In the current technological development era, ensuring information security in cyberspace is a matter of great concern. The risk of information insecurity is a major and growing threat to national security. There are many targets that hackers often target such as network service servers, network infrastructure systems.
In which website systems are quite popular targets due to the popularity and accessibility to hackers. Therefore, the security of the website is being focused on and places special requirements on testing.

1.1. Concept
Webserver : is a computer with internet connection installed with special programs to handle requests from users and respond to those requests. Web servers can process data and provide information to clients via personal computers on the Internet via HTTP protocol, a protocol designed to send files to a Web browser, and another protocol.
Request : can be understood as information sent from the client (client) to the server (server). When using the browser to access a certain address. For example, when accessing the google.com address, the browser will immediately rely on the domain name to send an access request to the IP address that this domain is pointing to, at which point the server side will analyze the request and will send the processing stream to the PHP source (or whatever source code) host location and the source’s job is to accept the request, parse the request and return the result back to the page client. web search found by the Google server.
Response : The data that the web server returns to the client. It can be a string of HTML or multimedia data such as pictures, videos … The client web browser will be responsible for processing and displaying these contents into a visual interface for the user.
Database : is a place to store the contents of a website. On the database, it is possible to store information about users’ accounts, passwords, emails …. Or even extremely important information like payment card information and medical records. So this is a popular hacker target.
Security vulnerabilities : are weaknesses in the system’s design and configuration, programmer’s error or operating negligence.
How basic Web vulnerability exploitation works: Hackers use scanning tools to detect a variety of websites with poor security configurations or websites on different platforms like “WordPress “Or” Joomla “has published vulnerabilities that have not been addressed yet. From there, Hackers will take advantage of them to attack, install malicious codes and sabotage websites for profit.
1.2. Web security vulnerability classification.
There are basically many different types of vulnerabilities and different subdivisions. Vulnerabilities can be classified according to the platforms or components that are vulnerable. Or divide by method of attack. The following are some of the vulnerabilities on the popular web applications and a lot of frequency and often in the “Top 10” of OWAP vulnerabilities:
1.2.1.SQL injection
Allows an attacker to take advantage of the vulnerability of checking input data and error messages returned by the database administrator to inject and execute illegal SQL commands.
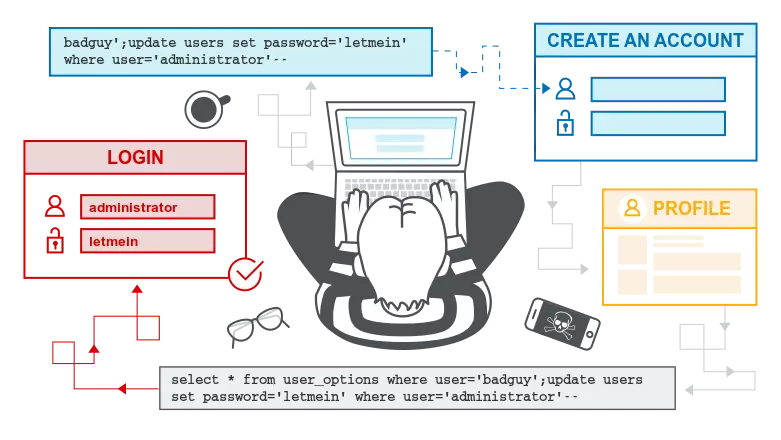
SQL Injection allows deletion, insert, update, etc. on the website’s database.
1.2.2. XML External Entity Processing
XML is an extensive, widely used markup language. It is used to exchange data between applications. Currently there are many types of documents using XML formats such as rtf, pdf, image file (svg) or configuration files.
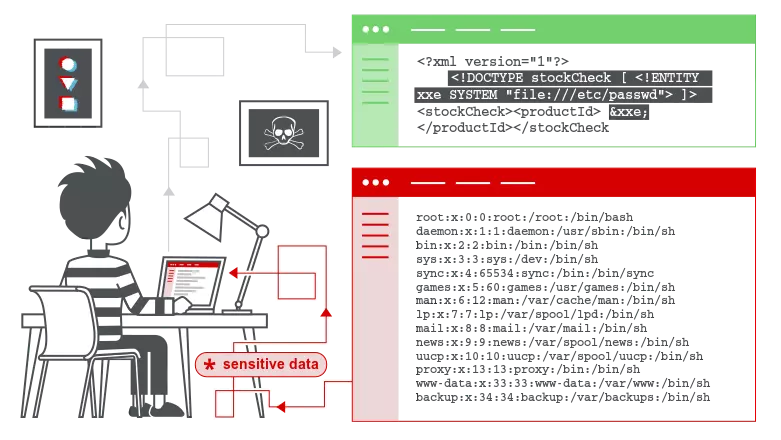
This attack technique is based on allowing the declaration of External Entity in the DTD part of XML data, the attacker can declare an entity to read the content of any file in the system if the parser XML (parser) is not well configured.
