1. What is pentest?
- Pentest (Penetration Testing) is a form of testing whether your IT system can be hacked, by simulating the generated test attacks.
- A process of reviewing services and systems to look for potential security problems or trace traces when a system is compromised.
- The person performing an intrusion test is called the intrusion test or Pentester.
- This action is allowed by the HT administrator or the authorized person in the system.
- To accomplish the pentest work – testers use business measures, find ways to get into and IT systems or websites. The ultimate goal will be to control the system, data or as high as possible it is to take control of the system.
- Final purpose: the found flaw will be reported back to the administrator or application developer so they can fix it.
2. What items are in pentest?
- Network evaluation
- Assess network structure, network devices, IPS / IDS system
- Security measures are established
- Review server system
- Windown & ubunutu server
- Version reviews, configuration updates, patches, security policies, logs
- Redundancy, load balancing, and database capabilities
- Review web application
- Using specialized tools to test, leak scanning holes
- Internal review: KT source code, data verification class, ql session
3. The method in pentest
- Black box
- The attack will be executed without any info
- Pentester will put itself in the position of black hat hackers and try every means to penetrate customers’ systems.
- Pentester will simulate a real attack on the system.
- White box
- Internal and external network information will be provided by the customer and Pentester will assess network security based on that.
- Gray box
- Assuming a hacker is provided with a normal user account and proceeds to attack the system as an employee of the enterprise.
4. The phase in pentest
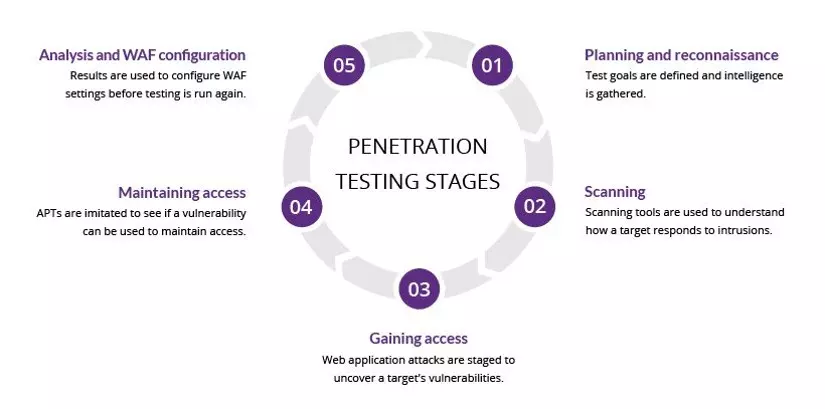
Introducing Web Application Penetration Testing 2018 (OWASP)
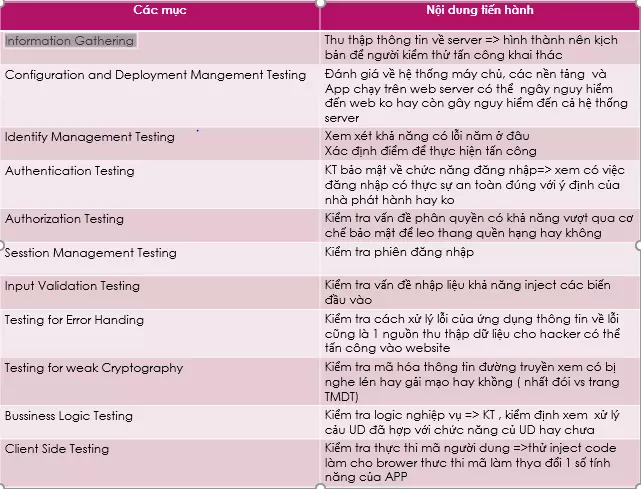
- Information Gathering
- Configuration and Deployment Mangement Testing
- Identify Management Testing
- Authentication Testing
- Authorization Testing
- Sesstion Management Testing
- Input Validation Testing
- Testing for Error Handing
- Testing for weak Cryptography
- Bussiness Logic Testing
- Client Side Testing

