Nowadays, when the application of Microservice architecture becomes more and more popular, we not only manage logs of one application on a server but now will be dozens, hundreds of different containers, logs lying garbage. on multiple servers. Debugging and monitoring the application becomes more difficult, so the build applications aim to focus the application’s logs on one place to become effective tools.
In this article, I will share how to build a Graylog application suite and how to configure containers to send logs to Graylog?
About Graylog
Graylog is considered a centralized log management application. Graylog can store every terabytes of logs every day, process and store it in memory. Graylog’s web interface allows you to search for records, quickly retrieve information, organize and display them in the form of maps, tables, …
Collecting Data: Graylog’s architecture allows input to be any type of data structure, including log messages and network traffic from:
- Syslog (TCP, UDP, AMQP, Kafka)
- GELF (TCP, UDP, AMQP, Kafka, HTTP)
- AWS – AWS Logs, FlowLogs, CloudTrail
- Beats / Logstash
- CEF (TCP, UDP, AMQP, Kafka)
- JSON Path from HTTP API
- Netflow (UDP)
- Plain / Raw Text (TCP, UDP, AMQP, Kafka) Organizing Data: Raw logs, raw messages are analyzed and enriched with information, making them useful for managers and downstream systems.
Implement Graylog with Docker
I will use Docker Compose to deploy the application. In production environment, we are not recommended to use Docker Compose , instead of Docker Swarm , it is also very easy to migrate the syntax of Docker Compose via Docker Swarm.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 | <span class="token key atrule">version</span> <span class="token punctuation">:</span> <span class="token string">'3'</span> <span class="token key atrule">services</span> <span class="token punctuation">:</span> <span class="token key atrule">mongo</span> <span class="token punctuation">:</span> <span class="token key atrule">image</span> <span class="token punctuation">:</span> mongo <span class="token punctuation">:</span> <span class="token number">3</span> <span class="token key atrule">volumes</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> <span class="token string">"./mongo/data/db:/data/db"</span> <span class="token key atrule">networks</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> graylog <span class="token key atrule">elasticsearch</span> <span class="token punctuation">:</span> <span class="token key atrule">image</span> <span class="token punctuation">:</span> docker.elastic.co/elasticsearch/elasticsearch <span class="token punctuation">-</span> oss <span class="token punctuation">:</span> 6.8.5 <span class="token key atrule">volumes</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> <span class="token string">"./elasticsearch/data:/usr/share/elasticsearch/data"</span> <span class="token key atrule">environment</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> http.host=0.0.0.0 <span class="token punctuation">-</span> transport.host=localhost <span class="token punctuation">-</span> network.host=0.0.0.0 <span class="token punctuation">-</span> <span class="token string">"ES_JAVA_OPTS=-Xms512m -Xmx512m"</span> <span class="token key atrule">ulimits</span> <span class="token punctuation">:</span> <span class="token key atrule">memlock</span> <span class="token punctuation">:</span> <span class="token key atrule">soft</span> <span class="token punctuation">:</span> <span class="token number">-1</span> <span class="token key atrule">hard</span> <span class="token punctuation">:</span> <span class="token number">-1</span> <span class="token key atrule">deploy</span> <span class="token punctuation">:</span> <span class="token key atrule">resources</span> <span class="token punctuation">:</span> <span class="token key atrule">limits</span> <span class="token punctuation">:</span> <span class="token key atrule">memory</span> <span class="token punctuation">:</span> 1g <span class="token key atrule">networks</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> graylog <span class="token key atrule">graylog</span> <span class="token punctuation">:</span> <span class="token key atrule">image</span> <span class="token punctuation">:</span> graylog/graylog <span class="token punctuation">:</span> <span class="token number">3.2</span> <span class="token key atrule">volumes</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> <span class="token string">"./graylog:/usr/share/graylog/data/journal"</span> <span class="token key atrule">environment</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> GRAYLOG_PASSWORD_SECRET=somepasswordpepper <span class="token comment"># Password: admin</span> <span class="token punctuation">-</span> GRAYLOG_ROOT_PASSWORD_SHA2=8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918 <span class="token punctuation">-</span> GRAYLOG_HTTP_EXTERNAL_URI=http <span class="token punctuation">:</span> //127.0.0.1 <span class="token punctuation">:</span> 9000/ <span class="token key atrule">networks</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> graylog <span class="token key atrule">depends_on</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> mongo <span class="token punctuation">-</span> elasticsearch <span class="token key atrule">ports</span> <span class="token punctuation">:</span> <span class="token punctuation">-</span> 9000 <span class="token punctuation">:</span> <span class="token number">9000</span> <span class="token punctuation">-</span> 5140 <span class="token punctuation">:</span> <span class="token number">5140</span> <span class="token punctuation">-</span> 1514 <span class="token punctuation">:</span> 1514/udp <span class="token punctuation">-</span> 12201 <span class="token punctuation">:</span> <span class="token number">12201</span> <span class="token punctuation">-</span> 12201 <span class="token punctuation">:</span> 12201/udp <span class="token key atrule">networks</span> <span class="token punctuation">:</span> <span class="token key atrule">graylog</span> <span class="token punctuation">:</span> <span class="token key atrule">driver</span> <span class="token punctuation">:</span> bridge |
I have used 3 more folders used for the purpose of volumes of services, so I need to grant read-write permission to those folders first.
