The story of hackers that brought down an entire nation’s internet
- Tram Ho
Kaye’s story shows just how devastating a cyber attack can be and urges cyber security to find a way to deal with it.
In October 2016, more than half a million security cameras around the world simultaneously connected to several servers being used by Lonestar Cell MTN, a mobile operator in Liberia, Africa. Not long after that, Lonestar’s network was flooded and overloaded. Internet access for 1.5 million customers of this network was slowed down and eventually stopped.
The technique used in this attack is DDoS, or distributed denial of service. Simple but effective, a DDoS attack uses an army of hijacked and controlled machines, also known as botnets, to simultaneously connect to a single online point.
For Liberia alone, one of Africa’s poorest countries, this botnet is one of the largest botnets they have ever faced. While most DDoS attacks last for only a moment, the attack on Lonestar takes place over several days.
And since the civil war ended in 2003, Liberia had absolutely no land line, half of the country was cut off from services like online banking, and farmers could not make phone calls. to ask for the price of farm produce, and students can’t look up Google. In the capital Monrovia, their largest hospital also lost its connection for a week. Infectious disease specialists are dealing with the Ebola outbreak that cannot contact other international health care agencies.
Not long after that, the attack began to spread.
By November 27, the German telecommunications company Deutsche Telekom AG began receiving tens of thousands of calls from customers who were angry at the failure of their internet service. Even the computer system in a water plant has lost its connection and they have to have a technician come down to check each pump manually.
By this time, Deutsche Telekom discovered a huge botnet, similar to the attack in Liberia, that was damaging their routers. The company quickly deployed a bug-fix software in just a few days, but the sheer scale of the attack caused a security researcher to think it was Russian or Chinese action.
Until the botnet knocked out dozens of websites of two British banks, the British Crime Service, and the German BKA (Federal Crime Police Office), with support from the US FBI, shook hands. into investigating the case. German police discovered a username, linked to an email and a Skype account, as well as a Facebook page belonging to a man named Daniel Kaye, a 29-year-old British citizen who grew up in Israel and considered himself a freelance security researcher.
On the morning of February 22, 2017, Kaye was arrested by British police while checking in at London’s Luton Airport to prepare to fly to Cyprus. Searching him, the police discovered a pile of $ 100 bills worth about $ 10,000 hidden in him. But contrary to many people’s predictions, this is not a Russian spy or a criminal boss.
The court indictment and police reports about Kaye interrogations show that Kaye was just a mercenary and a weak man with a history of severe diabetes.
Born in London, Kaye followed her mother when she was 6 years old to her parents after divorcing. By the age of 14, being diagnosed with diabetes made Kaye limit contact with the outside world, but the young man found a wider world on the internet.
He learns the code himself, devours the exercises he finds, and regularly participates in web forums about his ability to exploit security holes with the nickname “spy [d] ir”. In 2002 appeared the first trophy of spy [d] ir with screenshots showing the website of an Egyptian engineering company deface with the words: ” Hacked by spy [d] ir! LOL! This was too Easy . ” Over the next four years, a series of websites in the Middle East experienced similar attacks.
Also at this time, Kaye graduated from high school and decided to drop out of college to choose freelance programming. A smart but easily depressed person, Kaye does not seem to fit the business life like any ordinary employee. Often awkward when interacting with others, Kaye’s way of answering questions also made him appear to be hiding something.
Even in 2011, Kaye went to the final interview of a major cybersecurity company, RSA Security LLC, but was later rejected due to concerns from the human resources department. In his 20s, it was time for Kaye to focus entirely on freelancing with individual clients who knew him through hacking forums or word of mouth.
Shortly thereafter, in 2012, he moved to London with the girlfriend he had just proposed. A former university administrator, she wanted to continue her career in the UK, while Kaye wanted a new start.
By 2014, Kaye had heard from a friend of an entrepreneur offering a freelance job to someone proficient in hacking techniques in Israel. This friend introduced Kaye to a successful businessman named Avi who is looking for help with cybersecurity. At the time, this entrepreneur was having a business in Liberia – and the story began.
