INTRODUCE
- Mod Security is a firewall module that can integrate with Web Application Server (web application server) such as Apache, IIS, Nginx to allow analysis and logging of HTTP / S data streams. OWASP’s ModSecurity Core Rule Set project has made ModSecurity stronger and more flexible in analyzing behaviors that are likely to compromise web application security.
- Mod Security stands in front of the Web Server, acting as a firewall to control access to and from the Web Server. The information going from outside to inside and out will be strictly controlled to avoid information that may harm the Web Server or the leakage of special information from the Web Server to the Client.
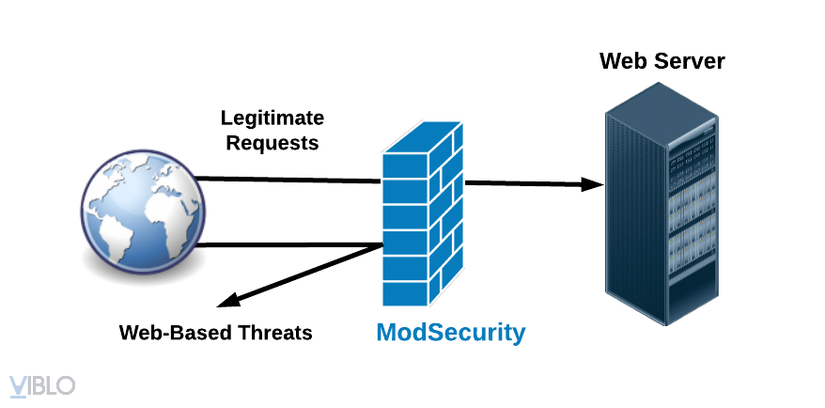
- Security Mod can:
- Request filtering: all requests sent to the web server are analyzed and filtered before they are sent to other modules for processing.
- Anti-evasion techniques: paths and parameters are standardized before analysis to combat evasion techniques.
- Understanding of the HTTP protocol: ModSecurity is a web application firewall so it is capable of understanding HTTP protocols. ModSecurity has the ability to filter based on the information in the HTTP header or can review each parameter or cookies of requests …
- POST payload analysis: In addition to filtering based on HTTP headers, ModSecurity can be based on the content (payload) of the POST request.
- Audit logging: all requests can be logged (including POST) so that the administrator can monitor if necessary.
- HTTPS filtering: ModSecurity can analyze HTTPS.
