In this article, I will summarize some ways on how to find out the real IP address of a server behind CloudFlare services, both to support people during the pentesting process as well as to the System Admin. know how to misconfig yourself leading to true IP leaks to prevent. First I will talk about the CloudFlare system
What is cloudflare?
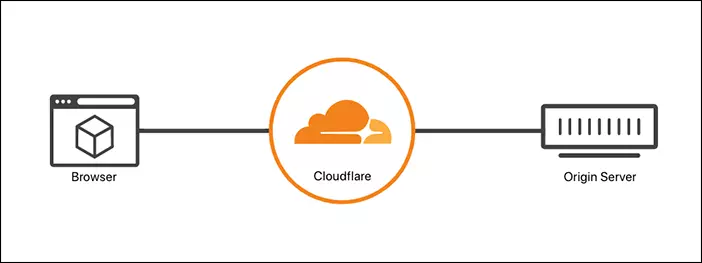
The simplest to understand is that CloudFlare is a service that will stand between Client and Server with domain name resolution (DNS) function plus traffic coordination, CDN as well as security solutions against Ddos, Spam. , SSL, Forward Domain, ..
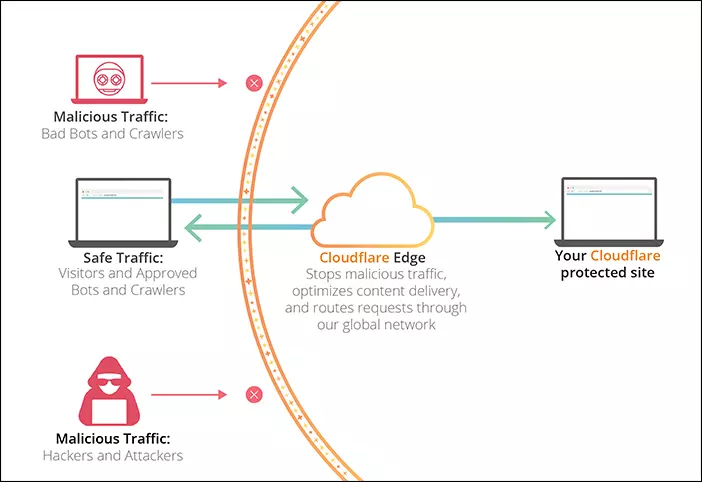
Then for a pentester, when a pentest website uses CloudFlare service, all requests must go through CloudFlare and from there it will be sent to the server so the payload will usually be removed before reaching the server.
Surely you also wonder how can force users to connect to CDN Server instead of directly to the real server. Then the CDN has the main solution is to re-declare the Name Server records of the domain website. That is, normally the Name Server is usually the Hosting Provider or Domain Registrar, but when using CloudFlare, the Name Server will be the CloudFlare and from there the DNS requests of the user will be resolved by CloudFlare Name Server instead of Registra Name Server.
Methods of finding IP
First to distinguish whether the real IP or CloudFlare IP is on the homepage of the service that provides CloudFlare IP range at: https://www.cloudflare.com/ips/
Method 1: PING
Ping to some subdomains like:
ping direct-connect.domain.com
ping direct.domain.com
ping ftp.domain.com
ping cpanel.domain.com
Nping mail.domain.com
Because in some cases the subdomains are configured to point A record to the server’s real IP. If, in the case of ping, the time out message is likely that the server is blocking ICMP requests, use the following nmap command:
nmap -sV -sS -F <domain>
where: -F: scan popular ports -Ss: determine if the port is open -sV: determine the service and version
Method 2: HISTORY
Find the IP history of websites that have been cracked by a bot before setting up CloudFlare: http://toolbar.netcraft.com/site_report?url= <domain> or on https://securitytrails.com/
https://sitereport.netcraft.com/?url=
Method 3: NMAP ENUM
Bruteforce / guessing subdomains with nmap
nmap --script dns-brute -sn <target>
Method 4: NSLOOKUP
In some cases, the web and mail server are on the same server, finding the real IP will be much easier because the MX records must resolve to the real IP of the mail server, so the MX record must be set to Real IP. In this case we will use nslookup and just ping or scan the IP is out
1 2 3 4 | nslookup > set type=MX > <domain> |
Method 5: SSL CERTIFICATE
In another case, suppose your web site supports SSL and has a certificate. But the problem here is that the Certificate used for Client – CloudFlare is shared by CloudFlare – Server. For this case you need:
Visit https://censys.io/certificates
Search parsed.names: <domain> and tags.raw: trusted syntax parsed.names: <domain> and tags.raw: trusted
Censys will scan and display the certificates with the above criteria and the next thing you will need to do is click through each search too.
Select “Explore” on the right -> What’s using this certificate? > IPv4 Hosts.
Then you will see the list of IPs using the certificate above, the possibility that the IP will be on the web server’s IP
Method 6: MALICIOUS UPLOAD
Method of Uploading an optional image to the website For this way the condition is that the website allows uploading images from the website or an external link.
First, go to http://iplogger.org/ and click “Generate an invisible IPLogger”
Now, copy the link and go to the page where you need to get its IP, create an account. Then go to change the Avatar or upload photos from the URL. Paste the copied link above
At this point, the system will download the image and upload it to its server, so the IP that accesses that image is the server’s IP. Now go back to the previous page, click View Log to see the access log. The result is like this.
Compare :
https://www.secjuice.com/finding-real-ips-of-origin-servers-behind-cloudflare-or-tor/
https://vpssim.vn/3533-tim-ip-cua-website-su-dung-dich-vu-cloudflare-de-ip.html
