1.VPC
When we use AWS services we run them as instances, just like any other physical network device, the instances in AWS communicate with each other over the network. Each AWS account can create multiple instances, so how do instances of other AWS accounts access your instances and vice versa, that’s thanks to VPC (Virtual Private Cloud), this is a a virtual private network, it helps you organize your AWS resources by providing a virtual private network where you can customize your intances to be public outside the internet or just communicated. in the internal range. By default, when newly created, VPC is isolated from the internet or other VPCs, but I can set it up so that VPC can access the internet or other VPCs. One VPC belongs to only one region.
1.1 VPC CIDR block (classless inter domain routing)
When creating a VPC, we have to give it at least a range of IP addresses, the VPC will automatically assign the instances within it the IP address in this IP range. An IP address range can be represented in many forms, but AWS uses the CIDR form to represent the range of IP addresses. The sequence of IP addresses in CIDR looks like this: 172.16.32.0/20 (172.16.32.0 – 172.16.47.255). where / 20 represents the prefix length or the number of bits occupied by the prefix, so the smaller the number, the more IP addresses this range will contain. In VPC, valid prefix lengths range from / 16 to / 28 (/ 28 has only 16 IP addresses). So how can the CIDR block know what the IP range is? We can refer to the calculation method here or if lazy, you can use the calculator quickly here
Although it is possible to create any ip range for the VPC as long as it is valid, AWS recommends using the RFC 1918 IP range to avoid conflicts with public IPs.
- 10.0.0.0–10.255.255.255 (10.0.0.0/8)
- 172.16.0.0–172.31.255.255 (172.16.0.0/12)
- 192.168.0.0–192.168.255.255 (192.168.0.0/16)
Note that once the IP ranges are assigned to the VPC, it cannot be changed, so we should choose carefully before creating the VPC.
1.2 Secondary CIDR Blocks
We have a sub-range of IPs outside of the main sequence after creating the VPC, this IP range must be the same range as the primary sequence or be a public IP range, but must not overlap with the primary sequence. For example, the VPC has the main IP range 172.16.0.0/16 (172.16.0.0 – 172.16.255.255), we can add the sub sequence 172.17.0.0/16 (172.17.0.0 – 172.17.255.255) but not use the range. 192.168.0.0/16 (192.168.0.0 – 192.168.255.255) because the address range is not the same (192.168 and 172.16). Note that when choosing 192.168.0.0/16 as the primary IP range for the VPC, because it is the last IP range of a valid IP range in the VPC, you cannot choose the sub IP range for the VPC according to RFC 1918 standards.
1.3 IPv6 CIDR Blocks
The IP ranges mentioned in 1.1 and 1.2 are IPv4, you can also use IPv6 for VPC, but unlike IPv4, if you use IPv6, AWS will not allow you to manually select the IP range for IPv6 but instead There, AWS will be spontaneous.
2.Subnet
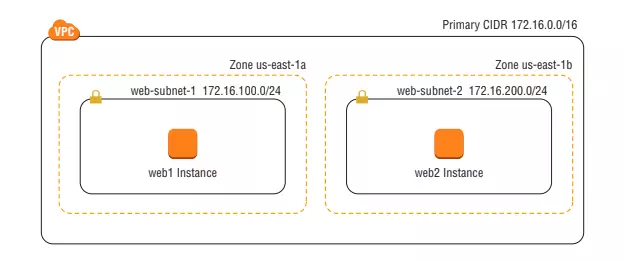
Subnet is a logical container inside the VPC where we will place the instances, which isolates some instances from others right in the VPC itself. It can be understood that VPC is a house, the subnets are the rooms inside that house, the purpose is to help us group the instances by functional aspect. For example: In a VPC that has servers and databases, the servers will be publiced on the Internet, we will put it inside the public subnet, and the databases are not allowed to be public outside the internet, but only accessible by servers. will put it in the private subnet. When creating an AWS instance, it is imperative to choose a subnet for it, a subnet can contain multiple instances and an instance belongs to only one subnet and once an instance is attached to a subnet we cannot convert it to another subnet, only can delete that instance and recreate it on another subnet. And what is the public subnet and private subnet, I will explain in the next section.
