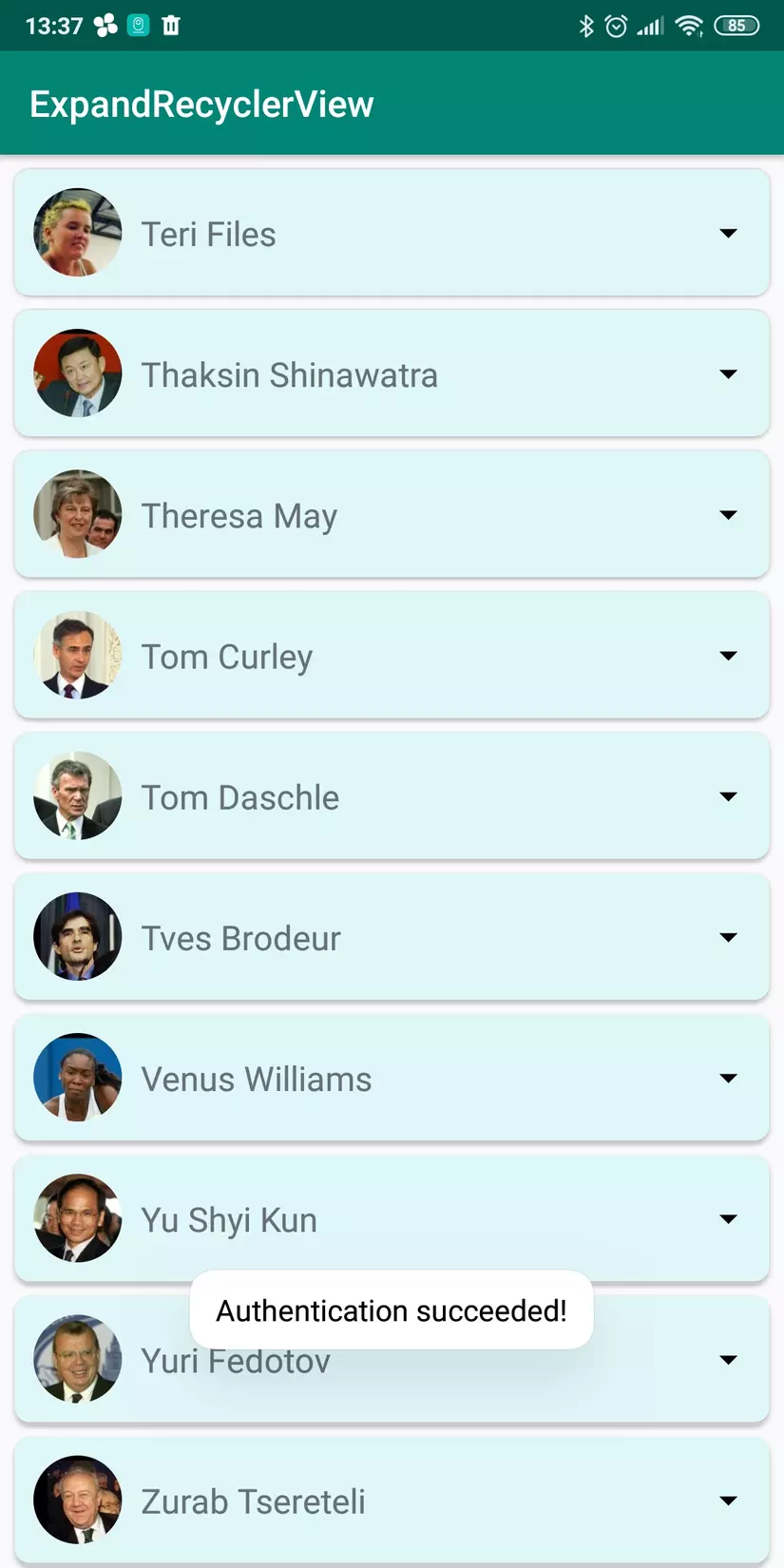
As we can see, the library of biometric authentication is quite simple but very confidential. We should prioritize installation choices if our application needs authentication before it can access the application.
