What’s dangerous with Cross-Site-Scripting (XSS) security vulnerabilities?
Every time I write writeup articles about an XSS vulnerability discovered on a website, I know there will be people who smirk and smirk because at that time they will think:
- "What the hell is this XSS error so dangerous?"
- "In addition to showing a dialog, what else can XSS do?"
- “It's a naughty hole. But the dialog box is also called a vulnerability? "
- …
So, what is dangerous about XSS?
Instead of writing a bunch of boring theories, we will look at the types of XSS exploits that have been applied in practice . In advance, to let anyone who is not yet aware of XSS, Google should see what it is before reading this article.
XSS worm
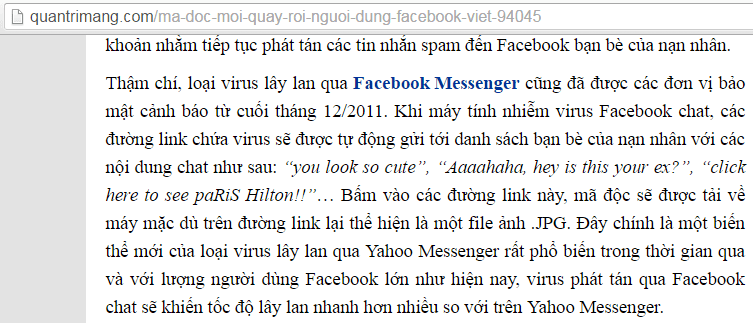
XSS worm is a web-based worm / malicious code and obviously written in JavaScript with the goal of infecting all users visiting the site. The most common example is on Facebook.
With their large number of users, the XSS worm has a dizzying spread rate on Facebook that we often see in the form of: A infected> sends a malicious message to B, C, D, … (located in A's friends list). B, C, D and those friends also continue to send messages to all of their own friends. And so the worm was spread exponentially uncontrollably.
* To be able to send messages, the XSS worm will work with CSRF .
More information: On Facebook there is another popular form called Self-XSS (this type combined with Social engineering skills). Facebook always alerts you when you press F12 (open Console) is to protect you from this XSS variation.
Browser-based Botnet
In 2014, security firm Incapsula (rival of CloudFlare) had an article about one of the world's largest websites (Alexa Top 50) hacked, making all visitors become zombies for a raid. DDoS public. And do you guess what turned the user into a zombie? Yes, it is XSS. Specifically in this case is a Persistent XSS vulnerability.
Based on the article, the flaw is in the change of avatar / profile picture. The attacker has inserted JavaScript snippets into the <img> using the onload event, each time the image is loaded it means that the other JS segment will be executed.
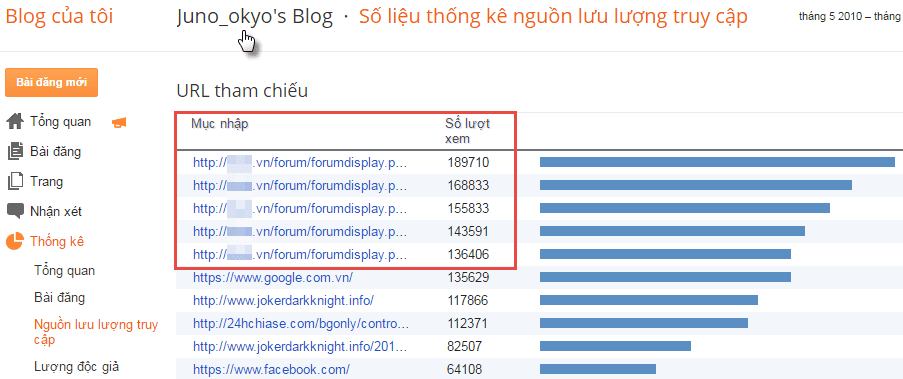
Because it is the top site, the large traffic has been taken advantage of to execute the JS segment using Ajax queries pointing to any website. And so that site becomes a DDoS victim.
* Additional Information: 3 or 4 years ago I discovered a SQL Injection vulnerability in a large forum (currently in the Top 500 Alexa VN) using vBB. After contacting the Board of Directors to make a mistake, I got scolded because they insisted that I "planned to sabotage the forum", I was very angry.
