Methods to detect holes
- Analysis of Deserialization vulnerability on PHP platform
- Magiac Method OOP has been significantly enhanced since PHP version 5, with the concepts of destructors, exceptions, interfaces, and so on. OOP allows packing data and functions into objects . Each class can be instantiated as an object, containing the properties and methods defined in the class. These properties are called attributes (or fields), while methods that describe a function are accessible to an object. Magic methods are special functions in PHP classes, the names of these functions have two underscores before them, they will be called implicitly at a specific event:
- __construct (): A magic method that inherits an initialization function inside a class and will be called whenever an object of a class is created. It is often used to initialize properties of an object or run other code before the object can actually be used.
- __destruct (): In contrast to the __construct () function, the __destruct () function will be executed when the object is destroyed. It is often used to call code that cleans up used data or terminates connections that can be established after the object is created.
- __call (): The function will always be called when the program calls a method that doesn’t exist in the object. It is very convenient in error handling, because accessing invalid methods often leads to serious errors and termination of PHP applications.
- __callStatic (): Equivalent to the __call () function, called when we call a static method that doesn’t exist in the object.
- __get ($ name): The __get () method is called automatically when reading the private, protected, or nonexistent properties of an object. Because private and protected properties cannot be accessed directly from outside the object, the $ name parameter is used to reference the desired property.
- __set ($ name, $ value): The __set () method is called automatically when trying to write to an object’s private, protected properties.
- __isset (): The __isset () method will be called when we check an attribute that is not accessible by an object, or check that an attribute does not exist in that object. Specifically, the isset () and empty () functions.
- __unset (): called when the unset () function used in an attribute is not allowed to access. Similar to isset function. When we unset an attribute that doesn’t exist, the __unset () method will be called.
- __sleep (): Called when serialize () an object. Normally when we serialize () an object, it will return all the properties in that object. But if we use __sleep (), we can specify the properties that can be returned.
- __wakeup (): In contrast to the __sleep () function, the __wakeup () method will be called directly after performing deserialization. It is often used to redefine the state of an application lost during serialization, such as connecting to a database.
- __toString (): Whenever an object is used in the string, this method is called to return a string representing the object (eg echo object).
- __invoke (): This method is called when we try to call an object as a function.
- __set_state (): Used when we call the function var_export an object. In an application, the var_export () function is used to display any type of data 10 in the form of PHP code that can be parsed. If an object is used as an argument, the __set_state () method is called to determine which attribute is exported.
- __clone (): Used when we copy an object into a completely new object unrelated to the old object.
- __debugInfo (): Called when we used the var_dump () function. Most of these functions will do nothing without the declaration and settings of the programmer. There are two Magic methods that we need to consider are __wakeup (), __destruct ().
- For example:
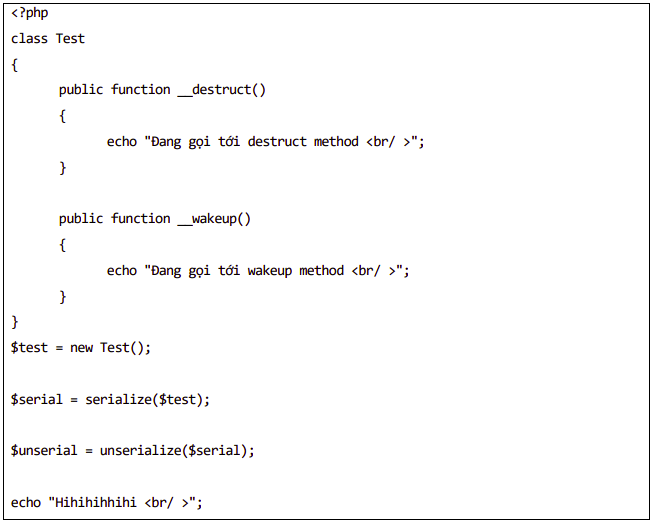
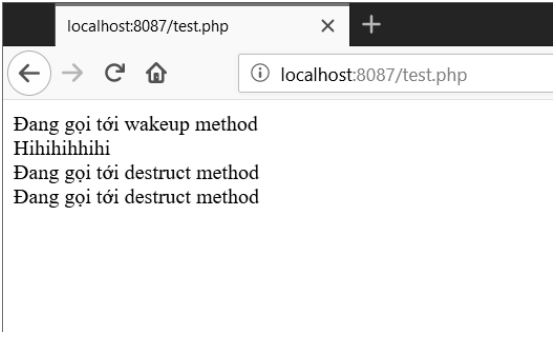
- We see that the __wakeup () function is called as soon as an object of the Test class is deserialized, and at the end of the above PHP script, the __destruct () function is also immediately called implicitly.
