Preamble.
JWT (JSON Web Token) is a popular technology today, but it is also very controversial at the same time.
Many people say never to use it, while others say it is great. So what is the truth? Should or should not be used? That is why we are here.
1. Brief introduction about JWT.
JWT is technically a mechanism for verifying the owner of some JSON data. It is a variable string, which can hold an unlimited amount of data (unlike a cookie) and it has been encrypted by signature.
When a server receives JWT, it can ensure the data it contains can be trusted because it has been authenticated with the stored signature. No intermediaries can modify JWT after it is submitted.
It is important to note that JWT guarantees data ownership but not encryption; Anyone can see the JSON data we store in JWT once they get JWT, because it is serialized, not encrypted. For this reason, it is recommended to use JWT with HTTPS.
2. So it’s good in any case?
JWT is a great technology for API authentication and server-to-server authorization.
It is not a good choice for sessions.
3. Use JWT to authenticate the API
The most common application of JWT Token, and the only purpose you should use JWT is to use it as an API authentication mechanism.
This is now so common and widely used, even Google also uses JWT to authenticate their APIs.
The idea is simple:You will receive a secret token from the service when you set up the API
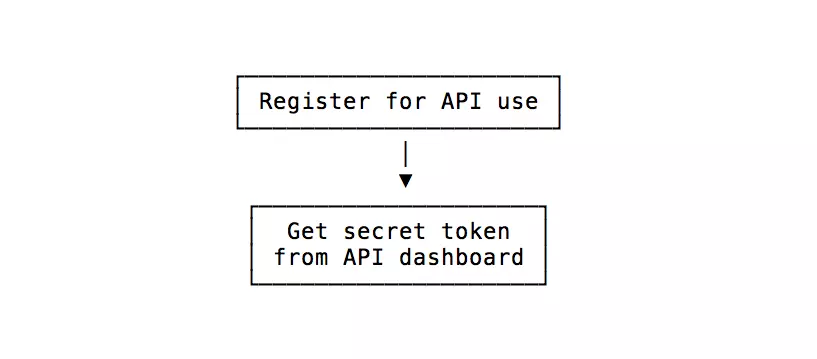
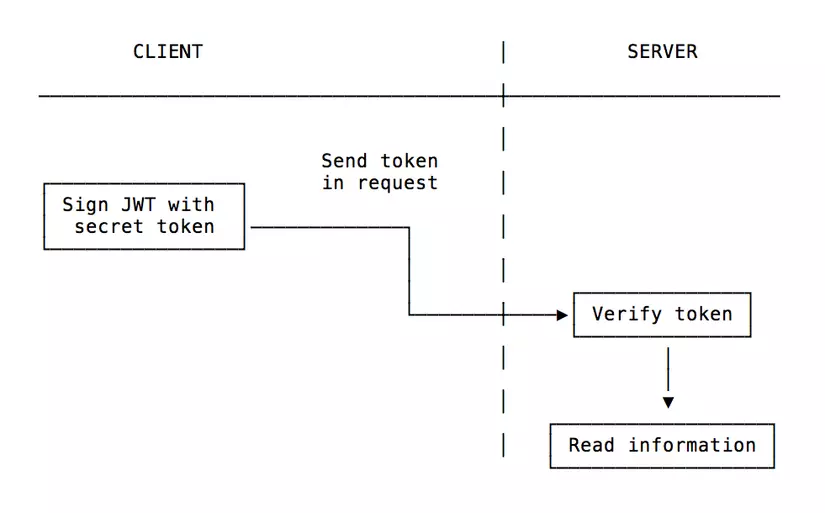
- On the client side, you will use the secret token to sign and attach it to the token (there are many libraries that support this).
- You will attach it as part of the API request and the server will know who it is based on the request signed with a unique unique identifier:
4. Disable 1 single token
How can you invalidate a single token? One simple way is to change the server’s secret key, invalidating all tokens. But doing so will stun customers, for some reason, their token “is so”.
Another way to handle this problem is to add a time element to the user object. The token automatically stores the created at value in the iat attribute. Every time you check the token, you only need to compare the value created at with the time value in the user object.
To disable the token, just update the server-side value and if the iat is older, you can reject the token.
5. Store JWTs securely
JWT needs to be stored in a safe place inside the user’s browser.
If you store it inside localStorage, it can be accessed by any script on your site (this is really bad, because an XSS attack can allow an outside attacker to get a token).
Do not save tokens in localStorage (or sessionStorage). If any third-party script you submit to your site is compromised, it can access all user tokens. JWT needs to be stored inside httpOnly cookie, a special type of cookie that can only be sent in HTTP requests to the server and it can never be accessed (either for reading or writing) from JavaScript running in the browser.
6. Use JWT to exchange secure information between two servers
Because JWT is signed, the recipient can be sure that the customer is really who they think he is.
6.1. Use JWT for SPA authentication
JWTs can be used as authentication mechanisms that do not require a database. The server can avoid using the database because the data stored in JWT is sent to customers as safe.
6.2. Use JWT to authorize operations on the server
Suppose you log in to a server, SERVER1, after successful login, you are redirected to another server SERVER2 to perform some processing.
SERVER1 can grant you 1 JWT to authorize you to connect to SERVER2. The two servers don’t need to share the same session or anything to authenticate you. Using tokens to handle this case is perfect.
7. Session tokens for regular web apps
You might think that using JWTs for session tokens is a good idea at first, for example:
You can store any type of user information on the client server The server can trust the client because JWT is signed and does not need to call the database to retrieve the information you have stored in JWT You do not need to combine sessions in a centralized database when you have problems requiring horizontal scaling Finally, if you already have a database for your application, just use the session table and use the regular sessions supported by The server side framework is sufficient.
Why? It takes a lot of effort to use JWT: because they are sent in every request to the server and it always takes more effort than using server-side sessions.
In addition, although the security risks are minimized when sending JWT with HTTPS, there is always the possibility that it is blocked, the data is stolen and “hacked” -> your customers will be “stripped bare.” ”.
8. How to choose the perfect JWT library
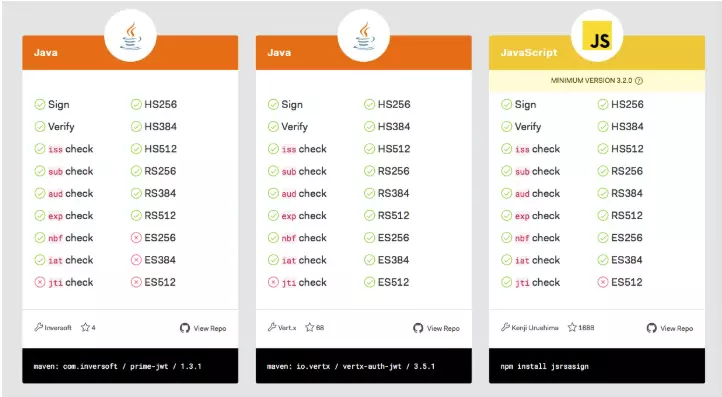
Go to jwt.io and see the library list. It has a list of the most popular libraries for deploying JWT.
Choose the language you use and choose the library you like, the best library is the library with the highest amount of green space.
9. Conclusion
JWT is a very common standard that you can use to authenticate requests using signatures and exchanging information between parties. Make sure you always use it, when you don’t, and how to prevent the most basic security issues.
Source: https://blog.logrocket.com/jwt-authentication-best-practices/
