In the process of finding Lab articles about Android Security, I stumbled upon this Lab EVABS. This is a very good lab, suitable for beginners to learn about Android Security. However, finding this lab is not easy, because this is a new lab that most basic documents have not updated EVABS information.
Say the basic lab because EVABS has 12 levels, each level is built based on a security hole of Android applications. However, to complete all 12 levels with new students is not easy.
When comparing EVABS with previous famous Android labs, we can see the following outstanding points:
- Catch up with technology : laboratories like InsecureBankv2, DIVA, … have been designed since about 5 years ago. And since then, the Android application has also grown stronger. The last EVABSv4 update about 6 months ago (compared to the time I wrote this article) makes the “clearing” this lab is like exploiting the vulnerability of an actual Android application.
- High challenge : until writing this article, I have not found a tutorial, or writeup for EVABS (maybe because I have not searched well). In the process of doing the lab, I can only reference from some other Lab and from the hint of each level, and hope that helps to find the flag. Even when I was level 11, I had to email the author to check if the flag was correct.
Further information about EVABS can be found at the original repo . Now we will “clear” 12 levels of EVABSv4.
Level 1: Debug Me
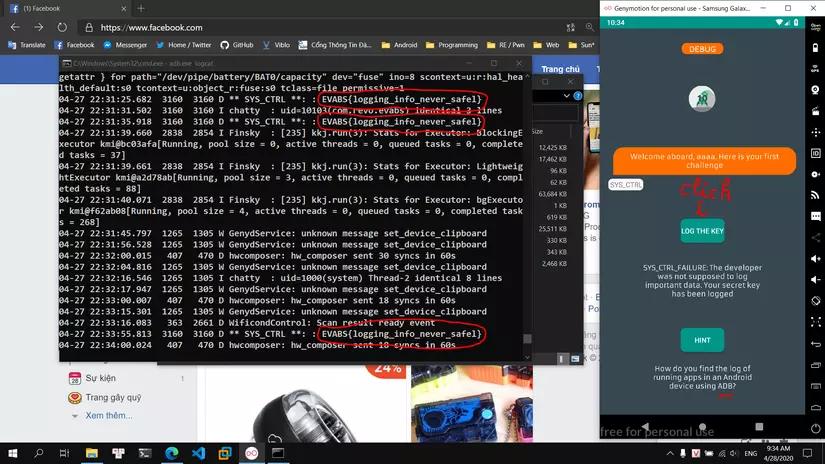
At level 1 we need to check the system log. This is also one of the things to do when testing Android apps. Revealing important information in the log is caused by the dev’s negligence.
Now it is no longer common to expose important information about a log application because the dev team has been recommended for this. However, this is also a direction to check, maybe there are no important logs left behind.
Simple log checking with command: adb logcat .
However, it will be very confusing, to eliminate the system’s log lines and focus only on the application’s log we will do the following:
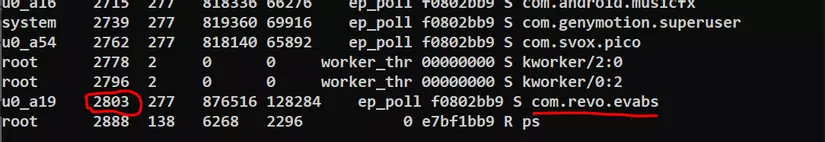
- B1: run
adb shell pscommand to find application’s PID. 
- B2: Once you’ve found the application’s PID, run
adb logcat --pid=[app's pid].
Once you have read the log, click on the “LOG THE KEY” button and see the flag at logcat.
Level 2: File Access
The directories in an Android project are very specific hierarchies, so we always know where an application’s resources are stored. One of the places the application uses to store resources is the assets folder.
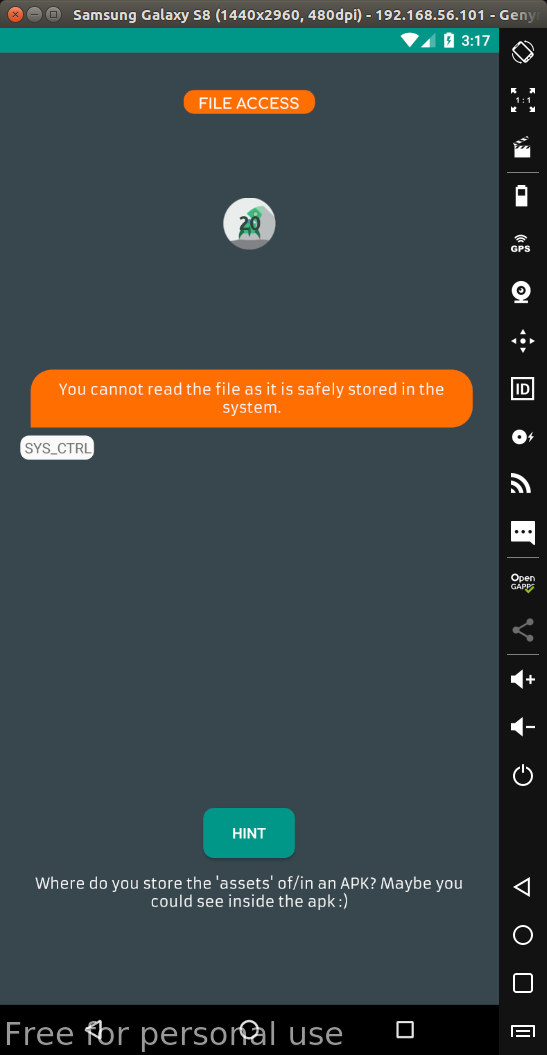
All of these resources are compressed into apk files along with the application’s code files. To get these resources, we just need to change the apk file -> zip and unzip (on linux, just unzip always without changing the file extension).
Now just go to the assets directory and we will see a file containing the flag.
Level 3: Strings
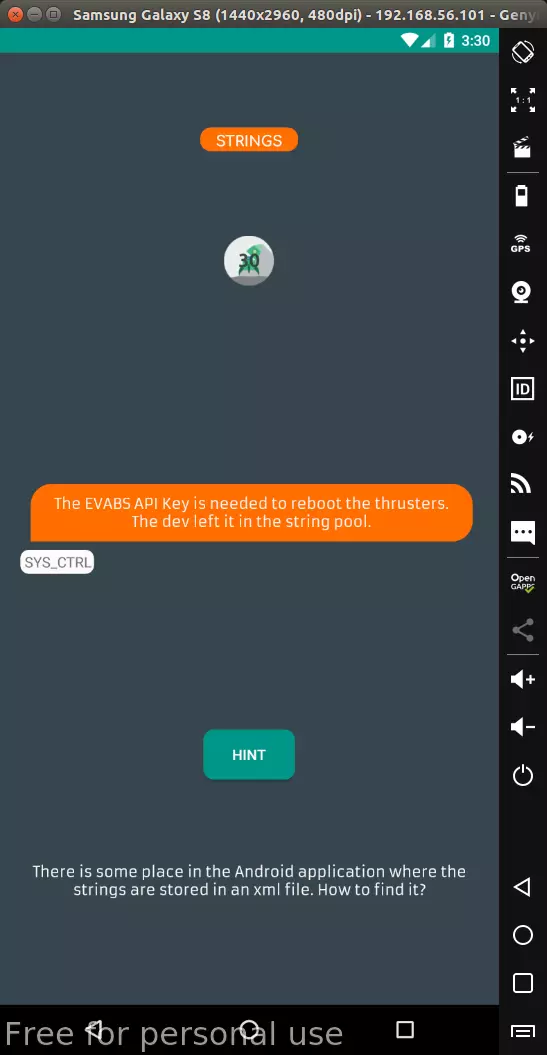
The strings used in the application are saved in the strings.xml file. Too familiar, decompile with apktool and strings.xml straight ahead.
In fact, rarely important information such as decryption keys, … will appear in this file, but the use of this file can aid in the process of decompiling the application.
Level 4: Resource
By suggestion, it’s easy to know that the flag is in a certain file among a bunch of files in the res directory. Of course we will only use one command, finding all the files is too tiring for a lazy person like me: grep -r "EVABS{" * . And we know the flag is located at res / raw / link.txt
Level 5: Shares and Preferences
SharedPreferences is an API that permanently stores data in XML files. The data stored by the SharedPreferences object has a key – value structure.
The SharedPreferences object can be declared for all applications used, or private. Data is stored in XML files at /data/data/<package-name>/shared_prefs/*.xml .
Use the adb shell to access the android system with the command cd /data/data/com.revo.evabs/shared_prefs and run grep -r "EVABS" * to find hidden flags in xml files.
Level 6: DB Leak
Android applications also need to store local data. One of the places the application uses to store data is SQLite DB. These databases are always located at /data/data/<package-name>/databases
After clicking the “FETCH CREDS” button, the DB will be generated in Local Storage.
Now run the adb shell "ls /data/data/com.revo.evabs/databases" to check for any available db. Here only 1 db is MAINFRAME_ACCESS.
Pull that DB to the real machine to open it using SQLite browser with the adb pull "/data/data/com.revo.evabs/databases/MAINFRAME_ACCESS" command adb pull "/data/data/com.revo.evabs/databases/MAINFRAME_ACCESS" . See the tables that see the flag as the password of the Dr.l33t user with the admin role.
Level 7: Export
In the Android application there is the concept of activity . Activity in Android is where all activities interact with users, because all application screens must be “attached” on an Activity.
Information about the activity is saved in the AndroidManifest.xml file, which appears in the <activity ….. /> tags . There is one important attribute in this card : android: exported . If this property has a value of true , that activity may be triggered by other applications.
When checking the manifest, there is information about an exported Activity on the fourth line:
1 2 | <span class="token tag"><span class="token tag"><span class="token punctuation"><</span> activity</span> <span class="token attr-name"><span class="token namespace">android:</span> exported</span> <span class="token attr-value"><span class="token punctuation">=</span> <span class="token punctuation">"</span> true <span class="token punctuation">"</span></span> <span class="token attr-name"><span class="token namespace">android:</span> name</span> <span class="token attr-value"><span class="token punctuation">=</span> <span class="token punctuation">"</span> com.revo.evabs.ExportedActivity <span class="token punctuation">"</span></span> <span class="token punctuation">/></span></span> |
When an activity is exported, we can start it with adb. Use adb to trigger exported activities with the command: adb shell am start -n [package name]/[package name].[exported activity] .
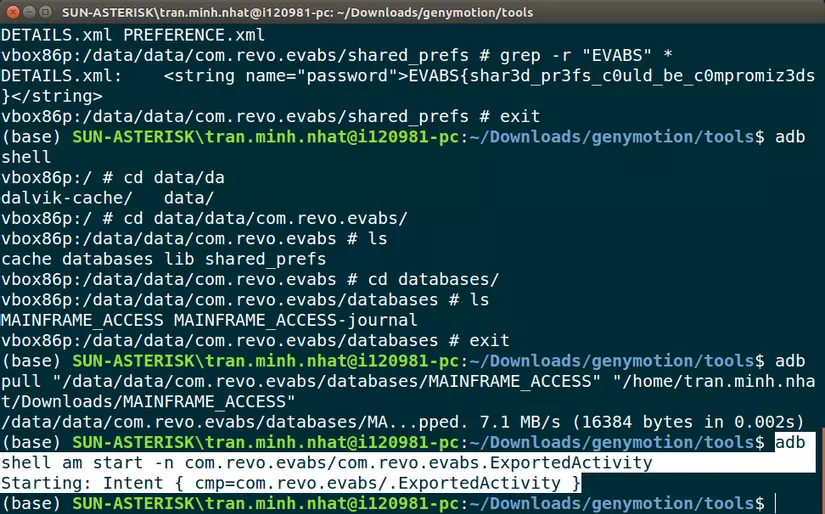
Level 8: Decode
Hardcoded important strings are not safe, as hackers can easily reverse the apk file and find these strings.
Reverse the java code with the Bytecode viewer, then open the Decode.class file – the java code file for level 8 immediately see 3 hardcoded text.
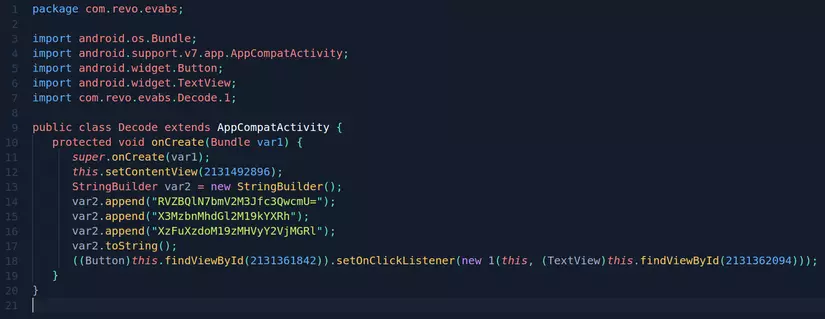
Decode B64 with these 3 strings we get the flag.
Above is the write up of the first 8 levels of the EVABSv4 lab. To do what I said above just need to know how to use computers and operating systems Linux / Windows is able to do.
The next level I will talk in part 2. With levels 9-12 will require more in-depth knowledge of Android applications and how to use the tools, frameworks genuine finesse.