- Compressed content filtering: ModSecurity will analyze after decompress the request data.
- And in this article we will conduct integrated Mod Security for Apache Web Server to combat SQL Injection and XSS attacks.
1. SQL Injection and XSS attack without Mod Security integration
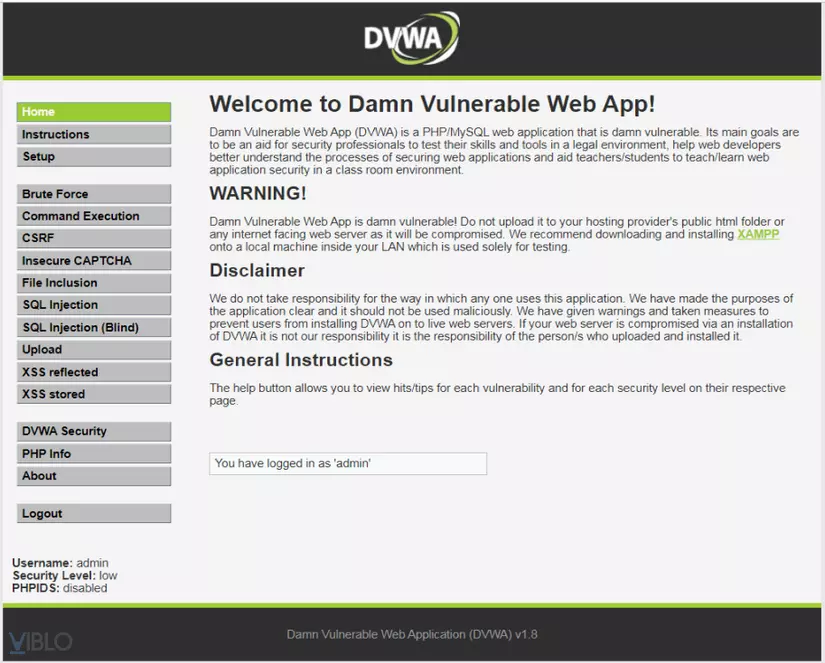
To test SQL Injection and attack XSS, I use Damn Vulnerable Web Application (DVWA), a PHP source application that gathers security errors including SQL Injection and XSS. After downloading the source code from: https://github.com/ethicalhack3r/DVWA , extract to C: xampp htdocs, launch and login with username / password: admin / password, the page interface The web is as follows:
1.1 Testing SQL Injection
In SQL Injection enter %' or '0'='0 and submit
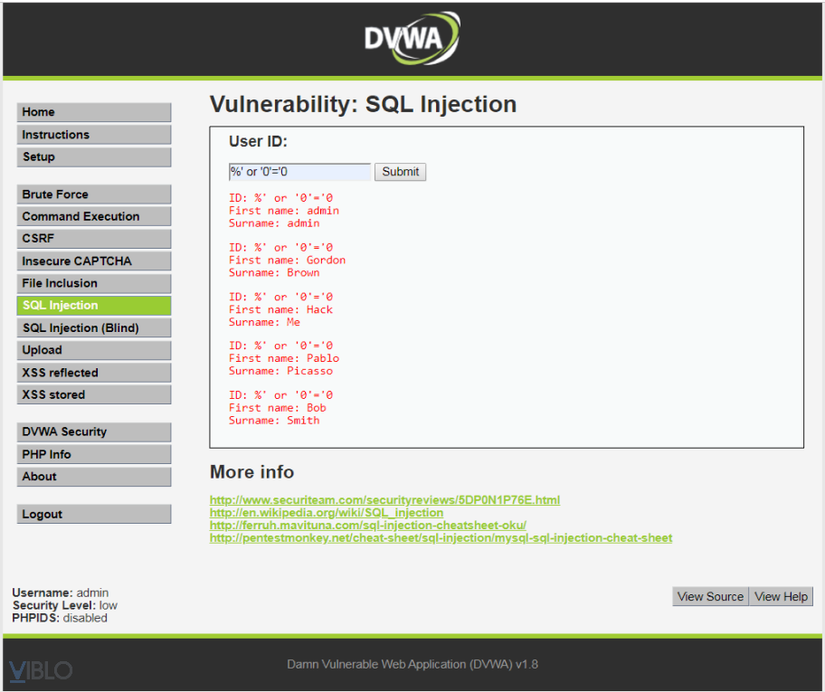
The result will receive information of all users who are in the database. Because the query now is understood as: SELECT * FROM users WHERE user_id = '%' or '0'='0'
1.2 Testing XSS
Go to XSS stored and submit the following script: <script>alert("Hacked! – KMA")</script> :
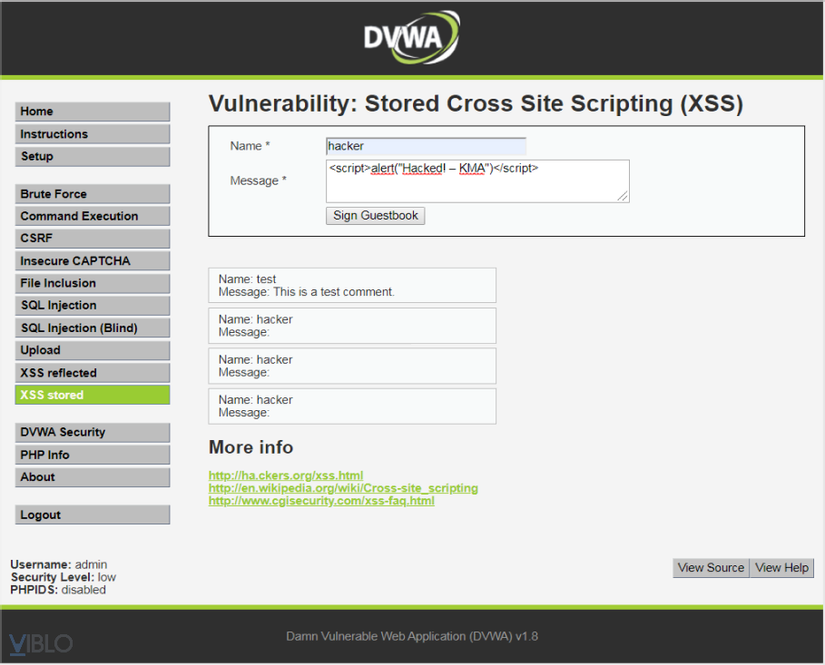
After submitting the above script, each time you visit, the website will display a notice to the user as follows:
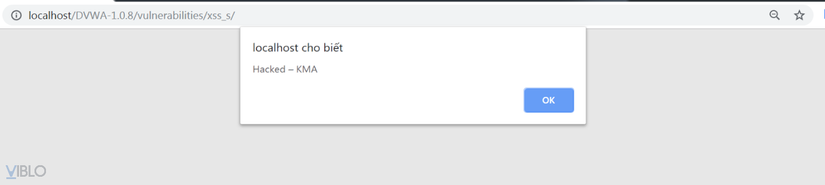
Through a few simple operations, it is easy to see that SQL Injection and XSS errors are easily exploited. Therefore, methods are needed to combat these types of attacks. There are many methods to combat SQL Injection and XSS attacks, but in this article I just mentioned the firewall integration method and specifically Mod Security on Apache.
