1. Virtual Private Cloud (VPC)
VPCs are the foundation of all EC2 cloud servers, in other words, when you use EC2, cloud computing, virtual machines provided by Amazon, you are using VPC.
Each Virtual Private Cloud is an independent part of the AWS cloud, it is like your own virtual network and you have full control over this environment, including:
- Defining subnets (subnet)
- Defining IP range for server (IPv4 and IPv6)
- Control access to and from the server.
Structure of VPC:
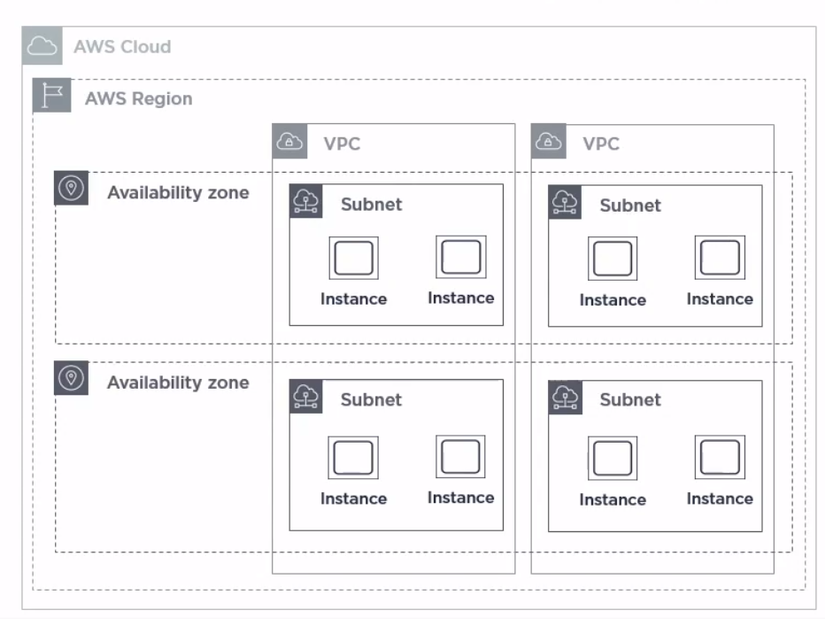
- VPC belongs to the Region and it will span all the Availability Zones in that Region
- In a Region there are many VPCs
- VPC can have one or more Subnet
- Each Subnet will be associated with 1 Availability Zones
- Each Cloud Server will be running on a certain Subnet
When you create an AWS account, Amazon creates a default VPC for each Region. This allows you to deploy a virtual machine for EC2 without configuring too complex. This default setting is very effective in the case of simple applications that do not require a lot of subnets or control over the intended IP ranges.
These default VPCs will have one Subnet available for each AZ, making it ready to deploy EC2 immediately. As the system grows, you can customize this default VPC or create new VPCs depending on your needs.
The VPC provided by AWS is guaranteed because it is built on a huge network infrastructure, where AZs and between AZs in the same Region are a separate AWS network (Private AWS Ntwork). ) with large scale and throughput. The AZs are designed so that the latency becomes extremely low, as if it is operated from a centralized place.
2. Control the outgoing and incoming VPC (Ingress and Egress Control)
VPC has very different ways to control its incoming and outgoing traffic
- Security Group (acting as a virtual firewall) is a very common way to specify which threads are allowed to go in and out of the VPC. Here we will specify some factors such as port (port), protocol (protocol), source and destination.
- Network access control lists (NACL) are also used to specify rules that allow or deny access to subnet entries. We can define a NACL and then link one or more subnets to that NACL.
- VPC can also be connected to VPC through peering . We can do this with VPC in the same or different accounts, in the same or other regions
- VPC is accessible via VPN.
- We can specify a Route Table in VPC to control outbound and outbound subnet traffic.
- An Internet Gateway can be attached to VPC to allow it to be accessed with external Internet.
- If a Private Subnet wants to access external Internet, we can use a NAT Gateway.
- VPC flow logs are used to record information about all access to the network, whether approved or denied access.
3. Example of basic working structure model of VPC
All VPCs are connected to the Internet
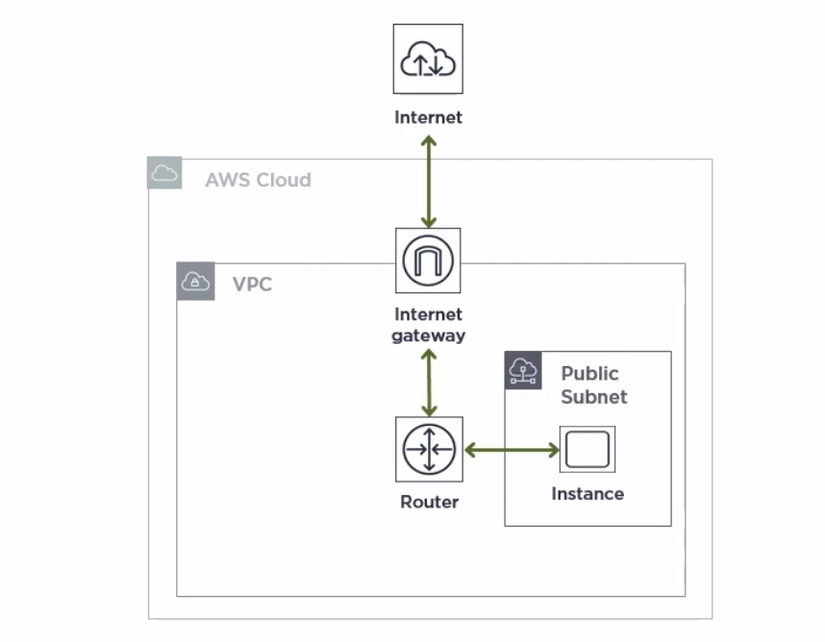
The VPC connects to a Public Subnet, that is, the cloud server in that VPC must have a Public IP address.
All cloud servers here will be connected to the Internet, so we need to install an Internet Gateway for this VPC, this will allow VPC to connect to the external Internet.
In addition, we also need to route a router.
In this structure, due to exposure to the external Internet, we need to pay attention to security. Therefore, we need to install a Security Group (acting as a virtual firewall) to avoid cloud server exposure to unnecessary risks.
Security Groups will include rules and regulations to regulate access to and from VPC.
Your VPCs will be required to assign one or more Security Groups, if you do not actively assign any of them, the VPC will be assigned with the default Security Group (made available by AWS for each default VPC).
This architecture is suitable for testing, development and in systems where all cloud servers require external access.
Reference source :
https://app.pluralsight.com/library/courses/aws-network-design-getting-started