1: Information Gathering
- This pentester will collect information about the object as well as information about the server running the application such as application version, framework, webserver, operating system, …
- This step is very important, as it has identified a lot of information related to the application that will facilitate the attack and exploit the appropriate scenario to attack.
- As identified by the WebServer, the attacker version of the pentester could exploit webserver-related errors regardless of whether the application is running safely or not.
2: Configuration and Deployment Mangement Testing
- Evaluate the server system, what platforms are running on it. It is possible that the web application has absolutely no holes, but the platform that runs the application has an error.
- For example, like the operating system, the web server has a bug, this can completely harm not only the web application but the whole server.
- Need to check the configuration for the application, mainly by the developer test. Test forms are whitebox and graybox.
3: Identify Management Testing
- Identify the possibility of an error. Determine which points to execute the attack.
- Check how the account is created in the application. Logical handling and User rights
4: Authentication Testing
- Login mode is common in applications, if the system administrator will have control of the application. It is therefore very important to check the security with the login function.
- Check login credentials, use techniques to bypass authentication and escalate privileges. Does the user management policy of the app work properly like the logout function, or requires strong passwords, etc.
5: Authorization Testing
- After logging into the system. checks whether the logic is sufficient and correct for the user who is logged in. The ability to bypass security mechanisms to escalate privileges.
- For example: Imagine user1 and user2 are two different users. If user1 user can access user2 user resources on the server to read the confidential private information of user2. This is extremely dangerous so the allocation of resources for each target group and its own object is very important. Checking
6: Sesstion Management Testing
- Check the login session.
- One of the core components of any web-based application is the mechanism by which it controls and maintains the state for users to interact with it. This is called Session Management and is defined as a collection of all controls that govern the state-wide interaction between users and web-based applications.

7: Input Validation Testing
- Execute the ability to inject input variables into these input variables.
- For this step we will try to execute SQL Injection, Cross Site Scripting (XSS), File Include, etc. For dangerous errors that can cause an administrator to lose control of the website even the Server.

8: Testing for Error Handing
- Check out how to handle application errors
- Examining how the application handles errors is of utmost importance. The application does not always run as intended by the programmer, or the non-cooperative user provides unwanted data.
- Error information is also a source of data for pentester attacks that can attack a website.
- At such times, the application should have a processing mechanism so that it does not encounter the natural phenomenon of rolling to death and the administrator does not often die when and why it dies.
9: Testing for weak Cryptography
- Check how the application encrypts information on the line
- For commercial websites, electronic transactions, the protection of data on the transmission line is very very important.
- From user accounts to transaction information all need to be kept confidential on the line. This part is to check whether the encryption part and the encryption level of the application is secure.

10: Bussiness Logic Testing
- Check the application’s business logic. For example, does the sales website handle the logic for invoices.
- Each application has its own function so the logic of each application is different. This test is to determine whether the application’s processing matches the application’s logic and functionality.
11: Client Side Testing
- Check code execution on user machines.
- The response received from the server will be displayed to the user brower. In addition to html code, there is also JavaScript code.
- If possible inject special code into javascript this response will cause the browser to execute code that changes some features of the application.
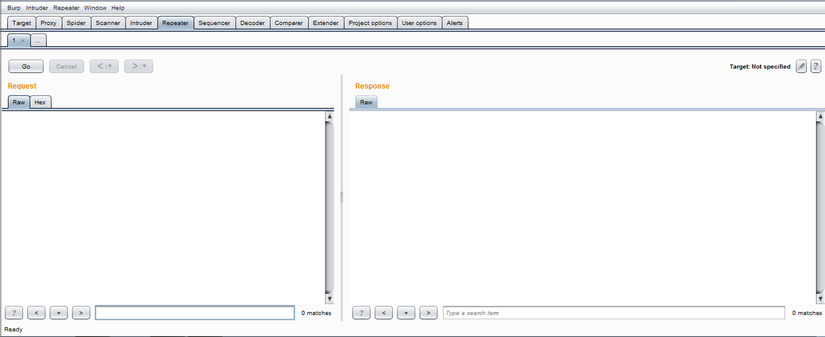
5. Burp Suite
- What is burpsuite?
- Burp Suite is a security vulnerability scanning toolkit for web applications.
- Burp Suite is an integrated platform for securing web applications security. Diverse tools work together to support the entire testing process, from initial mapping to finding and exploiting security vulnerabilities.
- Main functions BurpSuite
- Interception Proxy: It acts as a web proxy server and lies in the middle position between the browser and the destination web server. It allows blocking, checking and modifying traffic flowing through both directions.
- Scanner (Pro version only): Automatically scans vulnerabilities in web applications (XSS, SQLi, Command Injection, File Inclusion, …).
- Repeater: allows to modify the request content quickly.
- Intruder: This tool can perform automated attacks on web applications, automating the sending of payloads to the server.
- Decoder: decode and encode string in different formats (URL, Base64, HTML, …).
- Comparer: shows the difference between requests / responses
- Extender: API to extend the function of Burp Suite. You can download the extensions through the Bapp Store.
- Spider & Discover Content: crawl links, automatically browse to determine the “site map” structure of a web page.

