Preamble
Brothers follow this dev profession, probably half due to the love of games, the other half is due to the “black muscle” on the movie deception, And a small group that loves the profession I don’t talk about. Actually, the black guys in the movie are half real, they are the police of all kinds of chasing, and about the crazy key dance and shout “Access granted!” Where is it?
If you still do not believe and want the same, I think you can try Bollywood, you will be well trained starting with hacking the police database with the extremely stimulating music window media player: v
Hollywood is also an option if you want to hack the bank for 5 minutes while having a gun pressed to the head of a vacuum cleaner running in the groin =))
Also, I am not specialized in security, but this I learned from a senior in a sharing session, the opinions I also try to do my best to document and find out before sharing but can There are still errors. Furthermore, this is just a quick overview of me, the information is a summary and omission is a certainty. Hope you guys have stone bricks, please be gentle.
Part 1
Because, even though it’s basic, there are quite a few hacking techniques, so I will divide it into several sections to write for the article that is not too long, each part will be about 5-6, too short, then add later. And like I mentioned above, I am not specialized in security, so choosing the type of hack to introduce in the post can be quite messy, if you have comments, please comment below, I will correct it accordingly. well suited
SQL Injection
By definition, it is a security bug that would allow an attacker to insert sql code into the query. For simplicity, I will do a simple example later.
Suppose you have a login form, asking for username and password then you will query to login like that
1 2 3 4 5 | <span class="token keyword">SELECT</span> <span class="token operator">*</span> <span class="token keyword">FROM</span> users <span class="token keyword">WHERE</span> <span class="token keyword">user</span> <span class="token operator">=</span> <span class="token string">'username'</span> <span class="token operator">AND</span> pass <span class="token operator">=</span> <span class="token string">'password'</span> <span class="token keyword">LIMIT</span> <span class="token number">1</span> |
But if you get this error, they will enter the password like ' or 1=1-- and your query will be corrected to
1 2 3 4 5 | <span class="token keyword">SELECT</span> <span class="token operator">*</span> <span class="token keyword">FROM</span> users <span class="token keyword">WHERE</span> email <span class="token operator">=</span> <span class="token string">' <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> '</span> <span class="token operator">AND</span> pass <span class="token operator">=</span> <span class="token string">''</span> <span class="token operator">or</span> <span class="token number">1</span> <span class="token operator">=</span> <span class="token number">1</span> <span class="token comment">--' LIMIT 1</span> |
And boom, they log in without a password, all user information is revealed, but then in the hands of too much, you just need to fix a little more that you fly the table users, or get malicious code. That is.
This error is less common now because frameworks all support queries, so inserting code is almost impossible.
Prevention
1. Parameterization of the query
Instead of passing values directly into the query like that
1 2 3 4 | <span class="token variable">$email</span> <span class="token operator">=</span> <span class="token double-quoted-string string">" <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> "</span> <span class="token punctuation">;</span> <span class="token variable">$sql</span> <span class="token operator">=</span> <span class="token double-quoted-string string">"SELECT * FROM users WHERE email = '"</span> <span class="token operator">+</span> email <span class="token operator">+</span> <span class="token double-quoted-string string">"'"</span> <span class="token punctuation">;</span> |
Then you should use the methods to parameterize the statement like
1 2 3 | <span class="token variable">$statement</span> <span class="token operator">=</span> <span class="token variable">$dbh</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">prepare</span> <span class="token punctuation">(</span> <span class="token double-quoted-string string">"select * from users where email = ?"</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token variable">$statement</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">execute</span> <span class="token punctuation">(</span> <span class="token keyword">array</span> <span class="token punctuation">(</span> email <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
2. ORM
The query support mechanism instead of writing pure SQL as above, if you have used laravel then it is not strange ->first() or ->where(user, 'username') what kind of thing else =))
3. Escaping / Sanitizing Inputs
Filter carefully the input, remove special characters or dangerous components that can cause, simply the whitelist, instead of blocking from the one, then you block all at the whitelist you select but the ones allow entering, so delicious
Cross-site scripting (XSS)
English cross means X, so on Cross Site Scripting, it is not written as CSS, but abbreviated as XSS =)))
XSS is a hacker inserting malicious code to execute in the lobby, for example, a man simply sends <script>alert('Hello')</script> via the chat channel, whoever opens that chat channel will be turned on. alert shows Hello.
