1. Introduction
- Address Space Layout Randomization (ASLR) – Randomizing the address space map is a security technique used in operating systems, first deployed in 2001. Current versions of all Common operating systems (such as iOS, Android, Windows, macOS and Linux) all have ASLR.
- ASLR was first introduced as a patch for the Linux kernel, its goal is to randomly segment memory, helping to avoid being used by malicious programs.
- Before explaining what is ASLR, we need to learn about virtual memory.
2. A quick overview of Virtual Memory
- Virtual memory is a technique that allows processing of a process that is not fully loaded into physical memory.
- Virtual memory models the memory as a very large and homogeneous storage table, clearly separating the concept of address space and physical space. Users only see and work in the virtual address space, the transition to physical space performed by the operating system with the help of specific hardware mechanisms.
- Virtual memory allows an application program to think that it has a continuous range of memory (an address space), when actually this portion of memory can be fragmented in physical memory and even Can be stored both in hard disk.
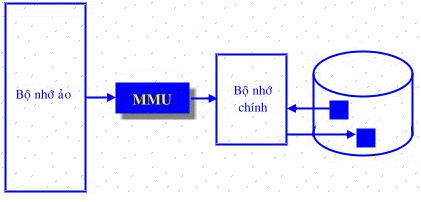
- Virtual memory makes it easier and safer for programs to manage their memory. Programs don’t need to worry about where other programs are storing data or how much RAM is left. This program is not allowed to view a memory of another program.
3. What is ASLR?
- ASLR is a defensive technique by randomizing the memory addresses of processes, attempting to prevent attacks through the location of applications memory maps. To increase the security of the system, instead of removing the vulnerability with open source tools, ASLR makes it more difficult to exploit existing vulnerabilities.
- In general, applications should be compiled with ASLR support. This feature has gradually become the default, and has been applied to versions Android 5.0 and above.
4. Configure ASLR on Linux
- Use either of the following 2 commands to check if your system is running ASLR.
1 2 3 4 5 | $ cat /proc/sys/kernel/randomize_va_space 2 $ sysctl -a --pattern randomize kernel.randomize_va_space = 2 |
- The meaning of the returned values is as follows:
0 = Disabled
1 = Conservative Randomization
2 = Full Randomization
- If you turn off ASLR, then run the following commands, the addresses shown in the output are exactly the same in successive ldd commands.
- ldd: see the libraries used for an application on Linux, load shared objects and show them where they end up in memory
Disable ASLR:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# sysctl -w kernel.randomize_va_space=0 kernel.randomize_va_space = 0 <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# ldd /bin/bash linux-vdso.so.1 (0x00007ffff7ffb000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007ffff7891000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff768d000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff729c000) /lib64/ld-linux-x86-64.so.2 (0x00007ffff7dd5000) <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# ldd /bin/bash linux-vdso.so.1 (0x00007ffff7ffb000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007ffff7891000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007ffff768d000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007ffff729c000) /lib64/ld-linux-x86-64.so.2 (0x00007ffff7dd5000) |
- If you set the parameter’s value to 2 to enable ASLR, the addresses will be different after you run the command.
Enable ASLR:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# sysctl -w kernel.randomize_va_space=2 kernel.randomize_va_space = 2 <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# ldd /bin/bash linux-vdso.so.1 (0x00007ffc349b0000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007f76d26db000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f76d24d7000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f76d20e6000) /lib64/ld-linux-x86-64.so.2 (0x00007f76d2c1f000) <a class="__cf_email__" href="/cdn-cgi/l/email-protection">[email protected]</a> :~# ldd /bin/bash linux-vdso.so.1 (0x00007ffebb689000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007f7e30c36000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f7e30a32000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f7e30641000) /lib64/ld-linux-x86-64.so.2 (0x00007f7e3117a000) |
5. ASLR minimizes buffer overflow attacks
- ASLR increases the integrity of the control flow of a system, making buffer overflow attacks harder to succeed by randomizing the offsets it uses in allocating memory locations.
 The address space of the programs is randomly changed
The address space of the programs is randomly changed - In order to perform buffer overflow attacks, an attacker needs to prepare as much junk data as possible, then a malicious playload. This payload will overwrite the data that the program intends to access.
- Buffer overflows requires the attacker to know the location of each part of the program in memory. The process of finding this exact location is difficult because there are many times to try and many errors will occur. Once determined, the attacker must create a payload and find a suitable place to inject it. If an attacker doesn’t know where the target code is located, then another declaration will become difficult or even impossible.
- ASLR works in conjunction with virtual memory management to randomly position each of the different parts of a program in memory. Every time the program is run, components (including the stack, heap, and libraries)) will be moved to another address in virtual memory. Attackers can no longer know where their targets are, because the address will be different each time.
- ASLR works significantly better on 64 bit systems, because these systems provide a much larger number of entropy (potential random location).
5. Limitations of ASLR
Although ASLR makes exploiting system vulnerabilities more difficult, its ability to protect the system is still limited:
- Do not solve the vulnerabilities
- Can’t track or report vulnerabilities
- Does not provide any protection for binaries not built with ASLR support
References
https://www.howtogeek.com/278056/what-is-aslr-and-how-does-it-keep-your-computer-secure/ https://www.networkworld.com/article/3331199/what- does-aslr-do-for-linux.html

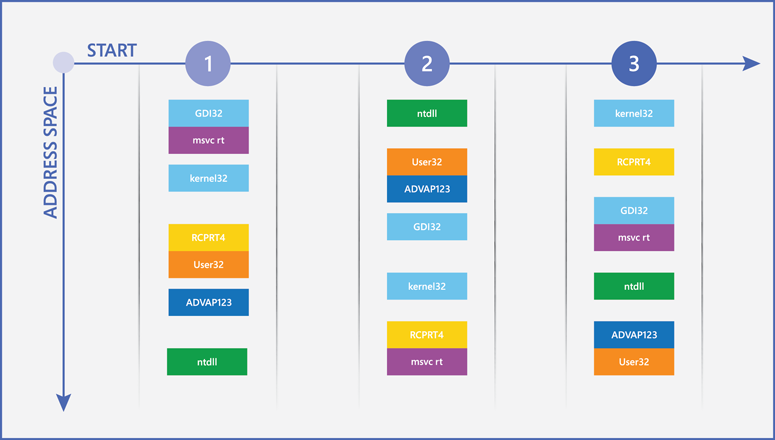 The address space of the programs is randomly changed
The address space of the programs is randomly changed