Let’s continue with these novel consensus. The article is only for introduction, so it will not go into analysis. Hopefully in the future there will be more detailed articles to send to readers near and far.

8. Delayed Proof-of-Work
Advantages
- Energy saving
- Increased security
Defect
- Only blockchains using PoW or PoS can be part of this consensus.
- When Notaries Active mode, we have to adjust the hashrate for different nodes (including normal and notary nodes), this section will be explained below.
Used
- Komodo
Type: Collaborative consensus.
Explain
Delayed Proof of Work (dPoW) is a hybrid consensus method that allows one blockchain to leverage the security of a second blockchain. This will be achieved through a group of notary nodes (also known as witness nodes), which add data from the first blockchain to the second.

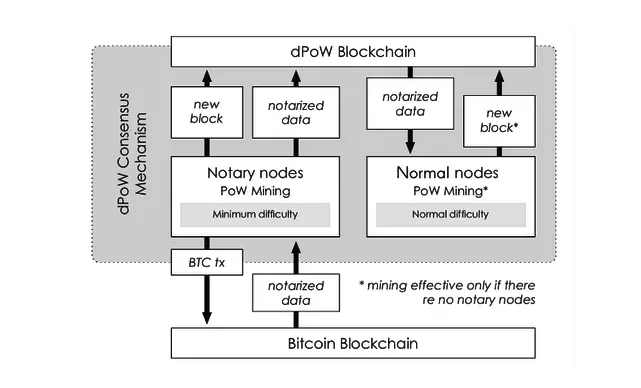
The dPoW-based blockchain can use either Proof of Work (PoW) or Proof of Stake (PoS) to work, or it can attach itself to any PoW-running blockchain desired. Bitcoin’s hashrate is currently the highest of any PoW blockchain. The illustration below shows the relationship between blockchains in dPoW:

There are 2 types of nodes in dPoW system that are notary nodes and normal nodes. There will be 64 notary nodes elected by the dPoW blockchain stakeholders to add (notarize) authenticated blocks from the dPoW blockchain to the PoW blockchain. Once a block has been completed, its hash is added to Bitcoin transactions signed by 33 notary nodes, creating a dPoW block hashes record on the Bitcoin blockchain, and they are also notarized by major groups of nodes in notary nodes
To prevent mining wars between notary nodes (which would reduce the efficiency of the network), Komodo used a Round-robin mining method that works with two modes. “No Notary” mode allows all nodes on mine blocks network, similar to traditional PoW mechanism; however, in “Notaries Active” mode , the notaries will be exploited one by one. In this scheme, by the way each notary is allowed to mine a block with the current difficulty level, while the other notary nodes have to mine at 10 times higher difficulty and all normal nodes will always mine with 100 times more difficult than the notary nodes. And this results in the hashrate of notary miners being different from normal miners.
The dPoW system is also designed to allow blockchain to continue operating without notary nodes. In such a situation, the dPoW blockchain could continue to function based on its original consensus method; however, it will no longer be the high security of the 2nd blockchain attached.
Delayed Proof of Work enables enhanced security and reduced energy usage for any blockchain that uses this consensus method. For example, since Komodo uses the Equihash hashing algorithm to prevent ASIC mining and relies on a round-robin mining method for notary nodes, this will reduce the likelihood of miners having to compete with each other, leading to distractions electricity charges and strong hardware purchases.
9. Proof of Capacity aka Proof of Space
Advantages
- Similar to PoW but uses space instead of computation. So much environmentally friendly.
- Can be used to detect malware, by determining if the processor L1 cache is empty.
- Can be used as anti-spam and anti-denial of service attack.
Defect
- Participants in the system get little profit.
Used
- Burstcoin, Chia, SpaceMint
Type: Collaborative consensus.
Explain
Proof-of-space (PoSpace) or also called Proof-of-capacity (PoC) is a method by allocating memory or disk space to solve the problem given by the service provider. . This concept was built by Dziembowski et al. in 2015.
Proof of Space is quite similar to Proof of Work, except that instead of using computation, it will store.
Proof-of-space is a piece of data that prover sends to another prover to verify that he has reserved a certain amount of space. One way to deploy PoSpace is to use hard-to-pebble graphs . A verifier will then ask the prover to label the hard-to-pebble graph. Prover will commits the labels. The verifier will then ask the prover to open some random positions in the commit.
Proof of Space is said to be a fairer, more economical solution than Proof of Work.
Document: Proof of Space
Proof of History
Use
- Solana
Explain
The idea here is that instead of trusting the transaction timestamp, we prove that the transaction happened before or after a certain event.
For example, when we take a photo with the cover of a magazine, it means we are creating evidence that our photo was taken after the newspaper was published. With Proof of History, you can create a “historical record” that proves that an event happened at a specific time.
That particular implementation is to use a hash function (SHA256) that runs continuously with the previous output used as the next input. Therefore, we can be sure that real time has passed
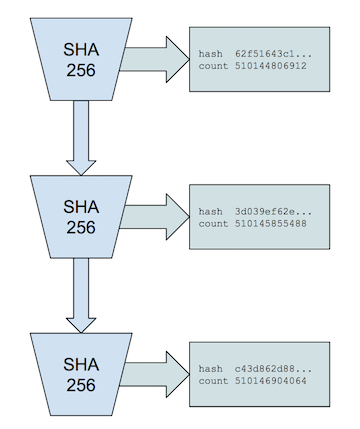
Document: Proof of History
10. Proof of Stake Velocity
Use
Explain
Proof of Stake Velocity (PoSV) is proposed as an alternative to Proof of Work (PoW) and Proof of Stake (PoS) to increase the security of the peer-to-peer network and confirm Reddcoin (a cryptocurrency) transactions. By nature they define the word velocity as velocity and are understood to be the rate at which money is exchanged in an economy. The higher the velocity, the more developed the economy is .PoSV is designed to encourage accumulation. store and exchange like real currency. In short, the more transactions that benefit users.
Document: Proof of Stake Velocity
11. Proof of Importance
Use
Explain
NEM’s consensus network is not only dependent on the number of coins, but also on paying for operations. When stacking the job chosen depends on many different factors, including the “popularity”, balance and the number of transactions made from that node. This is known as an important calculation (Importance calculation). It provides a broader view of a system member.
To be eligible for critical computation , that node needs to have at least 10,000 XEM in its balance. There are currently just under 9 billion XEM in circulation, achieving that goal is really not too difficult. It is possible that this 10,000 XEM threshold will change in the future, but for now, it remains the same. But the calculation of importance is done using a particular algorithm, not just by the probability and the amount they are staking.
The important thing to note about NEM’s proof of importance is that it is resistant to manipulation. Sybil and loop attacks are less likely to succeed using these basic mechanisms of consensus. Although it sounds like proof of stack but is rated on many more criteria.
Document: Proof of Importance
12. Proof of Burn
Use
- Slimcoin, TGCoin (Third Generation Coin)
Explain
Proof of Burn is essentially sending coins to an address where they cannot be recovered. This way you get the right to mine on the system and also rely on random selection.
Depending on how proof of burn is deployed, miners can burn coins of an existing blockchain or another blockchain like bitcoin. The more coins you burn, the more chances you have of being selected to mine the next block.
Over time, your rate in the system will decrease, so you will have to burn more coins to increase the rate you are selected for. (This process mimics the process of bitcoin mining, where you have to continuously invest in more modern computer equipment to maintain the hashing power.)
While this is an interesting alternative to Proof of work, it wastes unnecessary resources.
13. Proof Of Activity
Use
Explain
To avoid hyperinflation (what happens when there are too many coins on the system) bitcoin will only generate 21 million bitcoins. That means, at some point, the bitcoin block reward will end and bitcoin miners will only receive transaction fees.
Some have speculated this could cause security issues as everyone acts for the sake of their own self and crashes the system. Thus, proof of activity has been created as an alternative structure for the current bitcoin consensus. Proof of activity is a hybrid method combining both proof of work and proof of stack.
In Proof of activity, mining begins in the traditional proof of work style, with miners racing to solve a cryptographic puzzle. When the number of coins is no longer issued, the system switches to proof of stack. The more coins you own, the more likely you are to be chosen.
14. Proof of Time
Use
Explain
Proof of timing is introduced by Chronologic. They are planning to build a private blockchain. As stated by their main developer:
On the idea they created an Ethereum Alarm Clock Architecture described by two components: symbiotic and differential. The first component is the Ethereum Alarm Clock which is essentially smart contracts. They are deployed into the main Ethereum chain and work reliably. The second component is the TimeNode network . TimeNodes are the off-chain executables responsible for the logic processing of the executions.
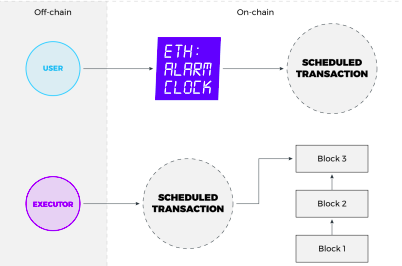
Document: Proof of Time
15. Proof of Existence
Use
- Poex.io
- HeroNode
- DragonChain
Explain
Proof of Existence is a service that verifies the existence of computer files at a specific point in time through timestamped transactions in the bitcoin blockchain.
It was launched in 2013 as an open source project. It was developed by Manuel Araoz and Esteban Ordano.
16. Ouroboros
Use
Explain
It is a variant of Proof-of-stake (with added security) used by Cardano.
Document: Ouroboros
17. Proof of Retrievability
Use
Explain
Proof of Retrievability (POR) is described as a method of proving the integrity of the file F downloaded by the client in the sense that the client can recover it. Because POR has lower transfer complexity than direct file transfer, it is an attractive solution for highly secure remote storage systems. It can be really useful as a consensus algorithm for Cloud systems.
Document: Proof of Retrievability
Reference
ConsensusPedia: An Encyclopedia of 30+ Consensus Algorithms
