What is OAuth 2.0?
OAuth is an open authorization protocol that allows resource owner access to resources by allowing clients on HTTP services such as Facebook, GitHub, etc. It allows sharing of resources stored on the resource. page after page without using their login information. Instead it uses token usernames and passwords.
OAuth 2.0 was developed by IETF OAuth Working Group, published in October 2012.
Why use OAuth 2.0?
- You can use OAuth 2.0 to read user data from another application.
- It provides authorization process for web, desktop applications and mobile devices.
- This is a server-side web application that uses authorization code and does not interact with user credentials.
OAuth 2.0 features
- OAuth 2.0 is a simple protocol that allows users to access resources without sharing a password.
- It provides user agent flow to run client applications using scripting languages, such as JavaScript. Typically, a browser is a user agent.
- It accesses data using tokens instead of using their credentials and stores data in users’ online file systems such as Google Docs or Dropbox documents.-
Advantages of OAuth 2.0
- OAuth 2.0 is a highly flexible SSL-based protocol (Secure Sockets Layer ensures data between web server and browser remains private) to store user access tokens.
- OAuth 2.0 is based on SSL, is used to ensure security protocols and is being used to keep data secure.
- It allows limited access to user data and allows access when the authorization token expires.
- It has the ability to share data with users without revealing personal information.
- It is easier to implement and provides stronger authentication.
Disadvantages of OAuth 2.0
- If you add multiple extensions at the terminals in the system specification, it will create a series of non-interactive implementations, meaning you have to write separate code for Facebook, Google, etc.
- If your favorite websites are connected to the central hub and the central account is hacked, then it will lead to serious repercussions on some sites instead of just one.
Flow done
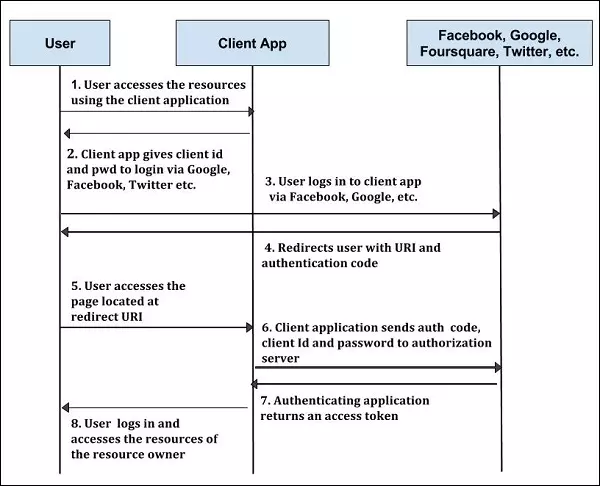
Step 1 – First, users access resources using client applications such as Google, Facebook, Twitter, etc.
Step 2 – Next, the client application will be provided with the client id and client password while registering for the Uniform Resource Identifier (URI).
Step 3 – User login with authentication application. The client ID and client password are unique to the client application on the authorization server.
Step 4 – The Authentication server redirects the user to a Uniform Resource Identifier (URI) redirected by the authorization code.
Step 5 – The user visits the page located at the redirect URI in the client application.
Step 6 – Client application will be provided with authentication code, client id and passoword and sent to the authorization server.
Step 7 – Authenticating application returns access token into the client application.
Step 8 – When the client application receives an access token, the user begins to access the resource owner resources using the client application.
Refer
https://www.tutorialspoint.com/oauth2.0/oauth2.0_overview.htm