To avoid exploiting this vulnerability, it is necessary to configure the XML parser (parser), not to allow the use of the External Entity declaration in the DTD document stylesheet.
1.2.3. Cross Site Scripting (XSS)
Allow Hackers to insert malicious scripts (usually Javascript or HTML) into the website and execute it in the user’s browser.
An attacker can use XSS to send malicious scripts to any user to get cookies, keylogging or conduct phishing.
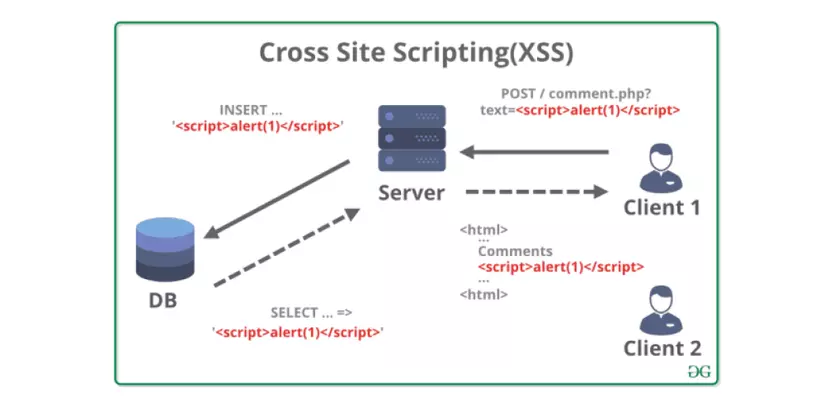
Also in some special cases, XSS vulnerability can also occur on the web server side. This often has serious consequences. The attacker can read sensitive files on the server.
1.2.4. Insecure Direct Object References
This is a typical case of assuming that what the user input is trustworthy, leading to a security vulnerability. This vulnerability occurs when the program allows the user to access resources (data, files, databases) without performing a permission control (or an incomplete process), resulting in Up to the attacker can gain illegal access to sensitive, sensitive data on the server.
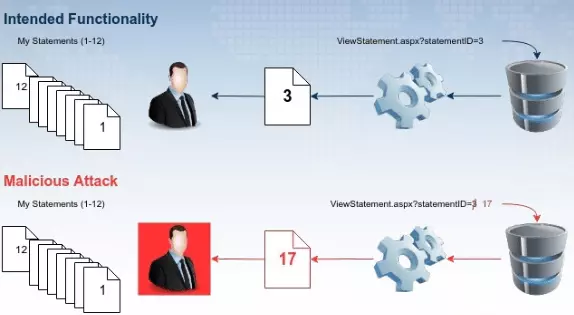
A piece of code has the module “download.php” and allows the user to download the file using the file name parameter to download the file from the server. For example “download.php? File = something.txt”. Due to developer error, the permission check was omitted. An attacker can use this vulnerability to download any file on the system that the application has access to. Such as application source code, sensitive files or other data on the server.
Another common example is a password reset function that relies on user input to determine a reset password. After clicking on the valid URL, an attacker can modify the username field in the URL to “impersonate” the administrator.
1.2.5. Sensitive data exposure
This vulnerability belongs to the resource management and encryption aspect. Sensitive data must be encrypted at all times, including when it is sent and when stored – no exceptions are allowed.
Credit card information and user passwords are never sent or stored unencrypted. In addition, web security standards suggest AES (256 bit or higher) and RSA (2048 bit or higher).
