- Wouldn’t it be great to log in to a web app or mobile app (e.g. Trello) with your login and print credentials stored elsewhere such as Google? Or Facebook? . Yes, yes, OAuth2 and OpenID Connect make us feel great, because we do not need to enter the password sometimes forgotten or some basic information to access to use the service. in the same opium.
- We will find out how these 2 guys work. Let’s first have a look at how OAuth2 works first and then OpenID Connect . BECAUSE OpenID Connect, it was developed from OAuth2 .
1. OAuth2
So it’s OAuth2 what it is
OAuth2 is an authorization framework that allows applications to have access to user accounts and has limited access to HTTP services.
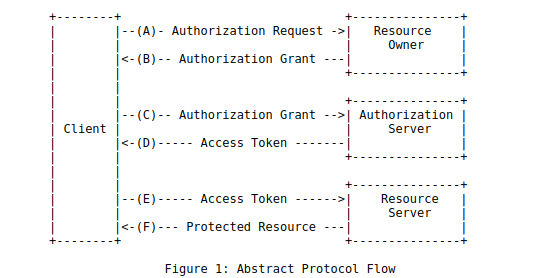
It works by delegating user authentication to the user account hosting service. To make it easy for people to use the flow, look at the following image:

Here I will explain the steps in the operation diagram: Suppose that we have application A, we want to log in with the facebook account (provided that we already have an account).
- Application A will require authorization to access the user-owned service resources.
- If the user accepts the request, application A will receive an authorization grant .
- The application will request access token from the authorized server by presenting its own identity and granting an authorization grant .
- If you have verified the identity of the application and the authorization is valid. The authorized server will provide access token to the application so the authorization is completed.
- The application will request resources from the server and present an access token for authentication.
- If the access token is valid, then the server will now allow the application to access and use it.
- The Resource Owner is the user.
- Application (client) is a 3rd party application.
- The Authorization Server is your proxy server, which specifies access to resources.
- Resource Server is the place to store your information.
- It could be something like this when you log in to your facebook account (assuming you already have a facebook account) with a 3rd party application, it will ask to give it access to use some of your resources. such as email, avatar ….
- The 3rd party application will move to the login dialog of facebook, this time create a reuquest to submit including Application ID and Application secret (When you have a facebbook account, you will). Of course, coming here will require you to log in if the session is still available, and will show you some rights, when you will agree to access what information.
- When you accept access it will return to the Facebook app and will give you an acess token to retrieve information from your profile.
2. Open ID Connect
- OnpenID Connect is a single identity layer developed based on the OAuth2.0 protocol, which allows the client to determine the enduser identifier based on the authentication performed by the authorization server or identity provider (IdP) as well as to obtain Enduser information in the same way as RESTfull HTTP . OnpenID Connect specifies the HTTP RESTfull API to use JSON as the data format.
- It is an increasingly popular protocol. Every time the application prompts us to log in with Facebook or Google, it can OpenID Connect
- Support multiple clients including web based, mobile, and Javascript client to request and receive information about authentication sessions and endusers.
- OneLogin provides connectivity options to easily customize application configuration. Your OpenID Connect can use OneLogin as an identity provider (IDP) in the operation of OpenId Connect.
The basic steps of the protocol:
- (A) The user will access a third party and request access.
- (B) A third party sends an authentication request to the OpenID provider, describing the scope to be requested and the response_type to be received.
- (C) The OpenID provider requires the user to verify the identity which will then grant the third party rights in the scope
- (D) The OpenID provider sends back the 3rd party Authentication Response containing the information wanted in step (A) to the merchant ID Token and Access Token.
- (E, F) The 3rd party will use the access token to exchange the information they want.
OpenID Connect Authorization flow
- Code Flow
- User requires login to a 3rd party application (trello, lazada …)
- The third party will redirect to the OpenID provider (this time the user provides information to verify this is created), along with information such as:
client_id: mã đăng ký đinh danh với OpenID providerscope: quyên mà bên thức 3 được cấpresponse_type: coderedirect_uri: Nếu xác thực thành công thì bên OpenId provider sẽ redirect lại bên app thứ 3- The OpenId provider renders the login page and requests permission. If successful, it will revert to uri in step 2 of that authorization code. 3rd party will send request along with token. This is why response_type is the code in step 2.
- At this time, the user has returned to the 3rd party application that has been successfully authenticated. Will send a request to the
OpenId providerwith data including code, grant_type (authentication / registration designation). If successful, theOpenId providerreturns the Token ID that may be associated with the access token. - The 3rd party will verify the ID Token successfully and can access to get data from the
resource server.
2. Implicit Flow, Password Flow
- This flow is the same as steps 1 and 2.
- In step 3 the same thing but response_type: id_token (and token). In this flow, it does not require explicit verification as in step 4 above, so it is called Implicit flow. Another difference of implicit flow is that the token returned to the client is attached to the fragment (or hash) of the callback url rather than the query.
- Hybrid Flow
- The steps for this flow are exactly the same as for authorization code flow. Except the response_type sent in the authentication request (step 2) is the code and id_token to get the ID token and either the token to access the access token or all 3. Then the
OpenId providerreturns the authorization code and the id token to send the request token as in step 4. The third party who receives the authentication response will have an access token to use and still have an authorization code to exchange for refresh tokens for long-term use (note that the access token life cycle is quite short, only a few dozen minutes).
In short, OpenID is about authentication (using the login information from the OpenID provider to log in to the 3rd application) and OAuth is authorized to allow 3rd party applications to access information. Basically, OpenId Connect’s Flow is similar to OAuth 2.0 authorization process, but there is a difference:
- In addition to access-token, the authorization server returns Id-tokens
- You can pass more scope when calling the Authorization server
- Id-token has not been verified user information
OpenId Connect standard pretty much everything that OAuth2.0 is the choice as can define specific access rights to usernames, emails .. kind of very detailed, endpoint discovery, flexible registration for the client. This helps developers to give users more choices of identity providers.
Reference links
https://stackoverflow.com/questions/1087031/whats-the-difference-between-openid-and-oauth https://developers.onelogin.com/openid-connect https://digimed.vn/2017/05/ 30 / openid-connect-1-0-for-new-people / http://techastute.blogspot.com/2012/05/openid-authentication-oauth.html