2.1 Subnet CIDR Blocks
Like the VPC, the subnet also has its own IP range (CIDR Block), this IP range must be a subset of the IP range of the VPC, for example: VPC has an IP range of 172.16.0.0/16 (172.16.0.0 – 172.16.255.255 ) then we can choose the CIDR block for sunnet is 172.16.100.0/16 (172.16.0.0 – 172.16.255.255). For each subnet, AWS will take the first 4 addresses and one last address of the IP range in the subnet for a purpose we don’t know yet: v, so we will not be able to use these addresses to assign the instance. inside that subnet. For example: subnet A has a CIDR block of 172.16.100.0/16 (172.16.0.0 – 172.16.255.255), the following addresses will not be used.
- 172.16.100.0–172.16.100.3
- 172.16.100.255
The IP range of the subnet must not overlap with the IP ranges of other subnets in the same VPC, this means when adding an IP range to the subnet, if using the IP range of the VPC, we cannot add any subnet. That VPC too, once we have added the IP range for the subnet, we cannot edit that IP range anymore, it can only delete and then recreate, and deleting the subnet means the instances within it are also deleted. So please consider carefully before creating the subnet. VPC can have sub-IP ranges as mentioned in 1.2, subnet has only one IP range, we can use VPC’s subnet IP range as IP range for subnet.
2.2 Availability Zones
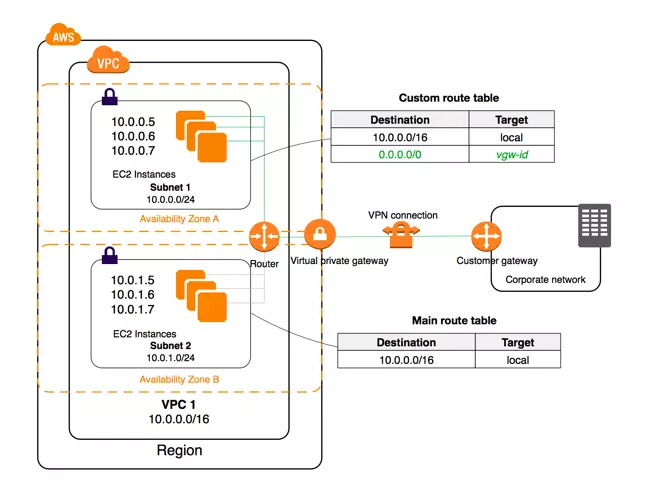
A subnet resides in an Availability Zone, which is a geographic location where AWS builds the infrastructure. One Region will have many Availability Zones connected to each other, but when one zone collapses, the other zones will still operate normally without being affected, so to optimize when designing the system, to increase the recovery for your applications should create two subnets in different Availability Zones and then spread your instances across those regions.
3.Internet Gateways & NAT Gateways
3.1 Internet gateways
As mentioned in section 1, VPC is isolated from the internet, so how can components in VPC such as instances can access internet or from internet can access instances in VPC? That’s thanks to Internet Gateways. It gives instances the ability to receive public IP addresses, connect to the Internet, and receive requests from the Internet. When you create a VPC, the VPC doesn’t have the Internet Gateway associated with it. You must create the Internet Gateway and manually attach it to the VPC.
3.2 NAT gateways
So if the instance wants to perform operations such as installing libraries or updating software versions, so it must be able to access the internet but not allow access from the internet? We can use NAT gateways, unlike Internet Gateways which allows instances to connect to the Internet and receive requests from the Internet, NAT gateway only allows the instance to access the public Internet.
4.Router & Route Tables
In a VPC to direct incoming and outgoing traffic, AWS uses a piece of software called an implied router . This router will follow the rules defined in the route table to direct traffic within the VPC. By default when creating a VPC, AWS will create a route table for the VPC called the main route table and once we create a subnet in the VPC, this subnet will automatically be attached to the main route table , if you don’t want to use the main route table. for the subnet, we can create a custom route table and attach the subnet to it. A subnet must be attached to a route table.
A rule in the route table is called a route, a route table can contain one or more routes. Routes define how the traffic flows of the instances within the subnet are attached to that route table. A route will have the following two values:
- Destination: is an IP range, the instances with the IP address in this range can access the destination with the value of the target .
- Target: are network resources in AWS such as instance, internet gateway …
A public subnet (all instances in that subnet have internet access and vice versa) is the subnet attached to the route table where Destination is the subnet of the IP range of the subnet and Target is an internet gateway. In each route table there will be a default route with a local Target called a local route , this route helps instances in the same subnet communicate with each other and can communicate with instances in other subnet in the same VPC.
5. Conclusion
In addition to the components mentioned above, in AWS there are also Security Group and Network Access Control Lists to serve the security of VPCs, but the theory of these two components is very long, so I will talk in another article. Thank you for watching