- Serialization in PHP
- The serialization process in PHP is supported via the serialize () function, and the deserialization process via the unserialize () function. The format of the string after performing serialization is as follows:
- a: Defines the parameter passed as an array. A is an integer value that specifies the size of the array.
- i: Define a numerical value.
- b: Define a boolean value.
- s: Defines a constant string, always followed by a numeric value declaring its length.
- S: Define a constant string in encoded format.
- O: Represents an object, by the length of the class name and class name. Then followed by the number of attributes and attributes defined. Note that an attribute can also include an object other than its defined properties.
- Example of serialization. In line 1, we have an array with 2 elements. On line 2, perform the serialization of the above array, the result is shown in line 4.
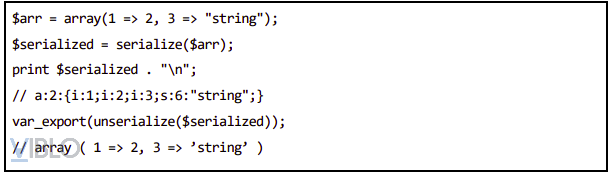
- After performing serialization, we get the following result:
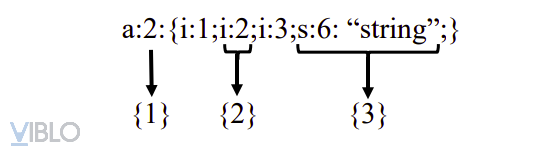
- {1}: Array has 2 elements.
- {2}: The first element has a numerical value of 2.
- {3}: The second element is a string “string” with a length of 6.
- For serialize arrays, a list of key-value pairs is contained in curly braces:

- To deserialize the object, there are two ways. The first method, serialize the properties of the object as an array. This mechanism uses O for identification.

- The character 0 above is NULL bytes. The private attribute has the prefix 0ClassName 0 and the protected attribute has the prefix 0 * 0.
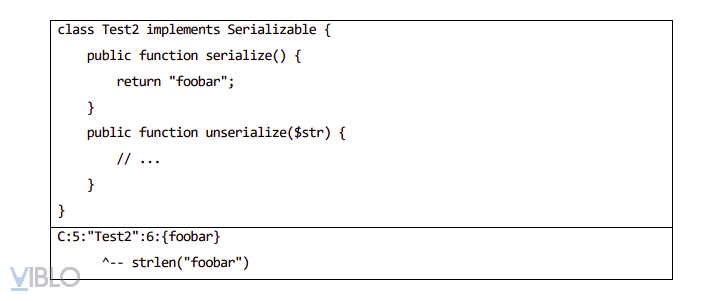
- The second way, serialize with custom format. Serializing implements the serialize method in serializable interfaces and uses C to define it.
- Deserialization attack in PHP
- Analysis of RCE Unserialize () vulnerability on vBulletin 5.xx
- Analysis of vulnerabilities Deserialize unsafe data on the vBulletin platform affects versions 5.xx. The level is extremely serious, an attacker can execute code remotely.
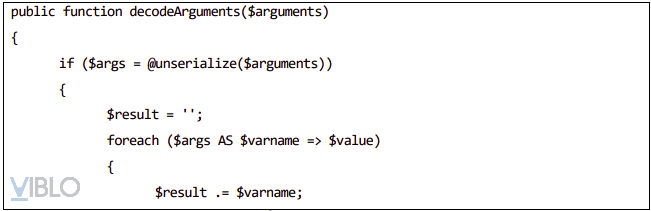
- The gap lies in the decodeArguments ($ argumentes) function.

