1. What is SSL
SSL is not just a security certificate. It also has a more technical definition. SSL is a protocol that allows information to be transmitted securely and securely over the network.
Connecting a web browser to any point on the Internet goes through many independent systems. And without any protection with the information on the line. No one, either the user or the Web server, has any control over the path of the data or can control whether someone enters information on the link.

To protect confidential information on the Internet or any TCP / IP protocol. SSL has incorporated the following factors to establish a secure transaction:
- Authentication: ensure the authenticity of the page that you will be working on the other end of the connection. Also, Web pages need to check the authenticity of the user.
- Encryption: ensures information cannot be accessed by third parties. To eliminate eavesdropping on “sensitive” information when it is transmitted over the Internet. The data must be encrypted so it cannot be read by people other than the sender and receiver.
- Data integrity: ensuring information is not misleading. Accurately represent the original information sent to.
- With the use of SSL, Web sites can provide information security. Authentication and data integrity to users. SSL is built into browsers and Web servers. Allow users to work with Web pages in safe mode.
2. SSL protocol
SSL was developed by Netscape. Today SSL protocol has been widely used on the World Wide Web in authenticating and encrypting information between client and server. The IETF (Internet Engineering Task Force) organization standardized SSL and renamed it TLS (Transport Layer Security). Despite the name change, TSL is just a new version of SSL. TSL 1.0 version is equivalent to SSL 3.1 version. However SSL is the more widely used term.
SSL is designed as a separate protocol for security, supporting for a lot of applications. The SSL protocol works above TCP / IP and beneath higher layer application protocols such as HTTP, IMAP and FTP.
SSL is not a single protocol, but a set of standardized procedures for performing the following security tasks:
- Server authentication: Allows users to authenticate the server that they want to connect to. At this point, the browser side uses public encryption techniques to make sure that the server’s certificate and public ID are valid and issued by a CA (certificate authority) in the client’s trusted CA list. This is very important to the user. For example, when sending a credit card code over the network, the user really wants to check if the server will receive this information is exactly the server they are sending to.
- Client authentication: Allows the server side to authenticate users who want to connect. The server side also uses public encryption techniques to check if the server’s certificate and public ID are valid and issued by a CA in the server’s list of trusted CAs. This is very important to the supplier. For example, when a bank intends to send confidential financial information to its customers, it is very tempting to check the identity of the recipient.
- Encryption connection: All communication between client and server is encrypted on the line to improve security. This is very important for both parties when there are private transactions. In addition, all data sent on an encrypted SSL connection is protected by automatic tampering and change detection in the data. (these are the hash algorithms).
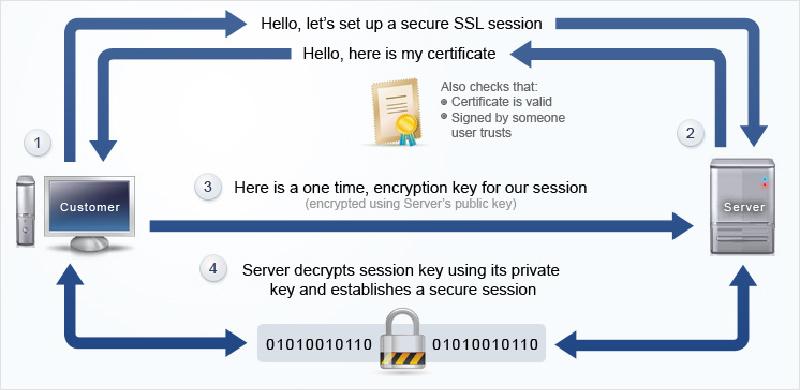
- How SSL works *
The SSL protocol consists of 2 sub-protocols:
- SSL record protocol: defines the formats used to transfer data
- The SSL handshake protocol (called the handshake protocol): uses the SSL record protocol to exchange some information between the server and the client and first establish an SSL connection.
3. Algorithms used in SSL
The encryption and authentication algorithms of SSL used include:
- DES (Data Encryption Standard) is an encryption algorithm whose key length is 56 bits.
- 3-DES (Triple-DES): is an encryption algorithm with a key length of 3 times the key length in DES encryption
- DSA (Digital Signature Algorithm): is part of the standard of digital authentication being used by the US government.
- KEA (Key Exchange Algorithm) is a key exchange algorithm being used by the US government.
- MD5 (Message Digest algorithm) was developed by Rivest.
- RSA: is a public encryption algorithm used for both data authentication and encryption developed by Rivest, Shamir, and Adleman.
- RSA key exchange: is the key exchange algorithm used in SSL based on RSA algorithm.
- RC2 and RC4: are encryption algorithms developed by Rivest for RSA Data Security.
- SHA-1 (Secure Hash Algorithm): is a hashing algorithm being used by the US government.
When a client and server exchange information in the handshake phase. They will determine the strongest possible encoder and use them in SSL session.
Refer:
