Overview of SQL Injection
Concept
- SQL Injection is a technique that allows attackers to take advantage of the vulnerability of checking input data in web applications and the error messages returned by the database management system to inject. and executing illegal SQL statements
- SQL injection can allow attackers to perform operations on the database of an application, even the server on which the application is running.
Reason
- Data input from users or from other sources is not checked or checked thoroughly
- The application uses dynamic SQL statements, in which data is connected to the original SQL code to create the complete SQL statement
The dangers of SQL injection attacks
Depending on the level of sophistication, SQL Injection may allow an attacker:
- Pass the user authentication stages
- Insert, delete or modify data
- Steals information in the database
- Seize control of the system
Classification of SQL injection attacks
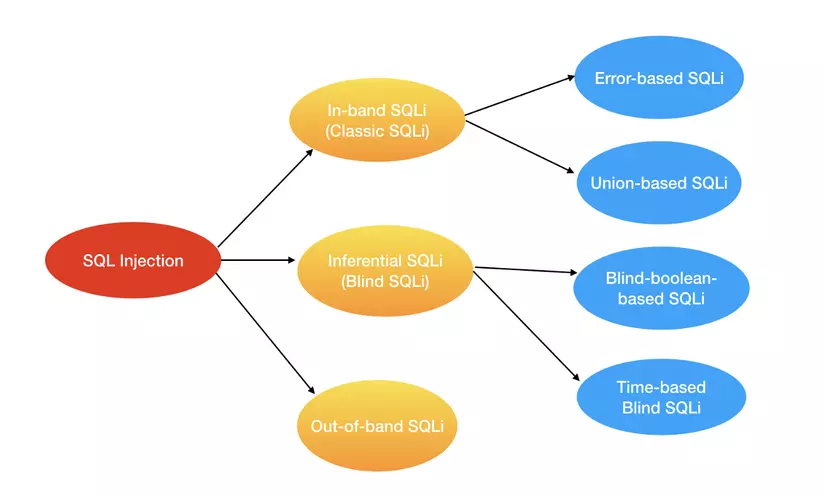
SQL Injection can be broken down into the following formats
- In-band SQLi
- Error-based SQLi
- Union-based SQLi
- Inferential SQLi (Blind SQLi)
- Blind-boolean-based SQLi
- Time-based-blind SQLi
- SQLi Out-of-band
In-band SQLi
- This is the most common type of attack and is also the easiest to exploit SQL Injection vulnerabilities
- Occurs when a hacker can organize an attack and gather results directly on the same communication channel
- In-Band SQLi is divided into 2 main types:
- Error-based SQLi
- Union-based SQLi
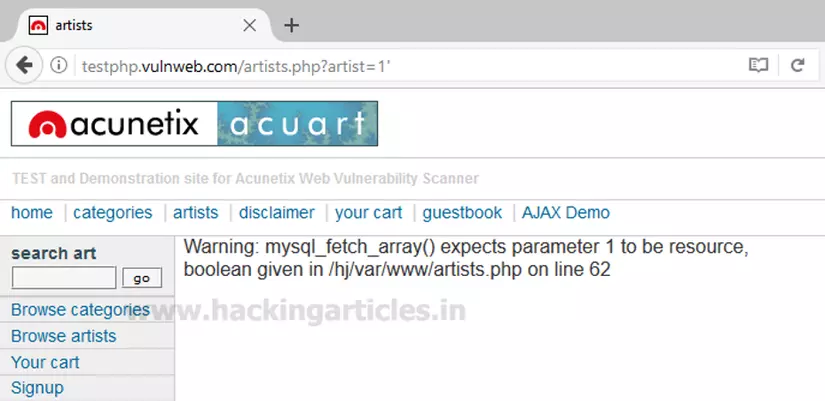
Error-based SQLi
- An SQL injection attack technique based on the error message returned from Database Server that contains information about the structure of the database.
- In some cases, Error-based alone is enough for a hacker to list database properties.
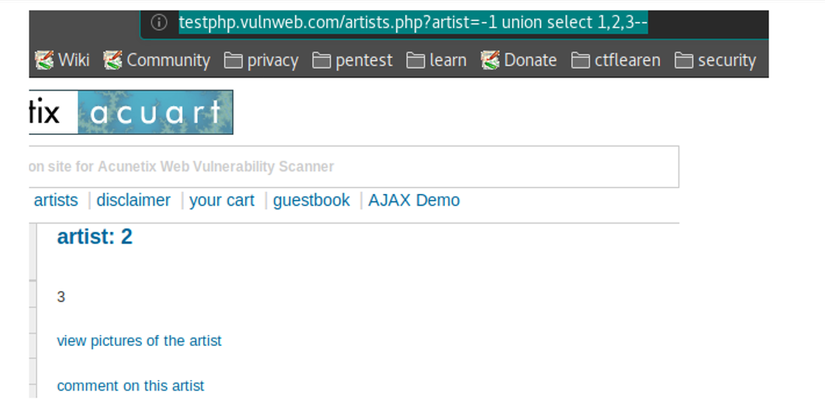
Union-based SQLi
- An SQL injection attack technique based on the power of the UNION operator in the SQL language that allows to sum the results of two or more SELECTION queries in the same result and be returned as part of the HTTP response
Inferential SQLi (Blind SQLi)
- Unlike In-band SQLi, Inferential SQL Injection takes longer to attack because no data is actually returned via the web application and hackers cannot track the results directly. In-band attack
- Instead, an attacker will try to rebuild the database structure by sending payloads, based on the results of web application responses and the results of database server behavior.
- There are 2 main types of attacks
- Blind-boolean-based
- Blind-time-based SQLi
Blind-boolean-based
- An SQL injection attack technique that relies on sending queries to a database that forces the application to return different results depending on whether the query is True or False.
- Depending on the result of the query, the HTTP reponse may change, or stay the same
- This type of attack is often slow (especially for large databases) because the attacker needs to list each data, or search for each character.

Time-based Blind SQLi
- Time-base Blind SQLi is an attack technique that relies on sending queries to a database and forcing the database to wait a certain amount of time (usually in seconds) before responding.
- Response time (immediate or delayed according to the time interval set) allows an attacker to guess whether the query result is TRUE or FALSE
- This type of attack is also time-consuming similar to Boolean-based SQLi
SQLi Out-of-band
- Out-of-band SQLi is not a common attack, mainly because it depends on the features enabled on the Database Server used by Web Application.
- This type of attack occurs when a hacker cannot directly attack and collect results directly on the same channel (In-band SQLi), and especially the response from the server is unstable.
- This type of attack depends on the server’s ability to make DNS or HTTP requests to transfer data to the attacker.
- For example, the xp_dirtree command on Microsoft SQL Server can be used to make DNS requests to another server controlled by an attacker, or Oracle Database’s UTL HTTP Package can be used to send HTTP requests from SQL and PL / SQL. to the server owned by the attacker
summary
SQL Injection is a familiar concept but still ranked in the top of the common web security vulnerabilities according to OWASP standard. In this article, I have mentioned the basic concept as well as how to distinguish the types of SQL Injection attacks that I have learned. People can rely on the keywords that they have mentioned above to further research as well as demos for each type. Wishing everyone success