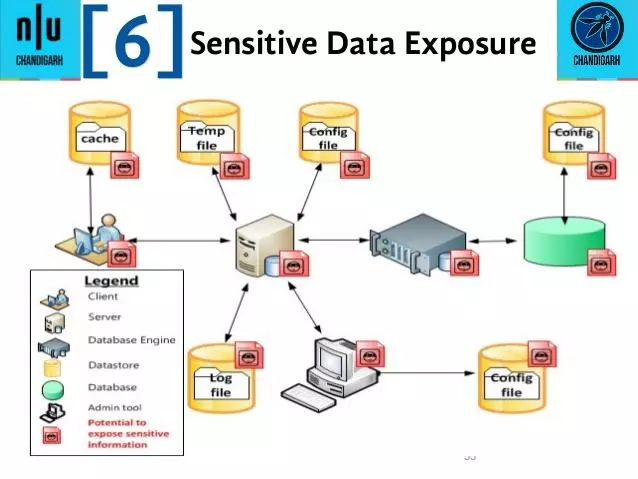
Disclosure of sensitive data can seriously affect the system, leaking high-value information that attackers can use this information to launch other dangerous attacks. more.
1.3. Techniques to exploit web security vulnerabilities
1.3.1. SQL Injection Attack
SQL Injection is one of the web attacks by injecting SQL query / command code into the data entry form before passing it to the web application for processing, which can be logged in without entering a username. and password and remote execution, data retrieval and administration of SQL server.
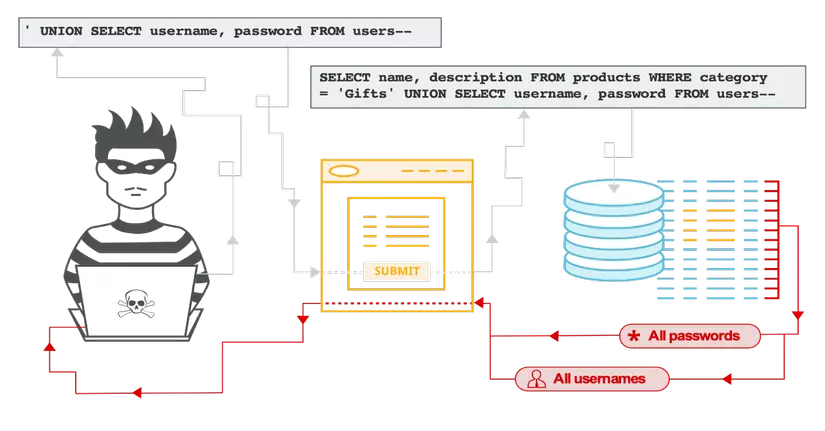
An example of how to exploit SQL Injection when testing a web site intrusion:
- Check the site’s weaknesses:
Search for locations that allow sending any data such as login pages, search, feedback, …
http://web-site.com/index.php?id=10
Some websites pass parameters via hidden fields:
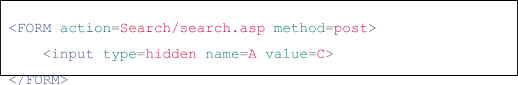
- Proceed to inject the query code:
For example for the login page, the following query snippets could be injected:
- Some payloads to perform the attack:
1 2 3 4 5 6 7 8 9 10 | ' or 1=1— " or 1=1— or 1=1— ' or 'a'=‘a ‘) or ('a'='a |
If the SQL query on Server has the form:

After injecting the code "admin" or 1=1--“ it becomes the query that is always correct, from which the attacker can log in without a username and password.

Common types of SQL injection exploits:
- SQL Injection UNION Attacks: The UNION statement is used to connect two SELECT clauses (both mysql and mssql are supported). An attacker can use this command to insert query into other data tables.
- SQL Injection Error Based Attack: An attack method that takes advantage of SQL Server’s error message function to retrieve data.
- SQL Injection Blind Attack: Use AND, SUBSTR (), … based on the result to return True or False or use SLEEP () and based on the command execution time to guess the table name, column name, data Whether, …
Consequences of SQL Injection:
- The biggest consequence that SQL Injection causes is: Disclosure of data in database. Depending on the importance of the data, the consequences can range from mild to extremely severe.
- Disclosing customer data can have a very serious impact on a company. Company image may be affected, customers switch to other services, resulting in bankruptcy, etc.
- This hole also greatly affects customers. Because they often share the same password for many accounts, just reveal the password of one account and other accounts will follow.
Prevention ways:
- Filter data from users: This prevention is similar to XSS. We use filter to filter the special characters (; ”’) or keywords (SELECT, UNION) entered by the user. Use the library / function provided by the framework because rewriting it from scratch is both time consuming and error prone.
- Do not add strings to create SQL: Use parameters instead of adding strings. If the data entered is not legal, SQL Engine will automatically report an error, we do not need to use a self-created function to check.