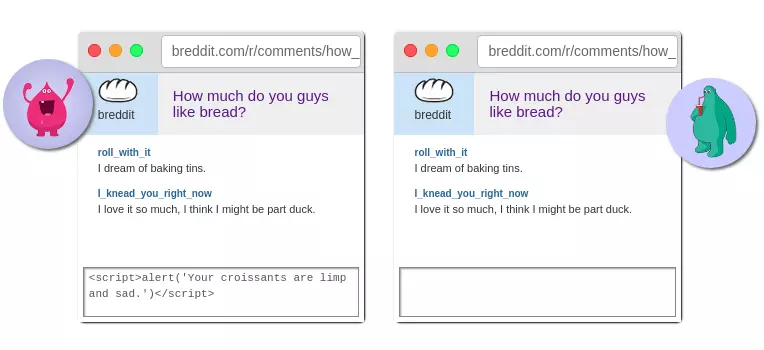
This may result in stolen browser data such as saved passwords, cookies, … or being forced to navigate to malicious websites such as x * xx, * videos, … Or if the viblo has this error, I can write a piece of code so that when someone reads the article, it will auto upvote for example, ez keycap =))
Prevention
1. Escape Dynamic Content
Basically, it is encoding special characters, there is no need to encode the entire content
2. Whitelist Values
Like the above error instead of choosing from which to ban, you just need to ban all and choose each to allow, so you will be more assured
Command Execution
This error is similar to SQL Injection and XSS above, but instead of affecting the database or clien, it affects the excuse commands on the server, usually linux.
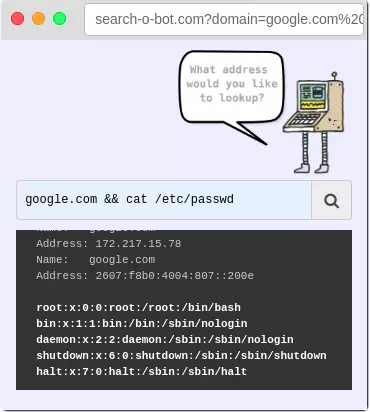
As you can see in the picture, it’s just a small example, a simple cat sentence and that’s the server’s uncovered full clip.
Prevention
As you can see in the picture, its implementation is similar to SQL Injection and XSS, so blocking is almost the same, starting with input normalization, and also having to delegate the right to execute the correct command. Blocking from accessing data from unauthorized people, it basically gets the following bullet points:
1. Espace inputs
2. Restrict the allowed commands
3. Run with limited permissions
4. Avoid calling commands together
5. And remember to ask everyone in the team to review the code carefully
Clickjacking
This one, everyone who watches pirated movies or reads online stories will surely meet many, many, but it is also intentionally plugged in by developers.
It’s that you guys click play video but pop up the ad, click close the ad, but pop up the ad, click it on everything and pop up the ad
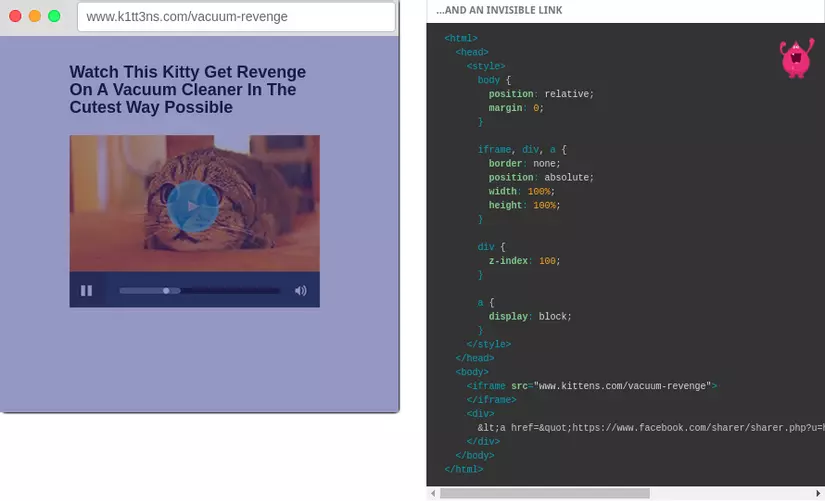
This can be done with css, or js. Anyway, I don’t teach and how to bypass I don’t just do it, everyone’s fishing rod.