 Interception Proxy: It acts as a web proxy server and lies in the middle position between the browser and the destination web server. It allows blocking, checking and modifying traffic flowing through both directions.
Interception Proxy: It acts as a web proxy server and lies in the middle position between the browser and the destination web server. It allows blocking, checking and modifying traffic flowing through both directions.  Intruder: This tool can perform automated attacks on web applications, automating the sending of payloads to the server.
Intruder: This tool can perform automated attacks on web applications, automating the sending of payloads to the server.  Scanner (Pro version only): automatically scans vulnerabilities in web applications (XSS, SQLi, Command Injection, File Inclusion, …).
Scanner (Pro version only): automatically scans vulnerabilities in web applications (XSS, SQLi, Command Injection, File Inclusion, …). 


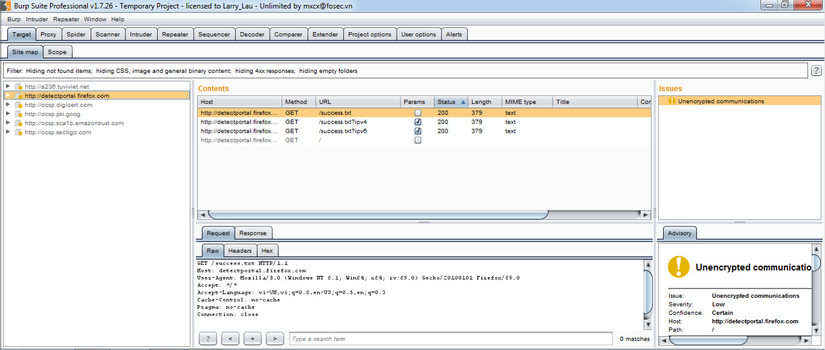
 Interception Proxy: It acts as a web proxy server and lies in the middle position between the browser and the destination web server. It allows blocking, checking and modifying traffic flowing through both directions.
Interception Proxy: It acts as a web proxy server and lies in the middle position between the browser and the destination web server. It allows blocking, checking and modifying traffic flowing through both directions. 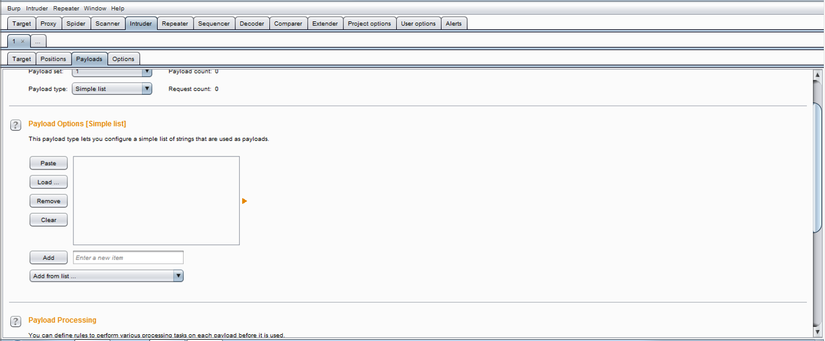 Intruder: This tool can perform automated attacks on web applications, automating the sending of payloads to the server.
Intruder: This tool can perform automated attacks on web applications, automating the sending of payloads to the server. 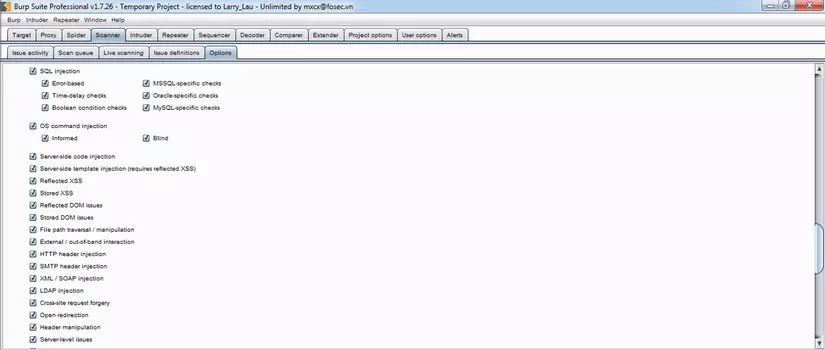 Scanner (Pro version only): automatically scans vulnerabilities in web applications (XSS, SQLi, Command Injection, File Inclusion, …).
Scanner (Pro version only): automatically scans vulnerabilities in web applications (XSS, SQLi, Command Injection, File Inclusion, …).