Static source code analysis technique
Static code analysis (also known as Source Code Analysis) is usually done as part of software penetration testing. This source code analysis step will be performed at the deployment stage of the Security Development Lifecycle (SDL). This is a method of finding software security vulnerabilities without running the software (dynamic analysis). To analyze static source code, we often use a combination of two methods:
- Manual analysis: Perform manual source code reading and review to find security vulnerabilities. This is done through reading and checking for dangerous entry points that exist in the design document, functional description, or code lines of the application.
- Tooling Analysis: Static source analysis often refers to running static code analysis tools to try to find out the “security weaknesses” that exist in software using techniques like Taint. Analysis and Data Flow Analysis. Ideally, such tools will automatically find security holes with a high degree of reliability. However, this is out of the modern state for many types of application security flaws. As a result, such tools often serve as a helper for an analyst to help them exploit pieces of code related to security so they can find flaws more efficiently, rather than a tool that simply automatically finds vulnerabilities.
Benefits of parsing static source code
- Static testing techniques can start early in the software development lifecycle, so errors can be detected at an early stage.
- With early fault detection, the cost for error correction is reduced.
- Due to the reduced cost of repairs and rework, product development productivity also increases.
- Static testing helps to raise awareness of product quality problems
- In short, the static test method is a very suitable method for improving the quality of software products
The following article will use manual analysis to find SQL Injection errors in WordPress Plugins through regex technique to find out the code that is at risk of SQLi security vulnerability.
Introducing the WordPress Plugin
A plugin is a piece of software that contains a group of functions that can be added to a WordPress website. They can extend functionality or add new features to your WordPress sites. WordPress plugins are written in the PHP programming language and fully integrated with WordPress. In the WordPress community, there is a saying that best demonstrates the role of the plugin: “there is a plugin for that function”. They make it easy for users to add features to their website without knowing a single line of code
There are thousands of free WordPress plugins in the official WordPress plugin directory. At WPBeginner, we write about all of the best WordPress plugins. We even shared a list of all the plugins we use.
In addition to free plugins, there are plenty of great commercial plugins available from third-party companies and developers. Because it is software, it still has potential security vulnerabilities such as: SQL Injection, Cross Site Scripting (XSS), Cross-Site Request Forgery (CSRF) …
Source code analysis
SQL injection – also known as SQLi – uses flaws in website input channels to target databases located in web application backend, where sensitive information is stored. Most valuable and appreciated. They can be used by an attacker to steal or tamper with data, interfere with application performance, and, in the worst case, it can gain administrative access to the server. database. Here’s what you need to know about SQL injection and how to protect your website from them.
SQL Injection occurs when the user input is not filtered for escape characters and is then passed on to an SQL statement. This results in the end users of the application being able to manipulate the statements executed on the database. The SQL statement is constructed by performing “concatenated” before it is passed to the function to execute the SQL statement. It is very dangerous when user input and unprocessed data is passed directly to the SQL query through string concatenation.
Examples of vulnerabilities through the use of string concatenation in an SQL query:
1 2 3 4 5 6 7 8 9 10 11 | <span class="token comment">// The user we want to find.</span> String email <span class="token operator">=</span> <span class="token variable">$_REQUEST</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'email'</span> <span class="token punctuation">]</span> Connection conn <span class="token operator">=</span> DriverManager <span class="token punctuation">.</span> <span class="token function">getConnection</span> <span class="token punctuation">(</span> <span class="token constant">URL</span> <span class="token punctuation">,</span> <span class="token constant">USER</span> <span class="token punctuation">,</span> <span class="token constant">PASS</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> Statement stmt <span class="token operator">=</span> conn <span class="token punctuation">.</span> <span class="token function">createStatement</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> String sql <span class="token operator">=</span> <span class="token double-quoted-string string">"SELECT * FROM users WHERE email = '"</span> <span class="token operator">+</span> email <span class="token operator">+</span> <span class="token double-quoted-string string">"'"</span> <span class="token punctuation">;</span> ResultSet results <span class="token operator">=</span> stmt <span class="token punctuation">.</span> <span class="token function">executeQuery</span> <span class="token punctuation">(</span> sql <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">while</span> <span class="token punctuation">(</span> results <span class="token punctuation">.</span> <span class="token function">next</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token comment">// ...oh look, we got hacked.</span> <span class="token punctuation">}</span> |
In this example, the email variable is received directly from the user’s request. This variable is then passed in via concatenation: “email = '" + email + "'";”
This causes an SQL Injection error when the above query is executed.
