In the era of technology and digital boom, cybersecurity has become a concern for almost every organization, service provider, … Although this is a rather difficult problem. solutions but many measures have been introduced to improve security and protect network systems.
This article will introduce two techniques that are quite familiar to international organizations but relatively new in Vietnam called “Penetration Testing” and “Vulnerability Assessment” (Evaluation security holes). The content of this article will also show the differences of the two above techniques, because in general in many places these two concepts are being used with equivalent ideas.
What is Vulnerability Assessment (VA)?
VA is a technique of identifying, discovery and quantitative measurement (scanning) security vulnerabilities in a given system environment. This is an in-depth, comprehensive assessment method for the entire information security system (result analysis).
Furthermore, it identifies vulnerabilities (potentially targeted attacks) as well as provides remediation methods necessary to be able to remove those weaknesses or at least reduce their risk level to an acceptable level.
The diagram below is an image description for the VA technique:
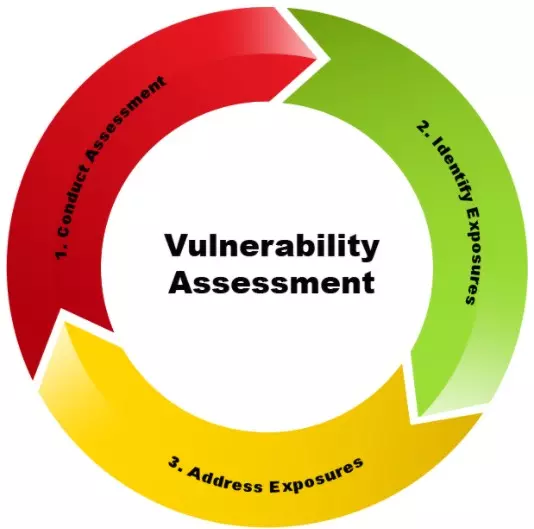
What is Penetration Testing (PenTest)?
Performing penetration testing (PA) simulates the actions of cybercriminals, such as disrupting information security, stealing valuable data, and disrupting the operation of an organization.
Using a wide variety of innovative tools and technologies, testers working with PenTest (with the permission of the organization) will try to fully exploit the system and seek access to sensitive information. cold.
Differences of 2 techniques
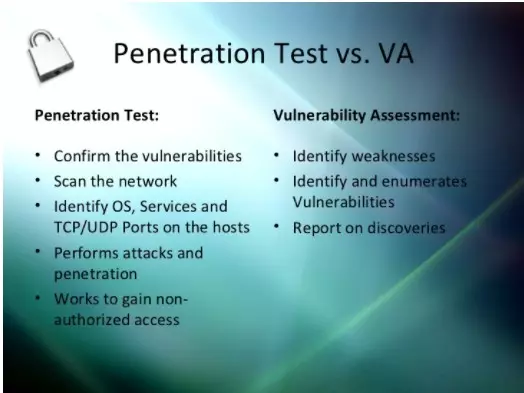
1. Language difference
Language is also important, and the existence of these two concepts shows that their differences are valid. But without a clear demarcation, users do not understand exactly the definitions, should we use these two concepts together to refer to security testing techniques at the same time? Obviously differences exist, but those are points that need further analysis to shape.
2. The difference in the definitions of the two concepts
The VA is designed to define a hierarchical list of system vulnerabilities that prioritize the vulnerabilities and weaknesses of the system, usually to cater to customers who already understand they are in a threatened state. potential concerns and they certainly don’t want to. They know they are in trouble and they simply need to perform well formulated testing to correctly identify these vulnerabilities and, importantly, assess the importance of fixing each. That gap.
The more problems that are identified, the better. For that reason, the implementation of this technique should use as much whitebox testing technique as possible. The final product of the testing phase is a list of vulnerabilities sorted by priority found during testing, and also suggesting ways to alleviate those problems.
Speaking of PenTest, it is designed to achieve a specific purpose: to simulate the behavior of a cybercriminal and require permission, requests from customers who already have a network. solid security system. A typical example might be asking a tester to break in and retrieve information about loyal customers in an internal database or edit an employee’s record in the HR system.
Which method to exploit more thoroughly?
