What is the SQL Injection description and how to check it
- Tram Ho
The article describes about sql injection and how to check web application for sql injection errors.
SQL injection is considered one of the most popular attacks because it can have serious and harmful consequences for your system and sensitive data.

What is SQL Injection?
SQL injection is a technique that attacks an application's database system (web, mobile or desktop …) through an attacker taking advantage of a vulnerability that checks input data and executes any SQL statements legal. The consequences of this action may be alarming.
As its name implies, the purpose of a SQL injection attack is to inject malicious, malicious SQL code into the application.
In applications where this data is specified go to the database such as:
- Login form (form) – user enters login data
- Search form – user enters search data
Instead of entering the correct data, the attacker will enter any malicious query statement, there is a possibility of serious damage to the database and the entire system.
SQL injection is implemented with the SQL programming language. SQL (Structured Query Language) is used to manage data stored in databases stored in a database. Therefore, in this SQL injection attack, SQL statements are used as malicious code.
This is considered the most common attack, because the database is used most for all technologies.
Consequences of SQL injection attacks
The main purpose of this attack is to hack the system's database, since most systems now have databases to store information. Therefore the consequences of this attack are really huge.
The following may be the result of SQL injection attacks:
- Hack accounts of others.
- Steal and copy sensitive data of the website or system.
- Change the data of the system, causing data deviation.
- An attacker can log in as a legitimate user, even as an administrator.
- An attacker can view personal information belonging to another user, for example: details of another user's profile, details of their transaction, etc.
- An attacker can change application configuration information and data from other users.
- An attacker can modify the database structure; even delete tables in the application's database.
- An attacker can control the database server and execute the above commands at will.
The consequences listed above can be considered serious, because recovering the database can cost a lot. It can cause companies to lose their reputation. Therefore, protecting the system against this type of attack and considering security testing is a top priority and a good investment for product and company reputation.
The nature of SQL injection attacks
To check, you first need to find vulnerable parts of the system (vulnerable) and then try sending a malicious SQL code through the input fields. If the system has this error, the injected SQL code will be sent to the database query in the application and execute it.
Any location that has input data and is associated with the database should be checked by: Instead of entering an accurate data I will enter any malicious SQL code and see the system Executing the entered code is exactly an SQL injection error.
To perform this attack, the action and purpose of a database query must be changed to suit each situation. One of the feasible methods of doing it is to make the query always correct and then insert the malicious code. Changing the query to always true can be done with a simple code ' OR 1 = 1; --
The tester should keep in mind that while checking whether the query change is always possible, it is recommended to try different citations – single and double. So, if you've tried a code ' OR 1=1;-- , you should also try with " OR 1=1;--
For example, let's assume that there is a query, which is to search for the word entered in the database table:
1 | <span class="keyword">select</span> * <span class="keyword">from</span> notes nt <span class="keyword">where</span> nt.subject = 'search_word'; |
Instead of finding the search word, enter the SQL injection query ' OR 1=1;-- , the query will always be correct. And will become
1 | <span class="keyword">select</span> * <span class="keyword">from</span> notes nt <span class="keyword">where</span> nt.subject = ' ' <span class="keyword">or</span> <span class="number">1</span> = <span class="number">1</span> ; <span class="comment">--</span> |
In this case, the user's subject parameter is closed with ' and then we have the code or 1=1 , which makes a query always correct. With the symbol -- will comment the rest of the query code, and the code behind will not be executed. This is one of the most popular and easiest ways to start query control.
Some other codes can also be used to make the query always correct, such as:
-
' or 'abc'='abc';-- -
' or ' '=' ';--
The most important part here is that after a comma, we can enter any malicious code, which we want it to be executed. For example: It could be ' or 1=1; drop table users; -- If the above injection statement is executed, then the users in the database will be deleted. If the above command can be run, any other malicious code can be written. Trogn this case depends on the attacker's knowledge and purpose.
How to check SQL injection
Checking this vulnerability can be done very easily. Sometimes it just needs to enter an unusual sign like ' or “ . If it returns any unexpected unexpected messages, then we are sure that this is SQL injection. For example: If you receive an error message like Internal Server Error in search results, you can confirm that this SQL injection attack can occur in the system.
Other results, it can be reported that SQL injection can be attacked:
- Returns an empty page.
- No error or success message – functionality and page not responding to input.
- Successful notification for malicious code entered.
Please rely on the actual case to guess.
For example: Check if the login window is vulnerable to SQL injection. In this case, the username field and the password, just enter the sign ' as shown below.

If the input returns an error message or any other non-conforming result, then it is reasonable to guess that a SQL injection attack can occur. Error message is similar to the image
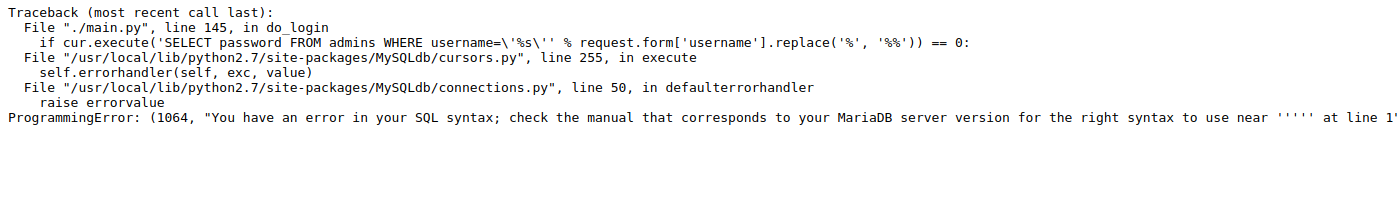
Testing SQL injection with a quote ' is a reliable way to check if this attack is possible.
If the single quote ' does not return any inappropriate results, then you can try typing quotation marks " and check the results.
In addition, the SQL code to change the query is always true 'OR 1=1;-- can be considered a way to check if this attack is possible. It closes the parameter and changes the query to True . Therefore, if not authenticated, such an input can also return any unexpected results and similar messages, and assert that SQL injection attacks can occur in this case.
Check SQL attacks can be done from the site's link. Suppose we have a link http://35.190.155.168/cf5ef2940d/fetch?id=1 returns the content of an image file. In this case, id is the parameter and 1 is its value.
If in the link, we will fill in ' instead of 1 to check. In this case, if the link http://35.190.155.168/cf5ef2940d/fetch?id=' returns an Internal Server Error or an empty page or any other unwanted error message, then This is SQL injection. Can send more complex SQL code.
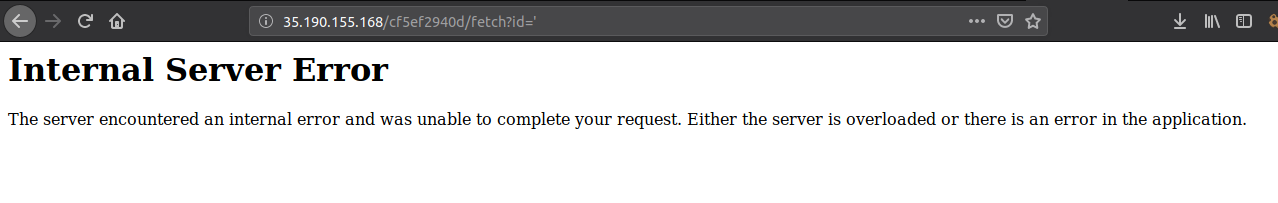
Not only will the new unwanted error message be considered a SQL injejction vulnerability. Many testers check for possible attacks only according to the error message. However, it should be remembered that no authentication error message or any success message for the code can be a sign that the attack is feasible.
summary
- In the article, I introduced about SQL injection, nature and how to check if an application has SQL injection errors.
- The word can be applied to more complex SQL statements
Source : manhnv
