Preamble
Today, backend developers are quite familiar with user authentication through passwords using salt hashes, and it is also the most powerful, most trusted authentication method. However, there are still other secure authentication methods that I think should be known so that I can use it later.
Today I will introduce another authentication method called Lamport (one-time secure password authentication).
What is Lamport, why is it called Lamport?
Lamport’s idea is to use sequential hash value strings, each value in this string will be used as a password, starting from the last element (born last in the hash string). So the challenge and response lies in the password hash provided by the user at the n + 1 login, the system must receive the password used at the nth time (immediately before).
They took the name of the person who created it in order to put the method always this
How does Lamport work?
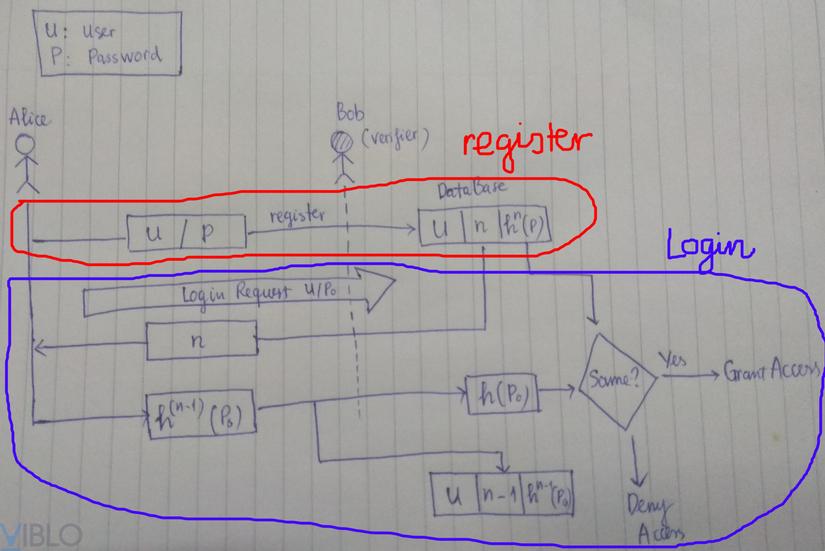
The mechanism of Lamport method is divided into 2 phases:
- Registration phase
- phase authentication.
Registration is only done once, the authentication is performed every time the user logs into the system. You can see the image below to better visualize (I drew a little bad 
 )
) 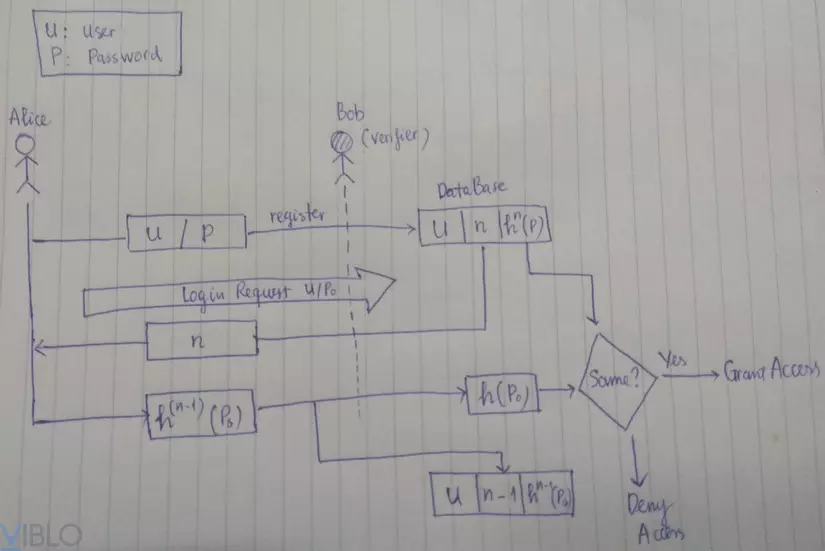
In the image above, the registration phase takes place as follows:
- User (Alice) enter user_name (U) and password (P) to register
- Server (Bob) inserts data into the Database, where:
- user_name is saved as plain
- Save a fixed n value
- The password (P) is hashed n times and stored in this database (
h^n (P))
So the end of the registration phase
Next is the login phase:
- Alice sends user_name (U) to the server
- Bob checks the database to see if user_name exists or not, if it exists then returns
naccordingly. - At this time, a form appears for Alice to enter the password (
P0),P0will not be transmitted in the form that it will be hashedn - 1once withnbeing the value of Bob just returned (h^(n-1) (P0)) - When Bob receives the post hash code and proceeds to hash it again, he gets
h^n (P0) - Bob compares
h^n (P0)toh^n (P)stored in database, if these two values match, then login successfully and update 2 valuesh^(n-1) (P0)andn-1to the database, so the password stored in the database will be refreshed.