- The decodeArguments () function takes input from the user who enters it and executes deserialize with the unserialize function.
- The rewind () function in the vB_dB_Result class. We can control the value of $ this-> recordset, to call the $ this-> db-> free_result () function.
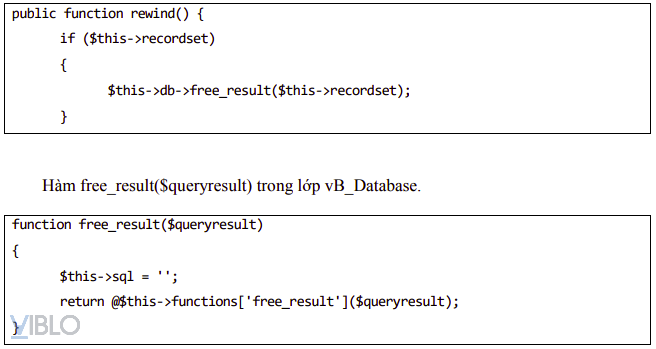
- The original value of $ this-> functions [‘free_result’] is mysql_free_result function. However, through the deserialize process, we can control the value of the functions [‘free_result’] to the desired value, for example, to the phpinfo function to display the php version information on the system.
- And here is the payload to generate PoC:
- Phar Deserialization vulnerability:
- The Phar file in PHP is similar to the Jar file in Java which is a format package that allows us to package multiple source files, libraries, images, etc. into one file. Structure of a Phar file includes:
- Stub: is a PHP file and must contain at least the following code: <? Php __HALT_COMPILER ();
- A manifest: a general description of the content that will be included in the file.
- The main content of the file.
- Signature: for integrity checking (this section is optional).
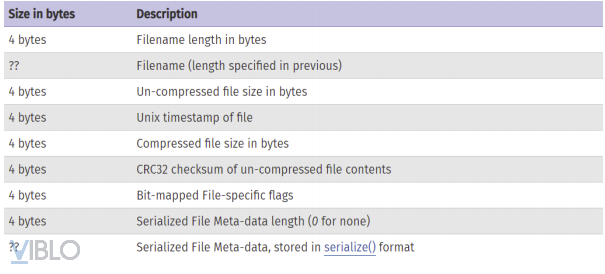
- The most noticeable point in the structure of a Phar file is the manifest, according to the PHP document, in each Phar file, the manifest holds the Meta-data that has been serialized. If there is a filesystem function that calls upon a Phar file, all of the above Meta-data will be automatically unserialized.
- The following is a list of filesystem functions that can be used to attack this vulnerability:
- To exploit this vulnerability, the following three conditions are required:
- Find the POP chain in the source code to be exploited.
- Put Phar file into the object to be exploited. 17
- Finding an entry point can send malicious code, which is where filesystem functions call the user-controlled Phar files.
- Detection method
- Black-box method:
- The black box test is a test method that tests the functionality of an application regardless of its internal structure / design or operation.
- For this vulnerability, it is often difficult to execute vulnerability attacks without the source code of the target application, but the vulnerability researchers came up with a PHPGCC tool including framwork and version. , where send payload. We can use this tool to conduct black box testing.
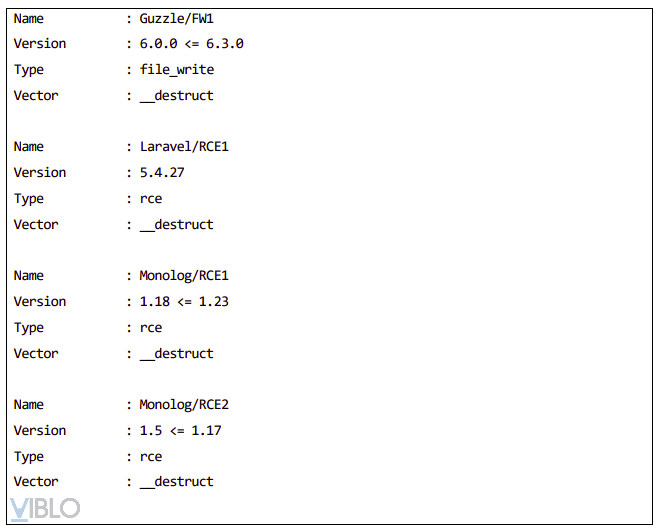
- PHPGCC is an extremely useful tool for creating payloads, having library gadgets, exploit frameworks available, and creating tools for platforms: Codelgniter4, Doctrine, Drupal, Guheads, Laravel, Magento, Monolog, Phalcon, Podio, Slim, SwiftMailer, WordPress, Yii and ZendFramwork.