- Do not display exception, error messages: An attacker relies on error messages to find the database structure. When there is an error, we only display the error message, but do not display full information about the error, avoiding the attacker.
- Decentralization in Database: If only accessing data from several tables, create an account in the database, assign access rights to that account, not the root or superuser account. At this point, even if an attacker injected sql could not read data from the main tables, edit or delete data.
- Back up data regularly: Data must be backed up regularly so that if it is deleted by an attacker, it can still be restored.
1.3.2. (De) Serialization
(De) Serialization features are supported in most object-oriented languages under various names such as Serialize in PHP and JAVA, Marshal in Ruby, Pickle in Python.
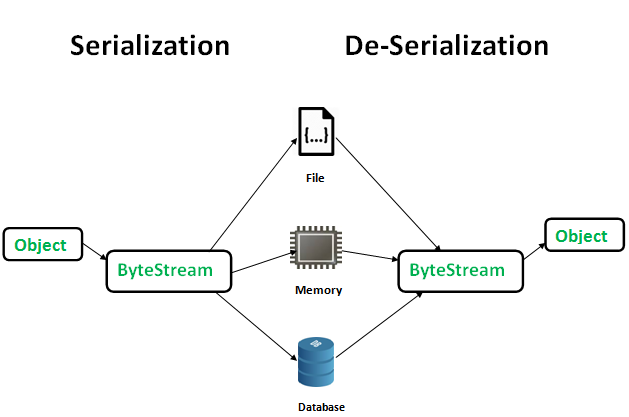
Serialization is the process of converting structured data or an object into a sequence of bytes that can be stored in memory or transmitted over the network. Deserialization is the reverse process of Serialization, which converts a sequence of bytes into an object.
Incorrectly formatted data or unexpectedly transmitted data can be used to alter the processing flow, insert malicious code for remote execution (RCE).
The Deserialization vulnerability in PHP (PHP Object Injection) can help an attacker perform many other types of attacks like Code Injection, SQL Injection, Path Traversal, … Magic method classes __wakeup (), __destruct (), __toString () together with POP Chain helps the attacker execute this error.
Analyze the following python program:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | <span class="token keyword">import</span> pickle <span class="token keyword">class</span> <span class="token class-name">Person</span> <span class="token punctuation">:</span> <span class="token keyword">def</span> <span class="token function">__init__</span> <span class="token punctuation">(</span> self <span class="token punctuation">,</span> name <span class="token punctuation">,</span> age <span class="token punctuation">)</span> <span class="token punctuation">:</span> self <span class="token punctuation">.</span> name <span class="token operator">=</span> name self <span class="token punctuation">.</span> age <span class="token operator">=</span> age <span class="token keyword">def</span> <span class="token function">info</span> <span class="token punctuation">(</span> self <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">print</span> <span class="token string">"Name:"</span> <span class="token operator">+</span> self <span class="token punctuation">.</span> name <span class="token keyword">print</span> <span class="token string">"Age:"</span> <span class="token operator">+</span> <span class="token builtin">str</span> <span class="token punctuation">(</span> self <span class="token punctuation">.</span> age <span class="token punctuation">)</span> p1 <span class="token operator">=</span> Person <span class="token punctuation">(</span> <span class="token string">"br"</span> <span class="token punctuation">,</span> <span class="token number">21</span> <span class="token punctuation">)</span> <span class="token keyword">with</span> <span class="token builtin">open</span> <span class="token punctuation">(</span> <span class="token string">"test.txt"</span> <span class="token punctuation">,</span> <span class="token string">"wb"</span> <span class="token punctuation">)</span> <span class="token keyword">as</span> f <span class="token punctuation">:</span> pickle <span class="token punctuation">.</span> dump <span class="token punctuation">(</span> p1 <span class="token punctuation">,</span> f <span class="token punctuation">)</span> |
The above program is responsible for saving an object in python into a file. To make it easy for users to transfer storage and reuse. Now when the user wants to reuse the object “p1”, he can use the following code:
1 2 3 4 5 | <span class="token keyword">with</span> <span class="token builtin">open</span> <span class="token punctuation">(</span> <span class="token string">"test.txt"</span> <span class="token punctuation">,</span> <span class="token string">"wb"</span> <span class="token punctuation">)</span> <span class="token keyword">as</span> f <span class="token punctuation">:</span> p <span class="token operator">=</span> pickle <span class="token punctuation">.</span> load <span class="token punctuation">(</span> f <span class="token punctuation">)</span> p <span class="token punctuation">.</span> info <span class="token punctuation">(</span> <span class="token punctuation">)</span> |
But is when reusing this object. The program is in danger of being hacked.