A mistake when comparing these two concepts that one might make is which technique is more effectively exploited? Many opinions said: “Finding vulnerabilities is implementing VA and exploiting these vulnerabilities is PenTest’s job”. This opinion is completely incorrect.
The extraction can be imagined as a slider between zero and full, which can be leveraged in both VA and PenTest computation evaluations. While most critical penetration tests are more visually oriented than descriptive (i.e., exploit-heavy), there is also a case of proving that a vulnerability is real without an exploit. Thorough waterfall. A penetration test team can simply take a picture of standing next to an open safe or show they have full access to the database etc … without actually taking the complete action. that an offender can commit. And a vulnerability assessment (VA) can also follow this process for any of the subgroups in the list of problems detected.
This may take real time, but by definition, exploitation does not get you out of vulnerability, attack on vulnerabilities. The only important and unique properties of VA compared to PT are the category orientation and the target type orientation, and the exploitation problem is not part of that calculation.
Penetration Tests includes Vulnerability Assessments?
To say that PenTest always includes VA is also inaccurate!
PenTest is a technique towards achieving an end goal. That means if you reach that goal, you have done an excellent job. Well then, you would probably do some VA to find a vulnerability then use it to do PenTest, but finding this vulnerability only takes a very little time. So when you find a hole to attack, you have reached the goal, what about the remaining holes? Will you take the time to find and evaluate it again?
In other words, PenTest is precisely dependent on finding one or more vulnerabilities in order to exploit them and that people often use a certain process to systematically find vulnerabilities. For the purpose of implementing PenTest but because they will stop when they get what they want and not give the customer a list of all the weaknesses, security gaps in the system, which are the best. In the process of doing PenTest, they do not actually implement a full VA procedure.
The following summary will show the fundamental differences between these two techniques
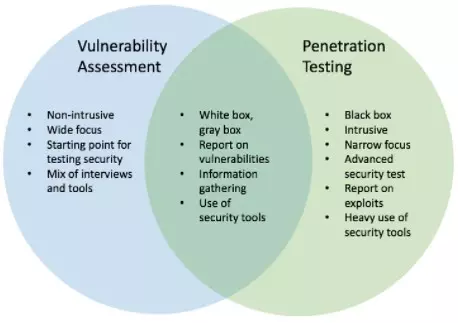
1. Penetration Testing
- Determine the scope of the attack.
- The test collects sensitive information.
- Collect target information and / or investigate the system.
- Clean the system and synthesize the report.
- Having performed environmental assessment analysis, creating documents, but not studying the system in-depth.
- Ideal for network architecture and physical environment.
- Applicable to critical real-time systems.
- Often times customers believe their system is very stable and they want to check how secure it is.
- Exploit in depth rather than width.
2. Vulnerability Assessments
- Create a directory listing the assets and resources in a system.
- Discover potential threats to each resource.
- Allocate quantitative value and importance to available resources.
- Efforts to minimize or eliminate gaps and weaknesses of resources are potential targets for hackers.
- Comprehensive analytical study through system and environmental assessment.
- Ideal for laboratory environment.
- Applies to non-systems.
- Customers are people who have security problems and they need help resolving them.
- Exploit by breadth rather than depth.
So which technology option is the most ideal for deployment?
Both methods have different functions and approaches. Therefore, depending on the security status of the system, one chooses which method to apply. However, because of the fundamental differences mentioned above between PenTest and VA, we can see that VA offers more benefits than PenTest.
VA identifies weaknesses and offers solutions to fix them. On the other hand, PenTest only helps us to answer the question: “Can anyone break the security of the system and if so, what harm could he do?”
Furthermore, the vulnerability assessment is an effort to improve security protection systems and to develop a more integrated and robust security program. Meanwhile, PenTest can only show us a picture of the security system, which is somewhat working in consequence.
Thus, we can see from the above analysis, after seeing the fundamental differences between the two concepts, VA has more benefits and gives more practical results when compared with PenTest. But experts in the field have suggested that, as part of a security management system, both techniques should be done regularly to ensure a “perfectly” protected environment.
Translation and reference from source: https://www.tutorialspoint.com/penetrationtesting/ and https://danielmiessler.com/study/vulnerability-assessment-penetration-test/#gs.LD6zJc4