- Use the Execute ./phpgcc -1 tool to display a list of gadget chains:
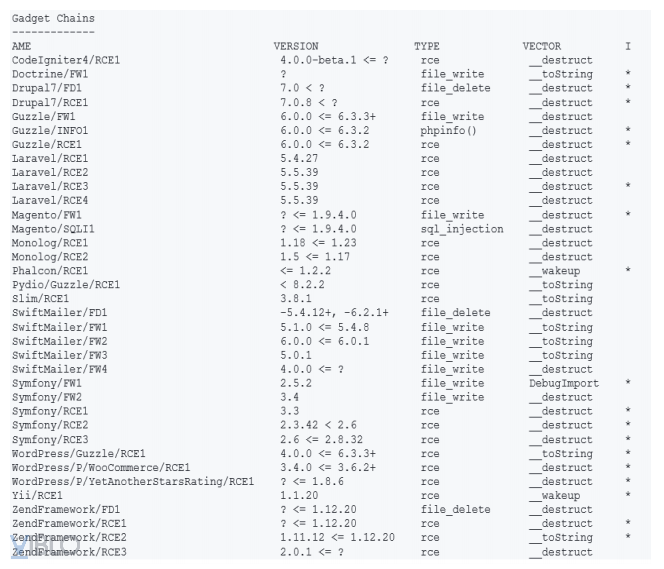
- Components in the utility chain:
- Name: Name of the library or framework.
- Version: The version of the framework or library used.
- Type: Type of exploit: Execute remote code, read file, write file …
- Vector: Magic method is used. 19
- I (Information): Other information about string.
- * Use -i for more information about strings:

- The syntax for creating payload is as follows: ./phpggc <gadget-chain> [parameters].
- For example, to create payloads for Monolog, the syntax is the same:

- Method white – box:
- White -box testing is a software testing method in which the design, internal algorithm structure and performance of the work are known by testing the logic of programme.
- White -box testing is a software testing method in which the design, internal algorithm structure and performance of the work are known by testing the logic of programme.
- Methods:
- Testing application programming interface – API testing. * Code coverage – Code coverage.
- Methods of error assignment.
- Conversion test methods.
- Static test
- With the white-box method, we will look in the source code for dangerous, improperly used functions such as unserialize (), file_exists (), file_get_contents () … or magic methods such as _detruct, _wakeup, _toString. We will use the white-box method through the examples containing the errors below:
- Example 1: Mining through __destruct method
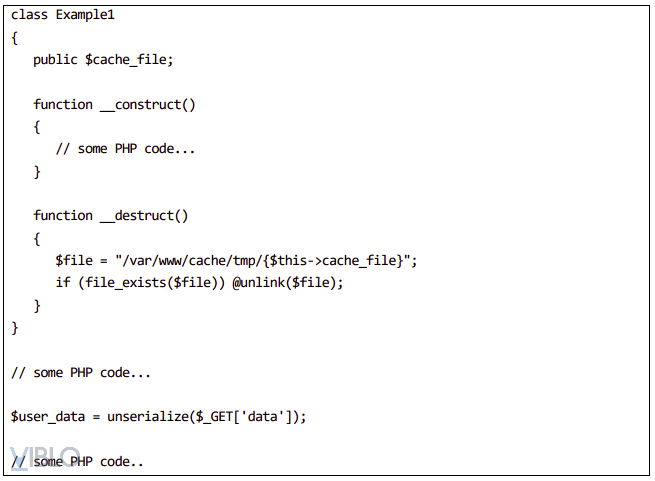
- Mining payload: http://testsite.com/vuln.php?data=O:8:”Example1″:1: {s: 10: “cache_file”; s: 15: “../../index. php “;}
- Example 2: Mining through the __wakeup method in the unserualize () function
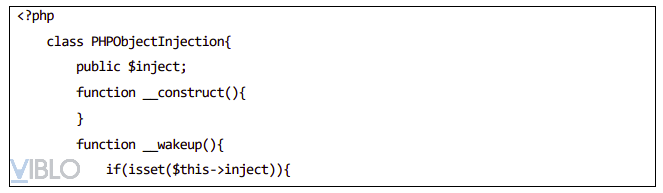
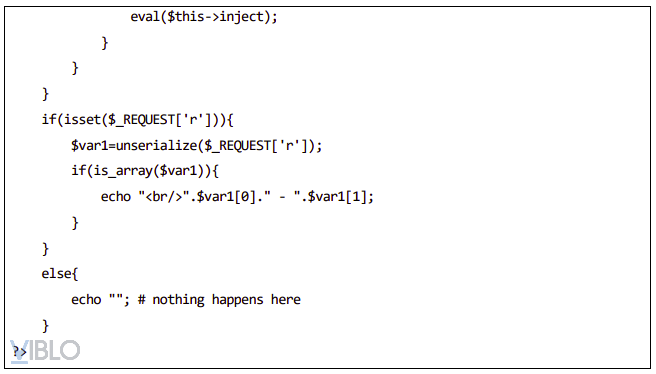
- Mining payload:
- Serialized data:
- a: 2: {i: 0; s: 4: “XVWA”; i: 1; s: 33: “Xtreme Vulnerable Web Application”;}
- Execute code: string (68) “O: 18:” PHPObjectInjection “: 1: {s: 6:” inject “; s: 17:” system (‘whoami’); “;}”
- Preventive methods
- Safe data deserialization:
- Do not accept objects that have been serialized from untrusted sources. This is essential in the application environment. By only allowing authorized users and processes to access your website. This is a measure to help reduce the likelihood of being exploited through the Deserialize vulnerability. This measure cannot be completely stopped because user accounts can be hacked and accessed through other malicious means.
