Learn the format of CTF Reverse Android: decompile and patch the APK file
- Tram Ho

Reverse Engineering (or RE for short) is an array that most CTF Jeopardy awards have. In RE articles we often see some file types like exe, elf, code files, … and apk files.
Due to the fact that making an Android app, it is necessary to leave in it the security shortcomings for players to exploit, finding flags takes more time and effort, so the apk file format does not appear much in competitions. CTF. However, in terms of difficulty and fun, the reverse file apk format is no less than other file types.
In this article, we will learn about the RE Android format through a simple CTF: Droids3 in picoCTF 2019.
Download link: Droids3
Tools
The basic tools that we need to do a CTF reverse apk include:
- Root Android device: real machine or emulator is okay. I use Genymotion
- Virtual box to run Genymotion simulator.
- JDK To run tools, most of them are written in java.
- ADB: a tool to connect to the Android virtual machine, available in the tools directory of genymotion, the default path on windows is C: / Program Files / Genymobile / Genymotion / tools.
- Apktool: decompile and build the apk file.
- Bytecode viewer: reverse file apk tool
Setting
After installing all the tools, we launch Genymotion, create any Android device. I usually create Google Pixel devices, these devices run quite smoothly.
Once everything is enough and the android emulator is on, we will install the apk file into the emulator to run:
- Copy file three.apk to the same directory as adb to proceed with the installation.
- Run the application installation command into the virtual machine: adb install three.apk
After successful installation, the PicoCTF app has been added in the emulator
Learn the application
The application interface has basic functions: 1 input field, 1 button and 2 texts.
When clicking on the button, it will display the text “don’t wanna”, and the hint is “make this app your own”.
Find the flag
Open the file three.apk with the Bytecode Viewer we can see many files and folders. How to find a file from the pile that works to help us get the flag is mainly based on experience. My way is to try to see if all the files are exploited or not.
Of course, you can’t find it without any directions. The main application code file is usually located in the form com / abc / xyz /. For this article, we see a file with a suspicious name located at com / hellocmu / picoctf / FlagstaffHill.class
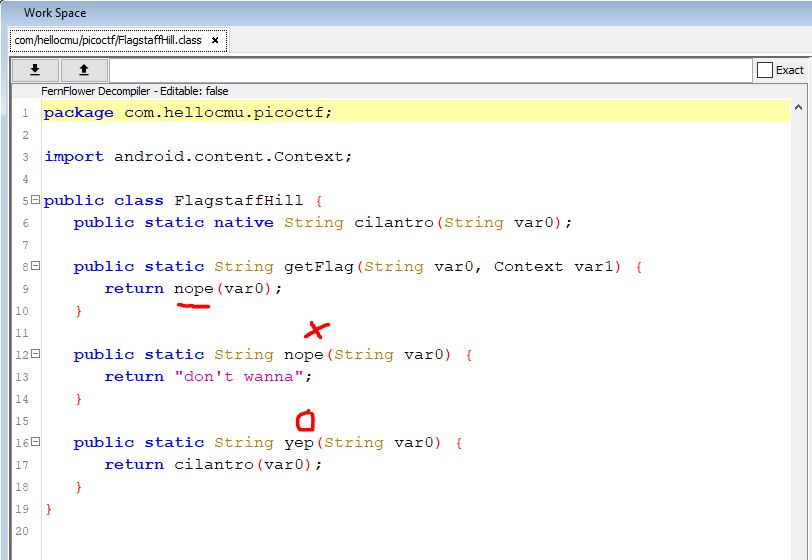
Here we notice that there are 2 functions nope () and yep (). The getFlag () function returns the result of the nope function – “don’t wanna”. So what we need here is getFlag to return yep. To do that we need to use the technique of patching apk files.
Before introducing the patch technique, I will talk briefly about the structure of the apk file. The apk file is actually a zip file, such as zip, rar, etc. We can completely rename three.apk to three.zip and extract it as usual. Of course, the files after extracting can not be viewed directly
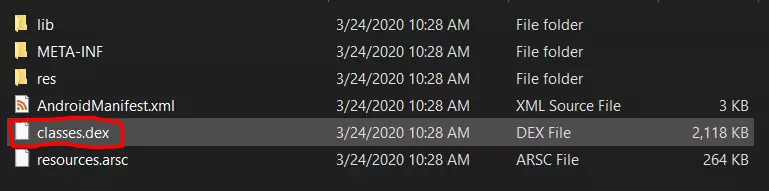
In the extracted file, there is a class.dex file, this file contains classes in java code. Developers will often code Android apps using java / kotlin. When compile, class files will be compressed into a dex file.
