I. Introduction
1. Virtual money
Definition: A type of digital asset, a medium of exchange, used with cryptography to secure transactions.
Characteristics:
- Eliminate the middleman role
- Create a peer-to-peer network of nodes.
2. Bitcoin
Bitcoin was announced in 2008 and first launched in 2009 by Shatoshi Nakamoto
Characteristics:
- Decentralization
- Anti-censorship
- Safe
- Borderless.
3. Blockchain
Definition: A chain of blocks containing information that is secured by encryption.
Structure of blockchain:
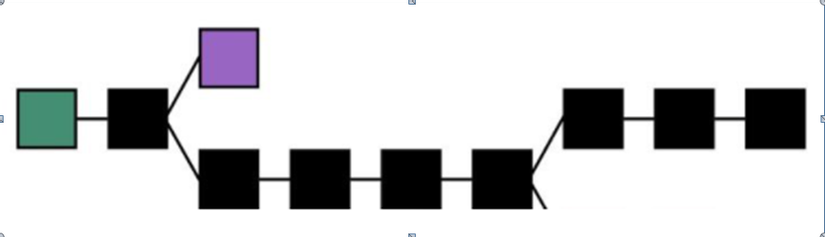
Sign:
- Blue: genesis block root block
- Black: main branch blocks (accepted)
- Purple: block changed (removed)
The structure of a block in bitcoin
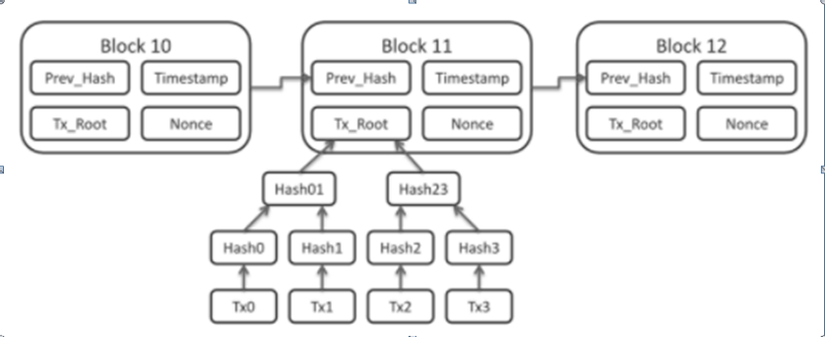
Characteristics:
- Independence and extensibility
- Immutability
- Dispersion
Blockchain security: Depends heavily on encryption, especially hash functions, digital signatures …
Advantages
- Advantages of blockchain characteristics such as decentralization, immutability
- Safe when more and more users
Defect
- 51% attack
- Difficulty in data modification
- Private key issues
- Highly competitive
II. Virtual currency transactions
Cryptocurrency transactions work on the principle of public key cryptography along with a “mining” method
In transactions, we use public encryption to authenticate the transaction. Public encryption consists of a Public key and a private key. The public key can be made public, but the private key is known only to its owner. The keys are always made up of a corresponding pair
The mining method is essentially adding new blocks to the blockchain chain through problems and rewards
Example of a transaction: Alice sends Bob 2 bitcoins
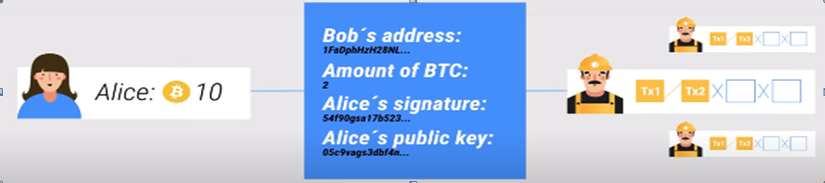
Alice needs to get the private – key to connect the wallet, from the private-key to the message will form a digital signature
The digital signature along with Bob’s address, Alice’s public key, the amount of bitcoins will form an encrypted message. This message is “broadcast” to all nodes => The nodes will decode the message to be the transaction content.

The nodes validate the message and receive a block of hashes from the message.
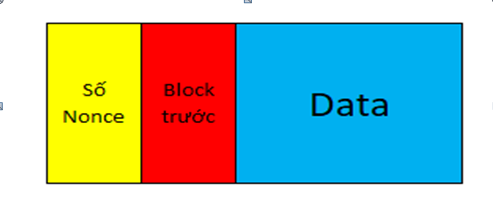
-> The problem posed for miners: The added block must contain the hash of the previous block plus data and the hash of the new block must contain a sufficient number of 0 bits
For example, the input might be: 00000d3ae2ac43b66283cf0c89636….
The block of data will be added to the nonce number. Miners have to find the number of nonce to satisfy the input
III. Hash function
Definition: An algorithm that produces hash values for each block of data
Property: A hash function H (x) satisfies the following conditions:
- H is applicable to x messages of different lengths
- The size of the output h = H (x) is fixed and small
- Unidirectional calculation: for a given h, x cannot be found again such that h = H (x) (in terms of computation time)
- Weak anti-coincidence: given an x, cannot find y ≠ x such that H (x) = H (y)
- Strong anti-coincidence: it is impossible to find any x, y pair (x ≠ y) such that H (x) = H (y), or in other words, if H (x) = H (y) then it can be certain. make sure x = y.
IV. Public key encryption
Public key cryptography is an essential element of blockchain technology – it is the underlying technology for wallets and transactions.
When users create a wallet on the blockchain, they are creating a public-private key pair.
The wallet address is a public keyword-generated string. This address is public to everyone and can be used to check the balance in that wallet or deposit funds there.
The private key associated with the wallet is a proof of wallet ownership and control. It’s the only way to send money out of it and a lost private key means the money inside will be stuck there forever.
For example 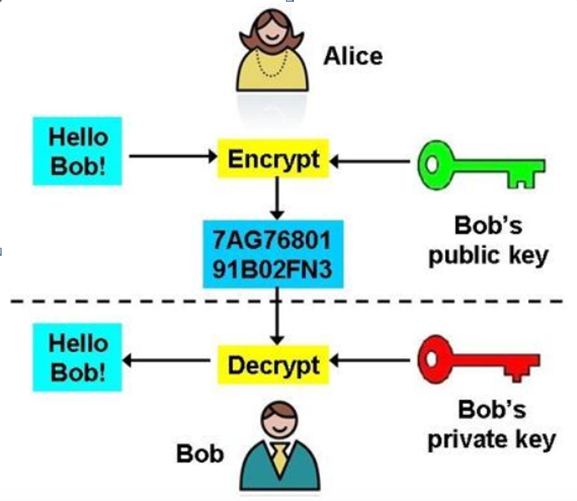
Suppose Alice wants to send an encrypted message to Bob:
Alice uses Bob’s public key to encrypt the message.
Alice sends an encrypted message to Bob – if a third party intercepts it, all they will see are random numbers and letters.
Bob uses his private key to decrypt and read the messages
V. Conclusion
Above are some of the research that I want to share for those who are just starting to learn about encryption or blockchain. Wish you a very productive and happy working day!