Then just run docker-compose up and wait for the application to pop up, you just need to visit the address: http: // localhost: 9000 to use the web interface. You log in with your account / password as admin / admin .
So I turned on the application, until the next step only.
Configure to send logs to Graylog.
Configure Input for Graylog
You access here to create Input configuration for Graylog http: // localhost: 9000 / system / inputs , I will send logs from Syslog via TCP so I configure the following: 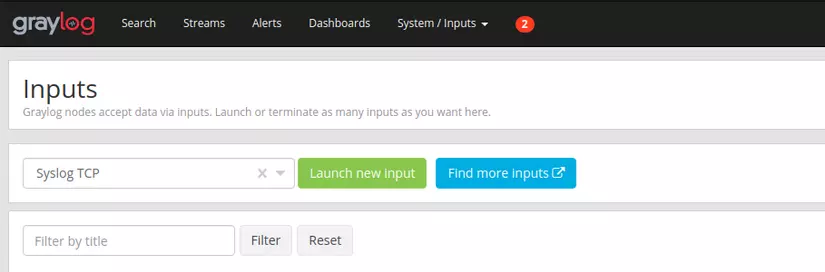
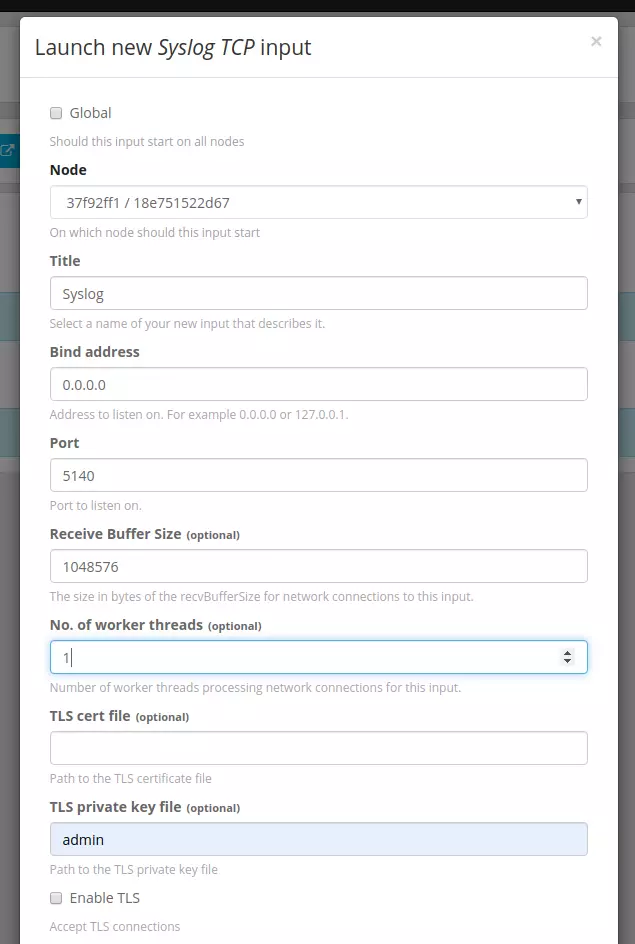
Click Save and wait for it to switch to the RUNNING state.

Configure on the application to send them to Graylog
Here I use Rsyslog to post logs to Graylog. Depending on your operating system, Rsyslog needs to be installed.
Configure the output of Rsyslog in /etc/rsyslog.conf :
1 2 3 | <span class="token punctuation">..</span> . *.* @@localhost:5140 <span class="token punctuation">;</span> RSYSLOG_SyslogProtocol23Format |
Then you restart service rsyslog to get the new configuration
1 2 | $ sudo service rsyslog restart |
I will test by logging in / logout of the computer =)) and BOM
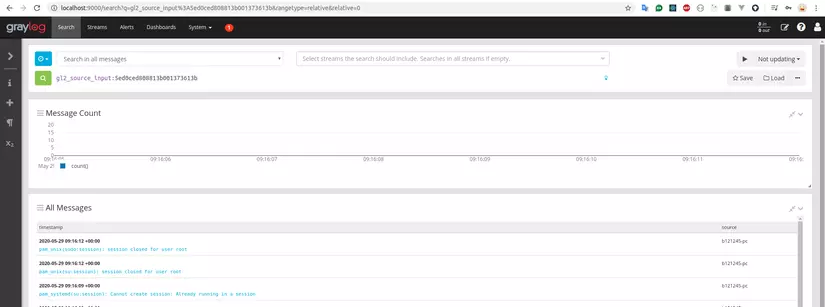
The log has been successfully submitted to Graylog.
Conclusion
Above are the basic configuration steps to build Graylog in order to collect logs from different sources to a place. A little more advanced, you can configure in Graylog filters to filter logs by each application, each log type, each different log level.
