How did LOZI.VN “accidentally” expose data of 2 million users?
- Tram Ho
In the process of writing the introductory security series, I still go on a walk, looking for security bugs in the spirit of “code walking” of the blog. Perhaps of course, finding errors must find big pages, many users a little, but small pages, who cares.
As a developer, I’m not good enough at the network or the infrastructure to be able to attack the server or something DDOS. So, I decided to just check the web and app , the two things I know best. Vietnam said that it was done, I started accessing the website of some big apps like tiki, lazada, foody ….
The error detection is like fishing, sometimes fishing big fish, sometimes the whole sentence is not good. This time, I caught a small fish that … dangerous of lozi.vn.
Detect from the web
When entering lozi.vn interface, hitting my eyes is the biggest mistake: no HTTPS!
Simply put, surfing the web has important information without HTTP, just like you go for a massage, mistaking, going without a condom. Hackers can steal your data in a flash when you don’t know anything. (See more about the security of the HTTP protocol ).
Next, I started playing naughty by … opening the Chrome Developer Tool . Don’t underestimate it, this tool is very popular. Well, what do we have?
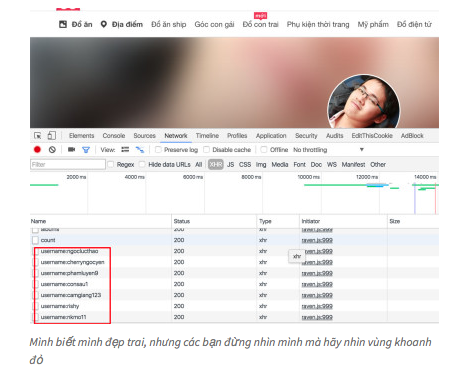
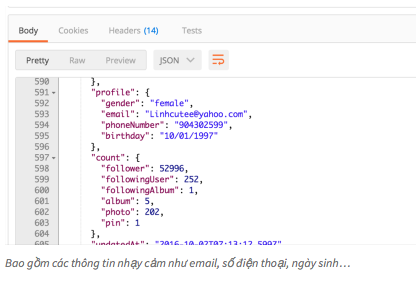
A series of AJAX functions in the get form, pass the username and get user information. More specifically, in JSON this function returns including sensitive information such as personal addresses, birth dates, e-mails.
This GET function has no authentication , so I can completely change the username and get the information of the entire user. However, it is not feasible to test each username quite a while.
How to continue? I started switching over … mobile application of lozi.
Go to the mobile app
There is a “little” truth that few of you know: Although I often write articles about C # and JavaScript, I’m actually quite familiar with Java and Android . Don’t show off, come back to the lesson.
The reverse of the application is not too complicated. I just need to upload apkpure.com to download the apk file, then use the tool decompile to have the source code of android application of lozi.
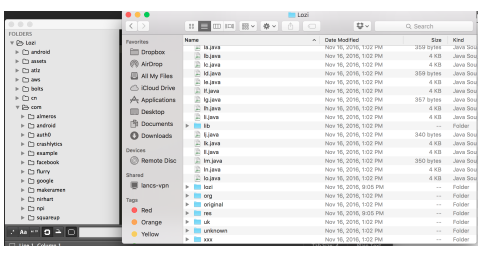
It seems that when publishing, team lozi has not obfuscate the code so the code is still the same. Because the team code is very standard with OOP and SOLID, it is not too difficult for me to look for lozi API code. The code that makes me pay attention is the SearchUser API call.
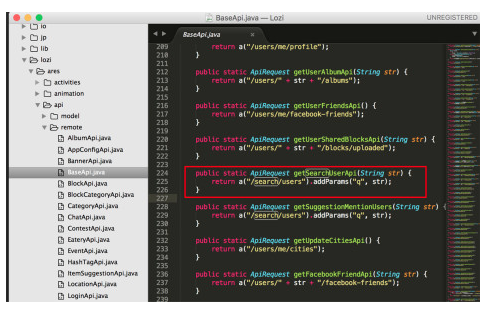
This API has GET format so I don’t need any more information. Turn on Postman, enter the url of the API and … bingo. Information about 2 million users here.
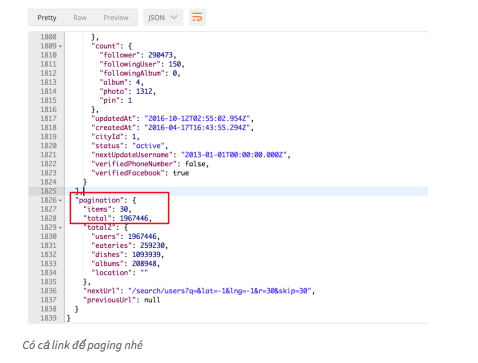
The process of handling errors
On Wednesday evening, November 16, I found this error, started contacting lozi.vn.
On Friday afternoon, November 18, I received a reply from the lozi fanpage. About 5 minutes after I sent the mail to the lozi team, the error was immediately fixed .

On Saturday morning, November 19, I received a very enthusiastic mail reply from the person in charge even though it is Saturday. Hooray lozi . The attitude of working is different from that of the cinema cinema , but it is more than half a month.
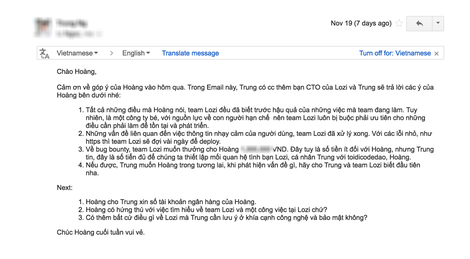
About 4.5 days after I reported the error, the lozi also updated https and added the token for the APIs already.
Comment
In the general thinking of developers, these RestAPIs are often hidden, so users can’t see them, so they can’t be reversed. Unfortunately, developers and hackers can easily decompiler the app and “play around” with these APIs.
In fact, it’s not just lozi team, most other teams are also quite lacking in vigilance about API security. Typically, the CGV case revealed 3 million users also by API mobile. However, Team Foody and Lozi have secured API quite well, I tried to play it without gaining any results.
It is worth mentioning this fact that these security holes are extremely basic , I am a “horizontal hand” that can be exploited without a specialized tool (Kali Linux, Tool Penetration Test), just Chrome and SublimeText.
Large systems that are sometimes lax in this way, is our data safe when “professional” hackers get started ??
With the “mind” of the developer, I contact immediately with the party to handle. What if the person who found the error was not me but a “mindful” hacker, ready to scratch the data and then share it or sell it to other companies, or competitors. with lozi.
How to prevent this? Hard to read all the introductory Security series on toidicodedao. These types of vulnerabilities and how to prevent them are all stated in the series.
Note: Posting is only nature and provincial, not meant to show off.
For “mindful” hackers, they have to plan an attack, or have to work hard to find a hole no one has found. My actions are just tinkering, playing around with the developers’ elementary mistakes , figuring there is nothing to be proud of to show off;)).
Any act of attack or sabotage of the system in order to “show up” is a childish, thoughtless act that can lead to “imprisonment money.” Remember to think carefully before acting.
ITZone via toidicodedao