This Avi businessman, or Avishai “Avi” Marziano, was then the CEO of Cellcom, the second-largest telecommunications operator Liberia. Founded in 2004, the network has grown steadily for many years thanks to a series of powerful marketing campaigns, such as giving motorcycles to the winners, sponsoring beauty contests, as well as constantly. attack their number one opponent – operator Lonestar – in the commercials.
But despite those efforts, Cellcom’s market share remains stagnant at number two in the Liberia market. Although the business narrowed in 2014 due to the Ebola epidemic, the CEO of Cellcom declared that the development period was over, now it was time to take the throne. His plan began by meeting Kaye. When he could not defeat his opponents in the marketplace, he would use another method to defeat them.
One of Kaye’s first tasks was to preserve the system for a sister company of Cellcom in neighboring Guinea. With his tool, Kaye encrypts all Cellcom’s data to protect it from political upheaval. As a result, Kaye was paid $ 50,000 by Marziano and thousands of dollars in prize money for each test. But the next mission is not so benevolent.
Marziano ordered Kaye to hack into Lonestar’s network to look for evidence of bribery or other illegal activities. Unable to find anything unusual in Lonestar’s system, Kaye downloaded the entire customer database of the network and sent it to Marziano – this is the true purpose of this mission. It allows Cellcom to send invitations to network customers. But that is not enough.
In 2015, Kaye and Marziano discussed how to attack DDoS and slow down Lonestar’s internet service to convince customers to switch networks. A real technical challenge. It is not easy to DDoS a large network like Lonestar even with Liberia’s weak internet infrastructure.
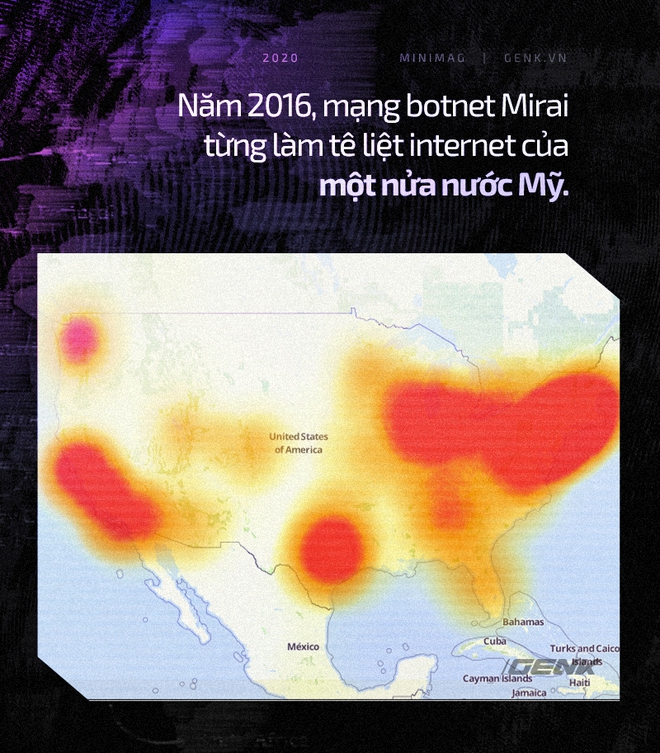
By 2016, luck is smiling at this duo. Cellcom was acquired by the giant French network, Orange, in January 2016 and Marziano was retained as CEO. But Kaye’s luck comes from another event. In 2016, the global internet exploded because of a notorious malware called Mirai. Mirai spreads through webcams, wireless routers, and other poor security devices to create the largest botnet ever recorded and used it to attack DDoS on Minecraft gamers.
Based on the Mirai code that was shared on the hacker forum, Kaye – now leisurely on Cyprus – had the godsend tool she was looking for. By tweaking the code in it, Kaye can target Chinese security cameras, which are poorly secured and prevent other types of Mirai from taking control of their botnets.
Excited by the power of the botnet Kaye owns, Marziano agreed to pay him $ 10,000 per month to use this “project”. Now is the time to embark on Marziano’s plan.
Liberia’s weak internet infrastructure has only one undersea fiber optic cable to connect to the outside world. Facing half a million machines and sending data back, Lonestar’s server quickly stopped working. Between October 2016 and February 2017, Kaye continuously attacked at least 266 more times. Every time the attack took place, half of the African country, which was Lonestar’s customer, fell out of touch.