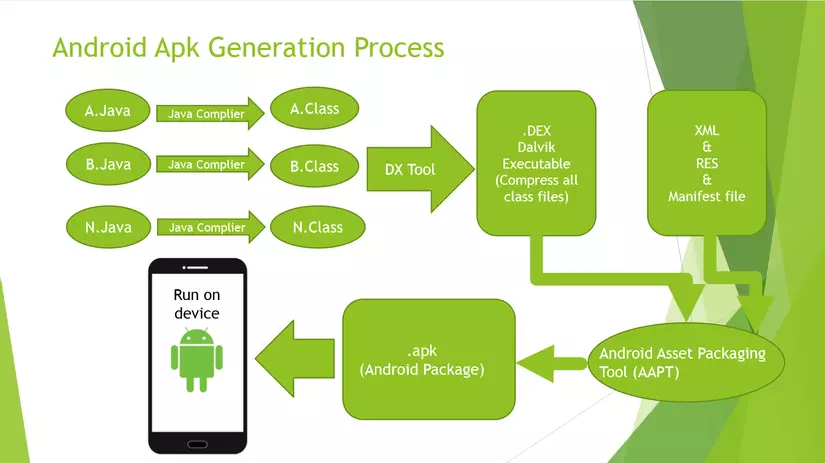
When doing the reverse file apk, we will not receive code files in java, instead we will receive the file smali code. From these smali files, the decompiler will turn to java code for us to read, but it won’t be completely accurate, and there will be a difference when using different decompilers. The most reliable thing when running a reverse app is the smali code (smali code in reverse android acts as an assembly code in reverse exe, elf).
I just briefly introduced like that. Now we will embark on re-pathing the app.
First we will decompile the apk file with apktool
Put apk and apktool files in the same directory and run the command: java -jar apktool_2.4.1.jar d three.apk
The result will be folder three with sub folders, files
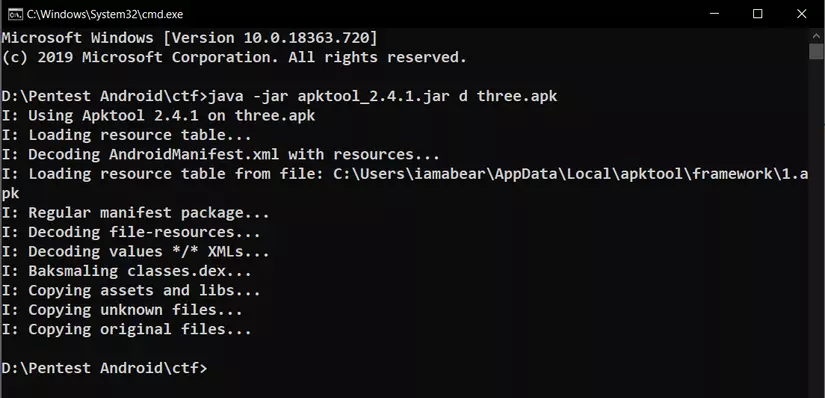
Next we will proceed to correct the code
Open file three /smali/com/hellocmu/picoctf/FlagstaffHill.smali
I use VScode to install the smali extension to make it easier to see, convenient for code editing.
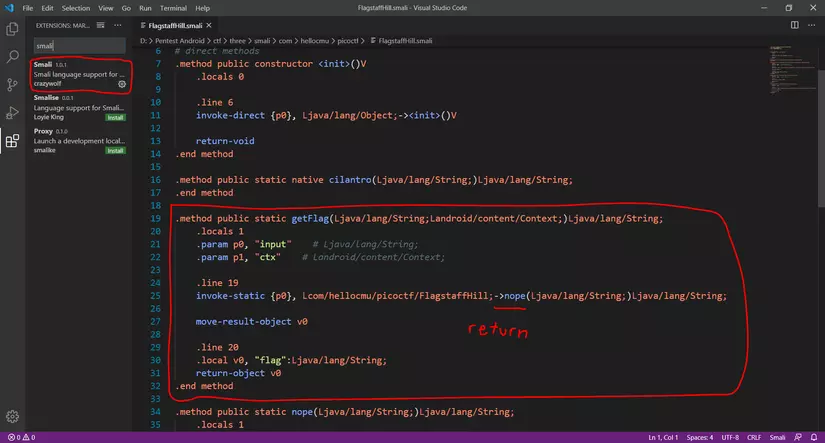
We will pay attention to the getFlag function, where I underlined -> nope corresponds to return nope in java code. Now let’s review java code:
- Firstly, we need the getFlag function to return yep instead of return nope
- Second: both yep and nope functions have the same argument
=> So, to getFlag return yep, we just need to change -> nope to -> yep, then save the file.