Next, we will use regex to find the same error codes in WordPress Plugins:
(?<!prepare)(('|")SELECT.+FROM.+('|").*..*
This Regex will find all SELECT queries in the Plugin without using prepare. Because the prepare () function is a library function in WordPress used to protect queries against SQL Injection attacks. Example: wpdb::prepare( string $query, mixed $args )
Here I use VSCode to grep: 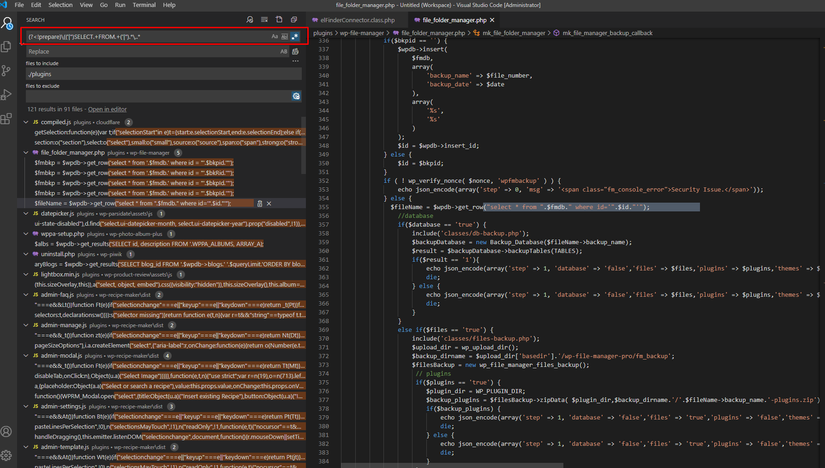
Some real results
Use regex (?<!prepare)(('|")SELECT.+FROM.+('|").*..* to find the error:
1. Official MailerLite Sign Up Forms <1.4.4 – Unauthenticated SQL Injection
Error code:
File: mailerlite-admin.php
1 2 3 4 5 | <span class="token variable">$form</span> <span class="token operator">=</span> <span class="token variable">$wpdb</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">get_row</span> <span class="token punctuation">(</span> <span class="token double-quoted-string string">"SELECT * FROM "</span> <span class="token punctuation">.</span> <span class="token variable">$wpdb</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token property">base_prefix</span> <span class="token punctuation">.</span> <span class="token double-quoted-string string">"mailerlite_forms WHERE id = "</span> <span class="token punctuation">.</span> <span class="token variable">$_POST</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'form_id'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
Proof of Concept The “form_id” parameter presents a risk of SQL Injeciton crashing.
$_POST['form_id'] is used directly in the SQL query through string concatenation. This causes an SQL Injection error
Reference https://wpvulndb.com/vulnerabilities/10235
2. SQL injection in the AdRotate 5.8.3.1 for WordPress exists via param “id”
Error code:
1 2 | <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token keyword">isset</span> <span class="token punctuation">(</span> <span class="token variable">$_GET</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'id'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token variable">$id</span> <span class="token operator">=</span> <span class="token function">esc_attr</span> <span class="token punctuation">(</span> <span class="token variable">$_GET</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'id'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
Faulty parameter $_GET['id'] receives input directly from the user. Then this parameter is passed directly to the underlying SQL query and causes the error:
1 2 | <span class="token variable">$stats</span> <span class="token operator">=</span> <span class="token variable">$wpdb</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token function">get_results</span> <span class="token punctuation">(</span> <span class="token double-quoted-string string">"SELECT * FROM ' <span class="token interpolation"><span class="token punctuation">{</span> <span class="token variable">$wpdb</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token property">prefix</span> <span class="token punctuation">}</span></span> adrotate_stats' WHERE 'ad' = <span class="token interpolation"><span class="token punctuation">{</span> <span class="token variable">$id</span> <span class="token punctuation">}</span></span> ORDER BY 'id' ASC;"</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
Proof of Concept:
Param "id" is vulneable to SQL Injeciton.
Example:
Use boolean-base to extract database information.
http://example.com/wp-admin/admin.php?page=adrotate-statistics&view=group&id=2+AND+1%3D(SELECT+IF+(+GREATEST(+ORD(MID(%40%40version%2C+1%2C+1))%2C+1)+%3D+53%2C+1%2C+0))
The query that checks the MySQL version is “5” or not.
Other vulnerabilities are exploited by Sun * Cyber Security Team
- Blog2Social: Social Media Auto Post & Scheduler <6.3.1 – Authenticated SQL Injection:
- Form Maker by 10Web <1.13.36 – Authenticated SQL Injection:
- Photo Gallery by 10Web <1.5.55 – Unauthenticated SQL Injection:
Conclude
This is a method of manual static source code analysis, although there are still many limitations because manual code reading takes a long time, the amount of code that needs review is very large. However, according to the initial assessment, this is a fairly effective and highly efficient approach. Localizing the error points makes finding errors simple and focusing on the right target (Because there are thousands of different WordPress). These are just a few methods used to find errors, we need to combine dynamic analysis methods to perform error checking and exploit to get the best results.
In the near future, Sun * Cyber Security team plans to release a static source code analysis tool to increase productivity in finding errors as well as helping to reduce manual work.
Reference
The article is referenced and built based on a paper of the team puclic on exploit-db (Public Website of the exploit codes). Original article at: https://www.exploit-db.com/docs/48583