Just like that after each login the hash value of the password will be changed in the database so that if the database is stolen, it is very difficult to get the user’s password.
Limit
- The processing speed is not high if
nis a large number - It is possible to perform a dictionary attack if there is no limit to how many incorrect entries are entered
Methods of attack
Surely the readers coming here can see that this authentication method seems to be safe, also looks delicious  Probably usable.
Probably usable.
However, there is a way to overcome it, which is called attacking Man In The Midlde
The schematic of this attack is as follows: 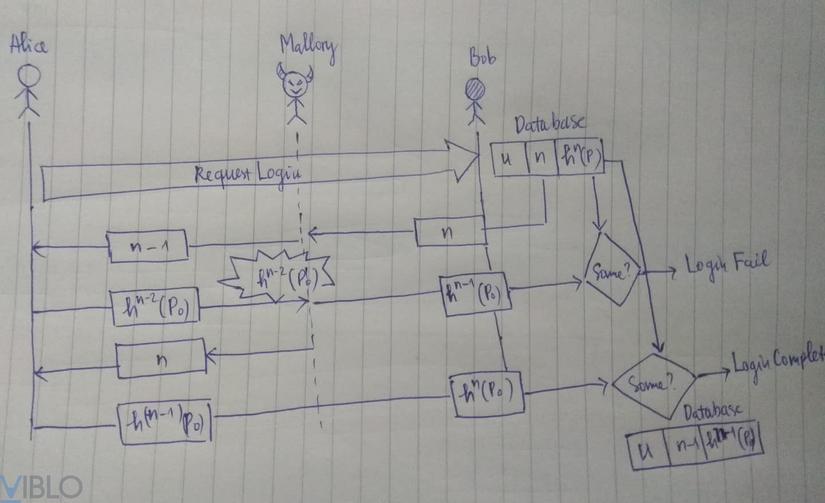
I would describe this attack as follows:
On a clear day, a man named Mallory saw Alice and Bob talking so loudly standing in the middle of eavesdropping.
Alice just told Bob: “Dude, let me log in, my user_name is …”
Bob checks find a new valid user_name sure: ” n Here he took it that log  ”
”
Before Alice could hear what n was, Mr. Mallory heard it, and then Mallory imitated Bob’s voice and told Alice: ” n - 1 here you take it and log in  ”
”
Alice thought that was true so she also hashed the password to h^(n-2) (P0) and told Bob: “My password is h^(n-2) (P0) let me in”
Mallory is hearing so bad now h^(n-2) (P0) 
Bob hears Alice’s password is h^(n-2) (P0) , hashes again h^(n-1) (P0) and compares it to be incorrect, telling Alice: “Password password, then re-enter, get n and hash ” 

Mallory at this time, do not say it wrong for Alice anymore, Alice will say the correct password and be entered, then Bob’s database will be updated with the hash password is h^(n-1) (P0) 
That’s it, the next time Mallory just pretends to be Alice and says the password is h^(n-2) (P0) , it will match the password in Bob’s database without knowing Alice and Bob have used What encryption algorithm
A little toilet for the article is not boring because it is all theory.
In fact, Alice and Bob can’t talk about each other like that, to overhear, Mallory will be a proxy between these two. You can use Burp Suite tool to do this.
The article here is over, wish you have a happy working day and effectively
