JWT and authentication method
- JWT (JSON Web Token) is an authentication method used in web and mobile applications. When a user logs into an application, the server generates a JWT containing information about the user and digitally signs it to validate the JWT. This JWT will then be sent to the user, and the user will send it back with the requests made in the application.
- Each time the user sends a request, the JWT is sent to the server and decrypted to extract information about the user. The server will check the JWT’s signature to ensure its validity. If the signature is valid, the server will return the data or perform the requested action.
JWT format
- JWT consists of 3 parts header, payload and signature encoded in base64, each element will be separated by a dot.
1 2 | eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJjb25jYXR4YW5obGEiLCJleHAiOjEyMzEyMywibmFtZSI6ImJheWJpc2hhcmsiLCJzdWIiOiJjYXJsb3MiLCJyb2xlIjoiYmxvZ19hdXRob3IiLCJpYXQiOjEyMzEyM30=.SYZBPIBg2CRjXAJ8vCER0LAENjII1JakvNQoP-Hw6GG1zfl4JyngsZReIfqRvIAEi5L4HV0q79qGhQZvy9ZdxEJbwTxRs6Lb-fZTDpW6lKYNdMyjw45alSCZ1fypsMWz2mTpQzil0lOtps5Eiz7mM7M8gCweAGpI53JxduQOaB5HkT5gVrv9cKu9CsW5MS6ZbqYXpGyOG5ehoxqm8DL5tFYaW3lB50ELxi0KsuTKEbD0t5BCl0aCR2MBJWAbN-xeLwEenaqBiwPVvKixYleeDQiBEIylFdNNIMviKRgXiYuAvMziVPbwSgkZVHeEdF5MQP1Oe2Spac-6IfA |
- Specifically, the header is a JSON object containing two pieces of information: the token type (type) and the encryption algorithm (algorithm) used to encrypt the token’s content.
1 2 3 4 5 | { "alg": "HS256", "typ": "JWT" } |
- The payload is a JSON object containing authentication and other information. This information is encrypted using the algorithm specified in the header.
1 2 3 4 5 6 7 8 9 | { "iss":"concatxanhla",=> viết tắt của issuer là thông tin hệ thống tạo "exp":123123, => thời gian hết hạn của token name":"baybishark", "sub":"carlos", "role":"blog_author", "iat":123123 => thời gian tạo của token } |
- The signatuer part is the final part of the JWT, created by combining the header, payload, and a secret key to create a unique signature string. This signature is used to validate the token.
HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), secret),
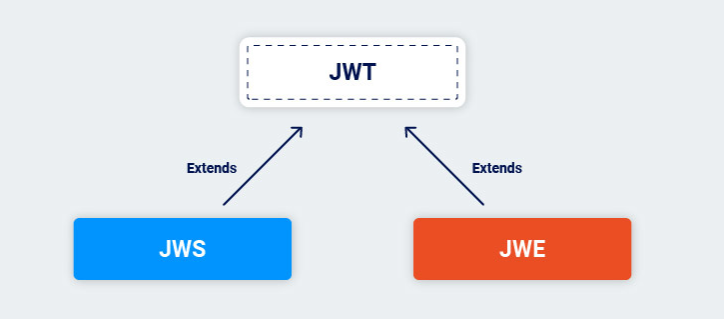
JWT vs JWS vs JWE
- JWT is used to authenticate users and transfer information between parties. JWS (JSON Web Signature) is used to verify the integrity of data and JWE (JSON Web Encryption) is used to protect transmitted data. These format standards can be combined to ensure the integrity and security of data in transit.

JWT Authentication
- On the server, generate a secret key. This secret key will be used to generate and authenticate the JWT tokens.
- When a user logs in or performs authentication, the server generates a JWT and sends it back to the client. This JWT contains the user’s credentials, such as information about the user and access rights.
- When the client sends a request to the server, it sends the JWT included in the header of the request. Normally, this header is named “Authorization” and its value is “Bearer [token]”, where [token] is the JWT string.
- On the server, when you receive a request from the client, you need to validate the JWT to ensure that it is valid and has not been modified. You can do the following steps for JWT validation:
- Extract the JWT code from the “Authorization” header of the request.
- Use the secret key shared between the client and the server to decrypt the JWT.
- Check the signature included in the JWT to verify its integrity. The signature is generated using an encryption algorithm with a shared secret key.
- Check the JWT’s expiration to make sure it’s still within the valid time.
- If the JWT authenticates successfully, the server can retrieve the information from the JWT and continue processing the client’s request.
- If the JWT is invalid or has expired, the server may return an appropriate response code, such as a 401 Unauthorized error code.
Types of attacks on JWT.
Do not verify JWT
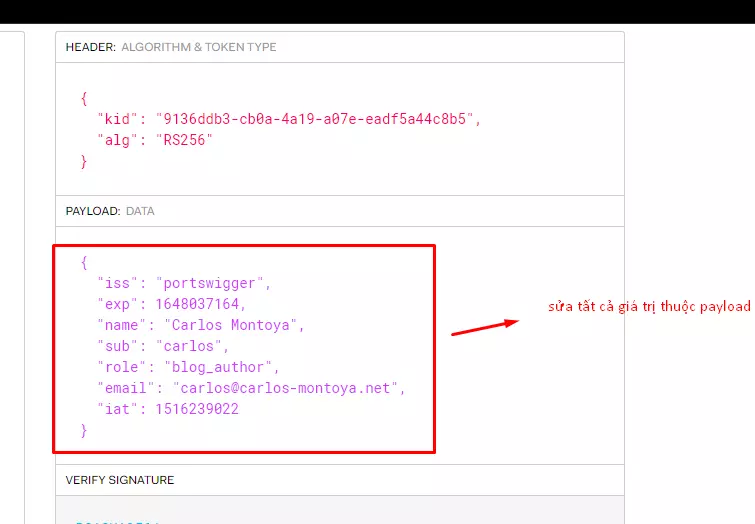
- In this case, DEV does not verify or confuses using decode function to get value from payload instead of using verify.=>
- The attack in this case just edit the payload field to the desired value and terminate.

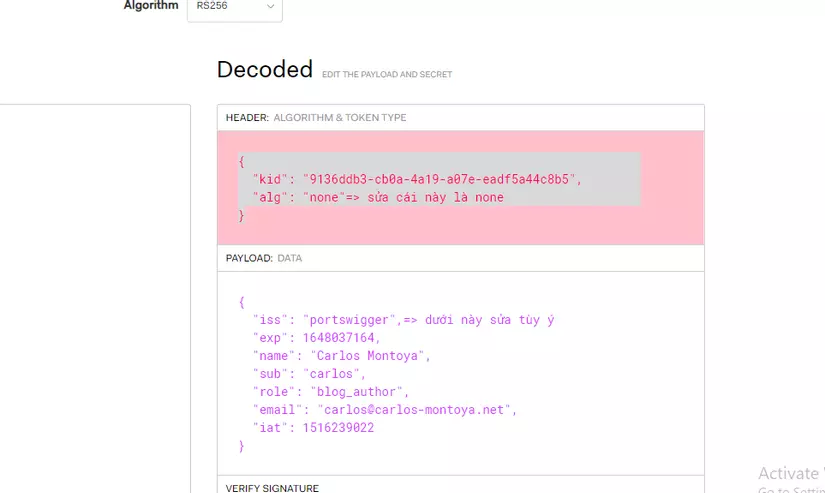
Accept token with signature of none
- In this case, the algorithm can be changed to none and the payload information can be edited freely

Use weak jwt key
- In this case use hashcat to brute the jwt secret key.
hashcat -a 0 -m 16500 <YOUR-JWT> /path/to/jwt.secrets.list=> secret list can use rockyou or seclist or something that exists on the internet.
Self-signed JWT injections via jwk . parameter
- JWK (JSON Web Key) is a standardized format for representing keys as JSON objects.
- For example
1 2 3 4 5 6 7 8 9 10 11 12 | <span class="token punctuation">{</span> <span class="token property">"kid"</span> <span class="token operator">:</span> <span class="token string">"ed2Nf8sb-sD6ng0-scs5390g-fFD8sfxG"</span> <span class="token punctuation">,</span> <span class="token property">"typ"</span> <span class="token operator">:</span> <span class="token string">"JWT"</span> <span class="token punctuation">,</span> <span class="token property">"alg"</span> <span class="token operator">:</span> <span class="token string">"RS256"</span> <span class="token punctuation">,</span> <span class="token property">"jwk"</span> <span class="token operator">:</span> <span class="token punctuation">{</span> <span class="token property">"kty"</span> <span class="token operator">:</span> <span class="token string">"RSA"</span> <span class="token punctuation">,</span> <span class="token property">"e"</span> <span class="token operator">:</span> <span class="token string">"AQAB"</span> <span class="token punctuation">,</span> <span class="token property">"kid"</span> <span class="token operator">:</span> <span class="token string">"ed2Nf8sb-sD6ng0-scs5390g-fFD8sfxG"</span> <span class="token punctuation">,</span> <span class="token property">"n"</span> <span class="token operator">:</span> <span class="token string">"yy1wpYmffgXBxhAUJzHHocCuJolwDqql75ZWuCQ_cb33K2vh9m"</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> |
- Ideally, servers should only use a limited whitelist of public keys to verify JWT signatures. However, a misconfigured server sometimes uses any key embedded in the jwk parameter.
- You can exploit this behavior by signing the modified JWT with your own RSA private key, and then embedding the appropriate public key in the jwk header.