With the SQLi vulnerability in hand, I exploited the Password (hash) and Salt of the entire Admin account then cracked the plain text of an account. Visit the AdminCP in the notification creation section, I insert a JavaScript to create a query that points to my Blog. Frankly, DDoS itself is easy to understand, because I know my blog cannot crash (Google says it, hehe). As a result, the number of visitors to the other forum becomes a huge amount of traffic hitting my blog, Alexa rank skyrocketed.
XSS> CSRF> Upload Web-Shell
This is the script I am most familiar with because it has been applied a lot, since vBB (vBulletin) is still popular. In addition, this scenario is often easy to apply to WordPress due to the plugin management structure of this platform. Details of how to attack:
- Find an XSS vulnerability.
- Try to occupy the user's Security Token based on the XSS vulnerability found.
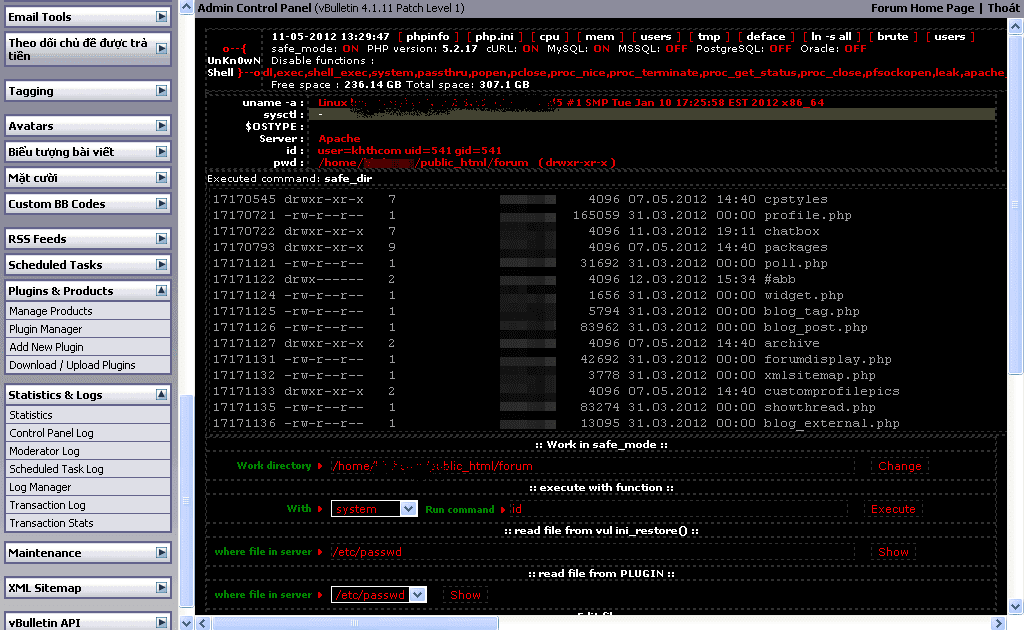
- Use the Security Token to create a plugin (or change the code of an existing plugin), thereby obtaining the Upload Form.
- Use the Upload Form in step 3 to upload to the Web-Shell. You have full control over that website via Web-Shell. Now you can start installing back-door or download the entire Database of the site.
* You can create web-shell right from step 3 but usually the code of a shell is very large, which can affect the query speed when exploiting. So I often create a Upload Form first.
Demo images in vBB:
Video demo process of exploiting DOM-based XSS vulnerability in Yoast SEO (aka WordPress SEO) – one of the most used statistic plugins from WordPress.
summary
In this article, I have given the 3 most dangerous scenarios when exploiting the XSS security hole according to my personal assessment. In addition, there will be many other scenarios based on the creativity and skills of a hacker. Do you know which drama is more interesting? Leave a comment below! ?
“Well, it sounds dangerous, but why do I see him writing about XSS? Isn't it too cool !? ”
Ah … a common mistake, located in the top 10 OWASP , is both dangerous and can be combined well with other errors. But easy to find, easy to fix, it is still counted bug bounty.
So why not? ?
Happy Hacking! ?