2 Install and configure Mod Security
2.1 Installation
Visit https://www.apachelounge.com/download/ and download the corresponding mod_security.
Unzip and find 2 files mod_security2.so and yajl.dll in the yajl.dll folder.
- copy
mod_security2.sointo...apachemodules - copy
yajl.dll...apachebin
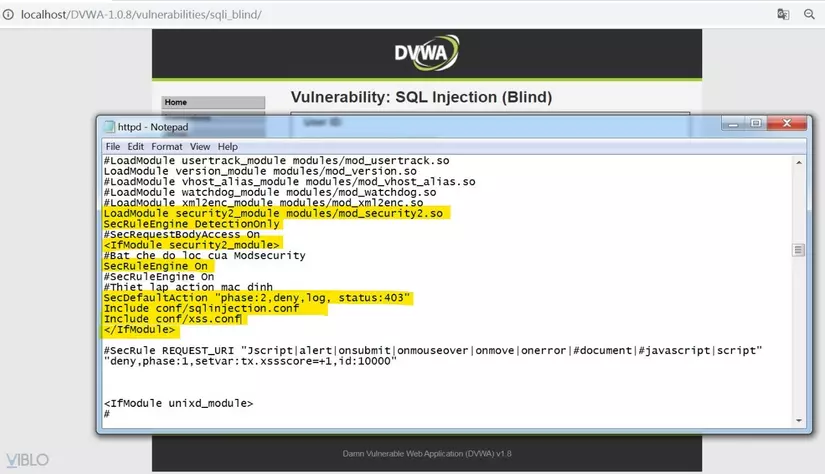
Open Xampp’s httpd.conf file and add the following lines:
LoadModule security2_module modules/mod_security2.so
SecRuleEngine DetectionOnly
<IfModule security2_module>
SecRuleEngine On
SecDefaultAction "phase:2,deny,log,status:403"
Include conf/sqlinjection.conf
Include conf/xss.conf
</IfModule>
2.2 Create conf file to set rules
Proceed to create 2 files sqlinjection.conf and xss.conf in the apacheconf directory of Xampp.
Clone all SQL Injection rules into sqlinjection.conf file and XSS Injection rules into xss.conf file.
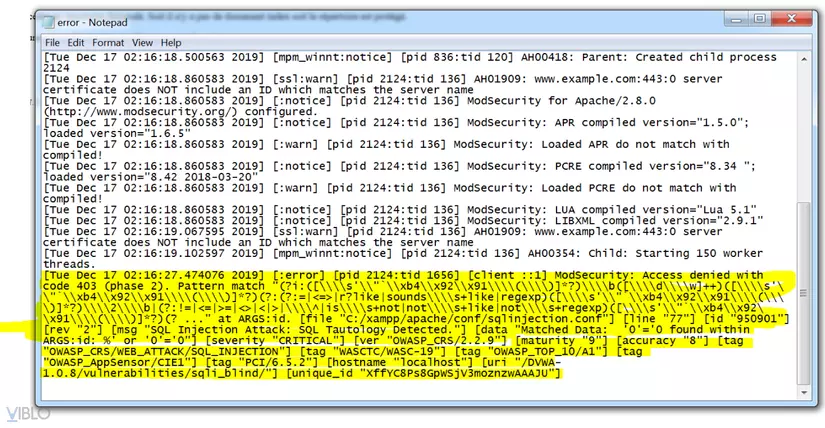
Proceed to restart Xampp Apache. Retesting SQL Injection and XSS attacks as shown in Part 1. The results are as follows:
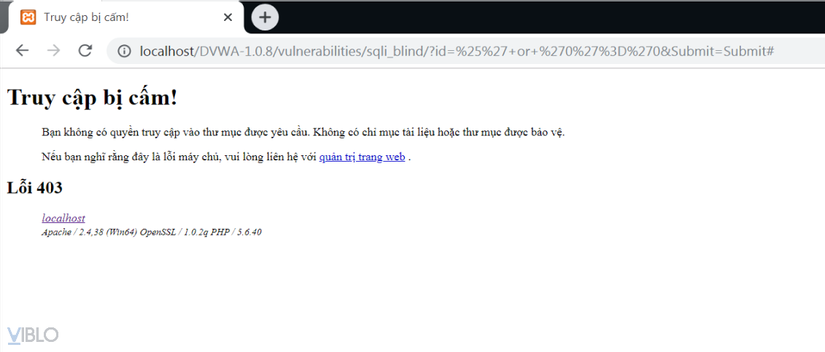
And at the same time, the log file that recorded bad requests from users has been blocked:
Demo video:
