Viruses?
Surely you have heard the concept of virus malware or worse, your PC has been infected with virus and many times you have to go out to the shop to reinstall the operating system because of these viruses. Its harmful effects are also heavy:
- Discomfort to us is the first harm.
- Causing loss of important computer data.
- It may even hurt the hardware.
So what is a virus?
In computer science, computer viruses computer viruses (often referred to as viruses by users) are program scripts designed to perform at least two things:
- Self-intrusion into the current computer’s operation properly, to perform self-replication and other programmer’s intentional work. After executing the virus code, the controller is returned to the executing program without “hanging”, unless the virus intentionally crashes.
- Self-copying, ie self-replicating, legally infects files or specific regions (boot, FAT sectors) in storage devices such as hard disks, floppy disks, or devices. flash memory (commonly USB), … even the main EPROM of the machine.
Previously, viruses were often written by some programmers who wanted to prove their ability, so viruses often acted like: for a program not working properly, deleting data, damaging the hard drive, … or make nasty jokes.
The recently written viruses no longer make jokes or damage to the infected victim’s computer, but mostly aim to steal sensitive personal information (codes credit card numbers) opens the back door for hackers to hijack or otherwise take advantage of the virus spreader.
So theoretically, in this article, I will go into how to create a virus with a tool, okay?
- First you need to install CFF explorer , Odbg110 and prepare an exe file (32 bit, the better – you can get it in Windows XP).
- So why do I tell you to prepare an exe file for me, I think I will try to insert malicious code into this exe file so that when we execute this exe file, the malicious code will be activated as expected. the meaning of the virus: 3
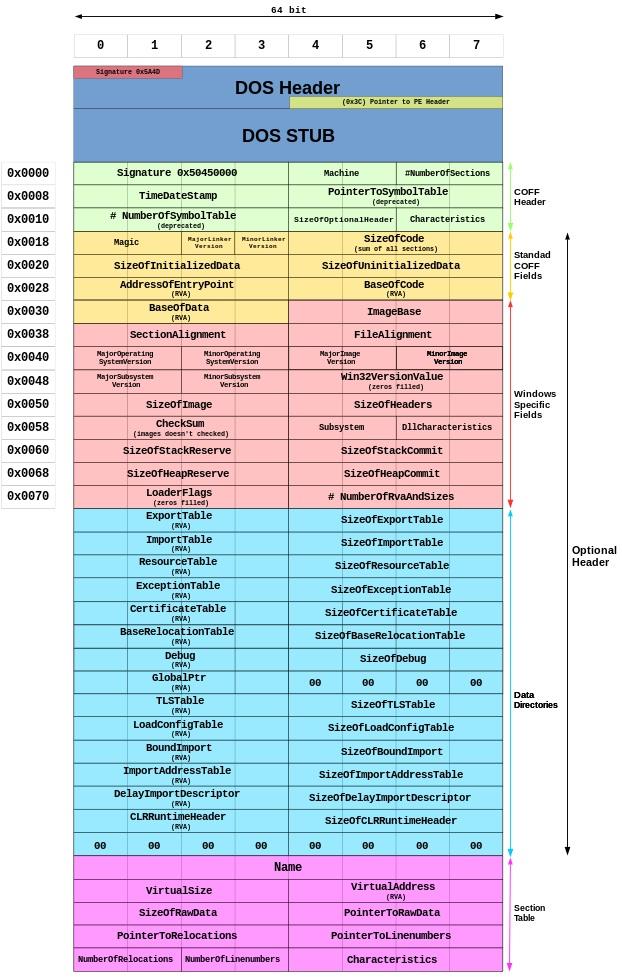
- We will learn about the structure of an exe file to see what it contains

* Here I would like to mention the main part we manipulate, and the other parts you can learn by yourself through the keyword PE format:>
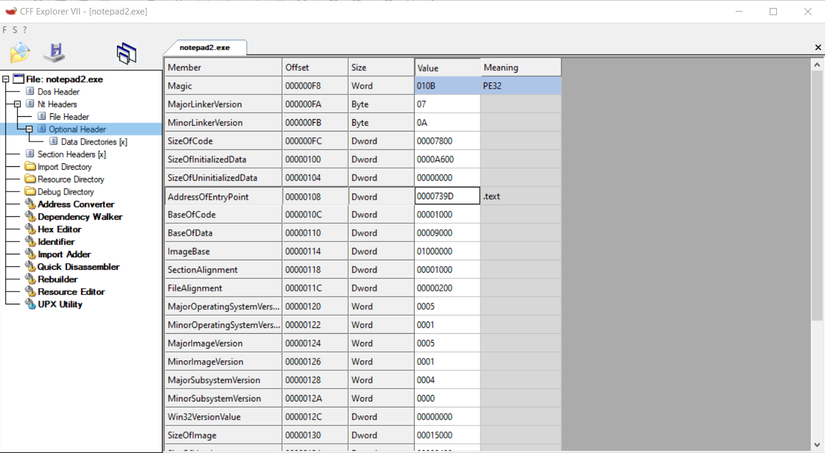
- In the optional Header -> Standard COFF Fields -> AddressOfEntryPoint , this is the key to running this program. Or in other words, for those of you who have learned to program, to execute a certain program, we will know it calls the main () function and sequentially execute the functions called in the main () function, then AddressOfEntryPoint is the call to the first function to execute in main () so if we change the value of this component, we will call another function and change the sequence of function execution.
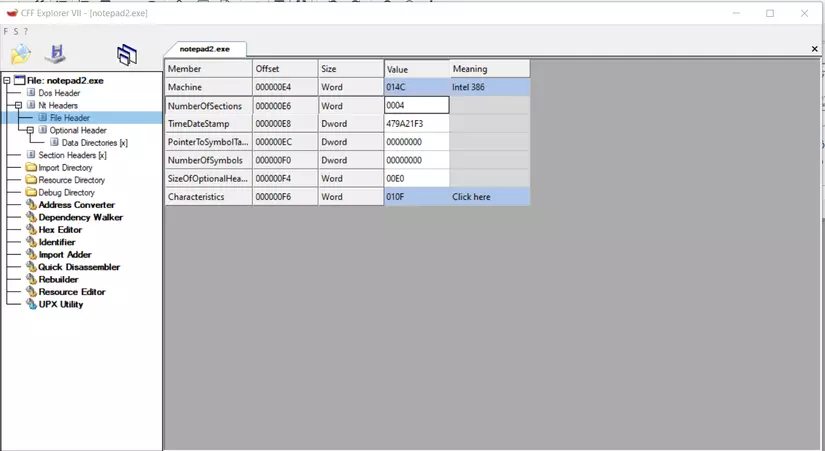
- So when a program runs, the content of this exe file will be divided into section tables (You can see that it is the last part in the above structure). A program when executed will run the section tables in order from top to bottom (each exe file will have a certain number of section tables ). In the COFF Header -> NumberOfSections section there is no section table number that this exe file executes. For example, the value of this component is 3, it only executes 3 section tables so if we try to attach the section table here, this exe file also only executes 3 section table .
- So we need to pay attention to the above components when implementing malicious code into the exe file.
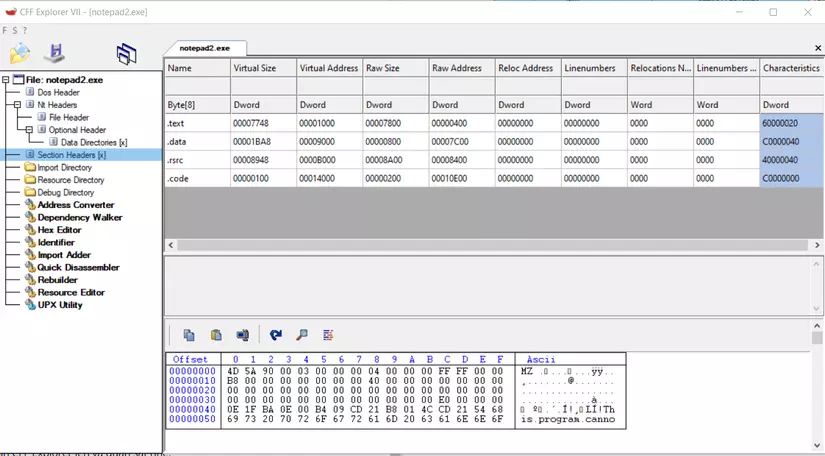
- Let’s open the CFF Explorer program and observe:

- On our left hand side is the menu table, including the parts of an exe file and I have the Section Header (the Section table ) enabled, then we observe here the notepad2.exe file includes 4 section tables : .text , .data , .rsrc , .code

- This is the AddtressOfEntryPoint part I showed you above, the Value of this component is the call to the first executable function in the main () function of this exe file.

- This is the NumberOfSections section I presented to you above, here its Value is the number of Section Tables and is equal to 4 exactly as the 4 Section Tables above.

- Now our job is to add an empty section to this exe file and add malicious code to this empty section.
- In this part, I would like to finish at understanding the concept and implementation ideas, in the next section I will start to detail the implementation steps. Please watch it together! Thank you for reading!