1 2 3 4 5 6 7 8 9 10 11 12 | <span class="token keyword">import</span> pickle <span class="token keyword">import</span> base64 code <span class="token operator">=</span> <span class="token string">" import _('os').popen('some evil os command').read()"</span> <span class="token keyword">class</span> <span class="token class-name">RunBinSh</span> <span class="token punctuation">(</span> <span class="token builtin">object</span> <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">def</span> <span class="token function">_reduce</span> <span class="token punctuation">(</span> self <span class="token punctuation">)</span> <span class="token punctuation">:</span> <span class="token keyword">return</span> <span class="token punctuation">(</span> <span class="token builtin">eval</span> <span class="token punctuation">(</span> code <span class="token punctuation">,</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token keyword">with</span> <span class="token builtin">open</span> <span class="token punctuation">(</span> <span class="token string">"test.txt"</span> <span class="token punctuation">,</span> <span class="token string">"wb"</span> <span class="token punctuation">)</span> <span class="token keyword">as</span> f <span class="token punctuation">:</span> pickle <span class="token punctuation">.</span> dump <span class="token punctuation">(</span> RunBinSh <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> f <span class="token punctuation">)</span> |
1.3.3. Directory traversal
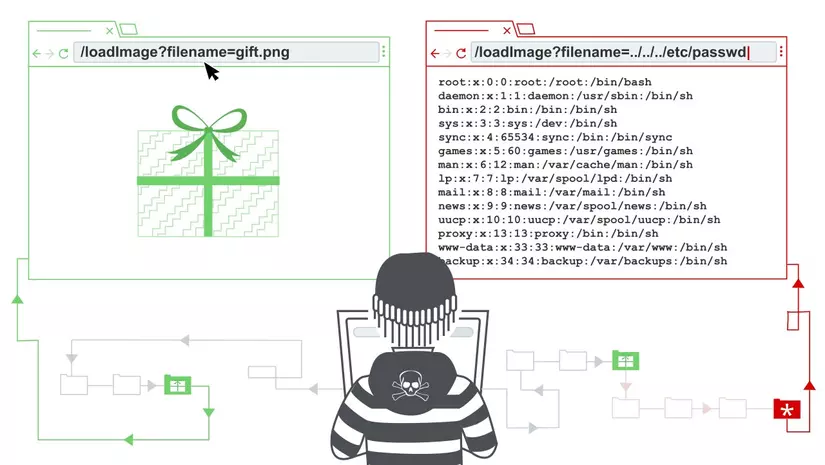
Directory traversal (also known as Path traversal) is a type of attack that allows hackers to access folders and resource files outside of the current directory. These unauthorized resources can be source code, server configuration information, system files and directories …
In addition, this vulnerability is often combined with a number of other vulnerabilities to improve attack efficiency.
How Directory traversal works:
A simple example is storing images in the system:
Assuming the image files are saved by the system administrator in the following directory: “/ var / www / html / blog / public / img /”. When accessing the avatar.jpg file on this directory, the programmer can leave the access path like:
http://exampleweb.com/get_photo/file?name=avatar.jp g. Now the webserver will access the file at /var/www/html/blog/public/img/avatar.jpg and return it to the user.
But instead of transferring the file name is avatar.jpg, hackers can pass the filename ../../../../../../etc/password . At this time, webserver will access and return the content of the file stored on the web server at /var/www/html/blog/public/img/../../../../../../etc/password.
This path is equivalent to “/ etc / password” so the web server will return the file system contents to the attacker.
In reality, depending on the web server and system settings, the exploitation method may be different, more difficult and varied. For example, with the window server, the attacker can use both “../” and “.. “
The reason for the Directory traversal vulnerability is so dangerous:
- This is a very dangerous vulnerability as it can affect the system. On a simple level, an attacker can read files in web directories or even sensitive files in the system.
- With a number of exploits and vulnerabilities at a more advanced level, an attacker can write a malicious file into the system and then insert the malicious code. Worst of all could result in an attacker being able to remotely execute code.
Some ways to prevent:
- It is recommended to check user input before processing it.
- Use whitelist (whitelist) for allowed values.
- Or the file names are numeric characters, letters should not contain special characters.