Cellcom’s long-standing statement about being the fastest carrier in Liberia has come true. It is difficult to describe Marziano’s satisfaction. He even captured the title of the article with the headline ” Paralyzed by cyber attacks: Liberia beseech the US, UK “, to send to Kaye.
Contrary to Marziano’s joy, Kaye began to feel danger when there were signs that many security researchers were paying attention to this attack, due to its similarity to the notorious malware Mirai.
Shortly thereafter, Kaye’s botnet began to lose control and spread to Germany. Malicious devices are constantly looking for new devices, forcing them to download malware. So they collapsed the Deutsche Telekom routers when they refused to join the botnet – an unexpected loss of attack, as Kaye later confessed. And so the German police force began to play. At this moment, Kaye was truly scared.
To distract the investigation from his attacks in Liberia, Kaye decided to share the botnet – or in other words, take them for hire to others – to be paid with Bitcoin (from 2,000 USD to 20,000 USD depending on scale). While many customers are gamers, wanting to use it to attack opponents, many other customers are more ambitious.
A moniker, “Ibrham Sahil”, took advantage of this botnet for ransom attacks. As a result, the websites of Lloyds Bank Plc and Barclays Bank Plc – two major lenders in the UK – were knocked out by dozens of DDoS attacks, because they refused to pay according to the attackers’ threats. To curb the attacks and maintain the website, each bank had to spend about 150,000 pounds – the same amount that the attacker demanded each bank.
These attacks ended only when Marcus Hutchins, a British security researcher, groped the server to control the attack and contacted its controller, someone with the code name “Popopret” – a special Other names of Kaye.
In addition to posting evidence of the aftermath of the cyber attack, Hutchins also warned that intelligence agencies would be involved because the banking system was considered a critical infrastructure of the country. At this time, the attacks on new banks stopped. The attacks on Liberia continue.
A few weeks later, Kaye flew from Cyprus to London to see Marziano and receive the prize money for herself. Both brought their families to the meeting. (It seems that their families are unaware of the illegal deeds of this twin beetle.) In a way, the quirky duo has become friends with each other rather than the usual business relationship.
Receiving $ 10,000 in cash from Marziano, Kaye went to Luton Airport to board a plane to Cyprus. This is where the British police picked up and caught Kaye while doing the procedures.
At first Kaye of course denied it all. It was only when he was extradited to Germany and the BKA cryptography room cracked Kaye’s cell phone, found WhatsApp messages between Kaye and Marziano, photos of the types of security cameras used in the botnet that attacked Liberia. , as well as a video showing someone manipulating the huge botnet that caused the attack, Kaye admitted.
For a year and a half later, there was a time of debate between Kaye’s legal team and the prosecutors. During that time, Kaye had to pay bail so that she would not have to go to jail and be kept under house arrest of her father and not leave England.
Kaye was sentenced on January 11, 2019 at the Blackfriars Crown court in South London. Escaping from criminal prosecution, Kaye’s cyber attack in Liberia is seen only as an ” offensive behavior promoted by financial interests into a legitimate business .” Finally, Kaye was sentenced to 32 months in prison without parole.
As for Marziano, he was arrested by British police in August 2017, not long after Kaye appeared in the courtroom in London. But he was soon released without any charges. In 2017, he also left the Orange Cellcom Joint Venture and cut off all communications since. Even his ex-wife didn’t know where Marziano was going.
In 2018, the carrier Lonestar Cell filed a lawsuit against Orange and Cellcom in London over allegations of cyberattacks. Both carriers issued a statement denying the allegations and said they were neither aware of Marziano’s activities nor benefited from the attacks.
In Liberia, many people believe that the attacks on Lonestar are politically motivated, not economic. The chairman of Lonestar during that time was Benoni Urey, the head of the All Liberian Party, who ran for president in 2017. Meanwhile, Cellcom always publicly supported one of Urey’s rivals, the former General Sirleaf system, who was in power in this country from 2006 to 2018.
In early 2020, Kaye will be released. By then, he will face restrictions on the use of phones, computers and security software, though he hopes to continue working on cybersecurity. Until then, he was still groping vegetables in Belmarsh’s kitchen, the highest-security prison that kept murderers, rapists, and terrorists.
Source : Techtalk