But this is just a small “application” of it, if in the hands of hackers, trickers, they can force you to download malware files, redirect you to malicious readers or combine with XSS, causing you to accidentally send. giving them personal information without your knowledge
Prevention
1. X-Frame-Options
Indicates to allow the browser to render tags such as <frame> , <iframe> , <object>
2. Content Security Policy
As part of HTML5, protected broader than X Frame, but how is it I don’t know
3. Frame-Killing
Insert this code into the page, it will check if the original page domain is the same as the browser’s domain or not, if it is, it will be allowed to display.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <span class="token tag"><span class="token tag"><span class="token punctuation"><</span> style</span> <span class="token punctuation">></span></span><span class="token style"><span class="token language-css"> <span class="token comment">/* Hide page by default */</span> <span class="token selector">html</span> <span class="token punctuation">{</span> <span class="token property">display</span> <span class="token punctuation">:</span> none <span class="token punctuation">;</span> <span class="token punctuation">}</span> </span></span><span class="token tag"><span class="token tag"><span class="token punctuation"></</span> style</span> <span class="token punctuation">></span></span> <span class="token tag"><span class="token tag"><span class="token punctuation"><</span> script</span> <span class="token punctuation">></span></span><span class="token script"><span class="token language-javascript"> <span class="token keyword">if</span> <span class="token punctuation">(</span> self <span class="token operator">==</span> top <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token comment">// Everything checks out, show the page.</span> document <span class="token punctuation">.</span> documentElement <span class="token punctuation">.</span> style <span class="token punctuation">.</span> display <span class="token operator">=</span> <span class="token string">'block'</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> <span class="token comment">// Break out of the frame.</span> top <span class="token punctuation">.</span> location <span class="token operator">=</span> self <span class="token punctuation">.</span> location <span class="token punctuation">;</span> <span class="token punctuation">}</span> </span></span><span class="token tag"><span class="token tag"><span class="token punctuation"></</span> script</span> <span class="token punctuation">></span></span> |
Cross-site Request Forgery
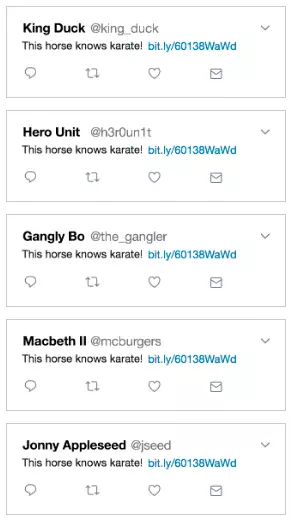
An attack technique using a user’s authority over a website. An example of an attack script would look like this:
- A web posting post used GET method and was noticed by a hacker
- he corrected the path including the request to be posted on the web like
www.tweeper.com/post?message=This+horse+know+karate!+www%2Cbit.ly%2F60138Wawdand sent it to everyone. - the recipient of the mail or something has not such a link
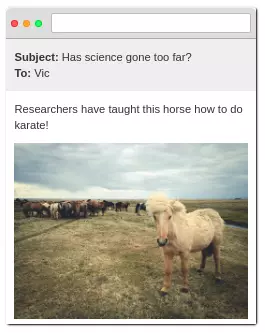
- When they click on the link, they will be redirected to that site and perform the act of posting articles that hackers have prepared, but introduce the corrupt web, spread viruses, install malware …
Prevention
This prevention should be done well both on the user and the server side
User
- Exit accounts at important websites after finishing work
- Don’t click on incoming links without knowing what they are for
- Do not save password information in the browser
- When doing important work, or opening important websites, do not visit other websites, which may contain malicious code.
Server
- Use the GET and POST methods properly
- Use captcha or confirmation messages
- Use tokens
- Use specific cookies for the admin site
- IP test