- The serialize process should be encrypted to avoid the creation of malicious objects and fake data that can run in your system too. This measure will require some improvement in the system.
- Run code deserialization with limited access. If a malicious object has been serialized try to initiate a program in the system or gain unauthorized access to resources in the server. This object will be rejected, the system administrator will know and prevent malicious actions affecting the server.
- Tracking the serialize process helps capture malicious code. This method checks the serialized code in real time, and saves it in the log file, after the serialize process is complete. The log file will be analyzed, and malicious actions that are dangerous to the system will be detected and prevented.
- Validate user input. This is an important step when the input data is processed by the serialize process. Hackers can use objects like a cookie to insert dangerous data into the database to change user rights. Hackers, on the other hand, can also elevate their permissions to administrative rights by using a pre-existing hashed password or cached from the previous session. From there, hackers can run DDOS, execute malicious code remotely, or whatever the hacker wants from the server.
- Using the Web Application Firewall to detect malicious code and unsafe unauthorized Deserialization. A WAP (Web Application Firewall) can be a hardware device, or software or a filter that controls HTTP data flow to prevent predefined attacks such as SQL injection, XSS, Deserialization of data are not safe.
- Use non-standard data format When using non-standard data format, it will limit unsafe deserialization. Hackers will not know the methods used in the code. Use a special data format like JSON … * Update libraries, frameworks
- In older versions of frameworks, there were often serialize vulnerabilities, in newer updates, the developers had measures to fix this vulnerability. So if you want websites that don’t want to be hacked through this vulnerability, use the latest frameworks to build your website. Before using a framework to build a website, find out if this vulnerability occurs in this framework on OWASP. Find out how many versions of the framework occur when this vulnerability occurs, then find a way to fix the flaw or update the latest version of the framework.
- Below is a list of frameworks with the same version that detected the vulnerability