Step 3: rebuild into a new apk file
Once the code has been fixed, we need to build the new apk file from those files. apktool also has the function to allow building the apk file after fixing the code, just run the command: java -jar apktool_2.4.1.jar b three
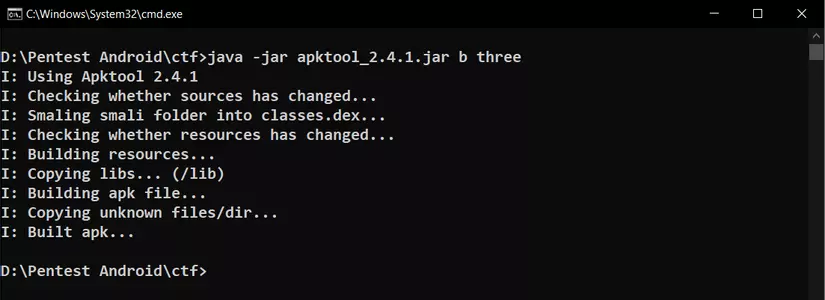
The new apk file is located in the three / dist directory. Delete the old app in the emulator and reinstall the new app, is there anything else?

This new file three.apk won’t install immediately, we need to continue with the last step.
Sign apk
Please copy the following 2 commands into the text file:
1 2 3 4 | keytool -genkeypair -v -keystore key.keystore -alias publishingdoc -keyalg RSA -keysize 2048 -validity 10000 jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore ./key.keystore %1 publishingdoc |
Rename the file to sign-apk.bat then run the command cmd: sign-apk.bat [file-name] .apk
In turn fill the keystore and the information, you can fill anything you want, let me “123123”. The first command will create key.keystore, the second will sign the apk with the key just created.
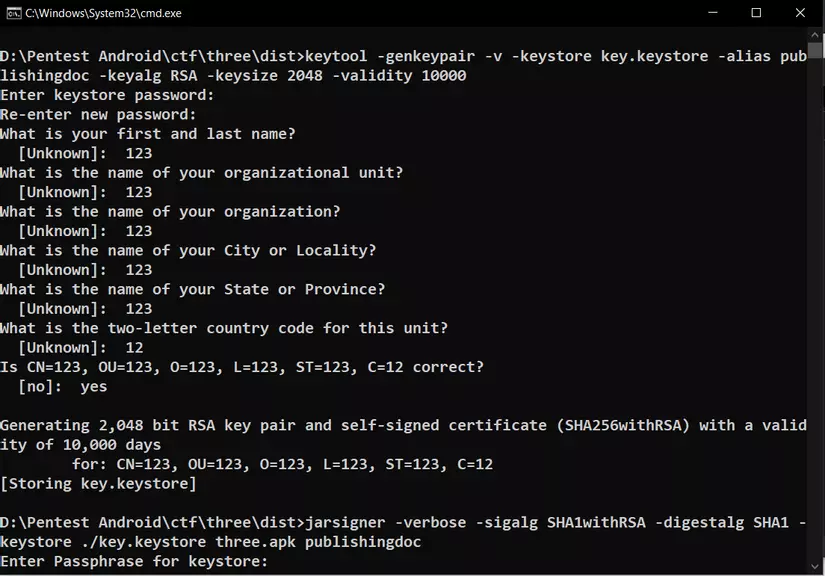
So we have successfully signed apk patched file. Now just delete the old application in the emulator, install the new patched application and press the button to get the flag.
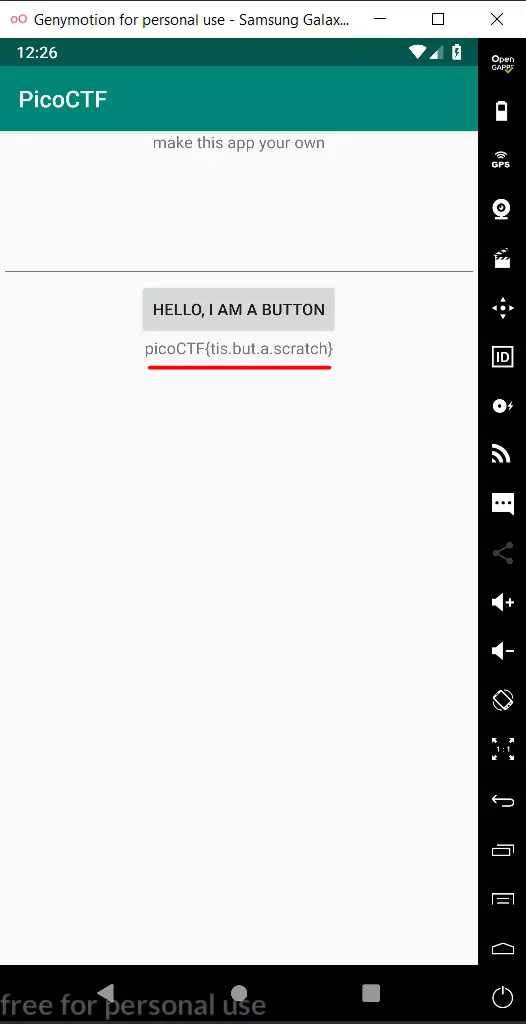
Flag: picoCTF{tis.but.a.scratch}
Through the article, surely you all know the basic knowledge to do CTF reverse apk then right? If you have any questions, please comment below the article so we can discuss it together.
Source : Viblo
